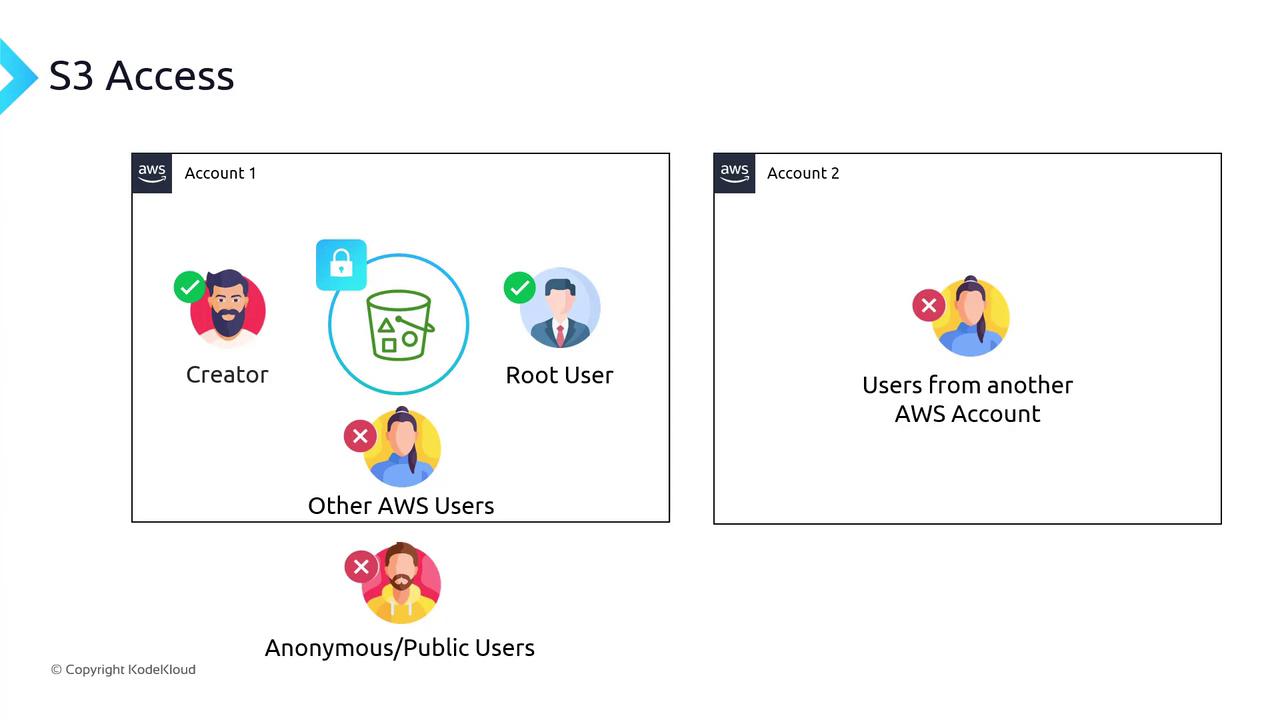
Understanding Default S3 Bucket Permissions
When you create a new S3 bucket:- Only the bucket creator (and the AWS root user) has access.
- No other IAM users—even in your own account—can access it.
- Public or anonymous users are explicitly denied until you grant permission.
Resource Policies (Bucket Policies)
A resource policy is a JSON document attached directly to an AWS resource. For S3, this is called a bucket policy. It specifies:- Principals: Who can access
- Effect: Allow or Deny
- Actions: S3 operations
- Resources: Which buckets or objects
- Conditions (optional): Additional restrictions

Anatomy of a Bucket Policy
Below is a minimal bucket policy. Use this as a template:| Field | Description |
|---|---|
| Version | Policy language version (use 2012-10-17 unless updated by AWS). |
| Sid | Statement identifier (optional). |
| Principal | AWS account, user, role, or * (everyone). |
| Effect | Allow or Deny. |
| Action | S3 operations, e.g., s3:GetObject, s3:ListBucket, or s3:*. |
| Resource | ARN of bucket or objects, e.g., arn:aws:s3:::bucket-name or arn:aws:s3:::bucket-name/*. |
Always specify the least-privilege permissions. Start by allowing only the actions and resources that are strictly required.
Multiple Statements
You can combine statements in one policy. For example, allow everyone to read objects but deny one user:- A principal of
*covers all AWS users and anonymous/public users. - You may add as many statements as needed.
Restricting by Prefix
To limit access to a specific “folder” (prefix):Adding Conditions
You can enforce network or request constraints:Granting Access to Multiple Folders
UseStringEquals on s3:prefix and s3:delimiter:
Block Public Access Settings
Even if a bucket policy usesPrincipal: "*", AWS provides Block Public Access as a safety net. With these settings enabled, public policies are overridden until you disable them.
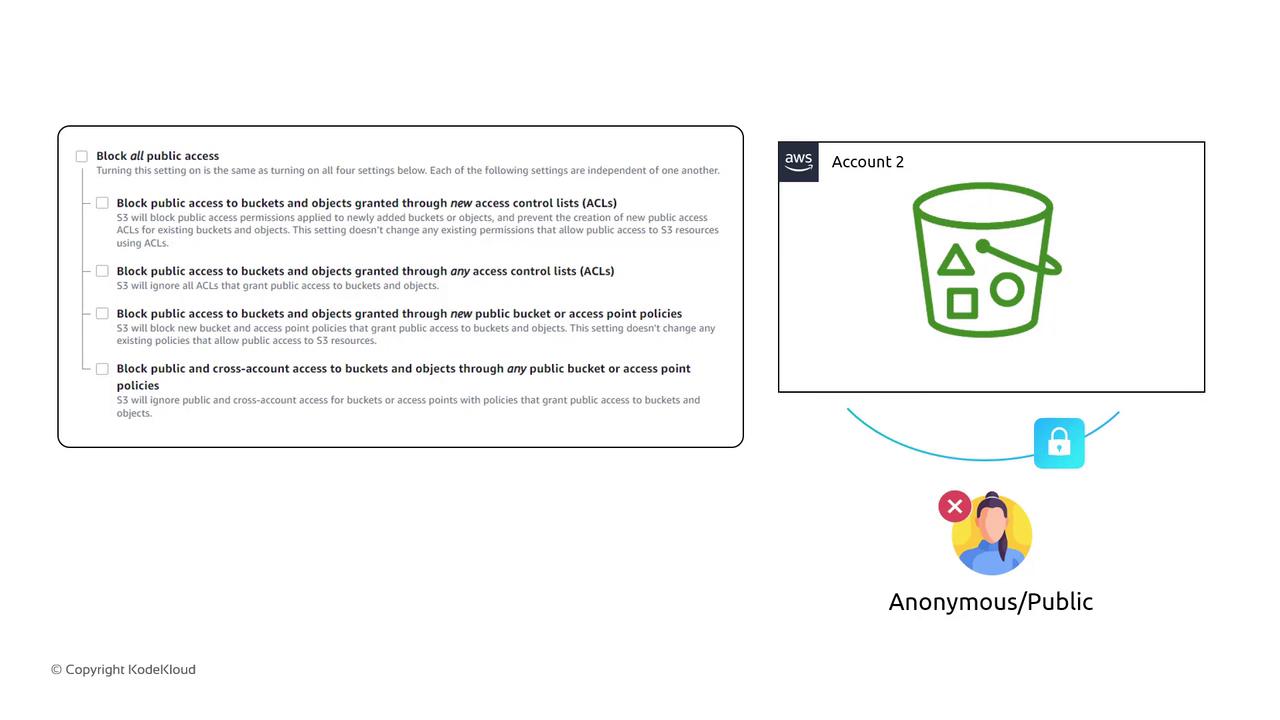
Disabling Block Public Access can expose your data to the internet. Confirm your policies and audit logs before making public.
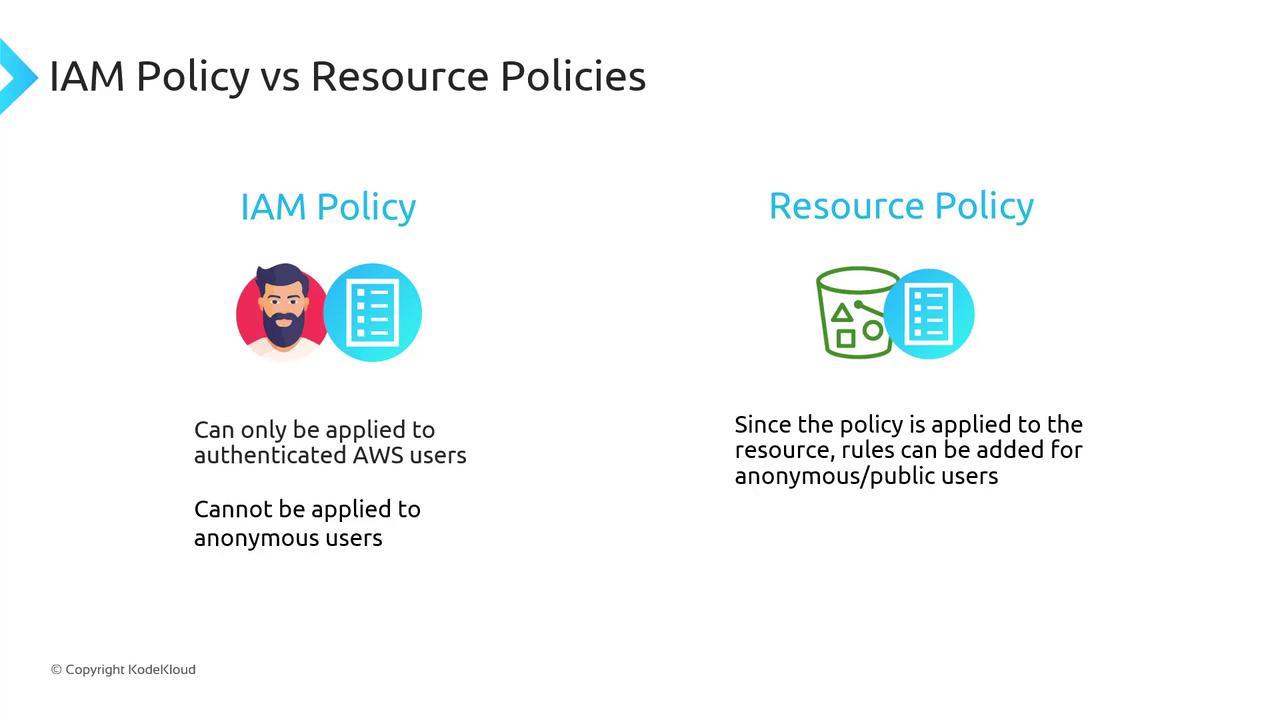
IAM Policies vs. Resource Policies
| Policy Type | Attached To | Scope | Can Include Public |
|---|---|---|---|
| IAM Policy | IAM user, group, or role | Authenticated AWS principals | No |
| Resource Policy | S3 bucket (or other) | Any principal (including anonymous) | Yes |
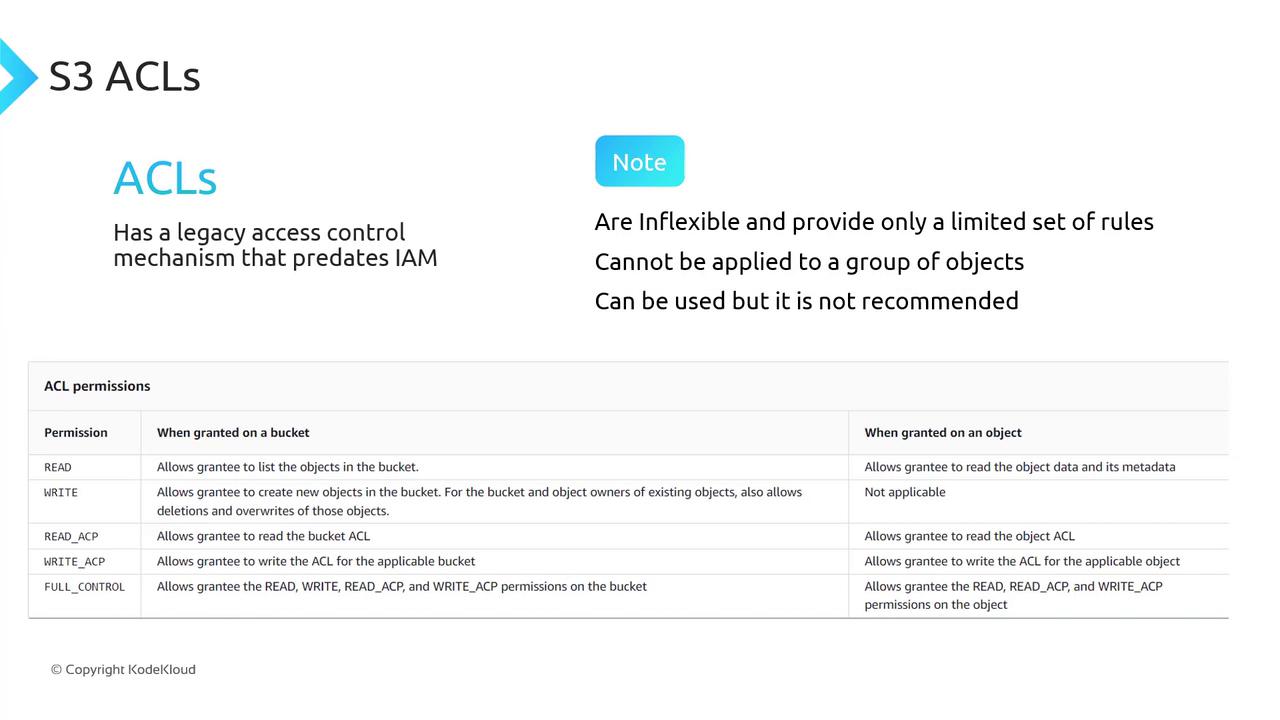
ACLs (Legacy)
S3 ACLs predate IAM and offer only five permission sets:| ACL Permission | Description |
|---|---|
| READ | Read objects |
| WRITE | Write objects |
| READ_ACP | Read bucket ACL |
| WRITE_ACP | Write bucket ACL |
| FULL_CONTROL | Full control (all permissions) |
AWS recommends using IAM policies and bucket policies instead of ACLs for fine-grained access control.
By combining IAM policies, bucket policies, and block public access settings, you can lock down your S3 buckets and grant exactly the permissions your applications need.