AWS Solutions Architect Associate Certification
Services Networking
Default VPC Demo
In this article, we explore the default Virtual Private Cloud (VPC) settings that AWS automatically configures when you create a new account. We will guide you through the VPC dashboard, inspect default configurations, and demonstrate how these settings enable internet connectivity for your AWS resources.
Accessing the Default VPC
Begin by navigating to the VPC section in the AWS Management Console. You can access this by selecting "VPC" from the list of services or by searching for "VPC." Although the console may display a specific region (e.g., Northern Virginia), note that the default VPC configuration remains consistent across all AWS regions.
For new AWS accounts, you will observe that there is only one default VPC created, even though additional security groups might be visible that are not part of the default configuration.
Inspecting the Default VPC Details
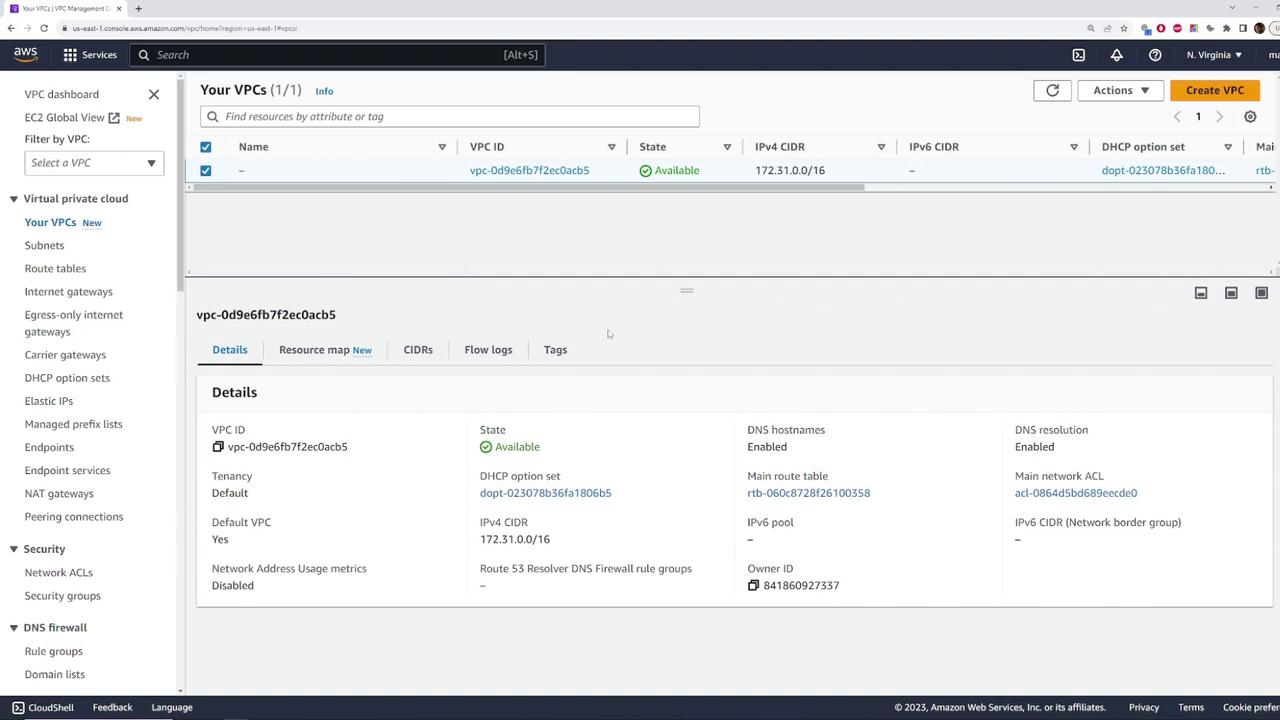
Click on the default VPC to view its detailed configuration. Here are the key elements you will notice:
- The VPC state is "available."
- The CIDR block is set to 172.31.0.0/16.
- It is explicitly marked as the default VPC.
Additional details such as route tables and network ACLs are also available, but these primary indicators confirm that this is your default VPC.
Exploring Different Regions
To verify consistency across regions, switch to another region, such as Ohio, and confirm that the default VPC setup is identical. In any region, you will find one VPC with the same CIDR block (172.31.0.0/16) and the default designation.
Returning to the Northern Virginia region, you can now dive deeper into the VPC resources.
Examining the Default Subnets
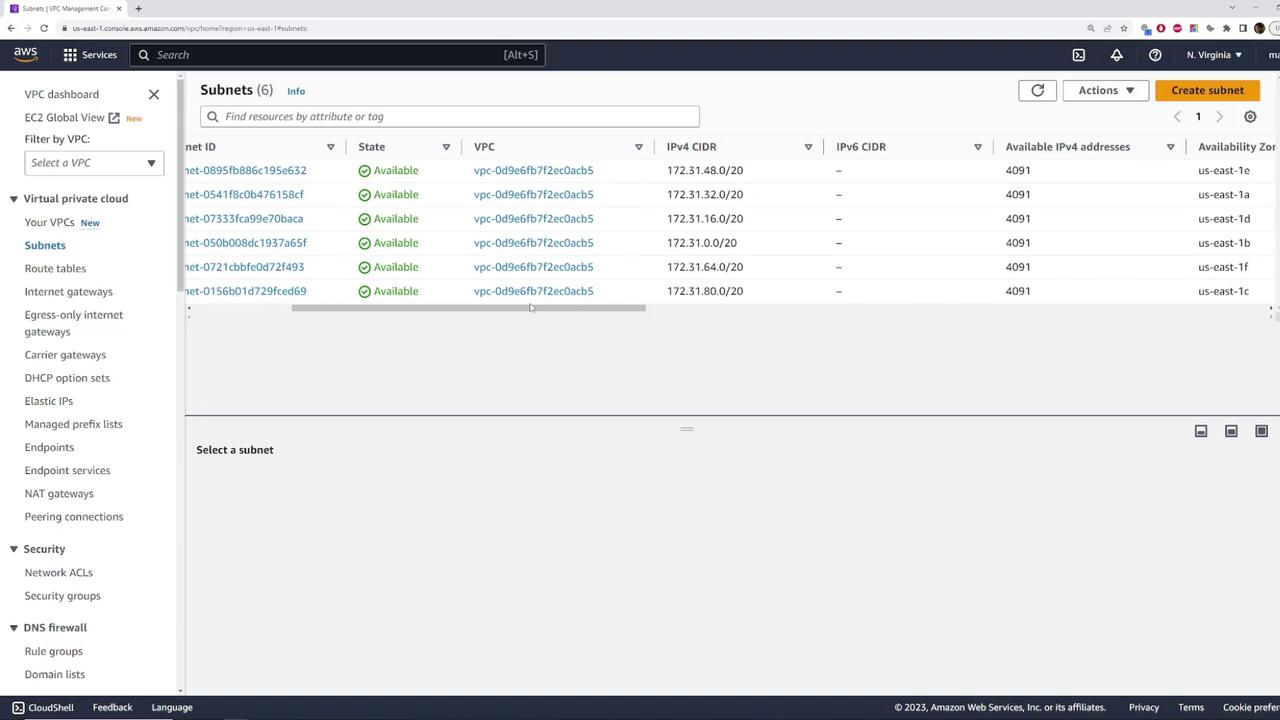
Under the default VPC, navigate to the "Subnets" section. Here are some important observations:
- The VPC ID is displayed in a truncated format (for example, ending in ACB5).
- There are six subnets, each associated with the default VPC.
Each subnet corresponds to a different availability zone (e.g., 1A, 1B, 1C, 1D, 1E, 1F), ensuring comprehensive coverage across the region.
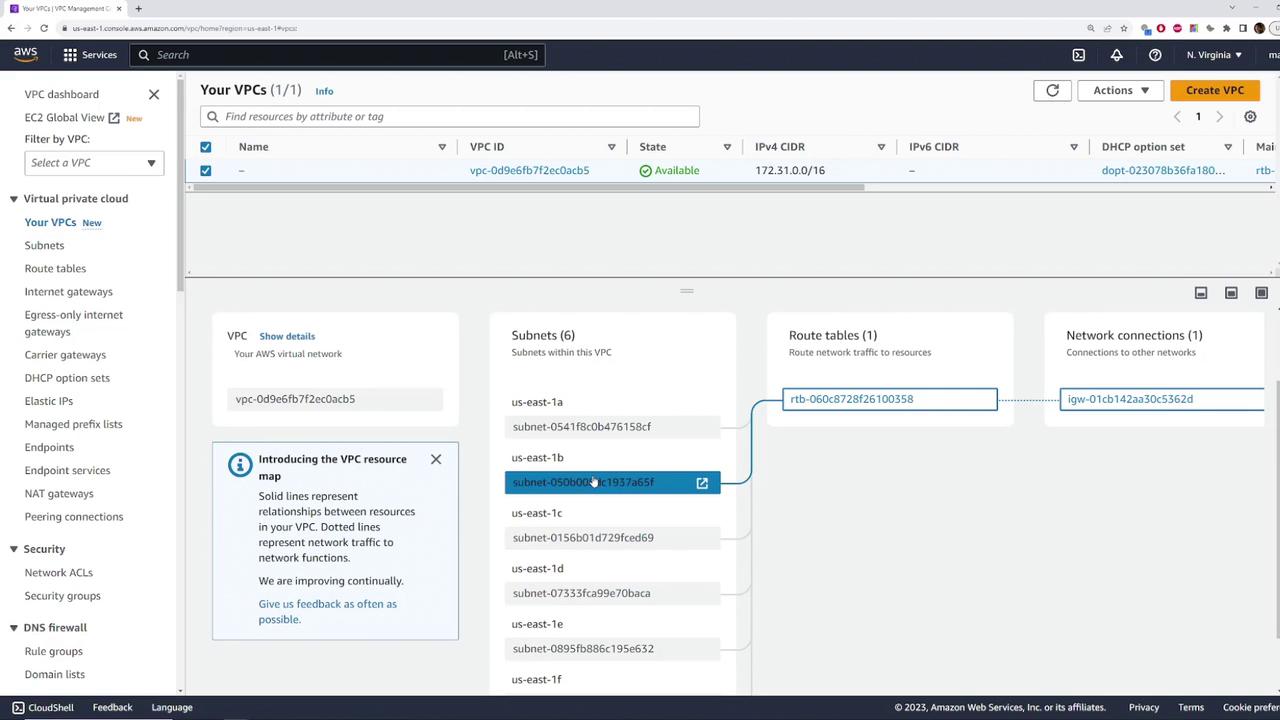
For a clearer view of the network topology, return to the VPC resource map page to see all six subnets mapped to their respective availability zones.
Route Tables, Network ACLs, and Internet Gateway
The default VPC includes a route table that manages the traffic between the subnets. By clicking on the route table, you can review its configuration, which appropriately directs subnet traffic. While we are not covering the route table in detail here, it plays a crucial role in routing network traffic.
Note
An Internet Gateway is automatically created and attached to the default VPC. This gateway allows resources within the VPC to access the internet. With the correct routing settings, any instance launched within a default subnet will have an auto-assigned public IPv4 address.
Deploying an EC2 Instance to Validate Internet Connectivity
To demonstrate the functionality of the default VPC, follow these steps to deploy an EC2 instance:
- Open the EC2 section in the AWS Management Console.
- Launch a new instance using the default settings (for example, choose Amazon Linux and a T2 micro instance).
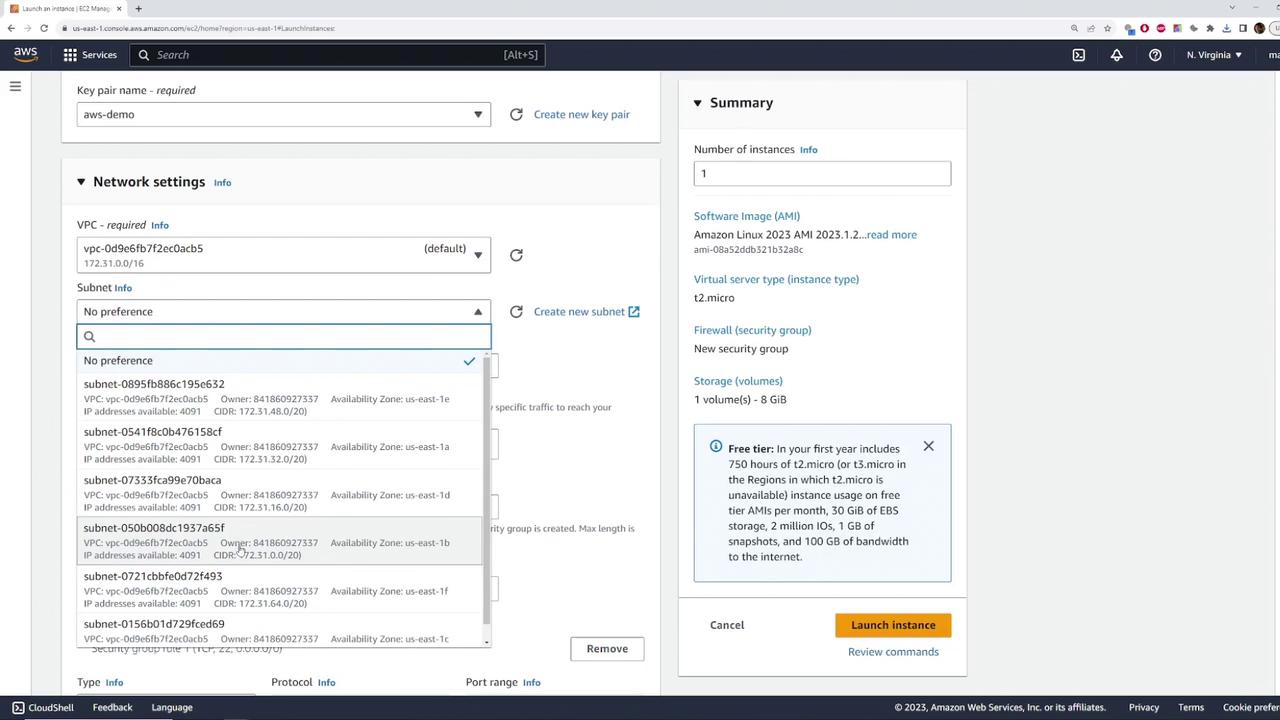
- During network configuration, confirm that the instance is launched in the default VPC with the CIDR block 172.31.0.0/16 and select one of the default subnets.
- Ensure the instance is set to auto-assign a public IPv4 address for immediate internet access.
When configuring the instance, double-check that the selected VPC is indeed the default VPC. You may also choose a specific subnet corresponding to an availability zone (e.g., US East 1B) if needed.
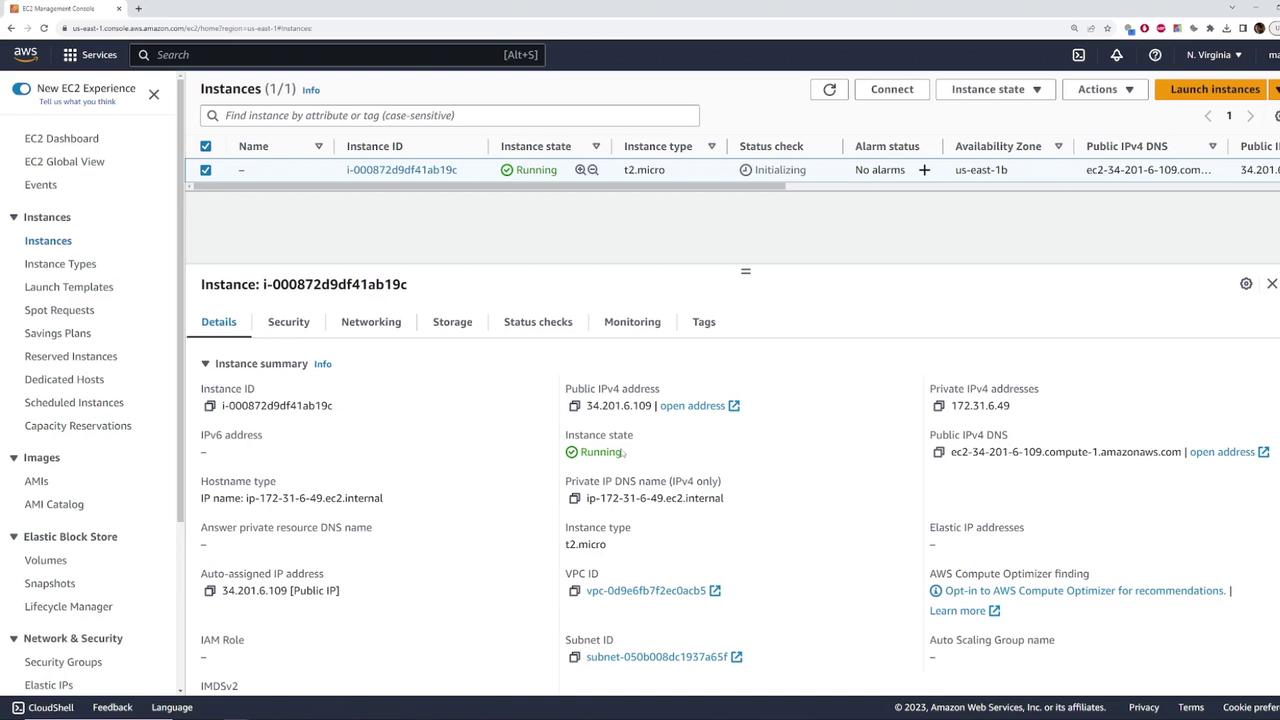
Once launched, navigate to the "Instances" section to verify the instance's status. The key details to verify are:
- The instance is in a running state.
- It has a private IP address from the subnet.
- It has automatically been assigned a public IP address.
Connecting to the EC2 Instance
To confirm internet connectivity, establish an SSH connection to the EC2 instance. If you have your PEM file ready, use the following command:
C:\Users\sanje\Documents\scratch\aws-demo>ssh -i aws-demo.pem [email protected]
The authenticity of host '34.201.6.109 (34.201.6.109)' can't be established.
ECDSA key fingerprint is SHA256:fa0CPuuMP2Fvn9aHeAw56Eei94znaTnFefIDRg1mE.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '34.201.6.109' (ECDSA) to the list of known hosts.
After connecting, test the connectivity by pinging an external address (for example, the Google DNS server) to ensure that the instance has proper internet access.
Conclusion
This article demonstrated how AWS pre-configures a default VPC to simplify resource deployment with built-in internet connectivity. By creating a default VPC, setting up subnets across all availability zones, and integrating route tables and an Internet Gateway, AWS enables you to quickly launch and manage EC2 instances with minimal networking configuration.
Happy cloud computing!
For further reading, check out these resources:
Watch Video
Watch video content