AWS Solutions Architect Associate Certification
Services Networking
VPN
In this article, we explore Virtual Private Networks (VPNs) and their integration with AWS, including their purpose, deployment, routing methods, pricing, and performance limits. You’ll also find architectural diagrams that clarify key components of VPN setups in AWS.
VPN Purpose and Use Case
Imagine you have an AWS Virtual Private Cloud (VPC) containing private subnets that host various resources without public IP addresses. These resources require secure connectivity to an on-premises data center. A VPN provides this secure link by establishing an encrypted IPsec tunnel between the two environments, ensuring that communication remains private and protected.
VPN Architecture in AWS
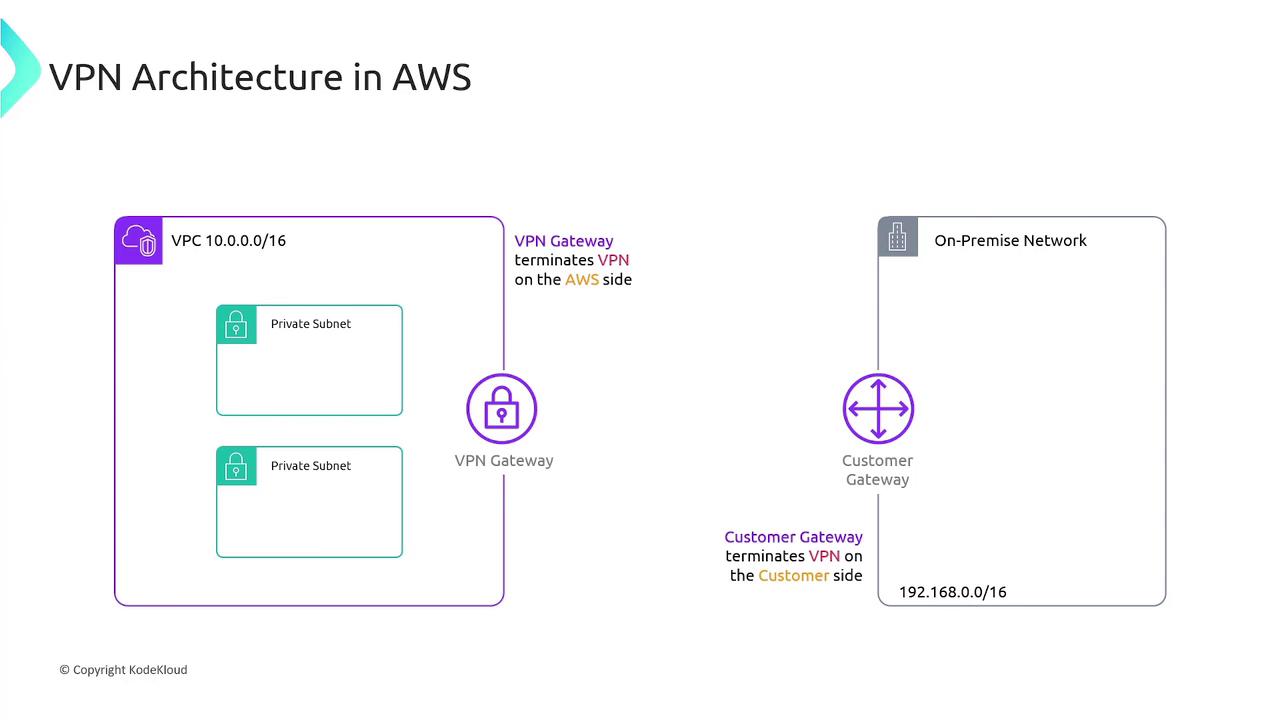
Consider a VPC with a CIDR block of 10.0.0.0/16 where your resources are hosted in private subnets. To connect to an on-premises data center (for example, using 192.168.0.0/16), two critical components are involved:
- VPN Gateway (VGW): Located on the AWS side, it terminates the VPN connection.
- Customer Gateway (CGW): Located on your on-premises network, it terminates the VPN connection on the customer side and possesses a public IP address.
For instance, if the Customer Gateway is assigned the public IP 1.1.1.1 and the VPN Gateway uses 2.2.2.2, an IPsec tunnel is established over the internet between these endpoints.
In this setup, the Customer Gateway represents your on-premises side, while the VPN Gateway is deployed on the AWS side.
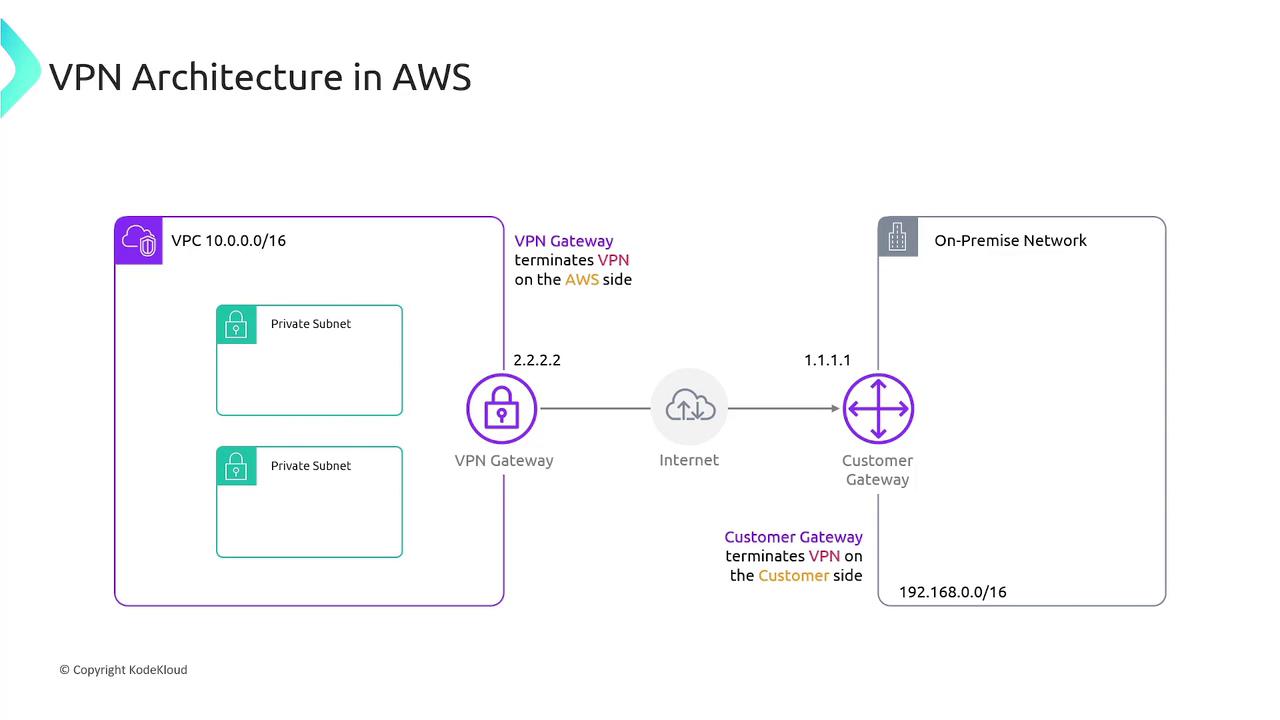
The encrypted IPsec tunnel ensures that all data transmitted across the public internet remains secure.
Routing Between AWS and On-Premises Networks
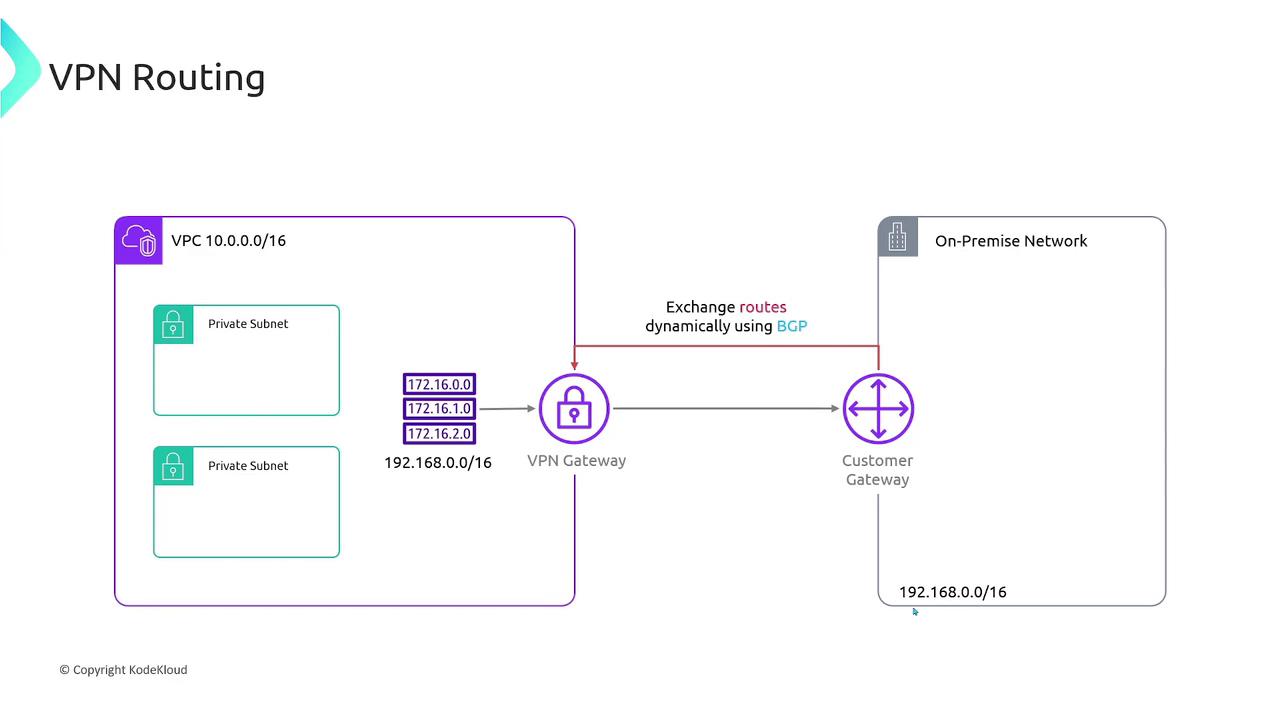
To facilitate communication between the on-premises network (192.168.0.0/16) and the AWS VPC (10.0.0.0/16), you must configure routing appropriately. Packets destined for the on-premises network should be directed through the VPN Gateway. There are two routing approaches:
- Static Routing: Manually add a route in the VPC routing table that directs traffic for 192.168.0.0/16 to the VPN Gateway.
- Dynamic Routing: Use a routing protocol like Border Gateway Protocol (BGP) to automatically exchange routes between the VPN Gateway and the Customer Gateway. This dynamic method allows AWS to learn the on-premises routes automatically.
Note
Using dynamic routing with BGP simplifies route management and provides improved resiliency by automatically adapting to route changes.
VPN Pricing
AWS charges for VPN gateways in two main ways:
- A fee for each hour that the VPN connection is available.
- Additional charges for data transfer out (egress traffic) from Amazon EC2 over the VPN.
Warning
Monitor your outbound data transfer closely to manage costs, as VPN egress charges can accumulate quickly.
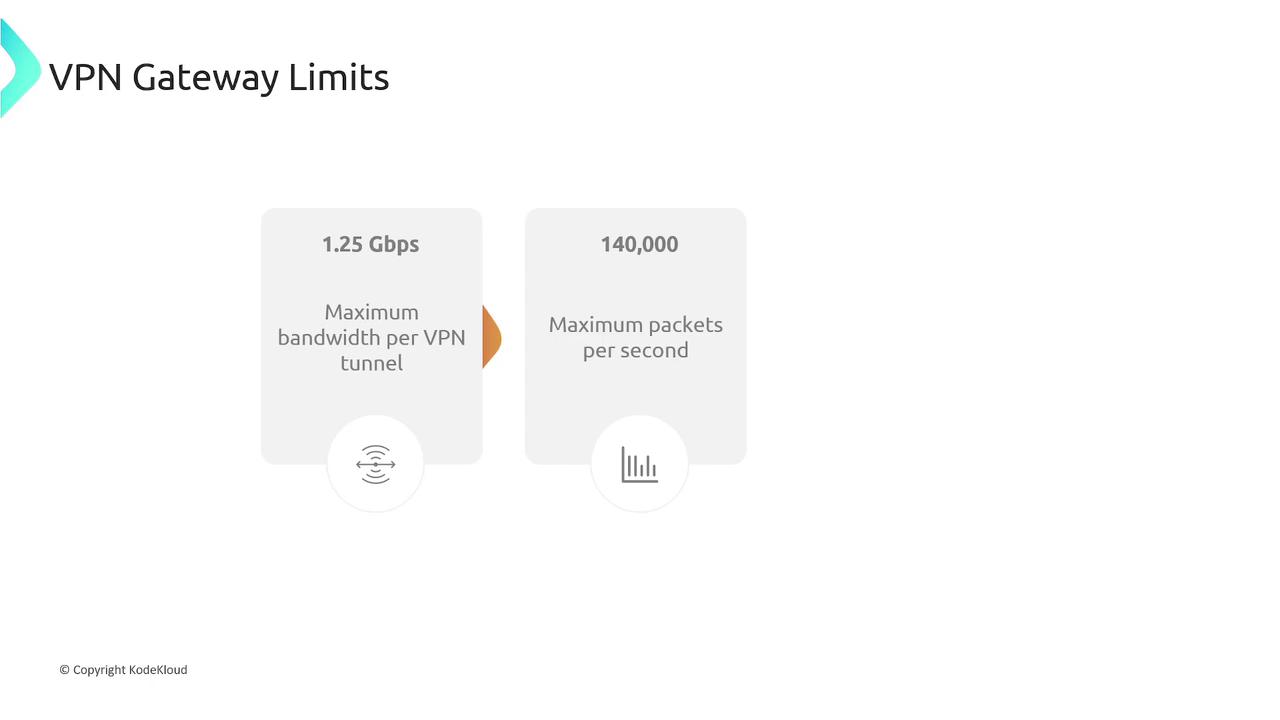
VPN Performance Limits
When deploying VPN gateways, consider these performance limits:
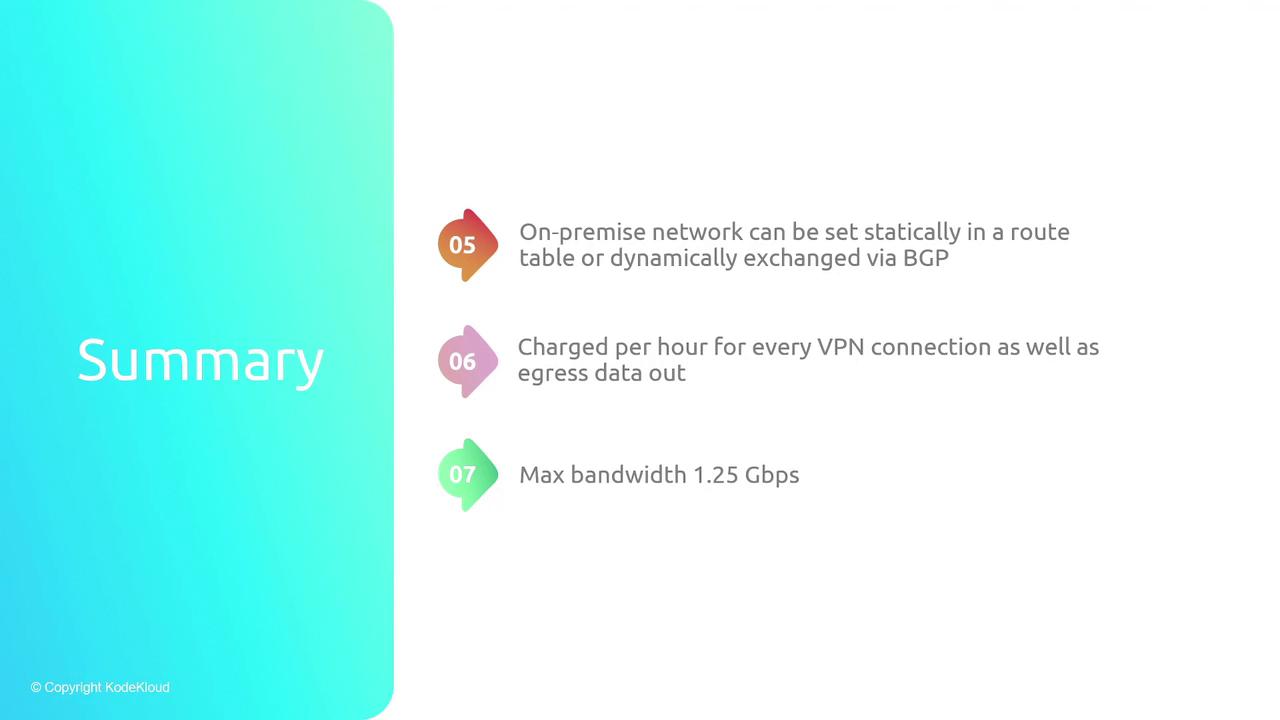
- Bandwidth: Up to 1.25 Gbps per VPN tunnel.
- Packets Per Second: Capable of handling up to 140,000 packets per second.
- MTU (Maximum Transmission Unit): Limited to 1,466 bytes.
If a single tunnel does not satisfy performance requirements, utilize Equal-Cost Multi-Path (ECMP) routing by establishing additional VPN tunnels to distribute the traffic load.
Summary
To summarize:
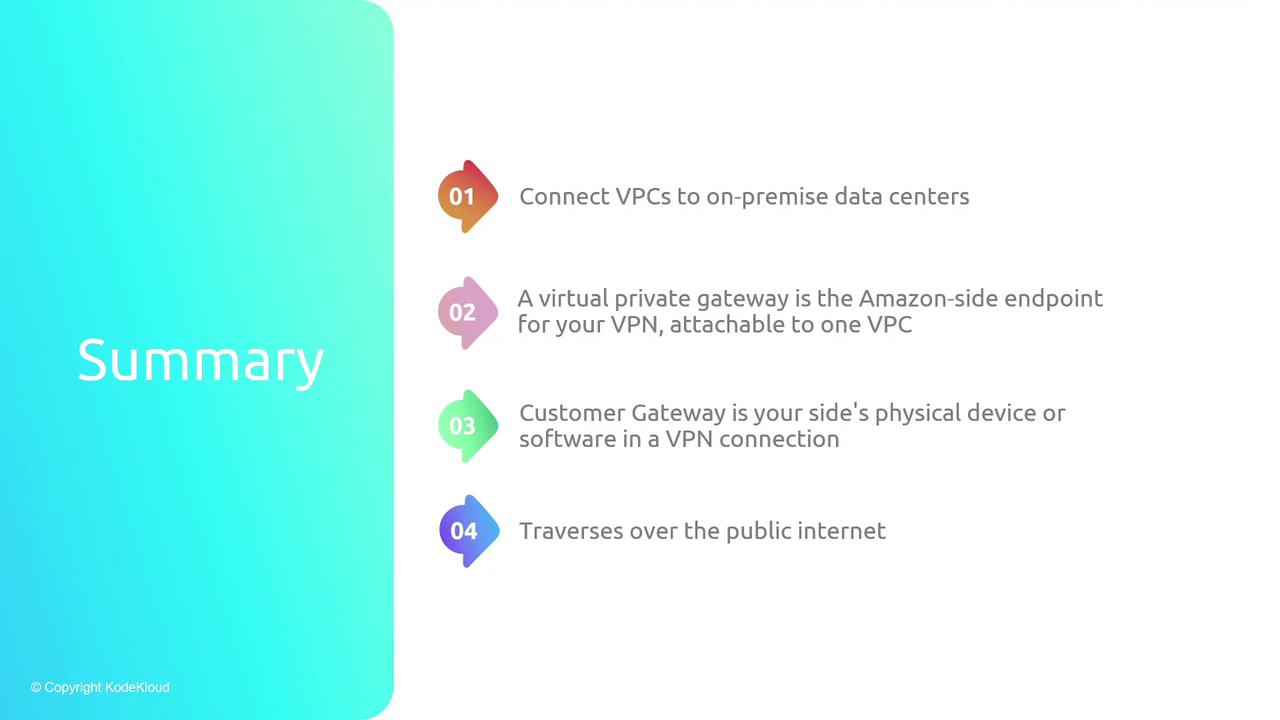
- VPNs provide secure connectivity between AWS VPCs and on-premises data centers.
- The VPN Gateway (AWS side) and Customer Gateway (on-premises side) serve as the endpoints for the encrypted IPsec tunnel.
- Routing can be managed either statically or dynamically using BGP to ensure proper packet flow.
- AWS charges for VPN usage based on connection uptime and data egress, and VPN tunnels have defined performance limits.
For further reading, consider exploring the AWS VPN Documentation and general VPN Concepts.
Watch Video
Watch video content