AWS Solutions Architect Associate Certification
Services Networking
NAT Gateways VPC Demo
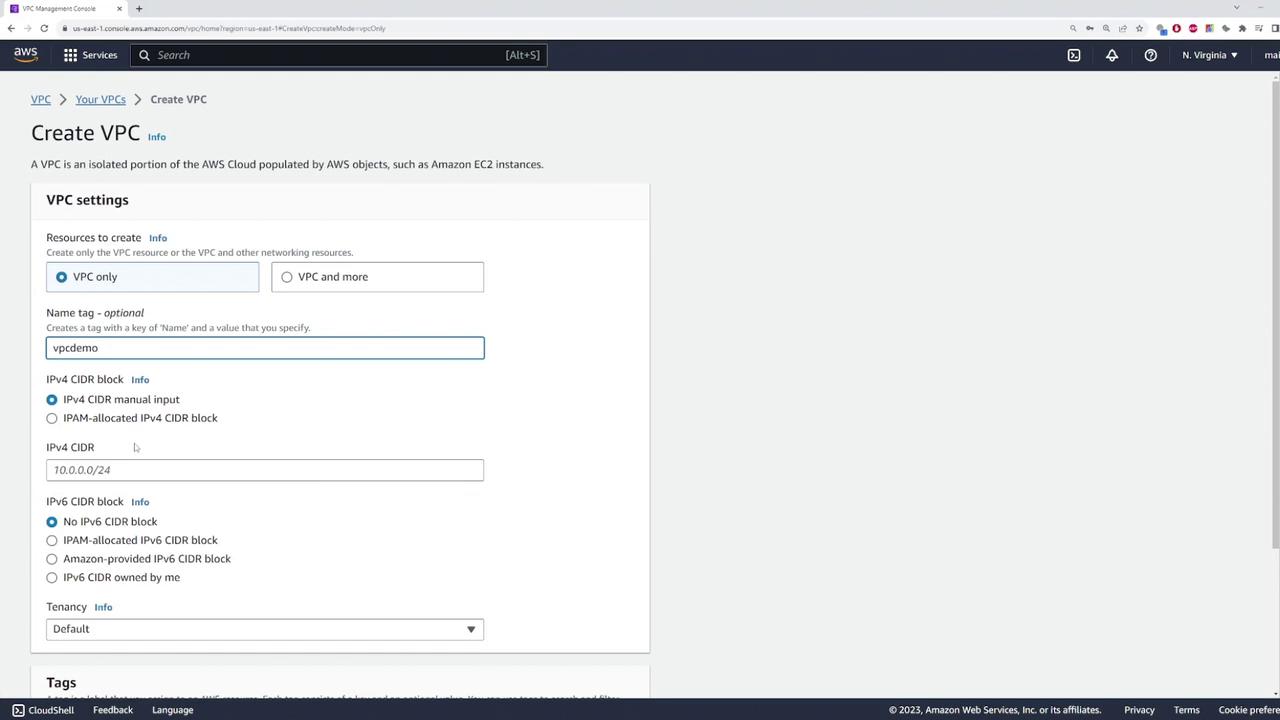
In this article, we demonstrate how to configure NAT gateways in AWS to allow an EC2 instance to access the internet securely. This setup ensures that only outbound connections initiated from within AWS are allowed. The EC2 instance makes internet requests via the NAT gateway, while external sources cannot initiate a connection to it. We create a dummy Virtual Private Cloud (VPC) using the CIDR block 10.0.0.0/16.
Step 1: Create the Private Subnet
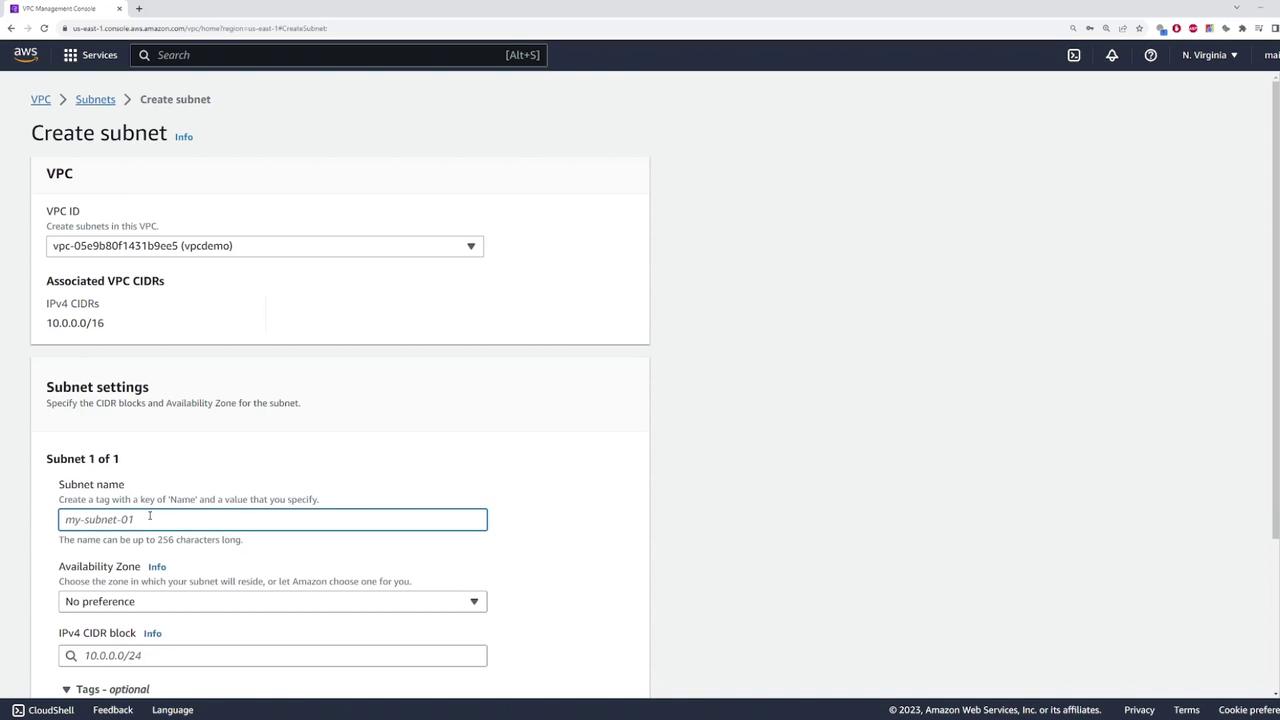
Next, create a private subnet where your EC2 instance will reside. For this demo, configure the subnet with the CIDR block 10.0.1.0/24.
Step 2: Launch an EC2 Instance
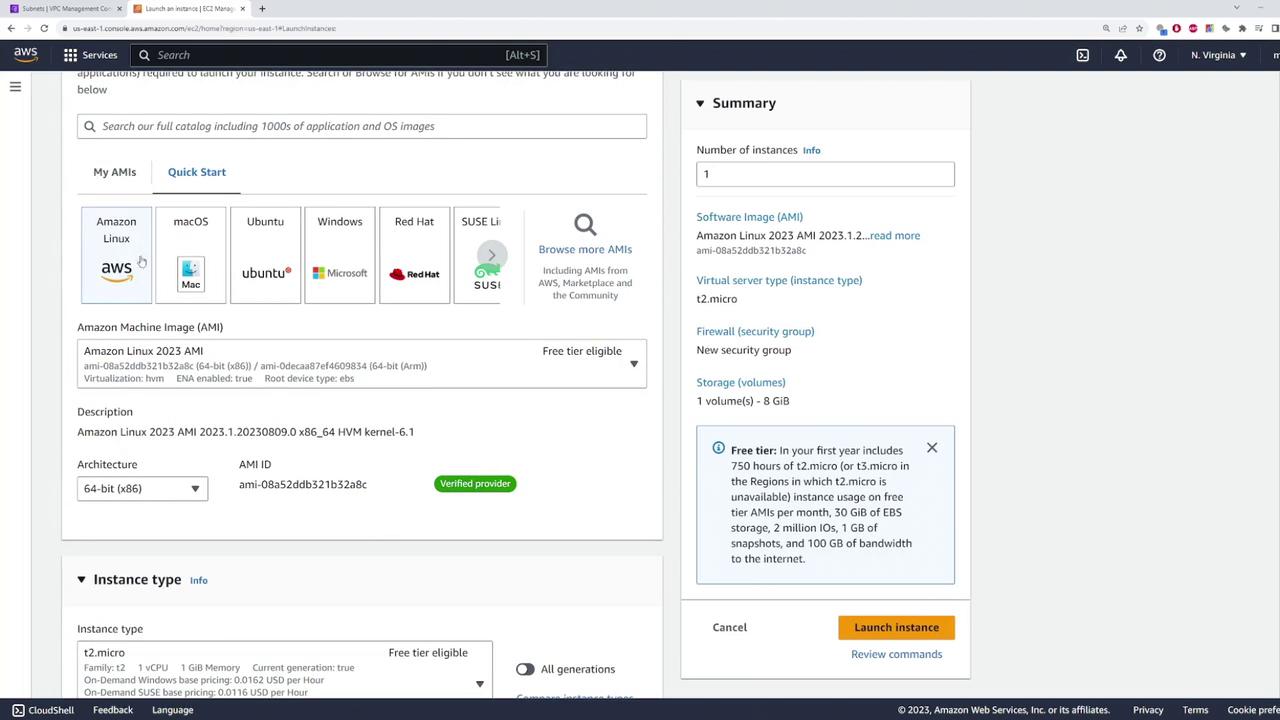
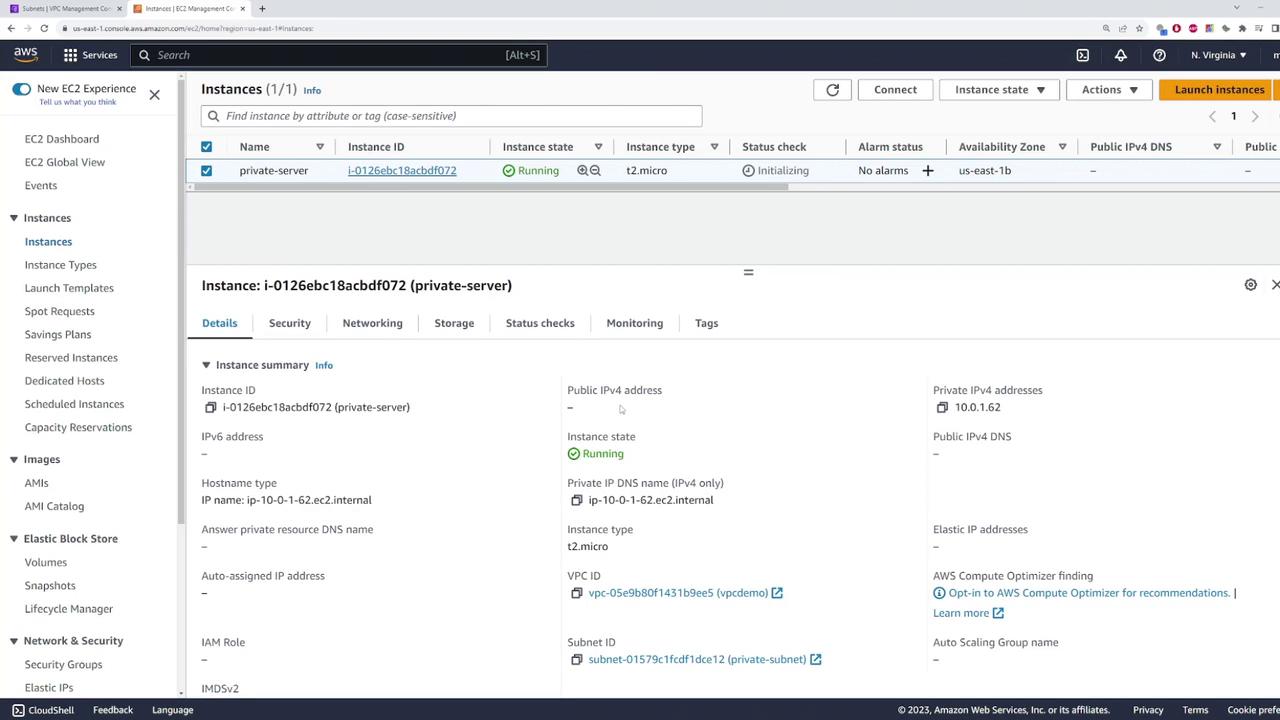
After setting up the VPC and private subnet, navigate to the EC2 console to launch an instance in the private subnet. Name the instance "private-server" and use the default Amazon Linux image.
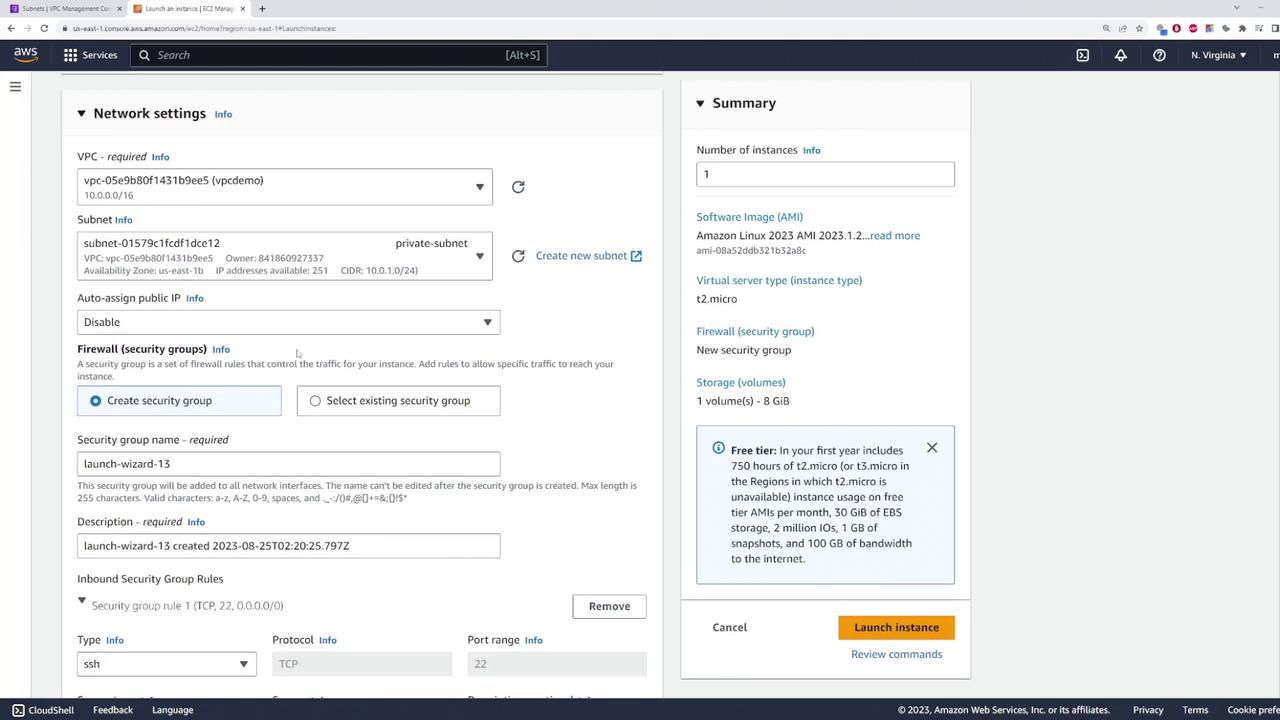
During the network configuration step while launching the instance, select the VPC ("VPC demo") and choose the private subnet. Do not assign a public IP address since internet access will be provided via the NAT gateway.
After the instance is launched, you will notice that no public IP address is assigned. This means the EC2 instance is not directly accessible from the internet. To manage or reach the instance, you should use a VPN connection or another secure method to access your private network.
Step 3: Configure the Internet Gateway and Public Subnet
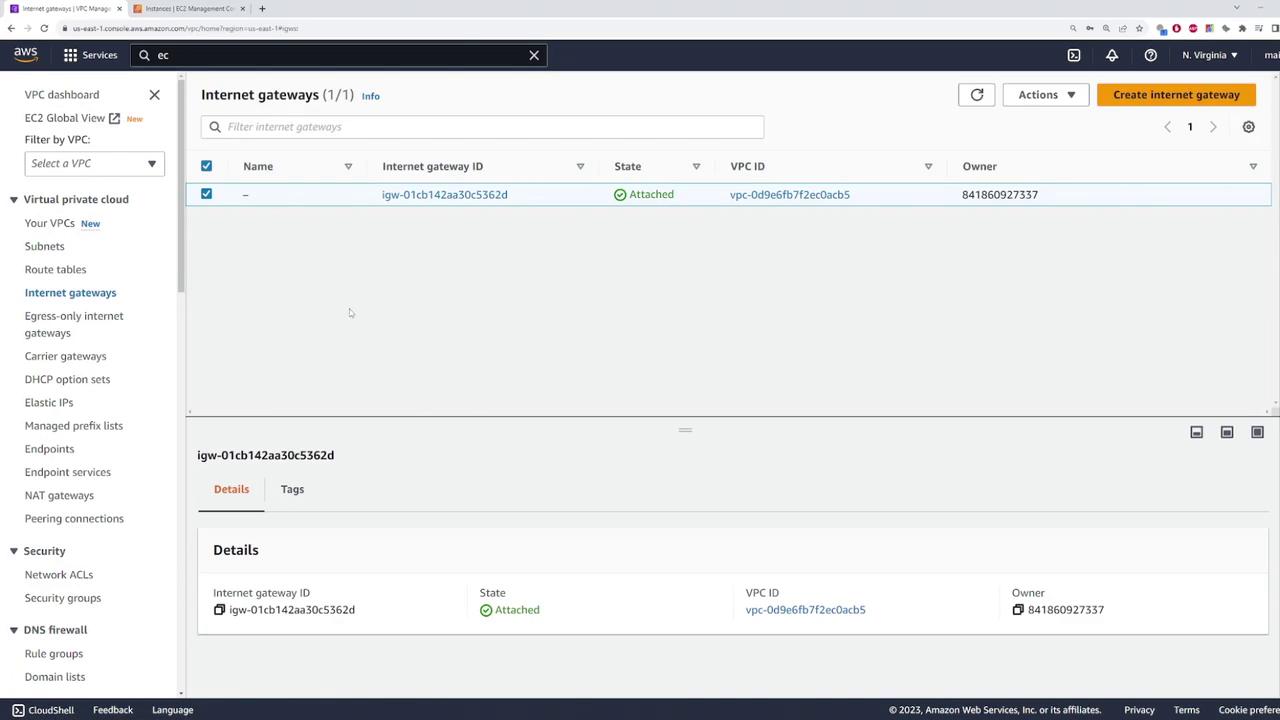
To enable internet access for the private instance via a NAT gateway, start by attaching an internet gateway to your VPC. Follow these steps:
- Create an internet gateway.
- Attach the internet gateway to your VPC.
Next, create a public subnet by specifying the CIDR block 10.0.2.0/24. The availability zone selection is arbitrary for this demo.
With both subnets in place, create two route tables:
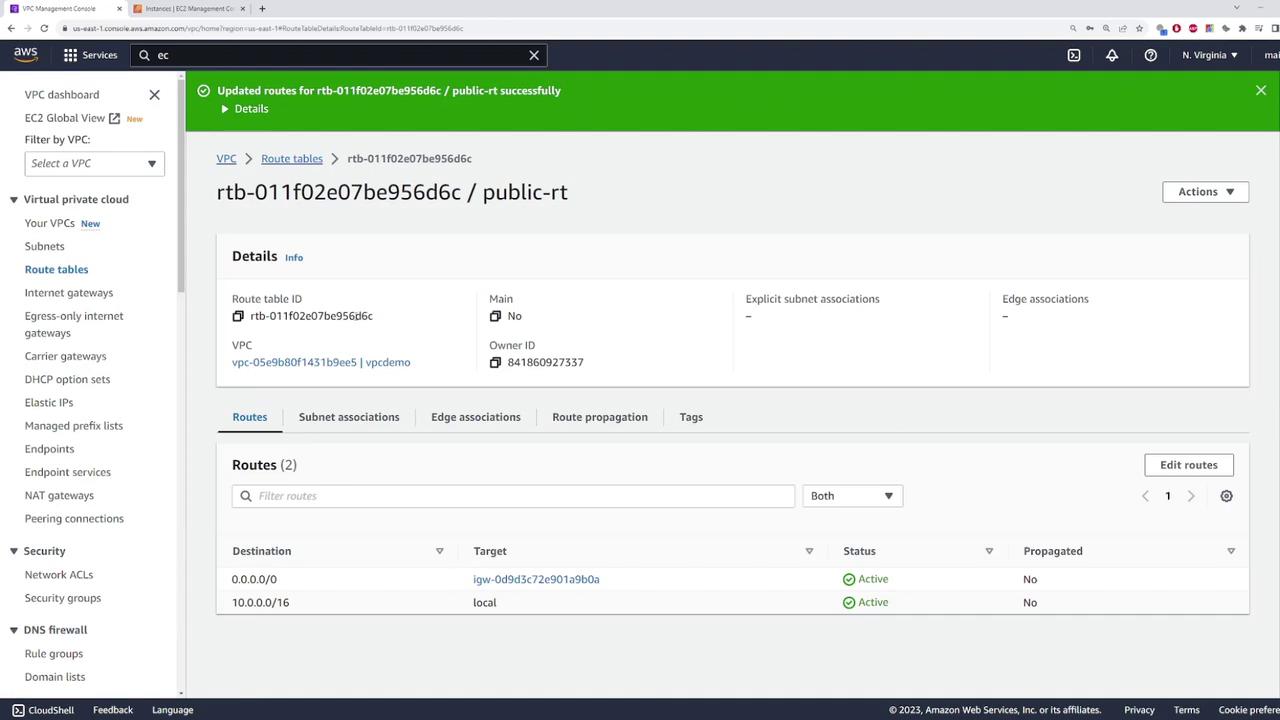
Public Route Table:
- Associate this route table with the VPC.
- Add a default route (0.0.0.0/0) pointing to the internet gateway.
- Associate the public route table with the public subnet.
Private Route Table:
- This route table will later include a default route that points to the NAT gateway.
- Associate this route table with the private subnet.
Step 4: Deploy the NAT Gateway
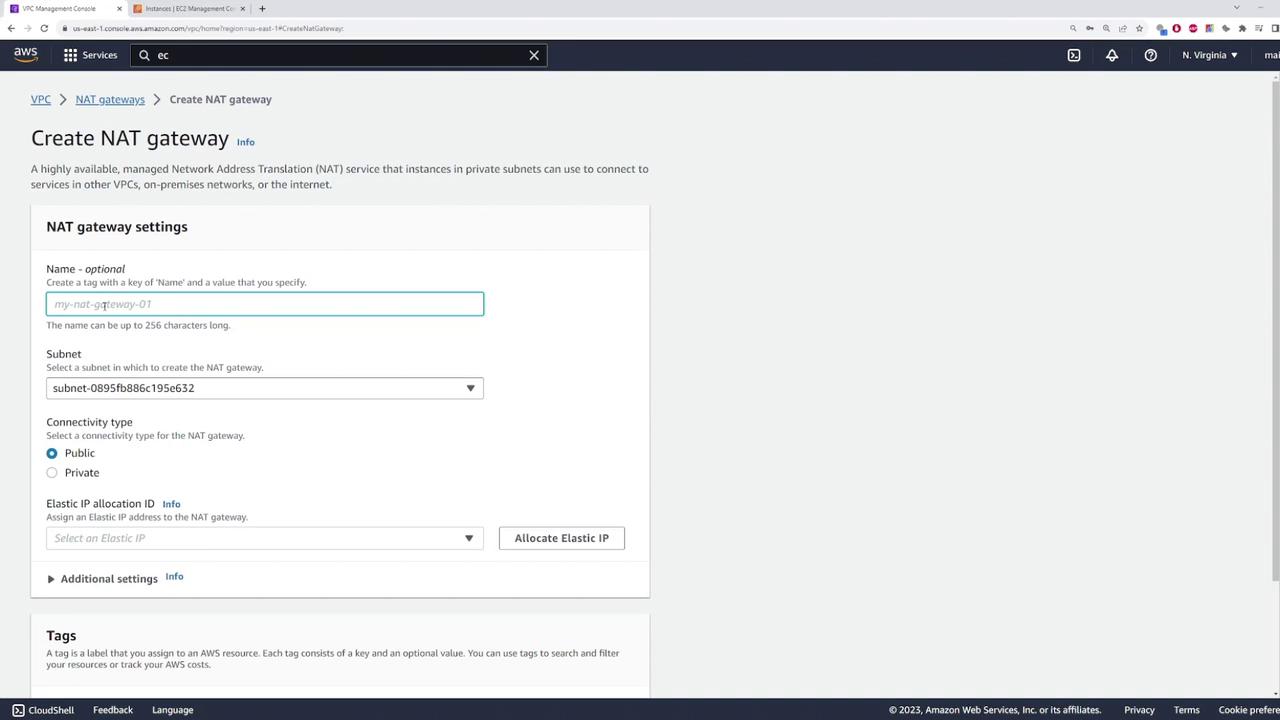
Deploy a NAT gateway in the public subnet by following these steps:
- Create a NAT gateway in the public subnet.
- Assign a name to the NAT gateway.
- Allocate an Elastic IP to ensure the gateway has a fixed public IP address.
After deploying the NAT gateway, update the private route table by adding a default route that points to the NAT gateway. Save these changes to complete the routing configuration for the private subnet.
Note
It is normal for the NAT gateway to show a pending status during initial setup—this indicates that the gateway is initializing.
Considerations for High Availability
NAT gateways are deployed within a specific subnet and are only resilient within their respective availability zones. For example, if a NAT gateway is deployed in us-east-1b and that availability zone experiences an outage, instances relying on that gateway will lose internet connectivity. In production environments, deploy multiple NAT gateways across different availability zones (e.g., us-east-1a, us-east-1b) and update your route tables accordingly to ensure redundancy and high availability.
For this demo, only a single NAT gateway is used, so high availability configuration is not implemented.
Conclusion
This demo has shown how to set up a secure environment in AWS using a NAT gateway. By following these steps, you can enable internet access for private EC2 instances while maintaining a secure network architecture. For more detailed information on AWS networking and NAT gateways, refer to the AWS Documentation.
Happy configuring!
Watch Video
Watch video content