AZ-400: Designing and Implementing Microsoft DevOps Solutions
Design and Implement Authentication and Authorization Methods
Design and implement permissions and security groups in Azure DevOps
In this lesson, you’ll learn how to configure permissions and manage security groups in Azure DevOps to enforce a least-privilege Role-Based Access Control (RBAC) model. This knowledge is essential for the AZ-400 exam.
We’ll cover:
- Managing organization-level users
- Configuring projects and teams
- Reviewing built-in security groups
- Creating custom security groups
- Securing repositories and pipelines
- Auditing permissions regularly
1. Manage Organization Users
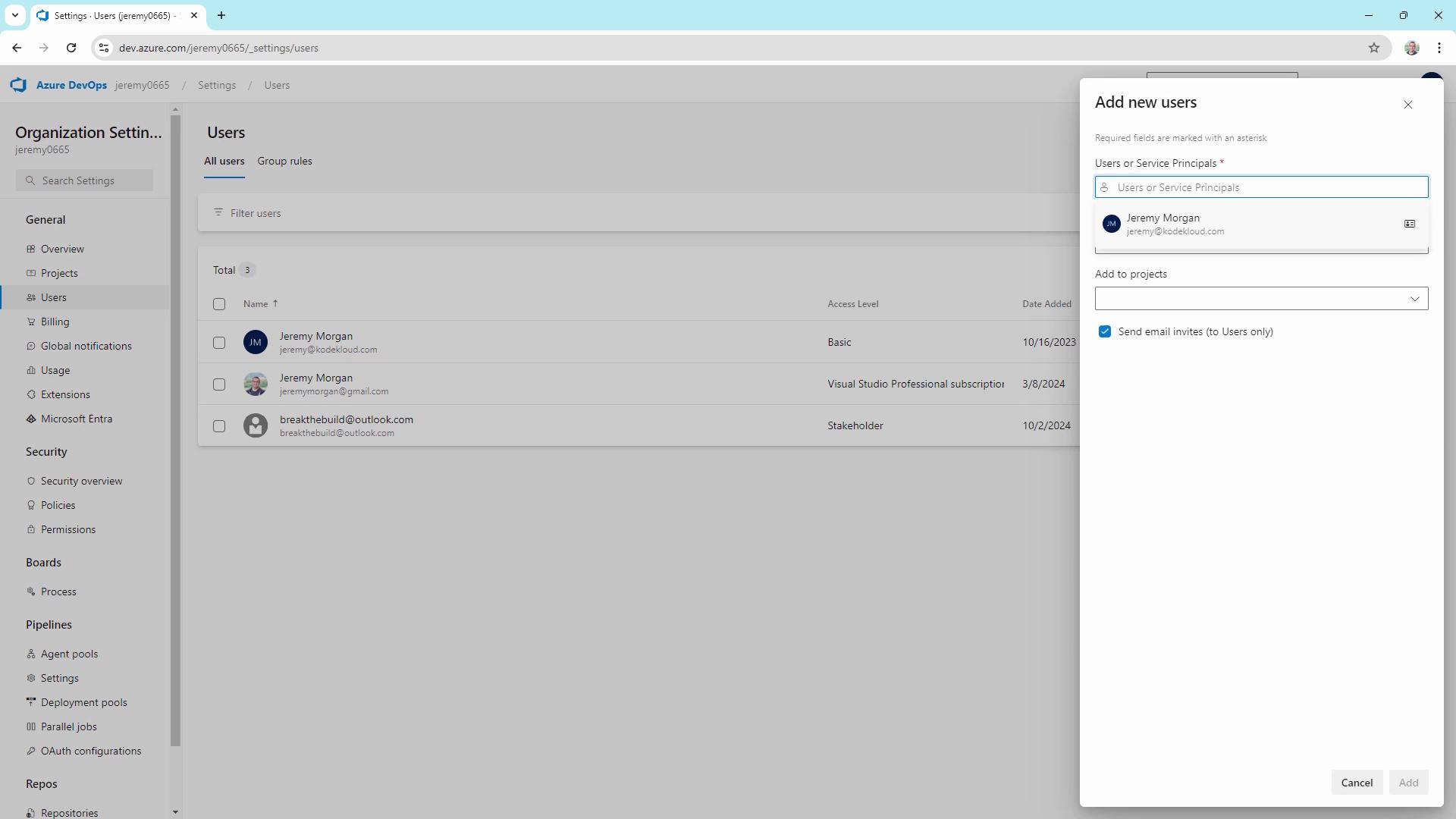
- Go to Organization Settings (lower-left) → Users.
- View existing members (e.g., [email protected], Jeremy [email protected], [email protected]).
- Click Add Users, enter the email or service principal, choose an Access Level (Basic, Stakeholder, Visual Studio Subscriber), and assign projects.
Note
Invitation emails are only sent to user accounts—not service principals. Recipients must accept the invitation to join the organization.
2. Configure Project Settings and Teams
- Select your organization (e.g., KodeKloud demo) and open the Simple Converter project.
- Navigate to Project Settings (lower-left) → Overview to see Project Administrators.
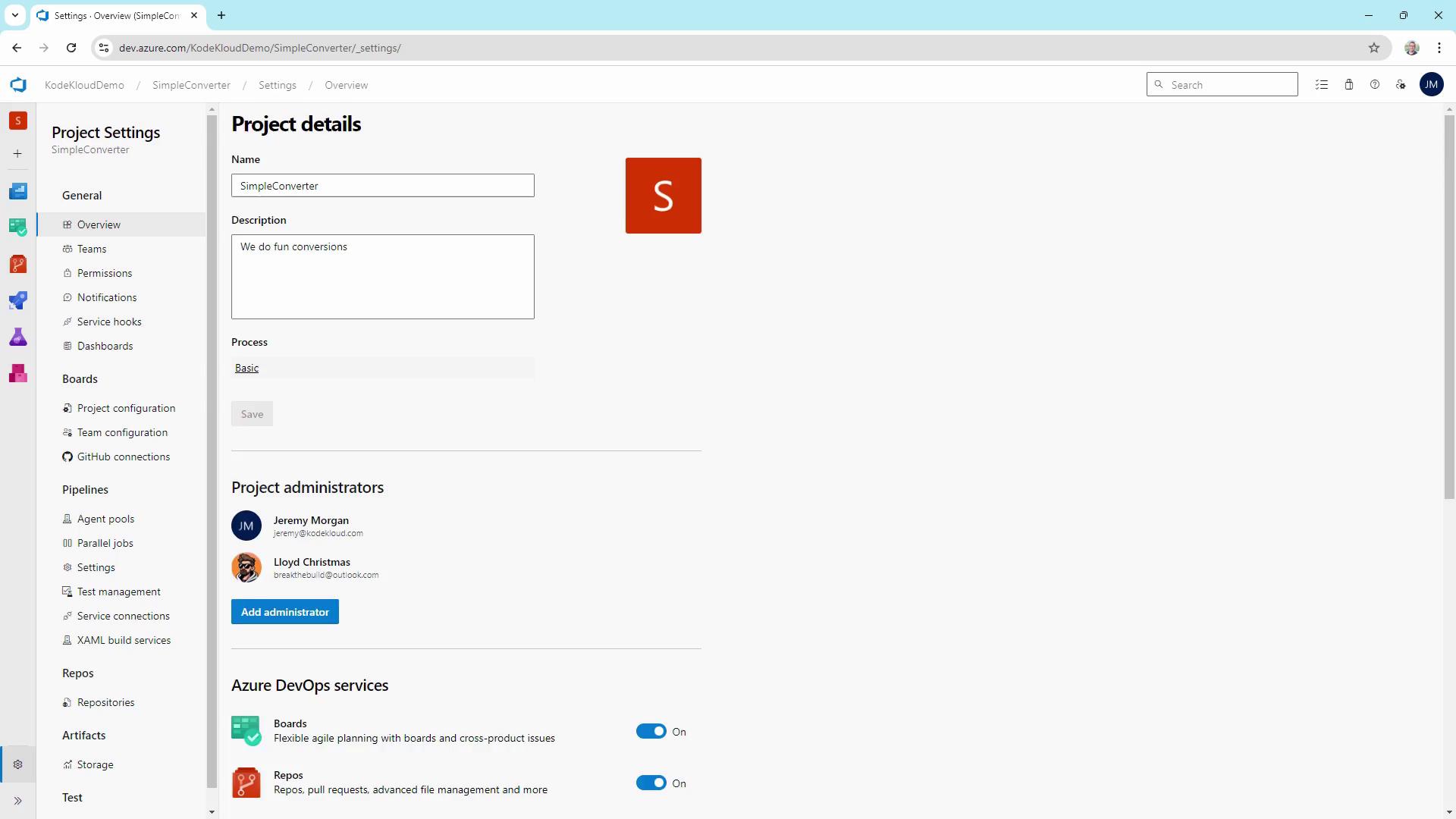
Default Team
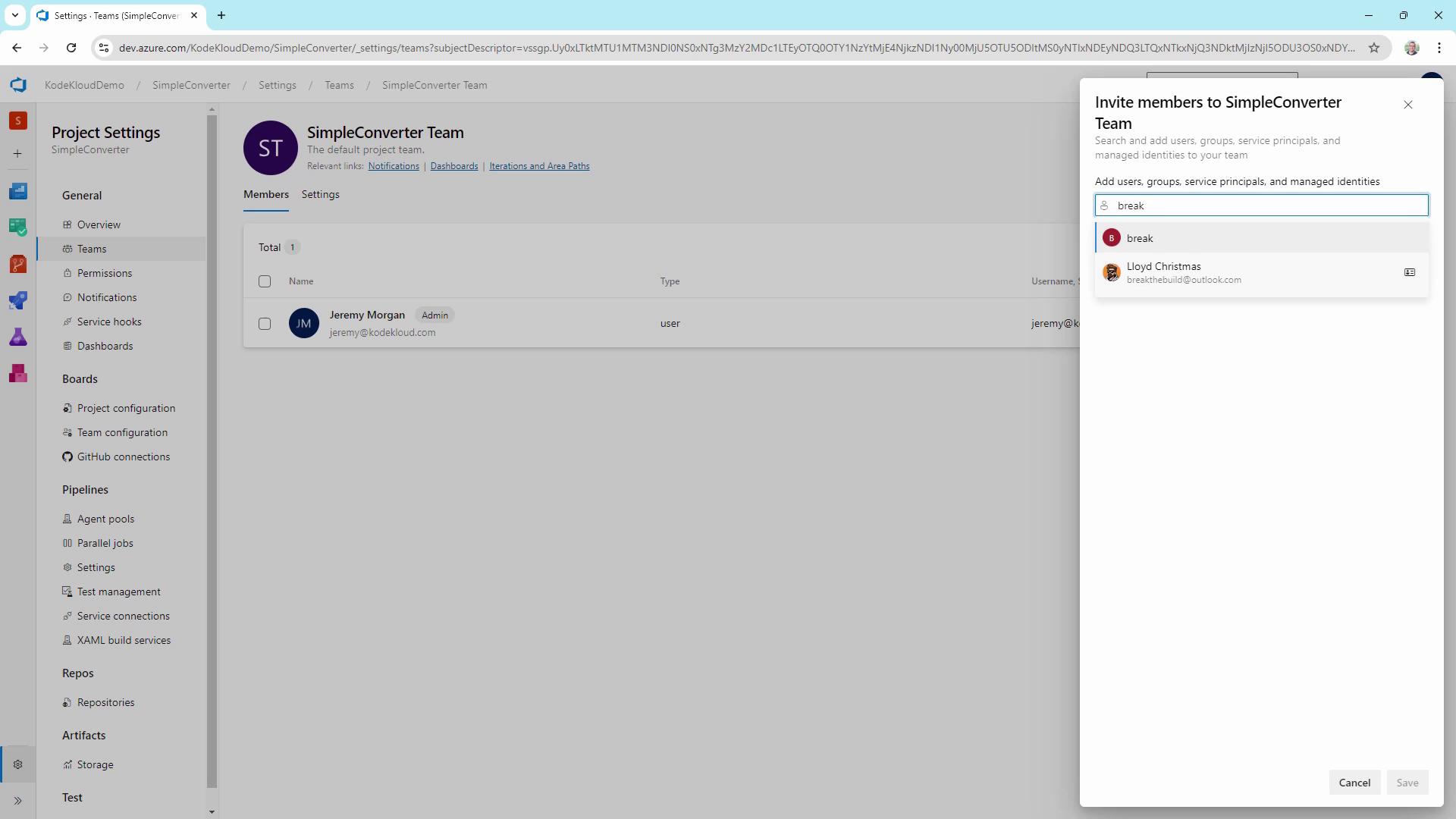
- Under Teams, click Simple Converter.
- Invite members explicitly—even project admins must be added here to inherit team permissions.
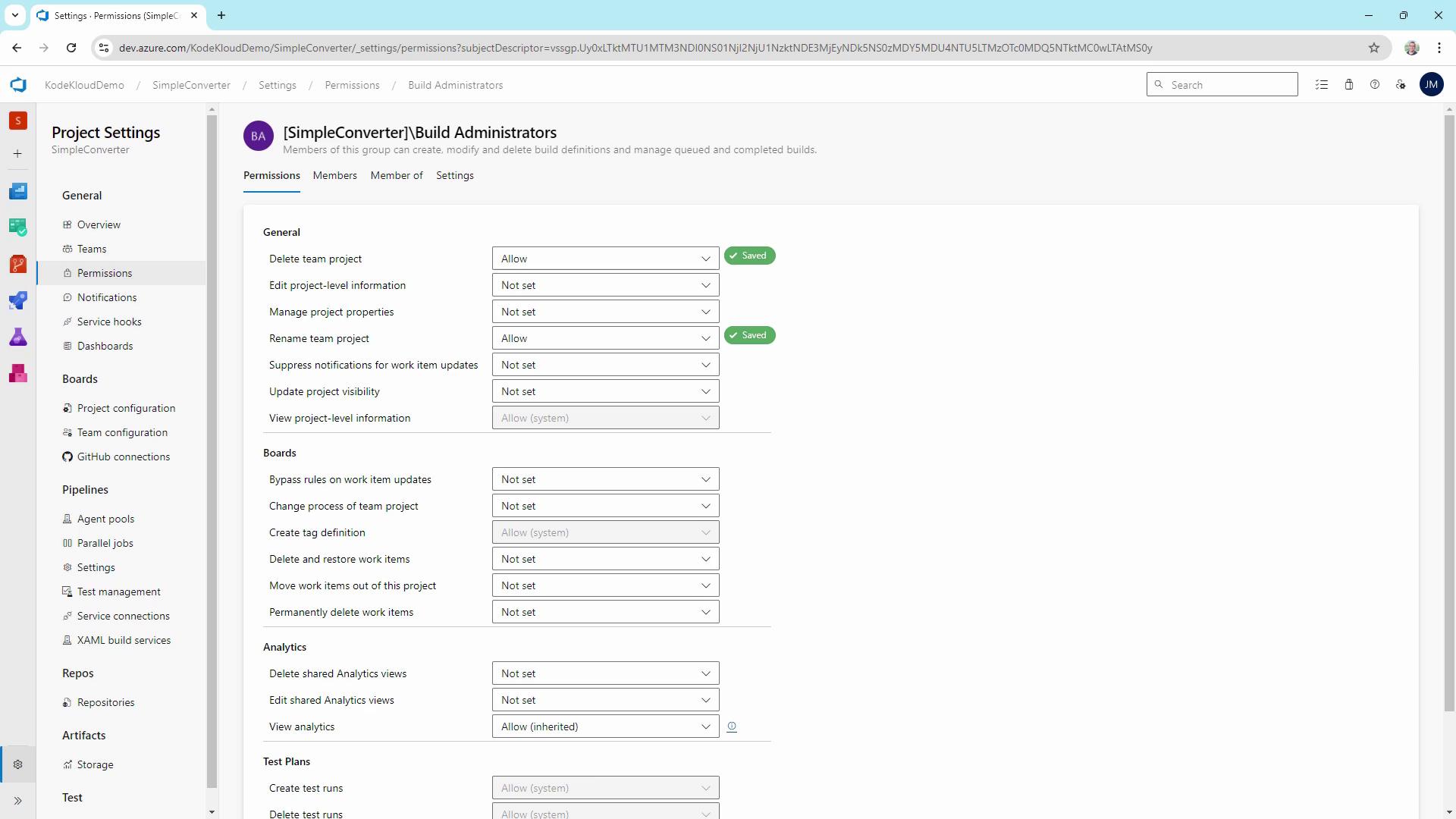
3. Review Built-in Security Groups
- In Project Settings → Security → Permissions, select a built-in group (e.g., Build Administrators).
- Inspect granular permissions:
- View analytics: Allow
- View project-level information: Allow
- Create tag definitions: Allow
- Create/Delete test runs: Allow
- Manage test configurations/environments: Allow
- View test runs: Allow
Best Practices
- Grant only necessary permissions (least-privilege).
- Use explicit Deny to override undesired inherited Allow.
- For temporary tasks, add users to privileged groups, then remove them immediately.
4. Create Custom Security Groups
- Navigate to Security → New Group.
- Name it
JavaScript Developersand add members (e.g., Lloyd). - By default, it inherits permissions from Project Valid Users.
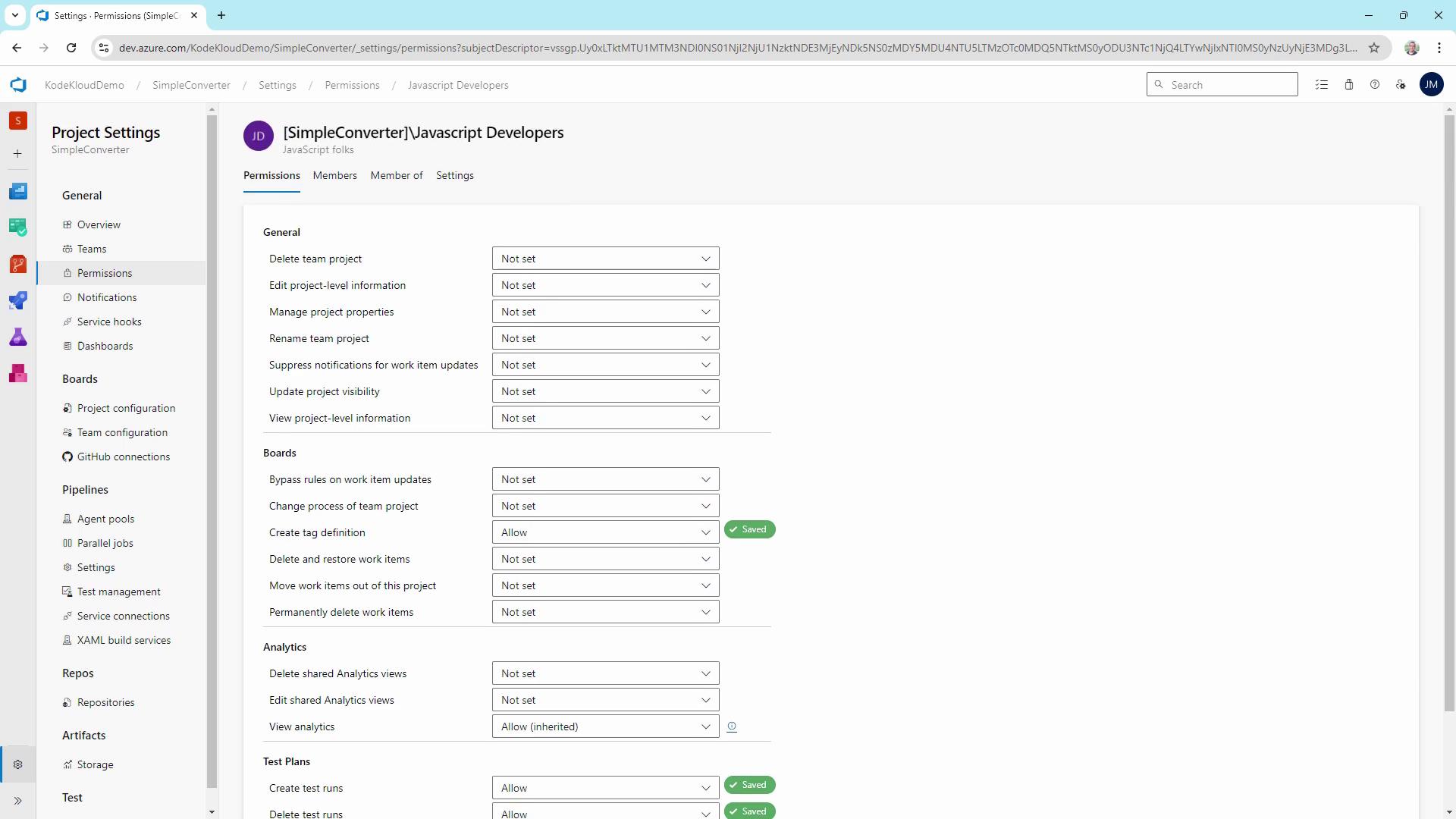
Grant additional rights:
- Create tag definitions: Allow
- Create/Delete test runs: Allow
Team-Level Customization
Under Teams → Simple Converter → Settings, you can:
- Create sub-teams (e.g.,
Test Group). - Assign only required permissions (e.g., View project-level information).
5. Secure Repositories and Pipelines
Use Azure DevOps security settings to fine-tune code and CI/CD access:
| Resource | Role | Actions Allowed |
|---|---|---|
| Repos | Reader | Clone, fetch, view code |
| Repos | Contributor | Push commits, create branches, manage pull requests |
| Pipelines | Reader | View pipeline definitions and run history |
| Pipelines | Contributor | Create, edit, queue builds |
- Go to Repos or Pipelines → Security.
- Adjust permissions per role.
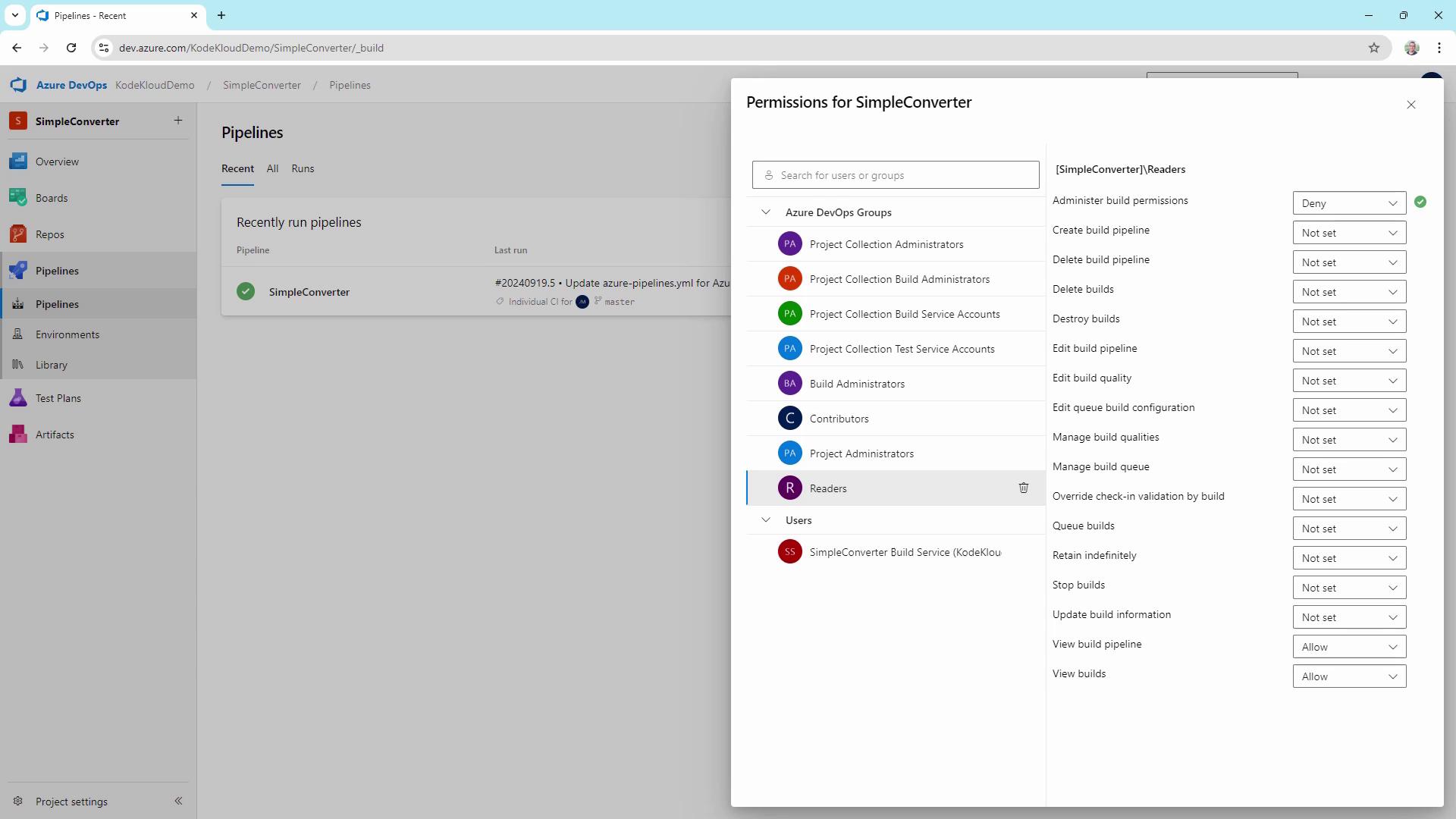
Warning
Avoid granting Destroy builds or other destructive permissions unless absolutely necessary.
6. Regular Review and Audit
- Periodically review all security groups and permissions.
- Remove or deny obsolete accounts.
- Track changes via Audit Logs to maintain compliance.
Note
Schedule quarterly permission reviews to ensure your RBAC model remains secure and current.
Links and References
- AZ-400 Exam (Microsoft Learn)
- Azure DevOps REST API Security
- Role-Based Access Control (RBAC) in Azure
Watch Video
Watch video content