In this guide, you’ll learn how to:
Redirect all HTTP traffic to HTTPS using Nginx.
Generate a local SSL certificate for testing.
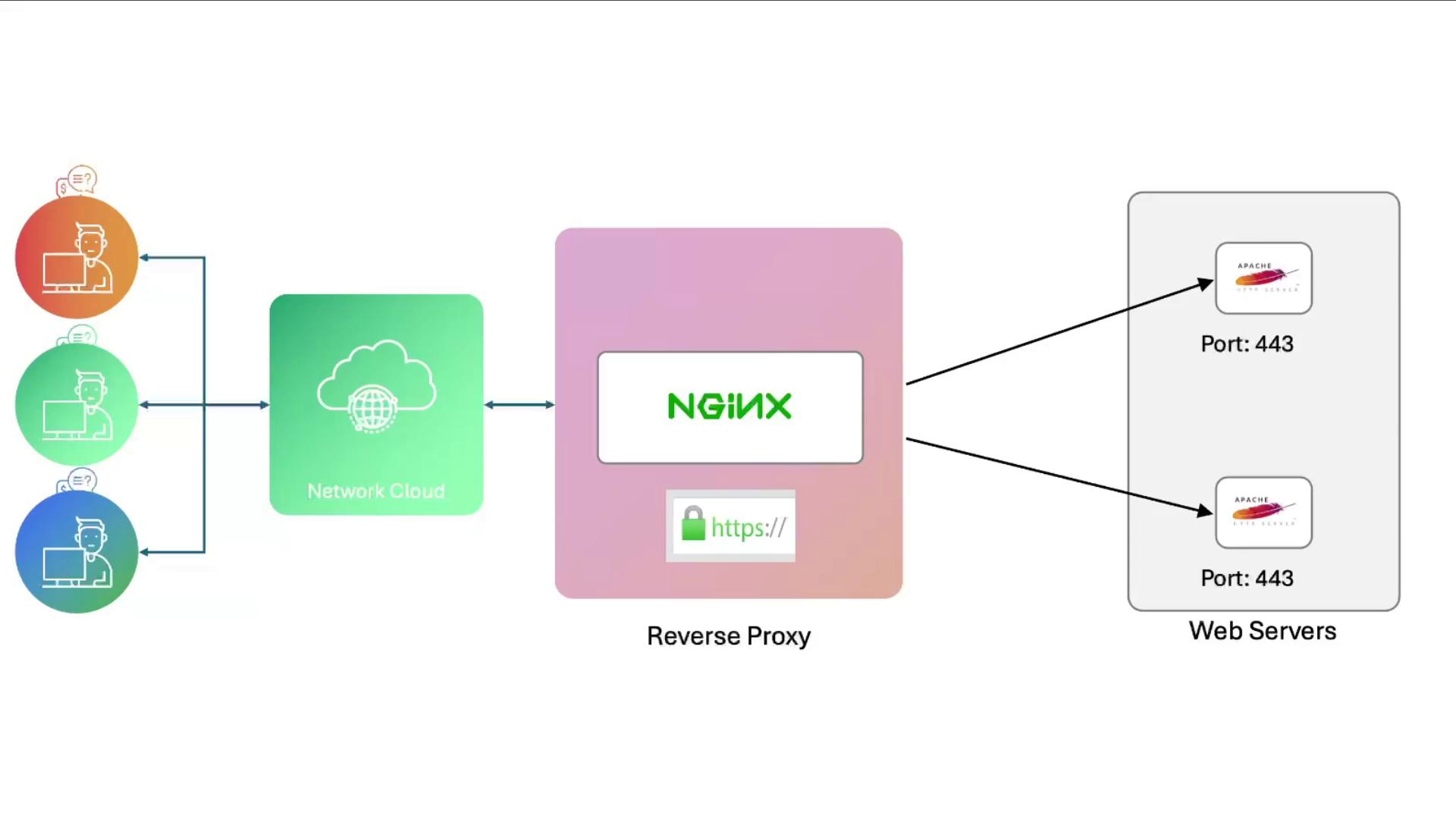
Configure Nginx as an HTTPS reverse proxy forwarding encrypted requests to Apache backends on port 443.
1. Simple HTTP → HTTPS Redirect 1.1 Open Port 443 in the Firewall Verify that TCP port 443 is allowed through UFW:
# Check current UFW status sudo ufw status # If 443/tcp is not listed, enable it: sudo ufw allow 443/tcp
1.2 Switch from HTTP-Only to HTTPS Remove the old HTTP site and enable the HTTPS configuration:
# Disable HTTP site sudo rm /etc/nginx/sites-enabled/example-http # List available site configs ls -l /etc/nginx/sites-available # Edit the HTTPS site template sudo vim /etc/nginx/sites-available/example-https
Add the following to example-https:
server { listen 80 ; server_name example.com; return 301 https://$ host $ request_uri ; } server { listen 443 ssl; server_name example.com; ssl_certificate /etc/ssl/certs/example.com.pem; ssl_certificate_key /etc/ssl/certs/example.com-key.pem; root /var/www/html; index index.html index.htm; location / { try_files $ uri $ uri / =404 ; } }
Enable the site and test Nginx:
sudo ln -s /etc/nginx/sites-available/example-https /etc/nginx/sites-enabled/ sudo nginx -t
Nginx will report missing certificate files until you generate them in the next step.
1.3 Generate a Test SSL Certificate with mkcert We’ll use mkcert to create a local CA and certificate:
cd /etc/ssl/certs sudo mkcert example.com
Sample output:
Created a new local CA 🏴 Note: the local CA is not installed in the system trust store. Run "mkcert -install" to trust it automatically. Created a certificate valid for: - "example.com" The certificate is at "./example.com.pem" The key is at "./example.com-key.pem"
Reload Nginx with the new certificates:
sudo nginx -t sudo nginx -s reload
Now visit:https://example.com
2. HTTPS Reverse Proxy to Apache Backends Edit /etc/nginx/sites-available/example-https to add an upstream block:
# Upstream Apache backends on port 443 upstream example { server 192.230.210.3:443; server 192.230.210.6:443; } # Redirect HTTP to HTTPS server { listen 80 ; server_name example.com; return 301 https://$ host $ request_uri ; } # HTTPS listener forwarding to upstream server { listen 443 ssl; server_name example.com; ssl_certificate /etc/ssl/certs/example.com.pem; ssl_certificate_key /etc/ssl/certs/example.com-key.pem; root /var/www/html; index index.html index.htm; location / { proxy_pass https://example; proxy_set_header Host $ host ; proxy_set_header X-Real-IP $ remote_addr ; } }
Test and reload:
sudo nginx -t sudo nginx -s reload
On each Apache node:
Allow HTTPS in the firewall:sudo ufw allow 443/tcp
Create /etc/apache2/sites-available/example.conf:
< VirtualHost *:80 > ServerName example.com Redirect permanent / https://%{HTTP_HOST}%{REQUEST_URI} </ VirtualHost > < VirtualHost *:443 > ServerName example.com DocumentRoot /var/www/html SSLEngine on SSLCertificateFile /etc/ssl/certs/example.com.pem SSLCertificateKeyFile /etc/ssl/certs/example.com-key.pem ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </ VirtualHost >
Enable the site and reload Apache:
sudo a2ensite example.conf sudo systemctl reload apache2
Now, https://example.com → Nginx → one of your Apache backends over HTTPS.
Configuration Reference File Purpose /etc/nginx/sites-available/example-https Nginx HTTP→HTTPS redirect & HTTPS reverse proxy /etc/apache2/sites-available/example.conf Apache vhosts for HTTP and HTTPS
Links and References