Overview of Firewalls
Consider a web server listening on port 443 (HTTPS). When a client sends a request, the firewall controls the flow of data by applying a set of predefined inbound (incoming traffic) and outbound (outgoing traffic) rules. There are two primary types of firewalls:-
Stateless Firewalls:
Evaluate each packet individually. Rules must be configured for both inbound and outbound traffic as there is no tracking of connection states. -
Stateful Firewalls:
Monitor active connections. When an inbound request is allowed, the corresponding outbound response is automatically permitted without the need for an explicit rule.
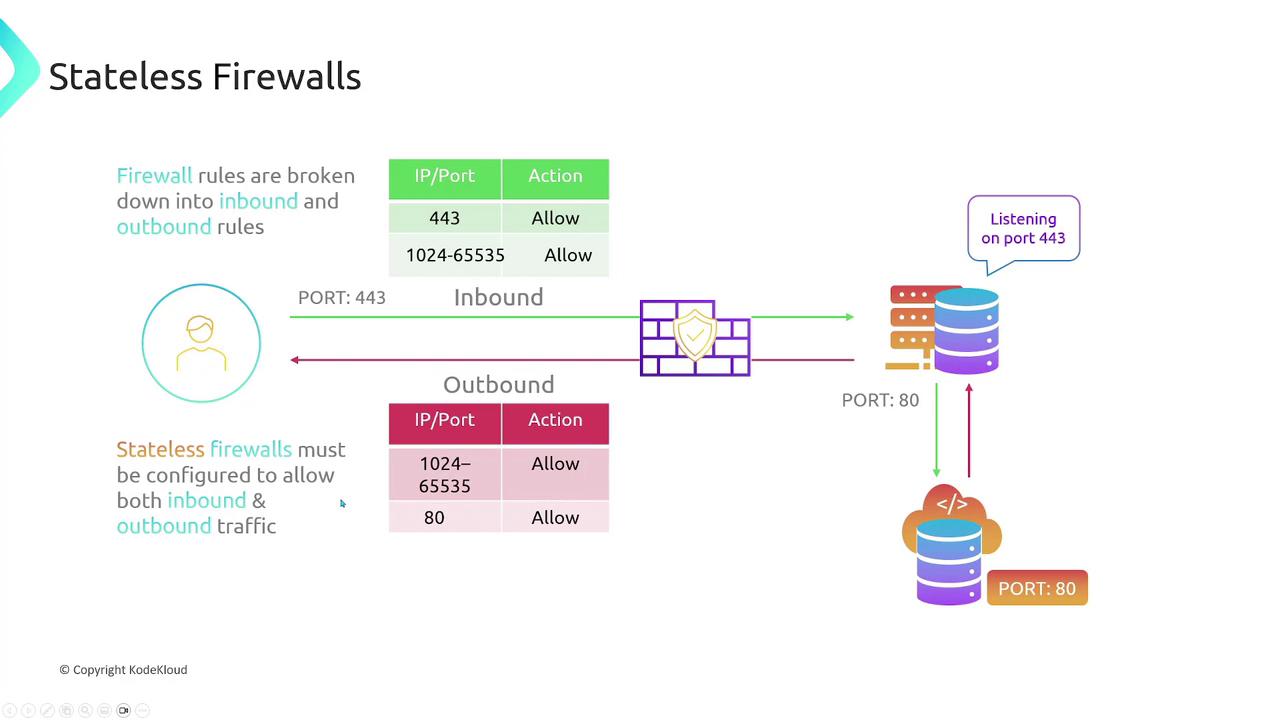
Configuring a Stateless Firewall
For a stateless firewall, imagine your web server that listens on port 443. You must configure rules separately for both directions:-
Inbound Rules:
- Allow incoming traffic on port 443.
-
Outbound Rules:
- Allow outbound traffic to the ephemeral port range (typically 1024 to 65535) since client source ports fall within this range.
- Additionally, if the server initiates a connection (for example, pulling updates from a server via port 80), you need to allow outbound traffic on port 80 and specify corresponding inbound rules to accept responses on the ephemeral port range.
Stateless firewalls treat inbound and outbound traffic separately, requiring manual configuration for both sides.
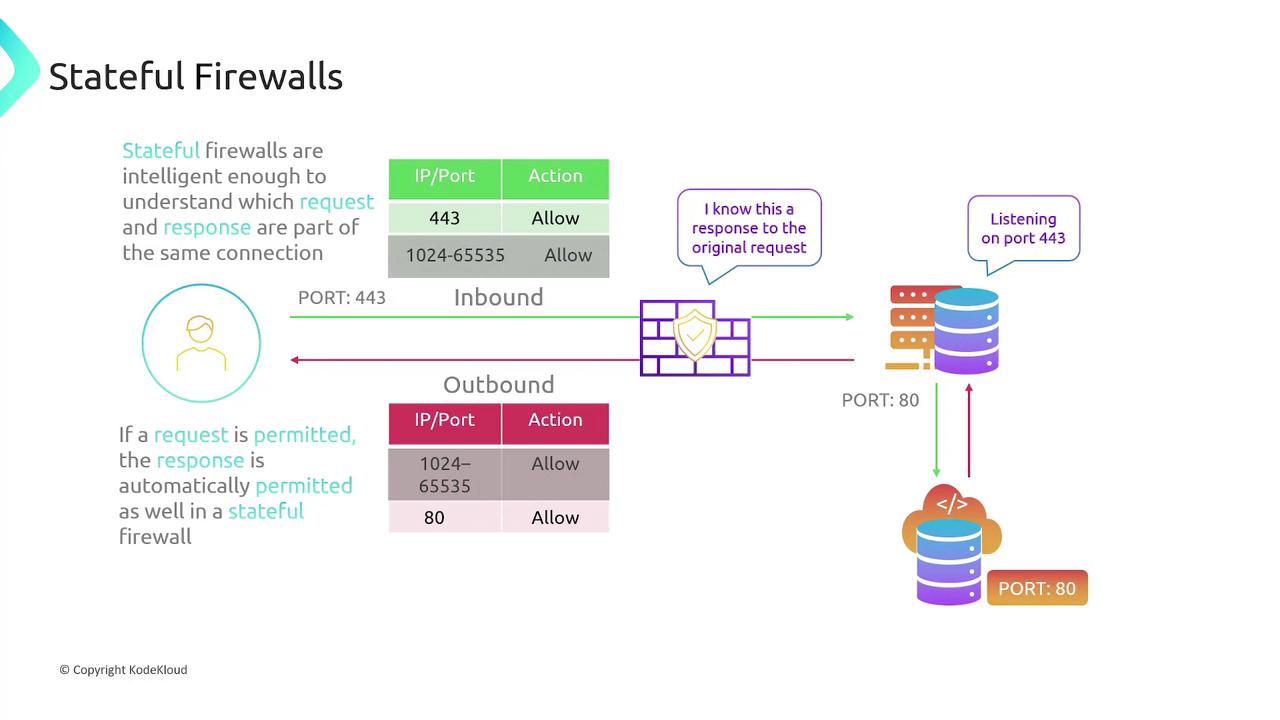
Configuring a Stateful Firewall
Using the same web server example for a stateful firewall, the configuration simplifies due to the system’s ability to track connections:-
Inbound Rules:
- Permit incoming traffic on port 443.
-
Outbound Rules:
- No explicit outbound rule is required for returning response traffic as the firewall automatically recognizes established connections.
- For additional outbound connections (e.g., connecting to port 80 on a different server), only the rule to allow the outbound request is required.
Stateful firewalls eliminate the need for duplicate rules by automatically permitting response traffic once a valid connection is established.
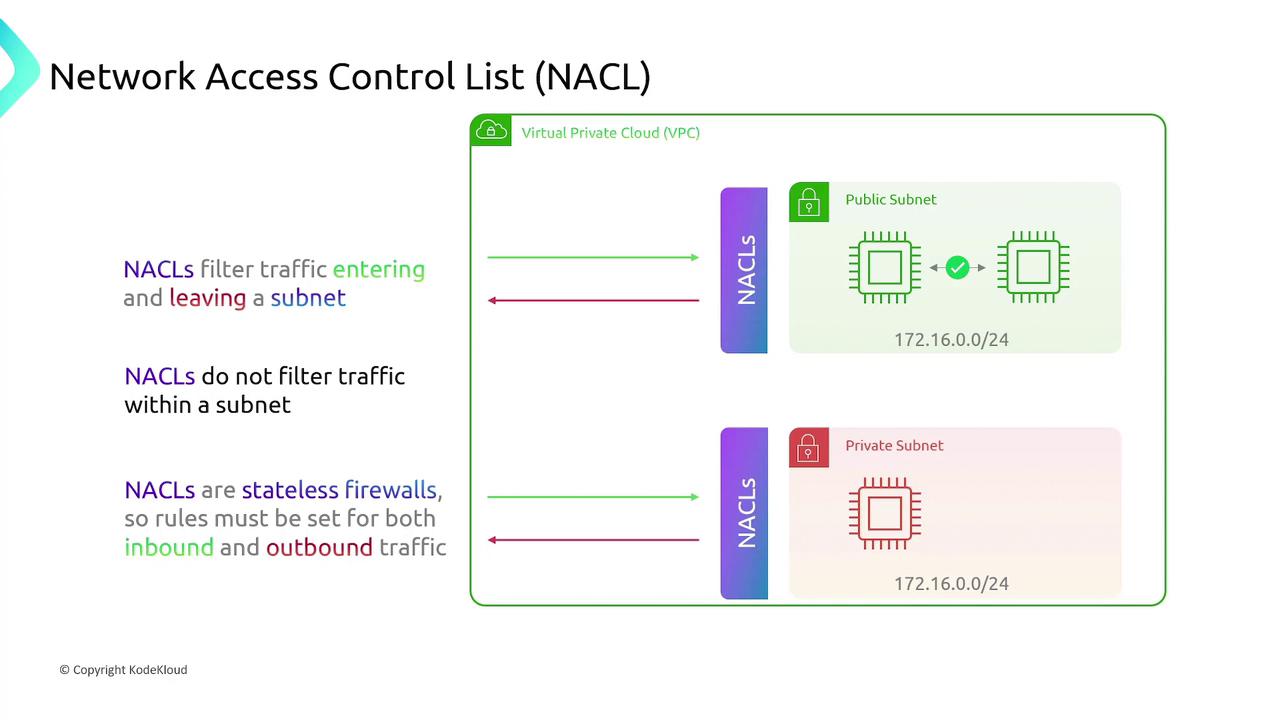
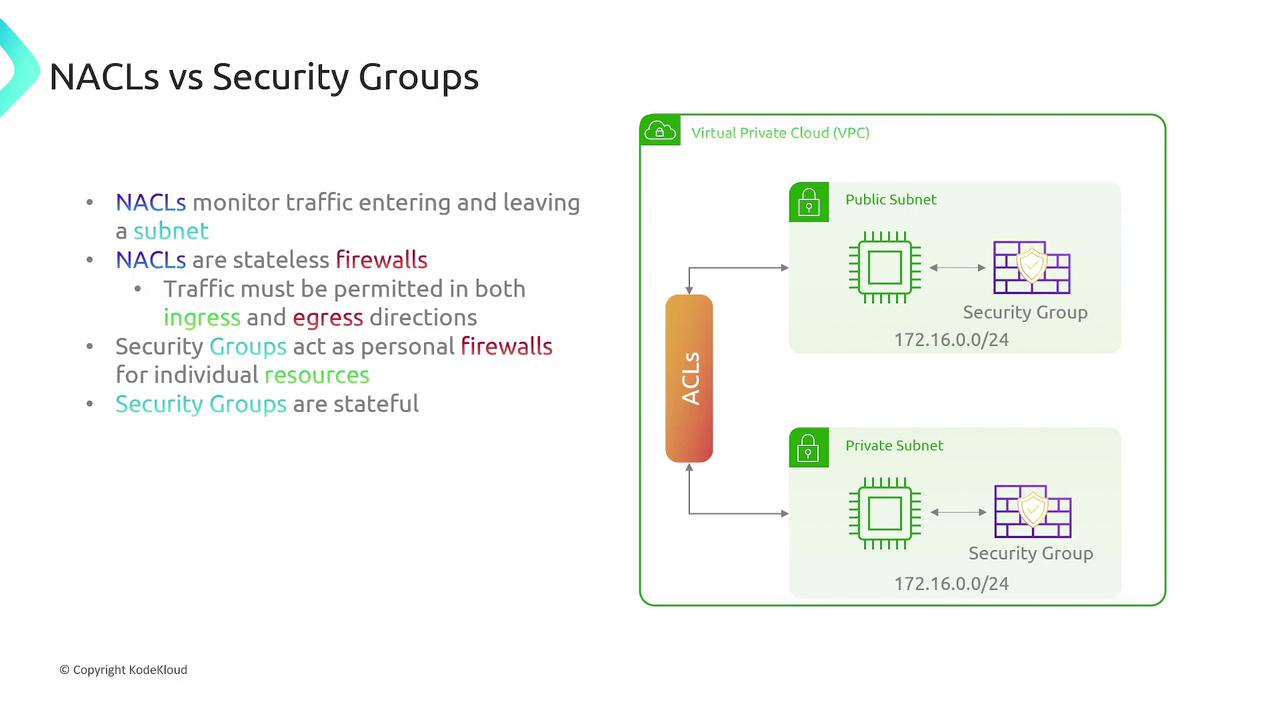
AWS Network Access Control Lists (NACLs)
AWS NACLs provide subnet-level filtering in a Virtual Private Cloud (VPC):-
Subnet-Level Filtering:
NACLs are associated with subnets rather than individual resources. Resources within a subnet are subject to the NACL’s rules, while traffic between resources in the same subnet is not filtered. -
Stateless Nature:
Being stateless, NACLs require explicit rules for both inbound and outbound traffic.
AWS Security Groups
Security groups act as virtual firewalls for individual AWS resources, such as EC2 instances, load balancers, and RDS databases. They differ from NACLs in the following ways:-
Resource-Level Protection:
Security groups protect individual resources rather than an entire subnet. -
Stateful Behavior:
Only the initial inbound traffic (or outbound traffic) needs to be explicitly allowed since the return traffic is automatically permitted. -
Allow Rules Only:
Security groups only contain rules that allow traffic. There is no provision to create explicit deny rules; any traffic not expressly permitted is blocked.
Configuring Security Group Rules
When configuring security group rules in the AWS console, you will encounter separate sections for inbound and outbound traffic. Here’s a breakdown of the typical fields within a security group rule:-
Name:
A descriptive name that helps identify the rule. -
Rule ID:
A unique identifier for the rule. -
IP Version:
Indicates whether the rule applies to IPv4 or IPv6 traffic. -
Type, Protocol, and Port Range:
For example, selecting “HTTP” sets the rule to allow TCP traffic on port 80. -
Source/Destination:
Specifies the IP address or range permitted by the rule. For instance, 0.0.0.0/0 allows traffic from any IP, while specifying an IP like 1.1.1.1 restricts access. -
Description:
Provides an explanation of the rule’s purpose.
-
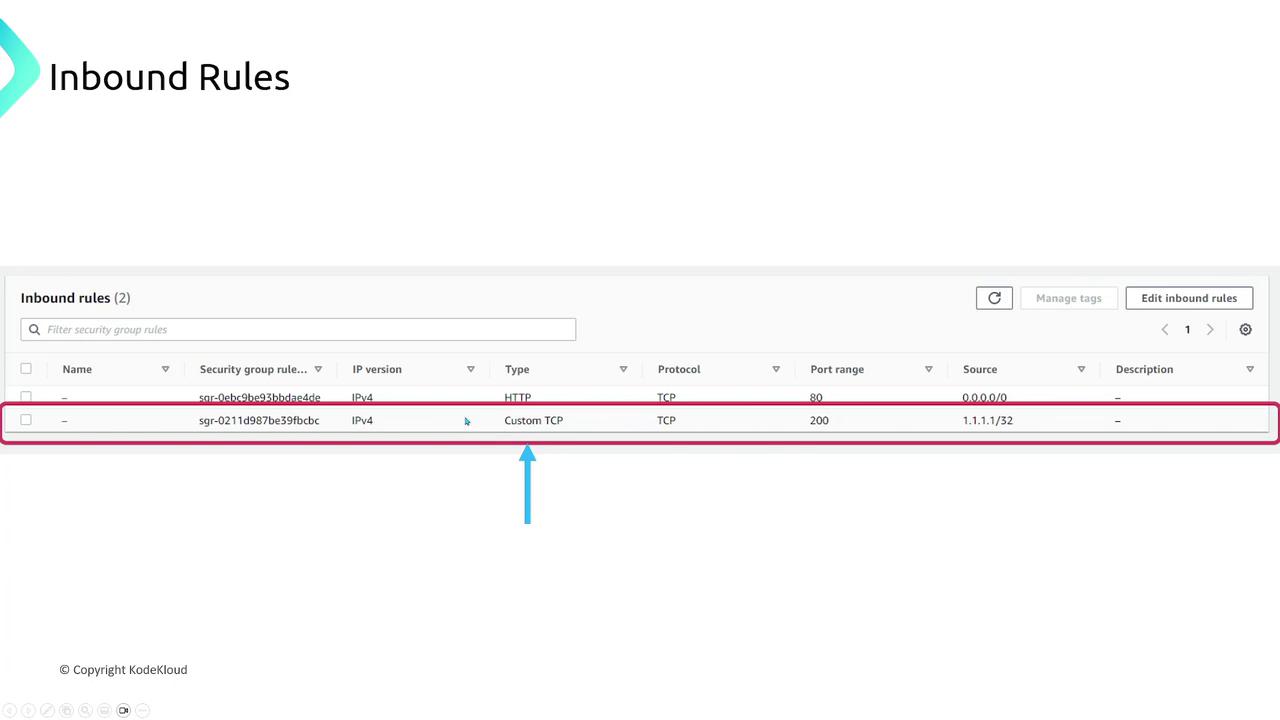
HTTP Traffic Rule:
Permits HTTP (TCP port 80) traffic from any IP address. -
Custom TCP Rule:
Configured as a “custom TCP” rule, it allows traffic on port 200 only from IP address 1.1.1.1. If a range (e.g., ports 200 through 300) is required, the rule can be configured accordingly.
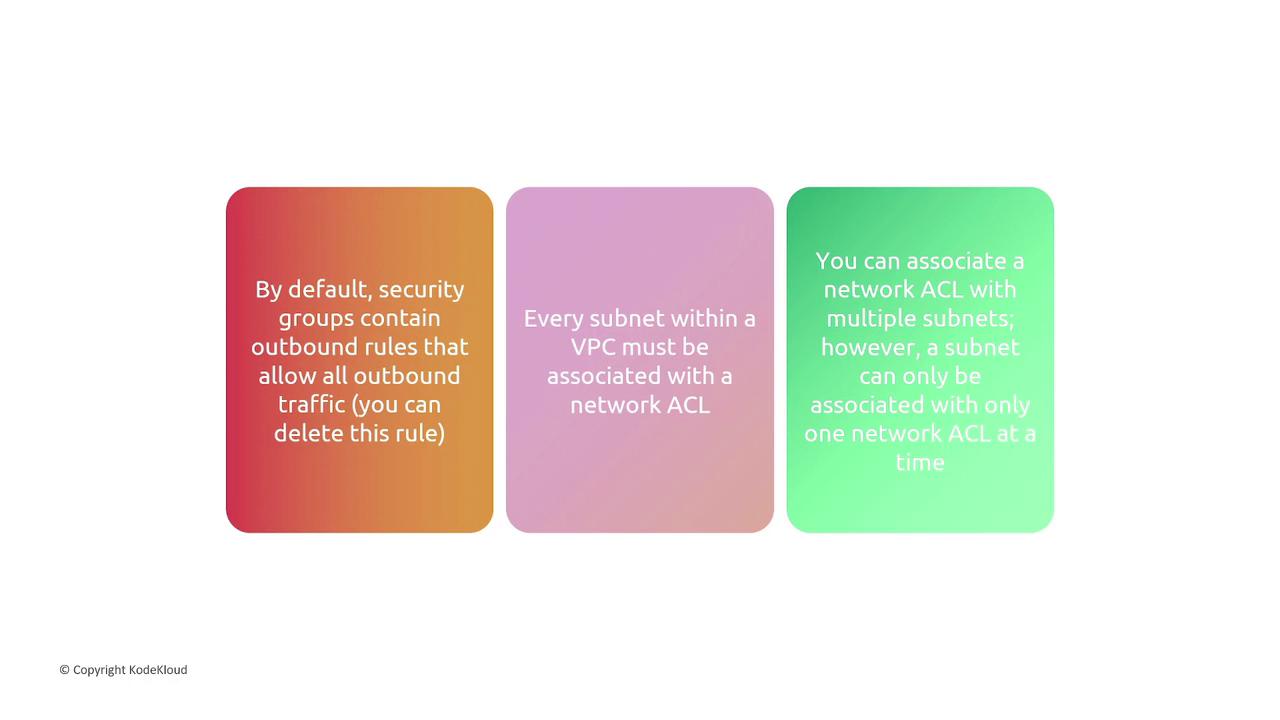
If no rules are defined, all traffic is blocked by default. Also, when multiple security groups are attached to a resource, their rules merge to form a consolidated security policy.
AWS Network ACL Rules
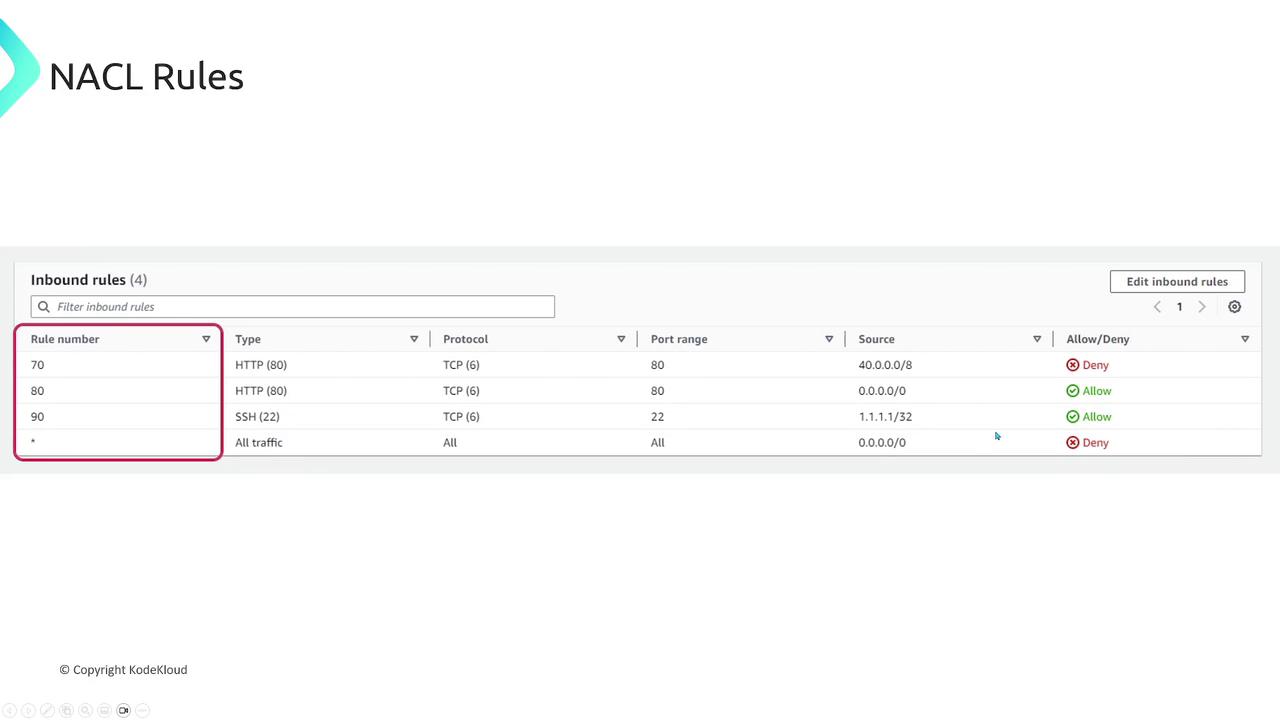
Unlike security groups, NACL rules offer greater control by allowing both allow and deny actions:-
Rule Order:
Each rule is assigned a number, and lower numbered rules are evaluated before higher ones. -
Allow and Deny Actions:
NACLs can explicitly allow or block traffic based on type, protocol, port range, and source address, offering granular control over subnet traffic.
Multiple Security Groups
AWS resources can be associated with multiple security groups simultaneously. When applying more than one security group (e.g., one for web access and another for management), their rules are merged. The final effective security policy is the combination of all allowed traffic flows from these groups.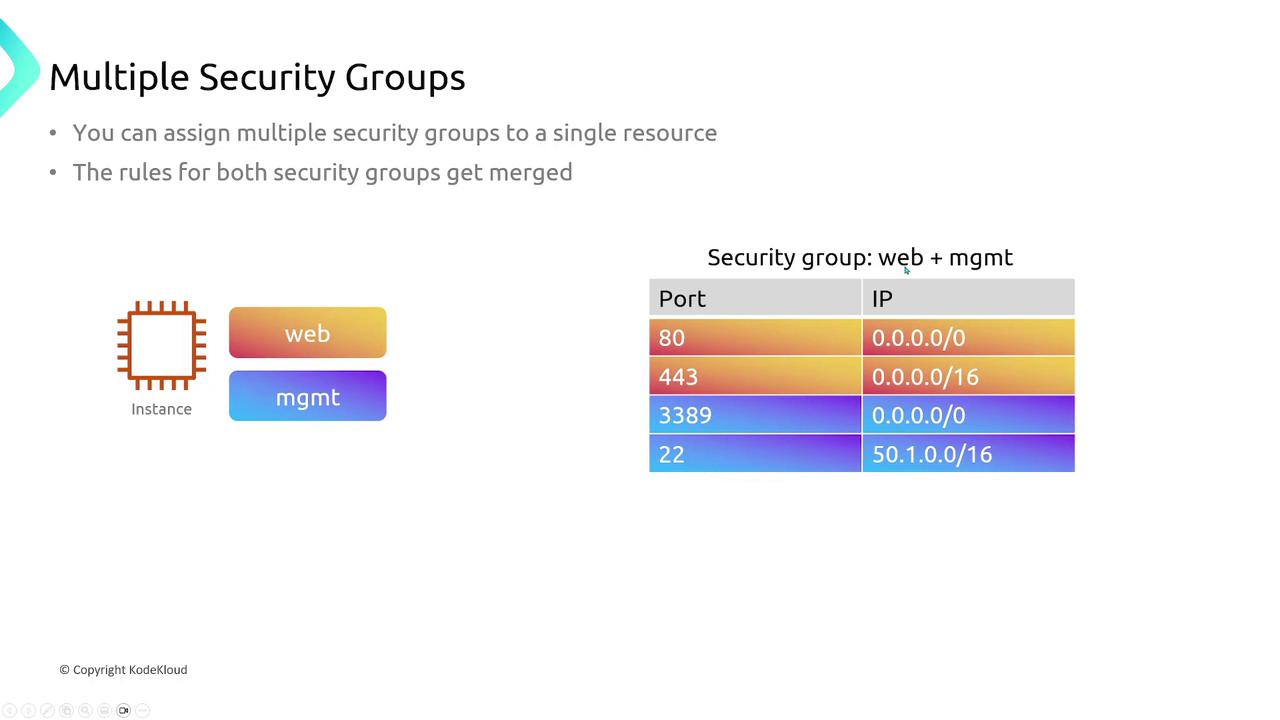
Final Notes on VPC and NACLs
- Every subnet in a Virtual Private Cloud (VPC) must be associated with a network ACL.
- A single network ACL can be linked to multiple subnets, but each subnet can only have one network ACL at a time.
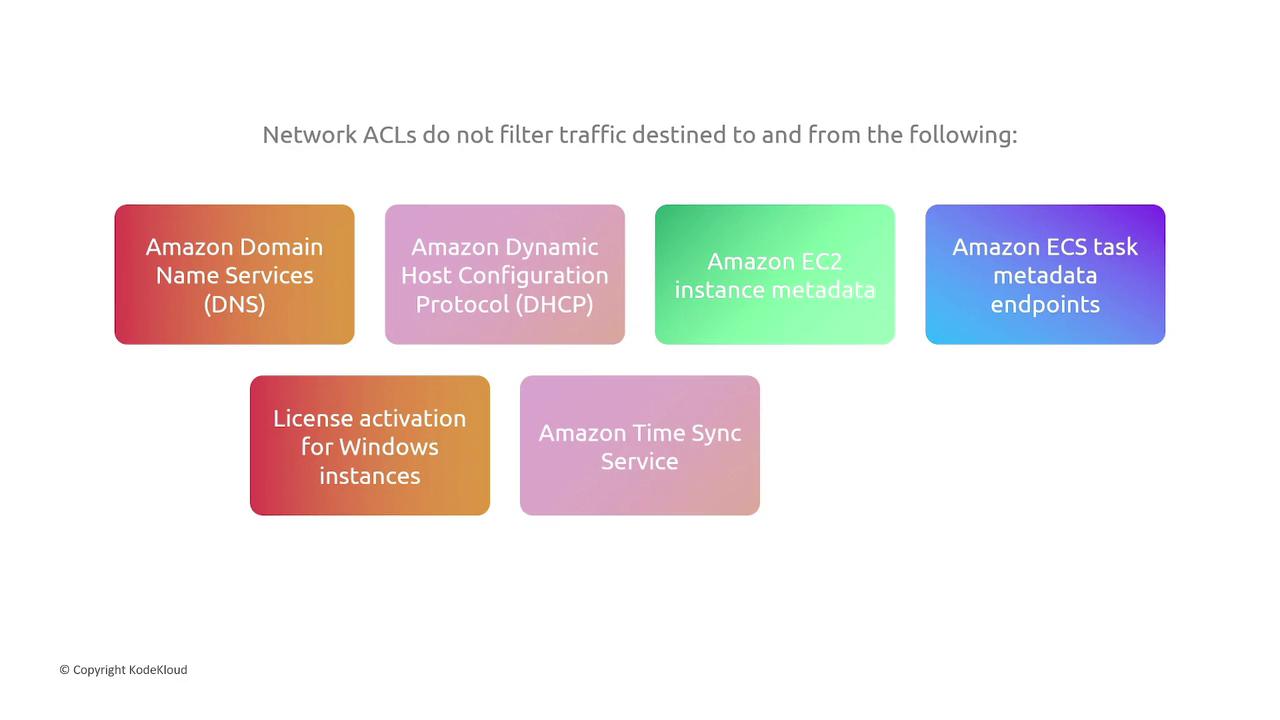
- Certain traffic types (such as communication with Amazon’s DNS, DHCP, EC2 instance metadata, Windows license activation, and time synchronization services) are exempt from NACL filtering.
Summary
-
Stateless Firewalls:
Require explicit configuration of both inbound and outbound traffic rules. -
Stateful Firewalls:
Automatically allow return traffic for approved connections, simplifying rule management. -
Network ACLs:
Function as stateless firewalls for subnets, allowing detailed allow/deny rules and processing rules in numeric order. -
Security Groups:
Provide stateful protection at the resource level, merging multiple groups’ rules to secure AWS resources like EC2 instances.