Understanding NACLs
A Network Access Control List (NACL) serves as an additional firewall for your VPC by regulating traffic moving in and out of subnets. NACLs offer flexibility as you can associate one NACL with multiple subnets if they require similar traffic filtering. Each rule within a NACL is defined by:- A rule number (lower numbers indicate higher priority)
- The traffic type (e.g., all traffic, TCP, or UDP)
- Port range (for TCP/UDP)
- Source IP address (for inbound traffic)
- Action (either allow or deny)
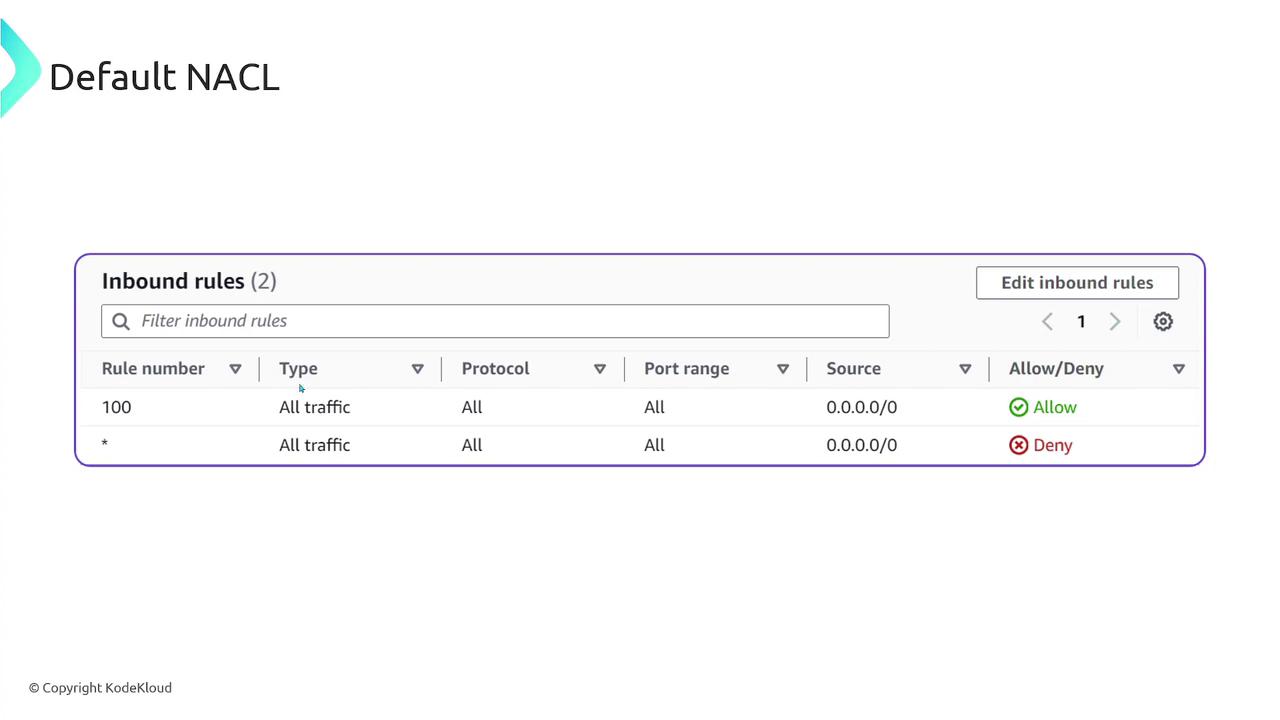
When you create a VPC and its corresponding subnets, a default NACL is automatically assigned that permits all traffic until you modify the rules to enforce more restrictive filtering.
Comparing NACLs and Security Groups
AWS employs two primary types of firewalls to secure your environment:- NACLs: Operate at the subnet level, filtering both inbound and outbound traffic.
- Security Groups: Provide instance-level security, managing traffic to and from individual EC2 instances and other resources.
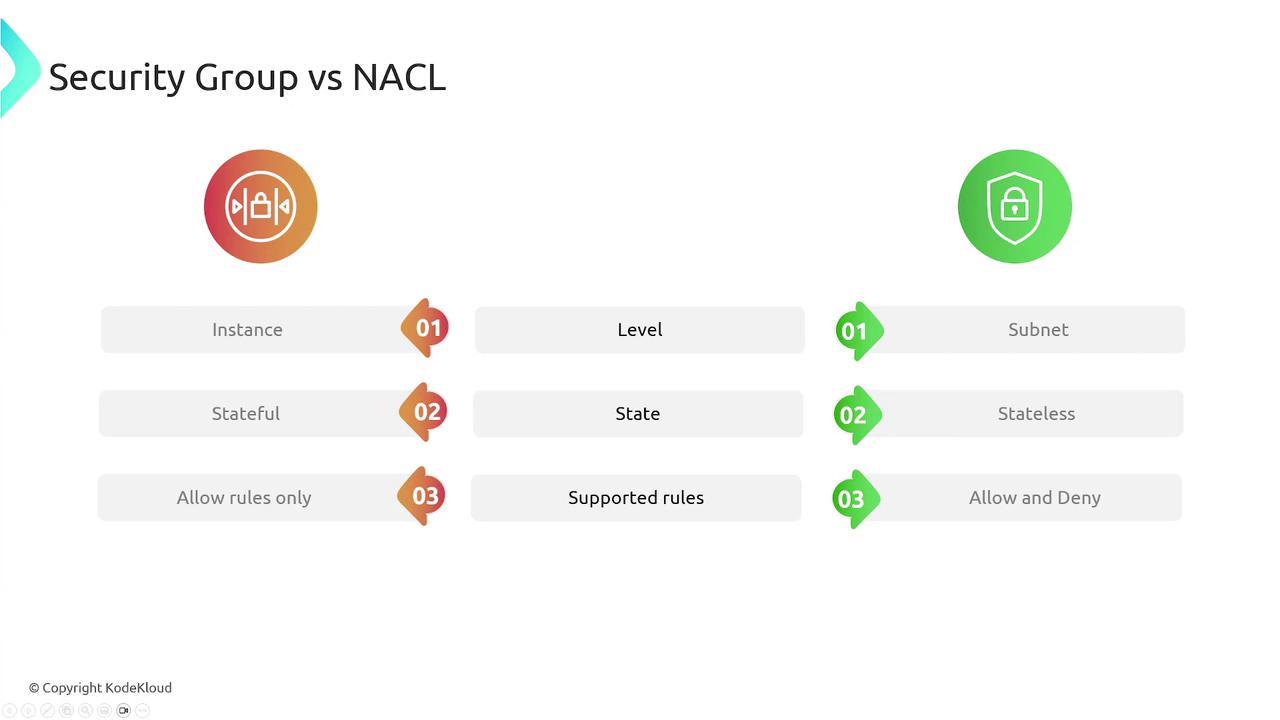
Key Differences in Traffic Handling
| Feature | NACLs | Security Groups |
|---|---|---|
| Level | Subnet-level | Instance-level |
| State | Stateless (requires explicit rules for both directions) | Stateful (inbound rules automatically allow outbound responses) |
| Rule Options | Allow and Deny | Allow only |
NACLs require you to configure rules for both directions since they are stateless, while security groups simplify management by automatically handling the response traffic.
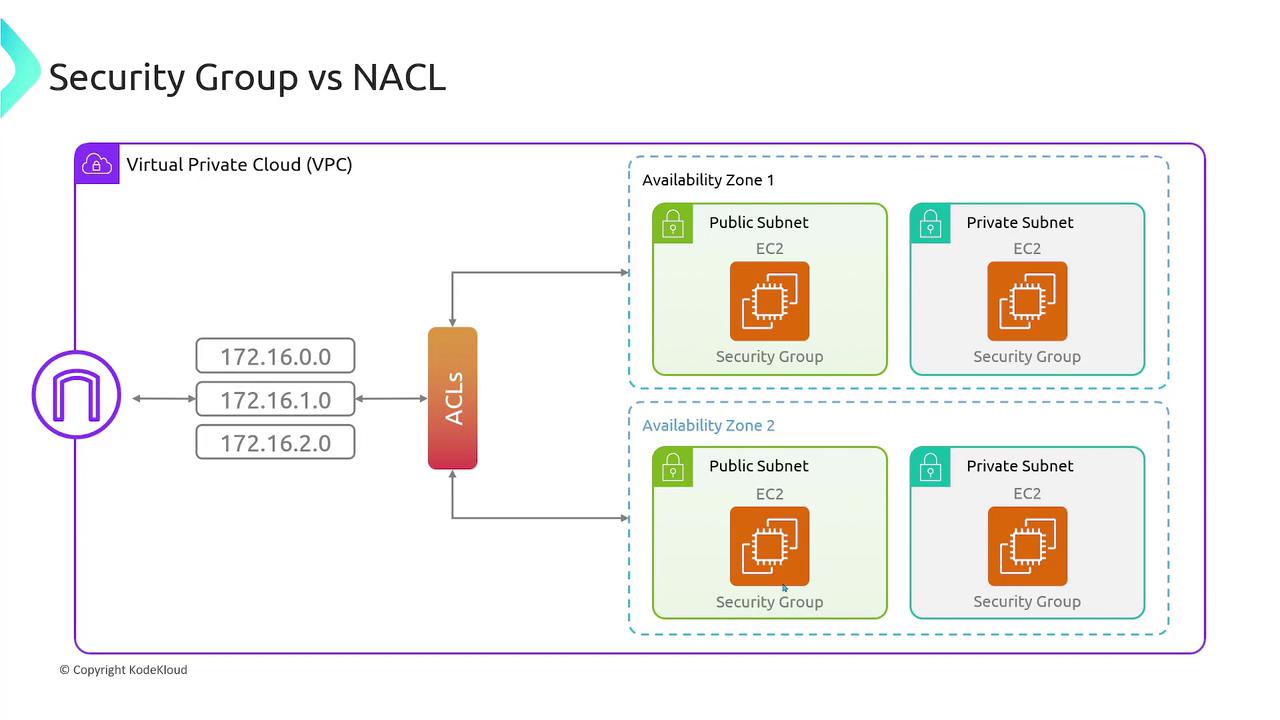
Integrating NACLs and Security Groups
NACLs and security groups complement each other by offering security at different layers of your VPC architecture:- NACLs control traffic at the subnet level.
- Security groups protect individual instances.
Deep Dive: Security Groups
Security groups act as virtual firewalls for individual instances, controlling inbound and outbound traffic. While every resource gets a default security group, you can tailor these groups to meet specific requirements.Managing Security Groups Effectively
Consider a scenario with multiple web servers that need only HTTP (port 80) and HTTPS (port 443) access. Instead of assigning unique security groups to each server, create one comprehensive web security group with the necessary rules and assign it to all. You can also attach multiple security groups to an EC2 instance to merge rules—such as combining web traffic with management traffic (SSH on port 22).Configuring Security Group Rules
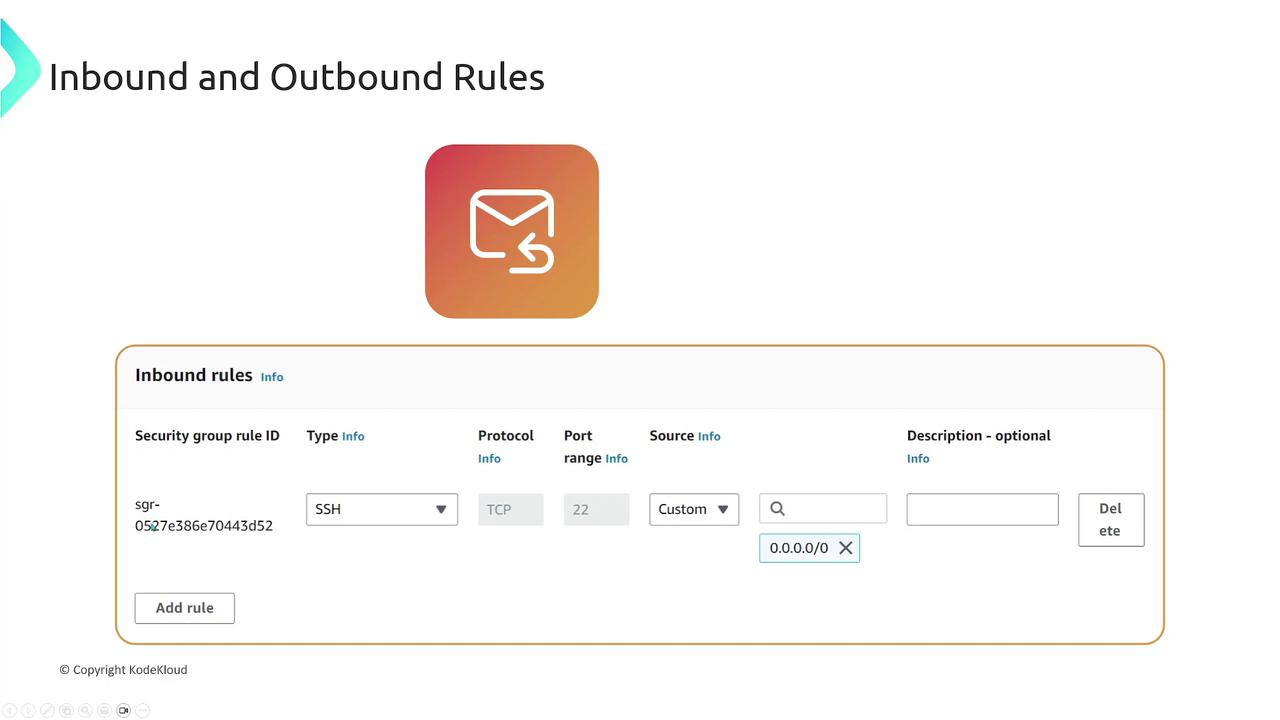
Security group rules are divided into two sections:- Inbound Rules: Control incoming traffic.
- Outbound Rules: Control outgoing traffic.
Automatic Traffic Exceptions in Security Groups
Certain traffic types are automatically permitted by security groups, ensuring essential communication is not interrupted. These include:- Amazon DNS servers
- Amazon DHCP traffic
- EC2 instance metadata service
- ECS task metadata endpoints
- Windows license activation traffic
- Amazon Time Sync Service
- Reserved IP addresses used by the default VPC router
You do not need to create explicit rules for the above protocols; they are automatically allowed by AWS to ensure critical services run smoothly.
This comprehensive guide has provided an in-depth look at how NACLs and security groups function, highlighting their individual roles and how they synergize to secure your AWS infrastructure effectively. For further reading and advanced configuration tips, be sure to check out the AWS Documentation and related resources.