AZ-400: Designing and Implementing Microsoft DevOps Solutions
Design and Implement a Strategy for Managing Sensitive Information in Automation
Implement and manage secrets in GitHub Actions and Azure Pipelines
Secrets—like API keys, passwords, and tokens—are critical for accessing protected resources in your CI/CD pipelines. Mishandling these credentials can expose your infrastructure to unauthorized access and data breaches. This article covers secure storage, access, and best practices for secrets in GitHub Actions and Azure Pipelines, plus integration with Azure Key Vault.
Both GitHub Actions and Azure Pipelines provide built-in secret management to keep sensitive data out of your code and logs.
Secrets Management Comparison
| Feature | GitHub Actions | Azure Pipelines |
|---|---|---|
| Storage Location | Repository > Settings > Secrets | Pipeline Variables (Secret-enabled) |
| Syntax in Workflow | ${{ secrets.SECRET_NAME }} | $(VARIABLE_NAME) |
| Integration with Key Vault | Via Actions (e.g., azure/keyvault-secrets) | UseKeyVault@1 task |
| Secret Rotation | Manual/API | Manual/API or automated via Key Vault |
Managing Secrets in GitHub Actions
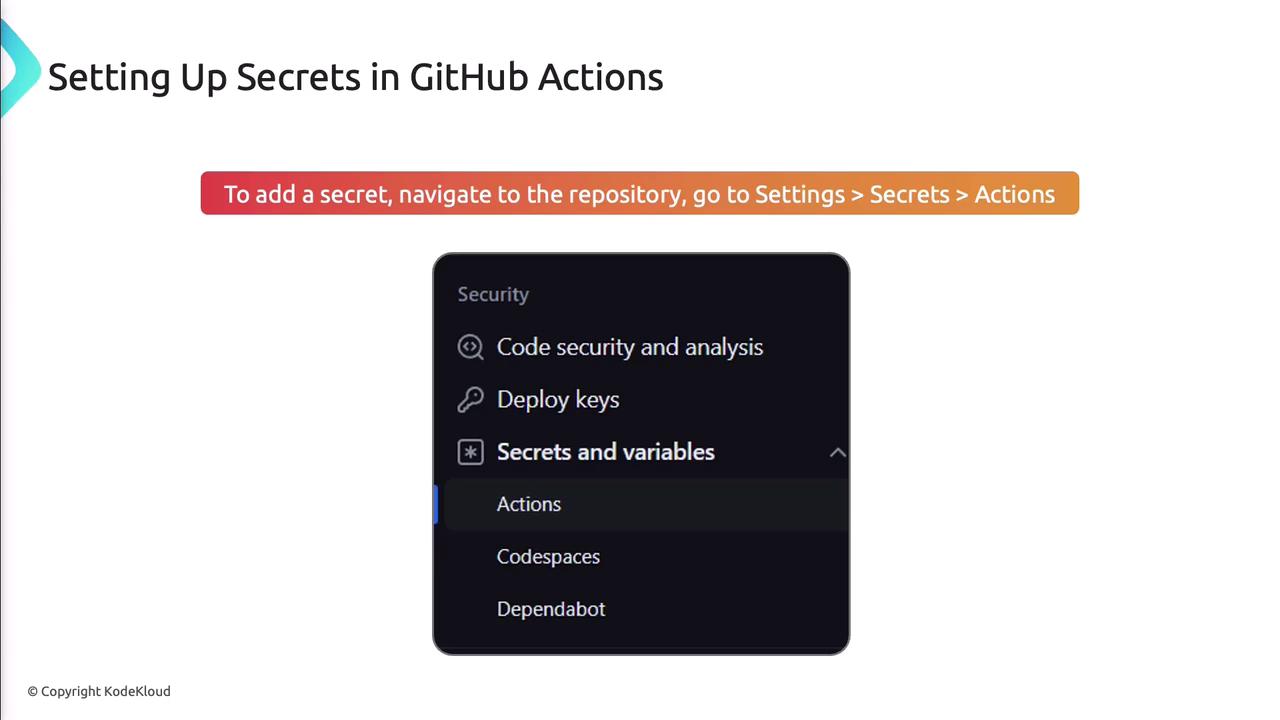
Store secrets in your repo settings:
- Go to Settings > Secrets > Actions in your repository.
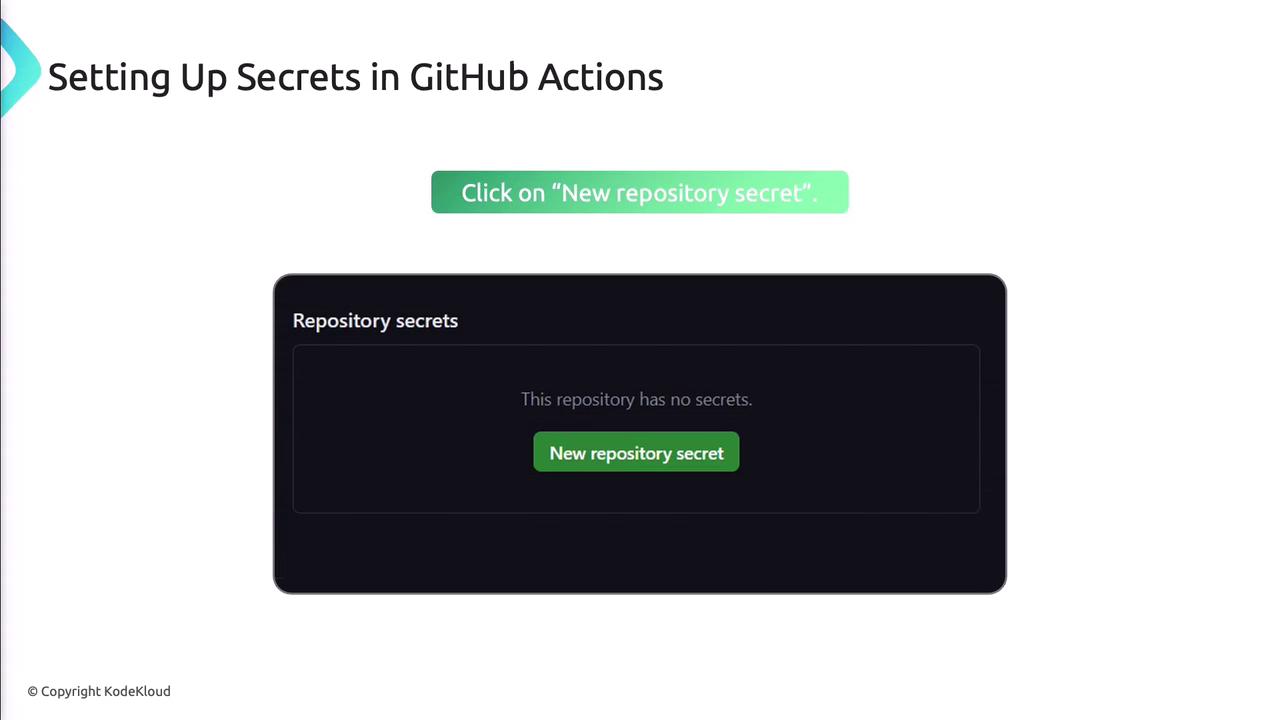
- Click New repository secret.
- Enter a descriptive name and the secret value.
- Save.
Access secrets in workflows:
Warning
Never print secrets in plain text. Always reference them using ${{ secrets.NAME }} to keep them masked in logs.
# .github/workflows/deploy.yml
name: Deploy Application
on:
push:
branches: [ main ]
jobs:
deploy:
runs-on: ubuntu-latest
env:
API_KEY: ${{ secrets.API_KEY }} # Secure reference
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Call API
run: |
curl -H "Authorization: Bearer $API_KEY" https://api.example.com
GitHub Actions Best Practices
- Use clear, descriptive names (e.g.,
DB_CONN_STRING). - Rotate secrets regularly to reduce risk.
- Restrict secrets to the least-privileged repos and workflows.
- Avoid hard-coding secrets—always reference the secure store.

Managing Secrets in Azure Pipelines
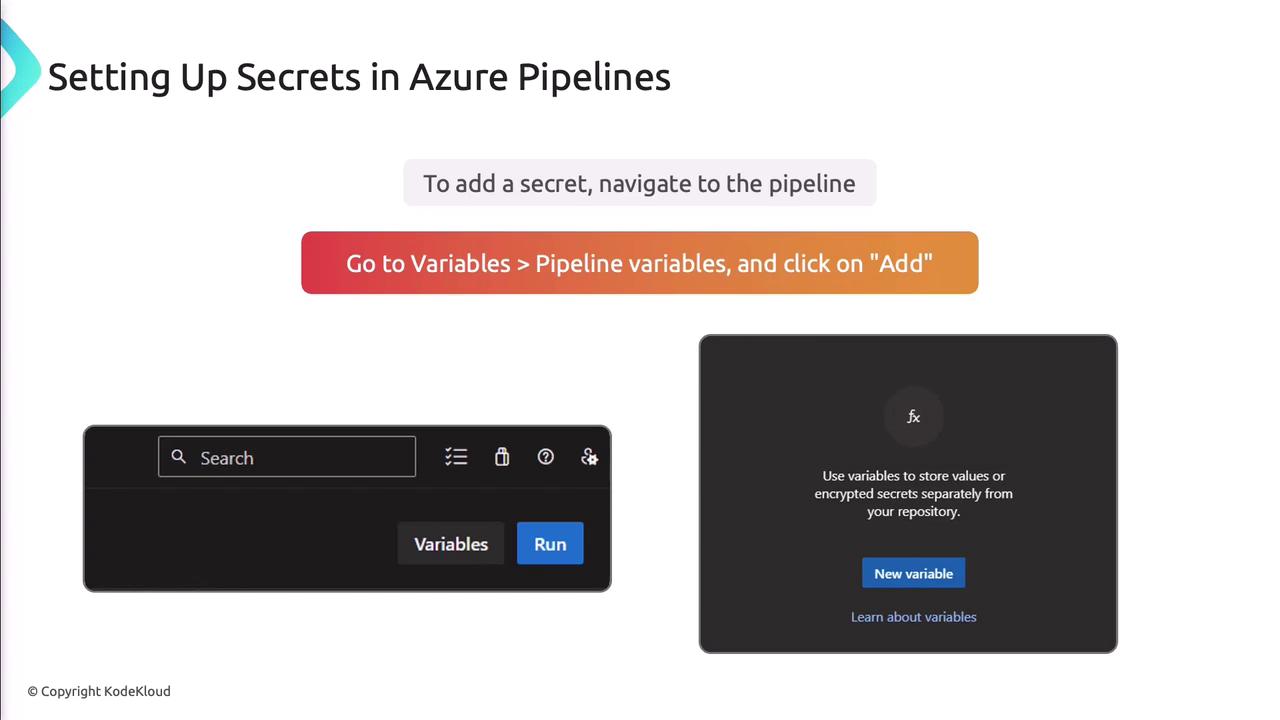
In Azure Pipelines, mark variables as secret:
- Open your pipeline in Azure DevOps.
- Select Variables > Pipeline Variables.
- Click Add, name your variable, enable Keep this value secret, and set its value.
- Save the pipeline.
Use secrets in scripts:
# azure-pipelines.yml
steps:
- script: |
echo "Calling API with key $(API_KEY)"
displayName: "Use Secret Variable"
Azure Pipelines Best Practices
- Integrate with Azure Key Vault for higher security.
- Grant variable access only to necessary pipelines or stages.
- Audit and rotate secrets on schedule.
- Use environment-specific variables to isolate credentials.
Using Azure Key Vault for Secret Management
Azure Key Vault centralizes storage for secrets, keys, and certificates, offering:
- Fine-grained access control (RBAC and policies).
- Audit logging of all secret operations.
- Automated secret rotation and versioning.
- Secure retrieval via REST API or SDKs.
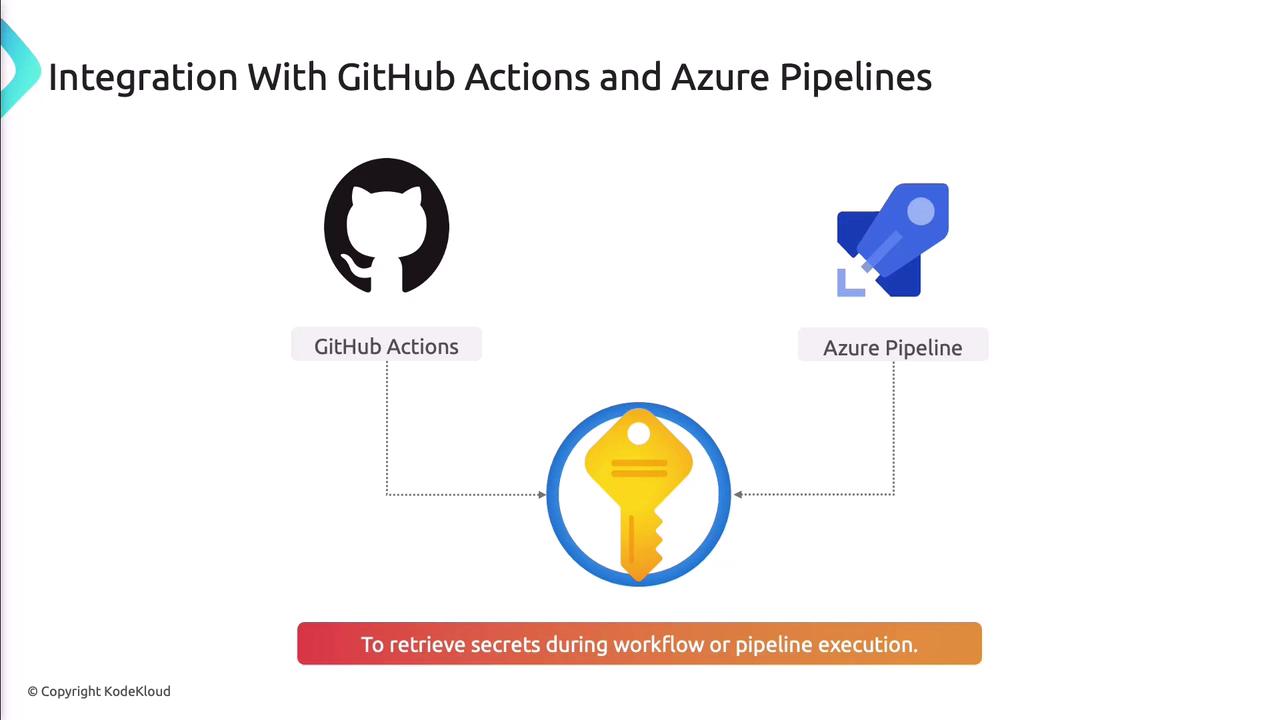
Platforms like GitHub Actions and Azure Pipelines can fetch secrets at runtime without exposing them in code.
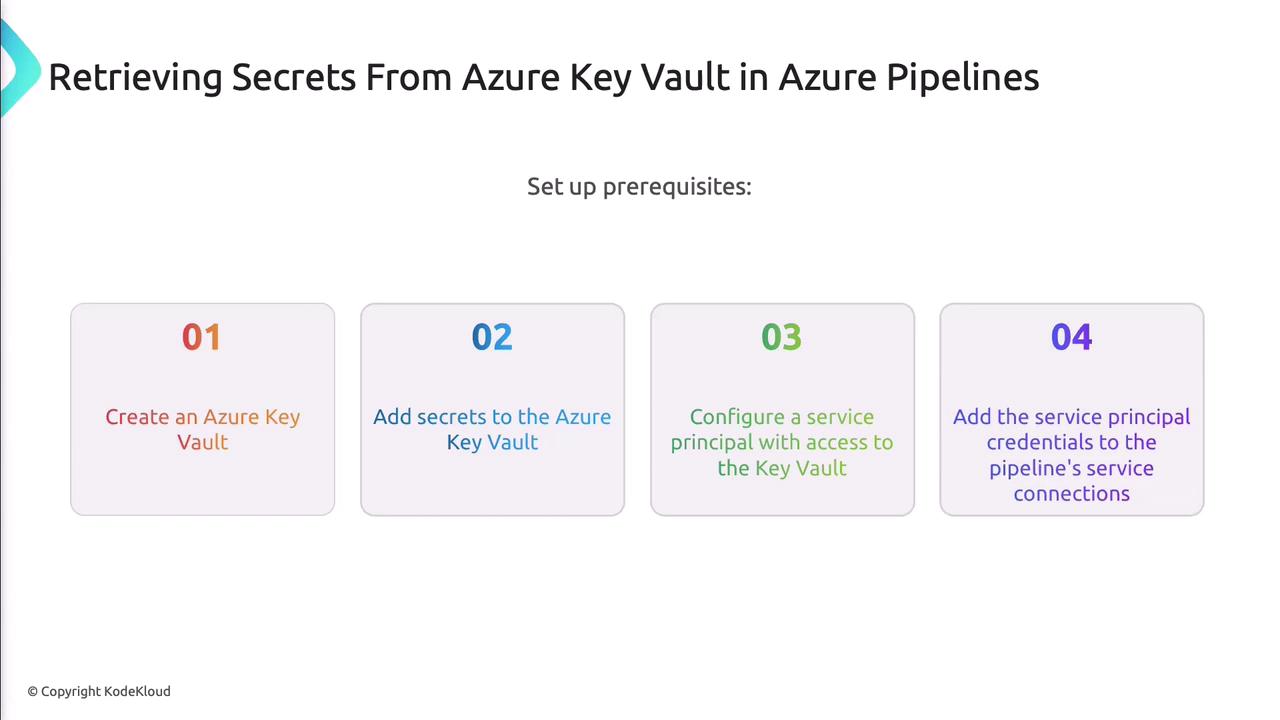
Prerequisites for Azure Key Vault Integration
- Active Azure subscription.
- Existing Key Vault with stored secrets.
- Service Principal (SP) with
Key Vault Secrets Userrole. - SP credentials saved as GitHub secrets or Azure DevOps service connection.
CI/CD Secrets Management Best Practices
Principle of Least Privilege
Only grant users and services the minimum permissions needed. In Azure Pipelines, use the UseKeyVault@1 task:
# azure-pipelines.yml
trigger:
branches:
include: [ main ]
pool:
vmImage: ubuntu-latest
variables:
- group: KeyVaultSecrets
steps:
- task: UseKeyVault@1
inputs:
azureSubscription: 'your-service-connection'
KeyVaultName: 'your-keyvault-name'
SecretsFilter: 'MY_SECRET'
RunAsPreJob: true
- script: echo "Secret Value: $(MY_SECRET)"
displayName: 'Retrieve and Display Secret'
Regular Secret Rotation
- Schedule periodic rotations to limit exposure.
- Automate rotation workflows using Key Vault features or custom scripts.
Monitoring and Auditing
- Enable logging for every secret access attempt.
- Set up alerts for unauthorized access or policy breaches.
- Review audit logs regularly to ensure compliance.

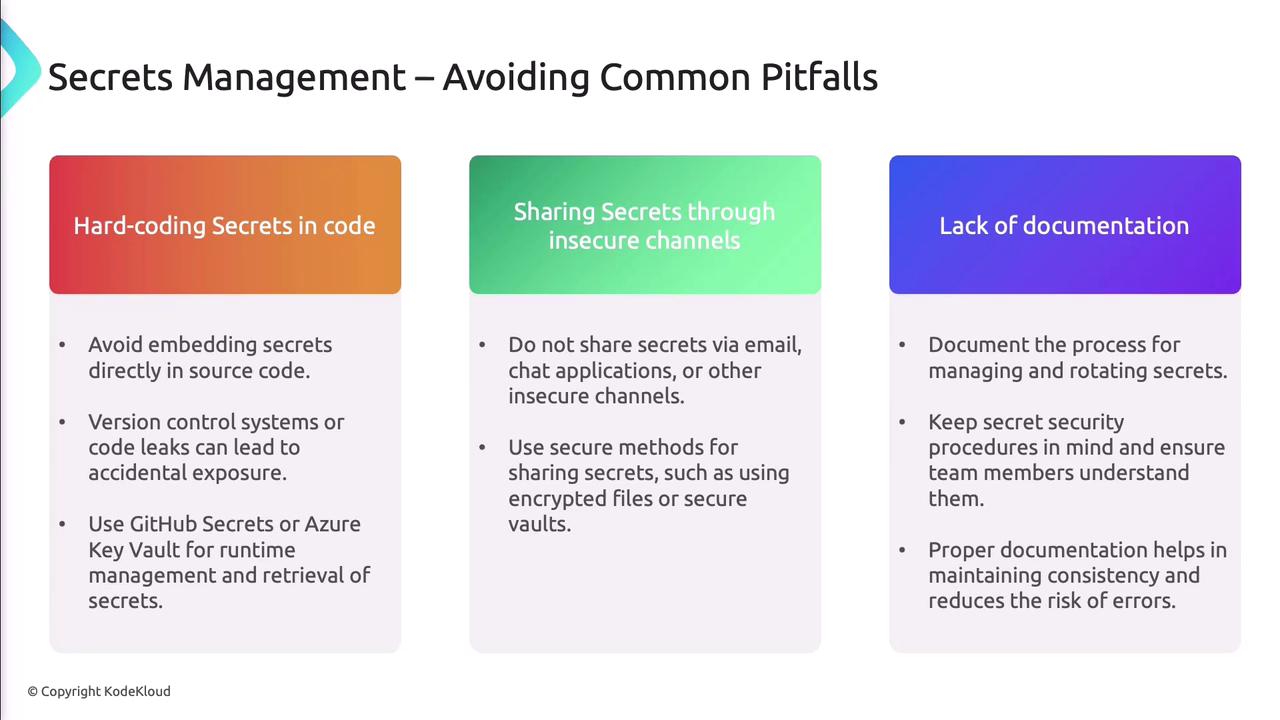
Common Pitfalls in Secrets Management
- Hard-coding secrets in repositories.
- Sharing secrets via unencrypted channels (email, chat).
- Skipping documentation for rotation and revocation procedures.
Avoid these issues by centralizing secrets in GitHub Secrets, Azure Key Vault, or similar vault services, and maintain clear, versioned documentation.
References
- GitHub Actions: Encrypting secrets
- Azure Pipelines: Variables
- Azure Key Vault Documentation
- Azure DevOps: Service connections
Watch Video
Watch video content