AWS Solutions Architect Associate Certification
Services Security
CloudTrail
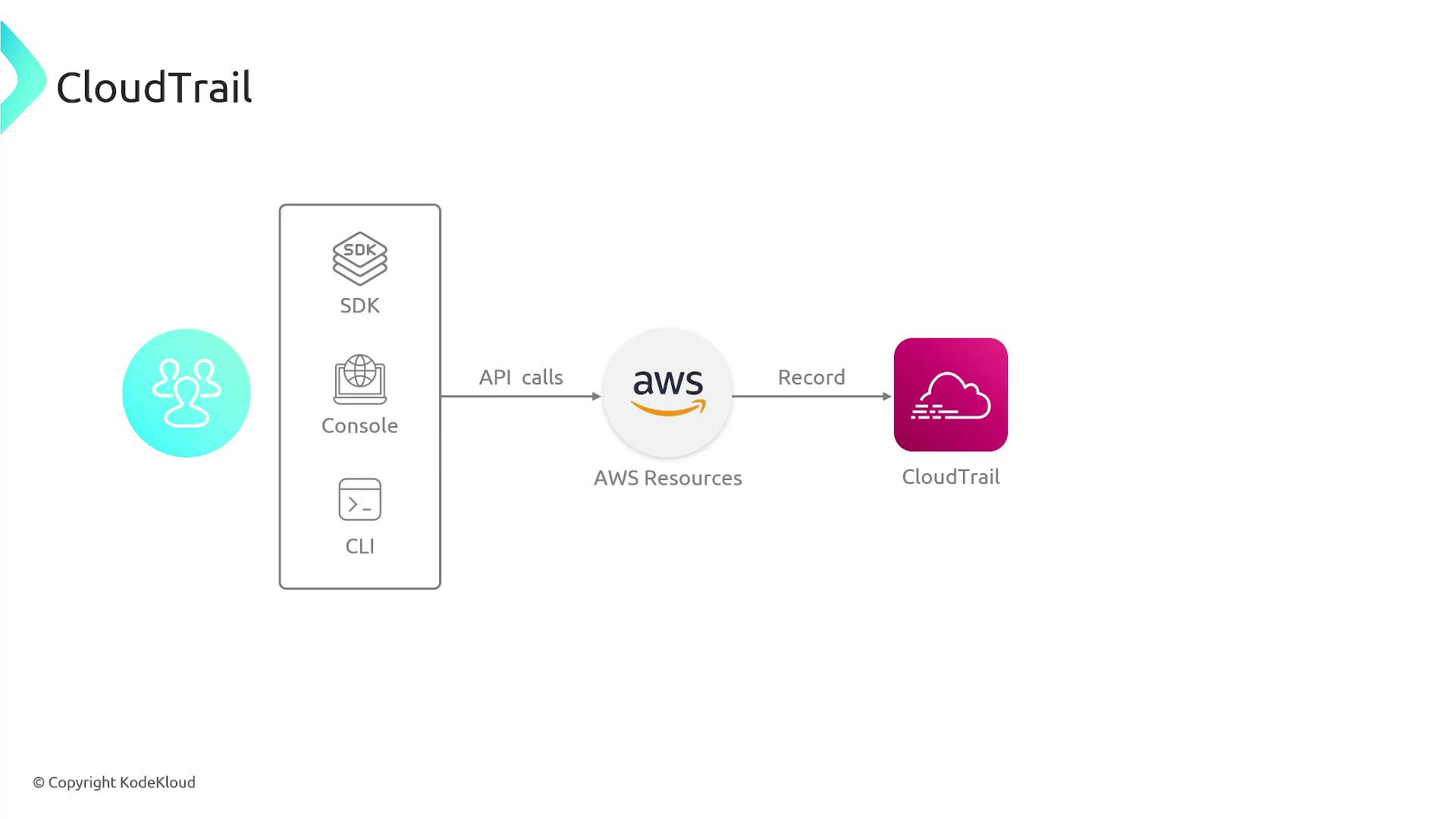
AWS CloudTrail is an essential service that records every API call made within your AWS account. Acting as a comprehensive audit trail, CloudTrail logs details such as the caller's identity, the action performed, and the event timestamp. It covers API calls initiated via the SDK, AWS Management Console, or CLI, ensuring that every interaction with AWS services is thoroughly documented.
Log Retention and Analysis
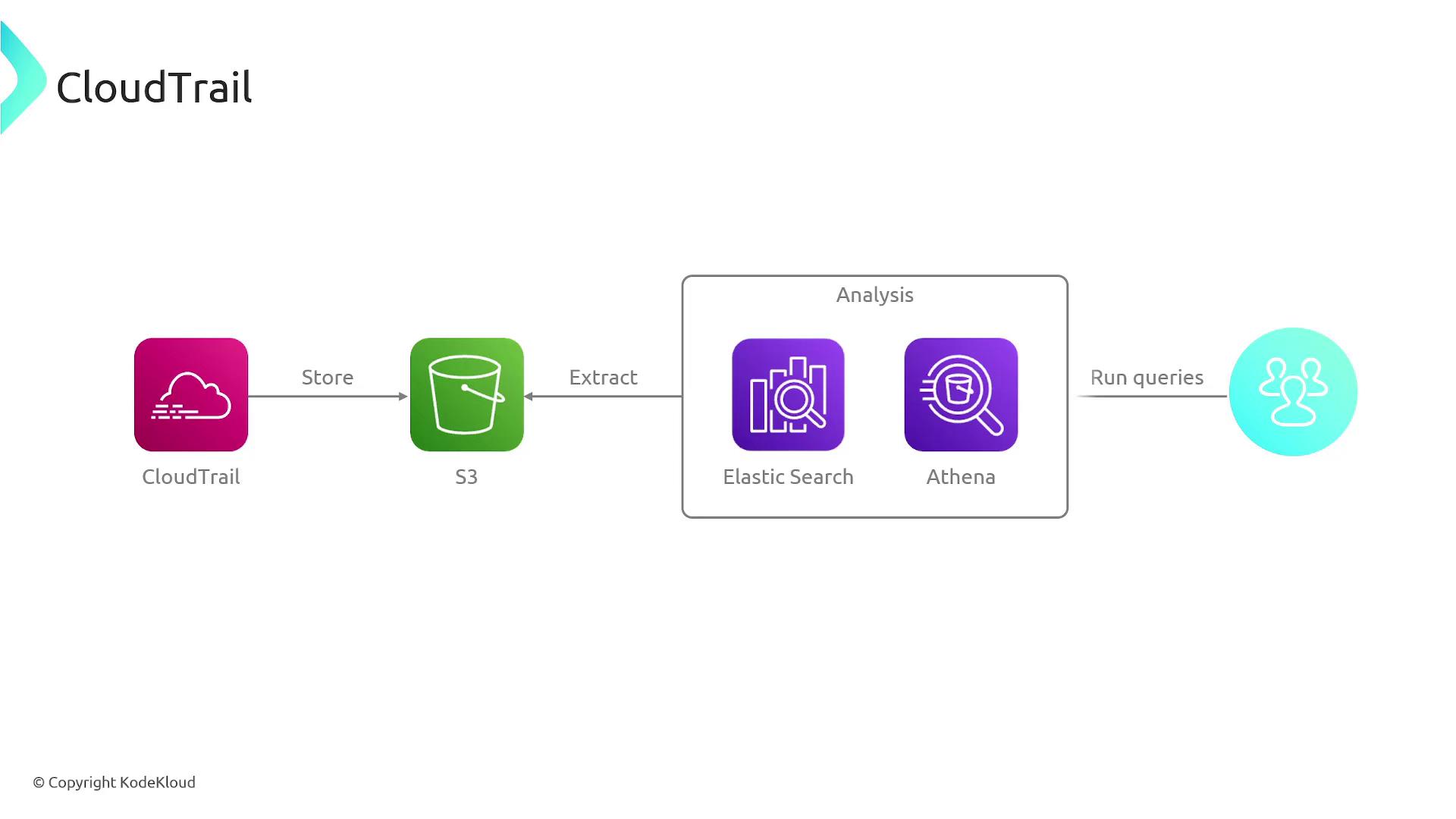
By default, CloudTrail stores event logs for 90 days. If you require a longer retention period, you can configure CloudTrail to deliver logs to an Amazon S3 bucket. Once logs are in S3, you have the flexibility to analyze them further using services like OpenSearch and Athena for enhanced querying and insights.
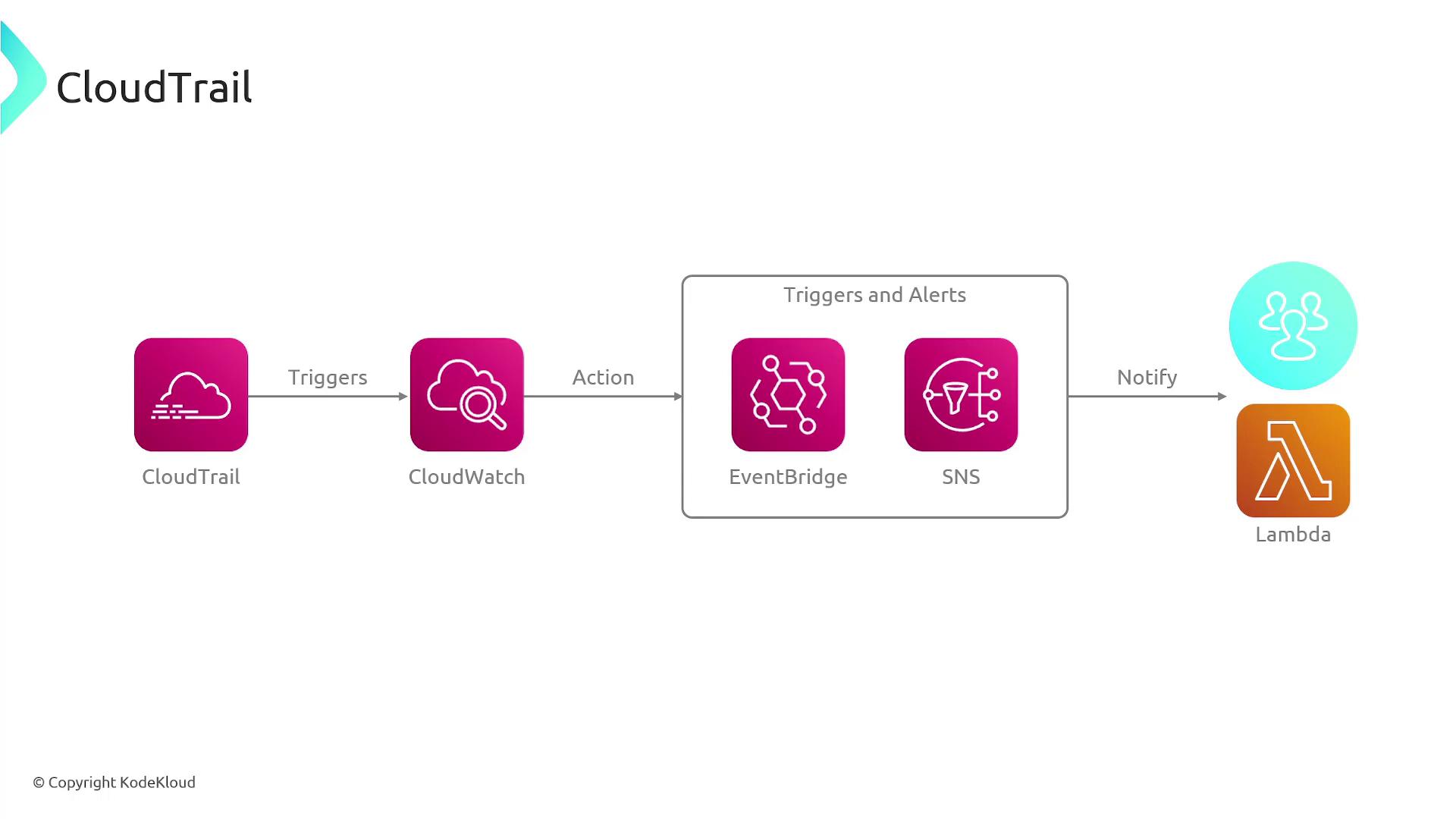
Real-Time Monitoring with AWS CloudWatch
AWS CloudTrail logs can be ingested in real time by AWS CloudWatch. This integration allows you to:
- Create alarms based on specific events or log patterns.
- Trigger notifications through Amazon SNS when defined thresholds are met.
For instance, establishing an SNS topic can alert your operations team immediately if a CloudTrail event indicates a potential security breach.
Tip
Consider integrating CloudWatch alarms with automated notifications to ensure prompt response to security events.
Automated Responses with AWS Lambda
You can further enhance your security posture by setting up AWS Lambda functions to perform custom actions in response to specific CloudWatch alarms. For example, a Lambda function can automatically disable a compromised AWS resource when a security-related CloudTrail event is detected.
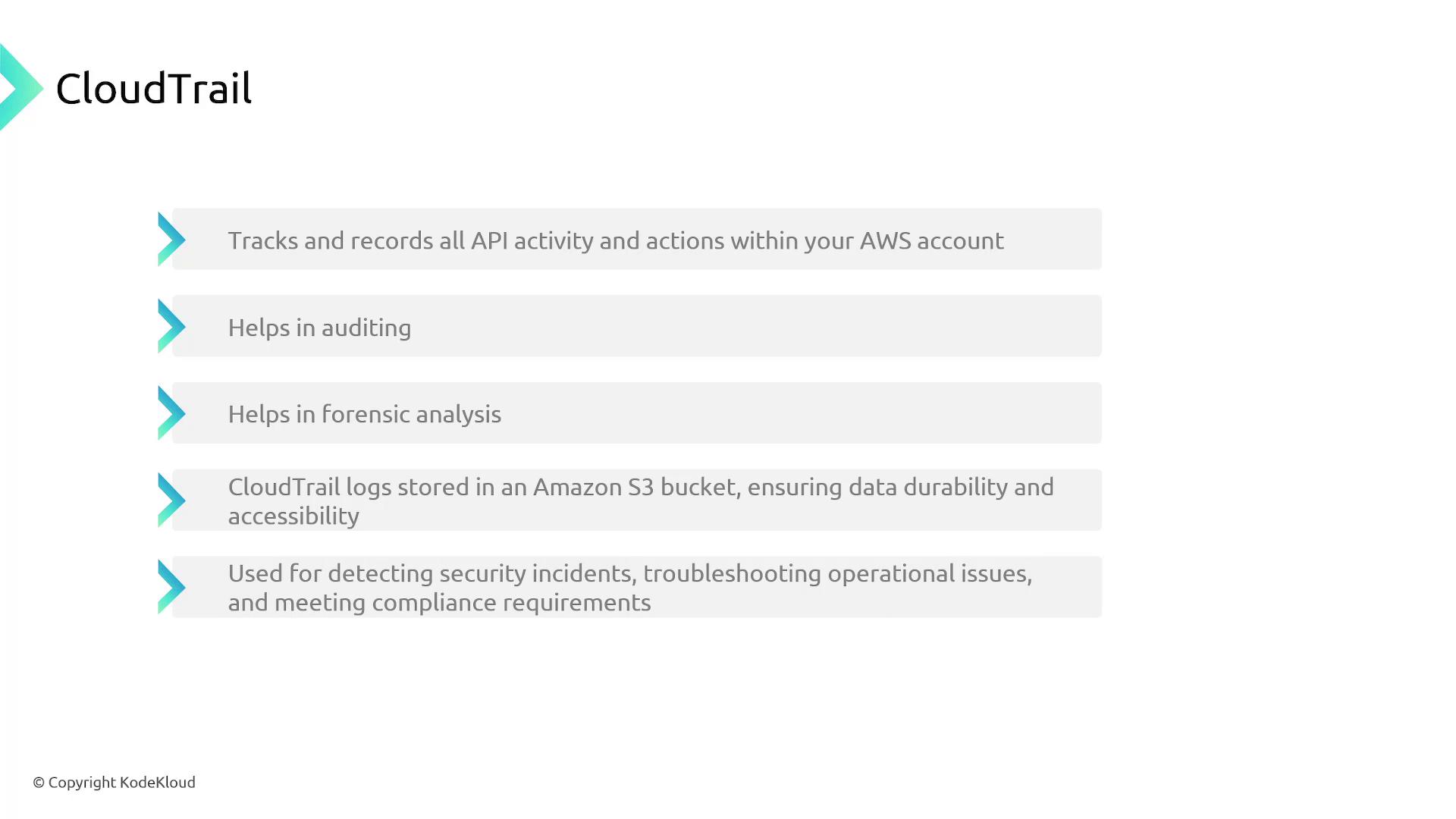
Benefits of AWS CloudTrail
AWS CloudTrail is critical for maintaining robust security, compliance, and operational troubleshooting. Its capabilities include:
- Monitoring API activity across all AWS services.
- Conducting thorough security audits.
- Performing detailed forensic analysis.
- Supporting compliance requirements with extended log retention in Amazon S3.
Security Advisory
Always ensure your log data is securely stored and access to these logs is tightly controlled to prevent unauthorized access.
Watch Video
Watch video content