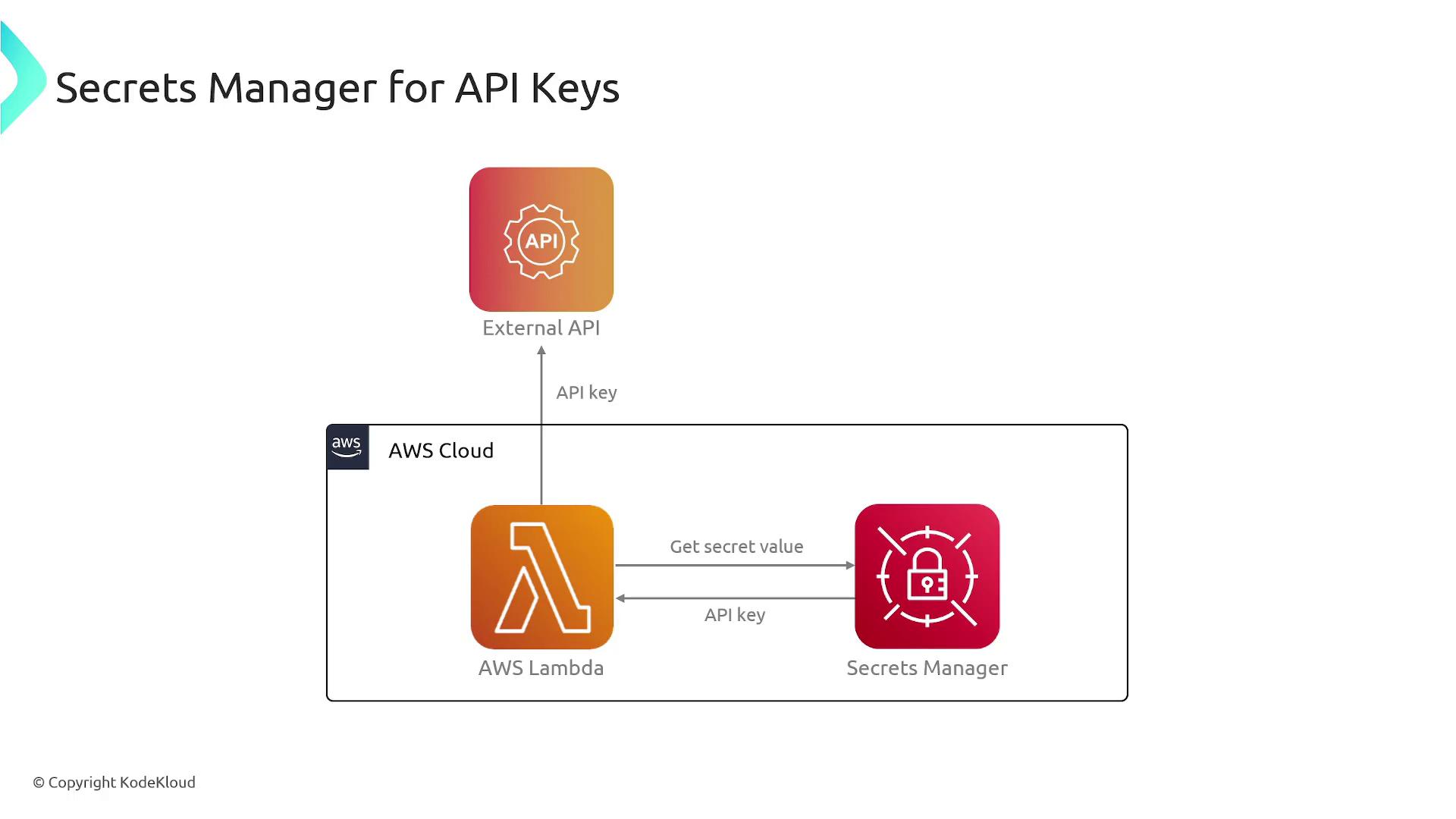
Never store credentials directly in your source code. Always use secure methods such as environment variables or services like AWS Secrets Manager to safeguard sensitive data.
The Risks of Hard-Coded Credentials
Embedding credentials in your application code exposes your systems to potential attacks. If an attacker accesses your repository, they may extract these sensitive credentials, putting your database and valuable customer information at risk.How AWS Secrets Manager Works
AWS Secrets Manager provides a reliable solution to this problem by allowing you to store, distribute, and manage sensitive data securely. This service handles various types of secrets including:- Database credentials
- Passwords
- Third-party API keys
- Any other sensitive configuration data
Secure Secret Management Workflow
Consider the following flow for managing credentials securely with AWS Secrets Manager:- Your application requires credentials to connect to a database.
- Instead of embedding these credentials in the code, you store them as secrets in AWS Secrets Manager.
- The credentials are encrypted using AWS KMS.
- When the application starts, it retrieves the encrypted credentials from Secrets Manager.
- AWS Secrets Manager decrypts the credentials using KMS and securely transmits them over TLS.
- The credentials are only available at runtime, ensuring they remain secure and hidden from the source code.
- AWS Lambda functions can be scheduled to rotate secrets automatically at defined intervals, enhancing overall security.
This workflow is applicable not only for database credentials but also for any sensitive data like API keys. Using AWS Secrets Manager helps centralize and secure all your critical secrets.
Key Features of AWS Secrets Manager
AWS Secrets Manager offers a range of benefits:| Feature | Description |
|---|---|
| Secure Storage | Encrypts secrets using AWS KMS, ensuring sensitive data is securely stored at rest. |
| Easy Retrieval | Simplifies secret management through straightforward API calls, reducing code complexity. |
| Automatic Rotation | Facilitates scheduled secret rotation, minimizing the risk of credential compromise. |
| Fine-Grained Access Control | Provides detailed access policies to control who can access specific secrets. |