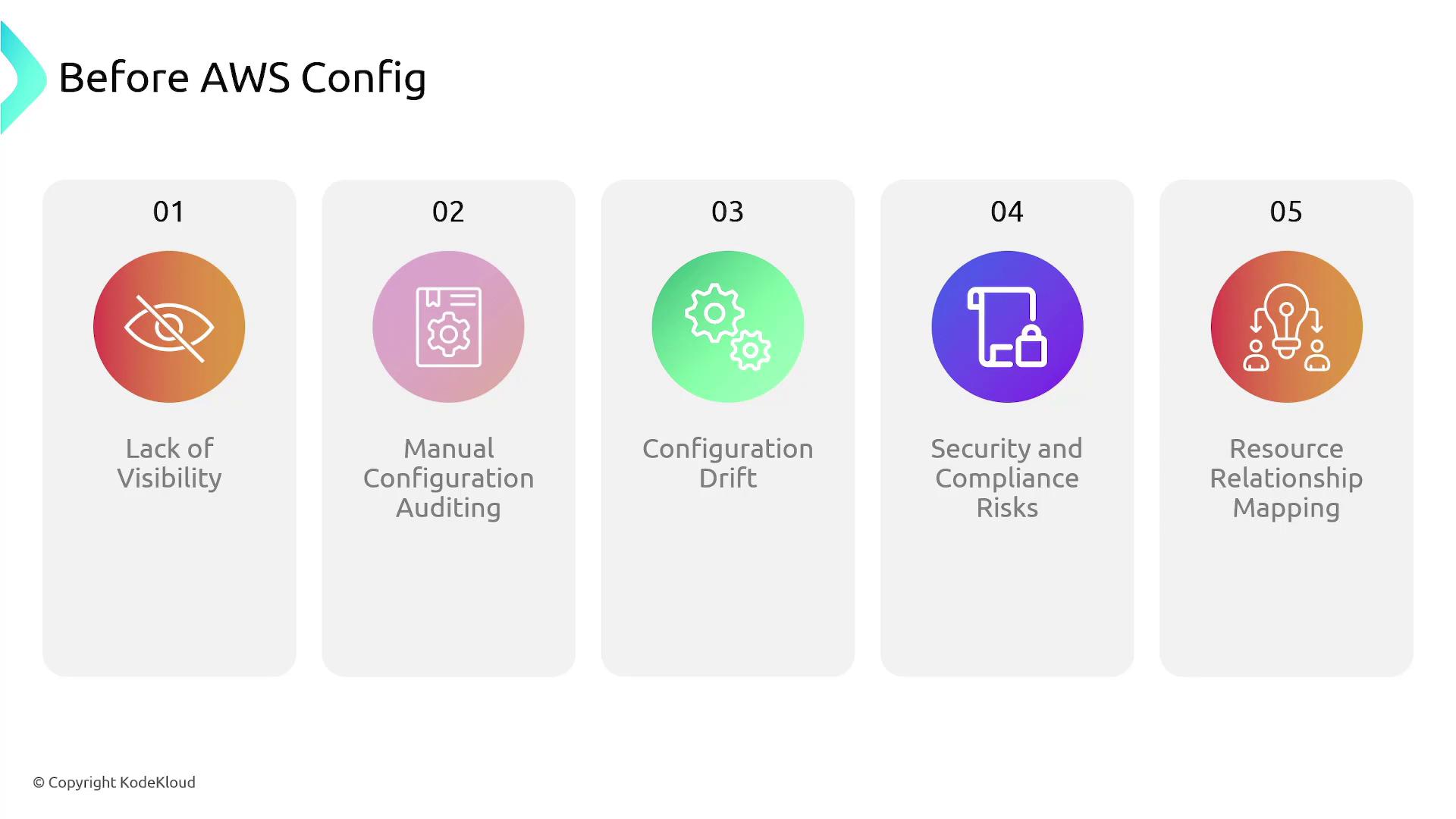
- Lack of complete visibility into resource configurations.
- Time-consuming, error-prone manual audits or reliance on ad hoc scripts.
- Configuration drift where resources deviated from their intended state.
- Increased security and compliance risks due to misconfigured resources.
- Difficulty understanding dependencies and relationships between resources.
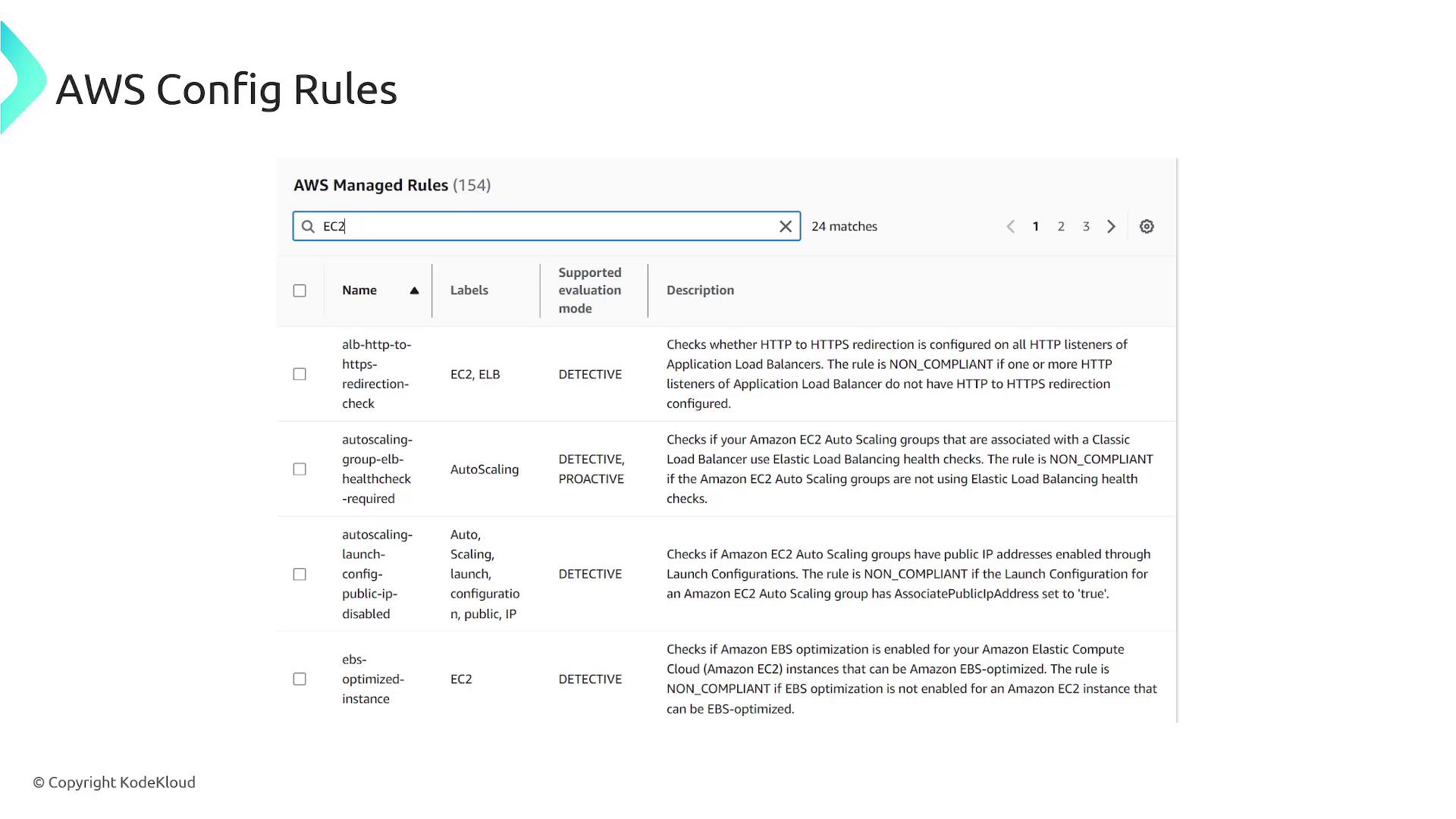
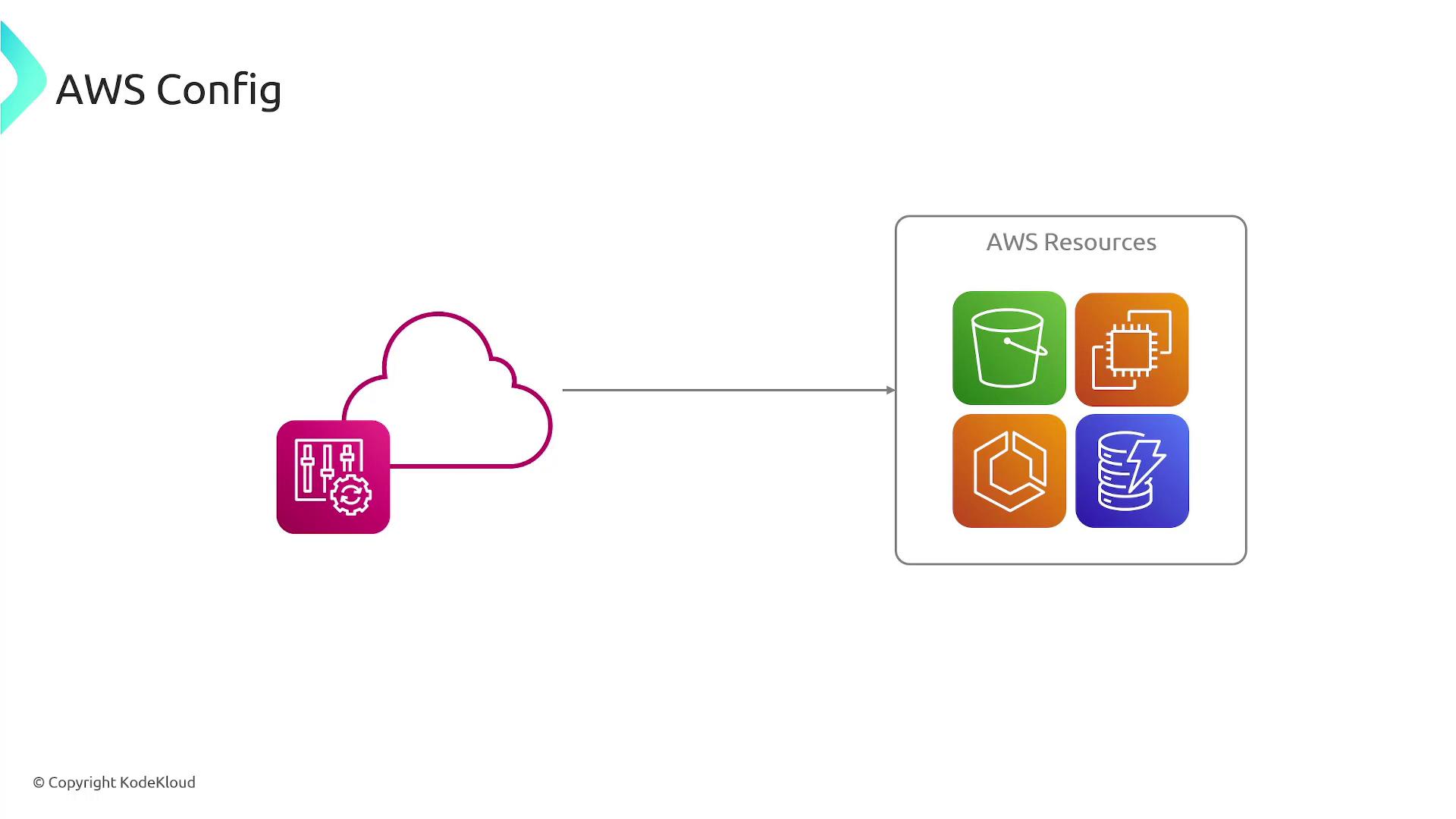
AWS Config addresses these challenges by:
- Keeping an inventory of all your AWS resources.
- Continuously monitoring and recording resource configurations.
- Capturing configuration changes over time.
- Reporting non-compliant resources.
- Enabling corrective actions through configurable rules.
- Sending notifications whenever a resource configuration changes.
- Analyzing relationships among different resources.
| AWS Config Feature | Benefit |
|---|---|
| Inventory Management | Maintains an up-to-date list of all AWS resources. |
| Continuous Monitoring | Records real-time changes in resource configurations. |
| Configuration History | Stores historical configuration data for auditing purposes. |
| Compliance Reporting | Detects non-compliant resources through rule evaluations. |
| Notification & Remediation | Automatically triggers alerts and remediation actions. |