- Encrypts traffic with mutual TLS (mTLS) by default
- Authenticates services via CA-issued certificates
- Authorizes interactions through Intentions policies
- Deploys transparently with a Sidecar Proxy or natively via the Consul SDK
Core Concepts
Mutual TLS Certificates
mTLS is the backbone of Consul Service Mesh. A Certificate Authority (CA) issues unique certificates to each service instance, providing:- Authentication: Both client and server validate each other’s certificate against the root CA bundle (“I am who I say I am”).
- Encryption: Standard TLS ensures all data in transit is encrypted without any application code changes.
Consul can serve as a built-in CA or integrate with external CAs such as HashiCorp Vault.
Sidecar Proxy Architecture
In the Sidecar Proxy pattern, every service instance runs alongside a proxy (Envoy by default). This proxy:- Intercepts all inbound and outbound traffic
- Handles mTLS handshakes, routing, and policy enforcement
- Keeps application code unchanged and unaware of mesh mechanics
Key Components of Consul Service Mesh
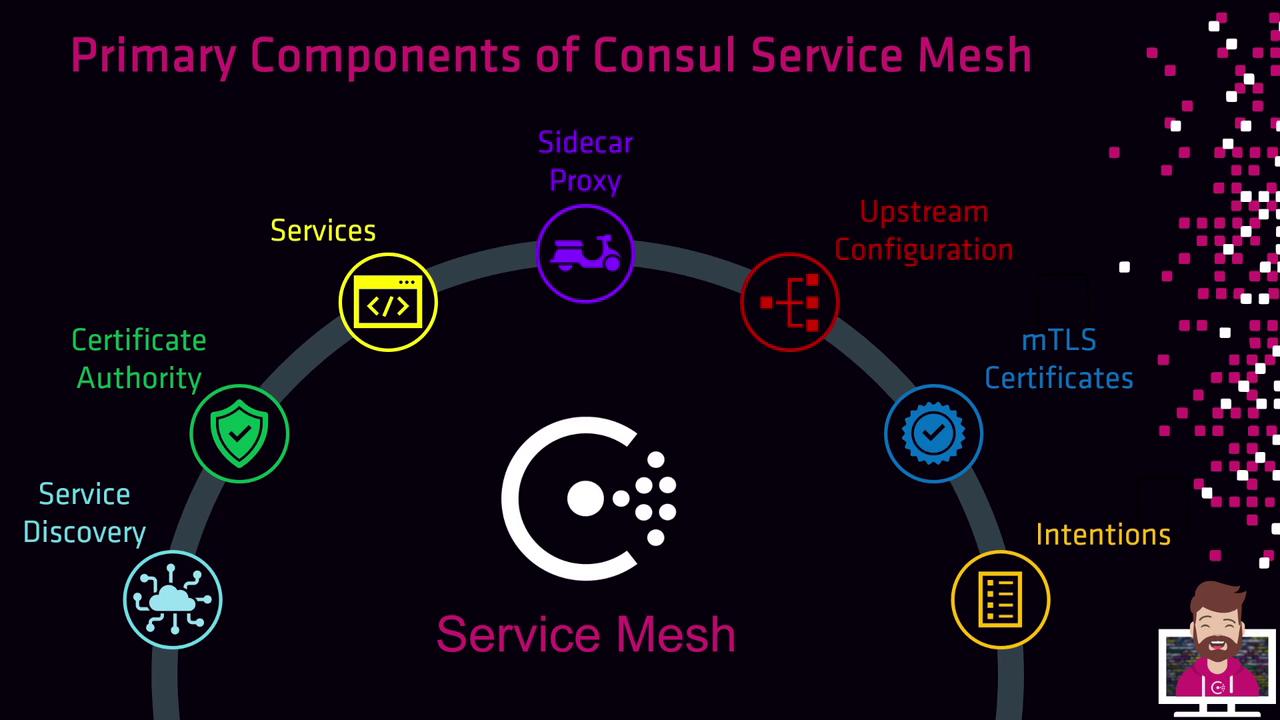
| Component | Purpose | Configuration |
|---|---|---|
| Service Discovery | Registers and catalogs services for dynamic lookup | Built-in registry via consul agent |
| Certificate Authority | Issues and rotates mTLS certificates | Built-in or external CA (Vault) |
| Services | Applications (HTTP, gRPC, TCP) registered with Consul | consul services register |
| Sidecar Proxy | Secures, routes, and enforces policies at the network layer | Envoy (default) or Consul’s built-in proxy |
| Upstream Configuration | Defines service-to-service routing rules | Service defaults in Consul catalog |
| mTLS Certificates | Ensure both authentication and encryption of traffic | Auto-issued by the configured CA |
| Intentions | Allow/Deny policies governing service communication | Defined via HCL, CLI, HTTP API, or UI |
Diving Deeper: mTLS and Intentions

- The CA issues a certificate to each service instance.
- mTLS certificates are deployed to each Sidecar Proxy.
- Intentions validate incoming connections against Consul’s policy store.
- The certificates also encrypt all service-to-service traffic.
Intentions & Sidecar Proxies

- Intentions are top-down Allow/Deny rules configured via CLI, API, or UI.
- A Sidecar Proxy intercepts traffic and enforces mTLS and Intentions.
- Envoy is the most common proxy; you can also use Consul’s built-in proxy or your own custom proxy.
Misconfigured Intentions can inadvertently block critical service communication. Always validate policies in a staging environment before production.
Platform Agnostic & Observability

- Platform Agnostic: Runs on VMs, containers, public cloud, on-prem, and hybrid setups.
- Layer 7 Observability: Proxies capture metrics, traces, and logs—forwardable to Prometheus, Jaeger, and other tools.
- Enable Connect in the agent configuration (
dev-modeon by default; add aconnectstanza in production).
Upstream vs. Downstream
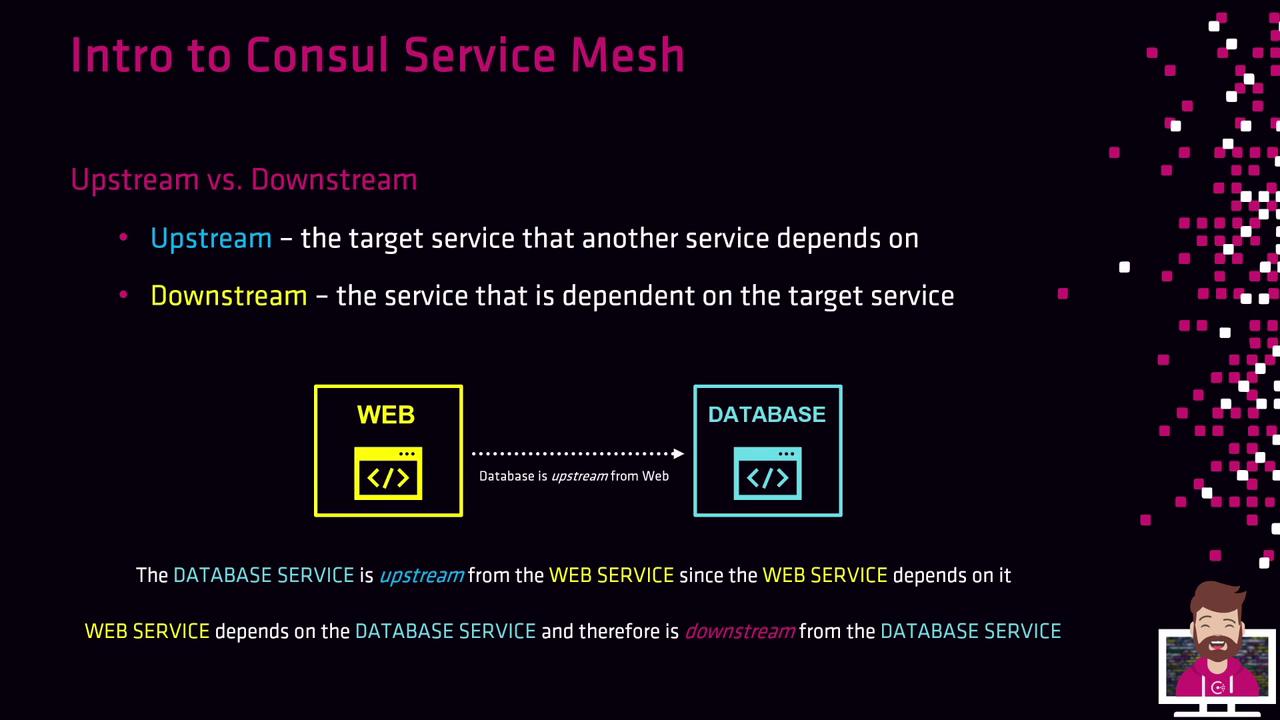
- Upstream: The service your application calls (e.g., a database).
- Downstream: The caller service that relies on an upstream (e.g., a web front end).
High-Level Architecture
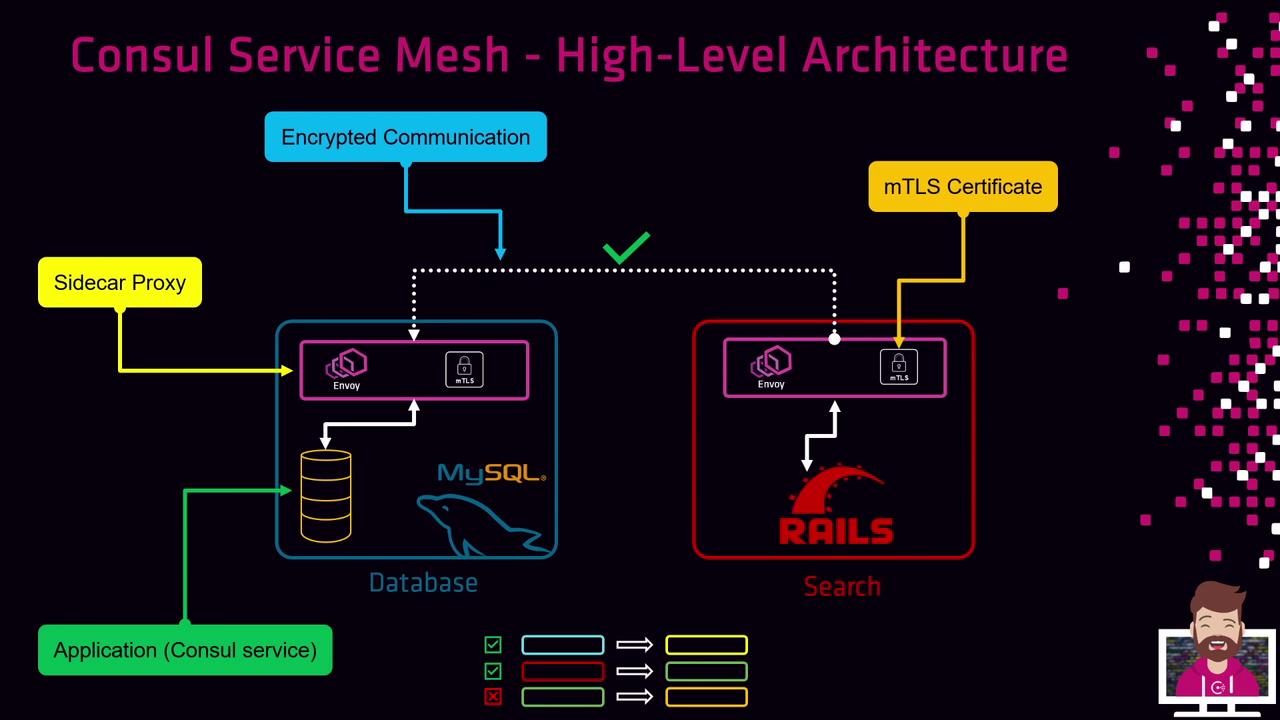
- Each application instance registers with Consul.
- A Sidecar Proxy (Envoy or equivalent) runs alongside the application.
- The proxy presents an mTLS certificate issued by the CA.
- All inter-service traffic is encrypted over mTLS without touching application code.
- Intentions enforce allowed or denied communications.
Service Mesh Workflow
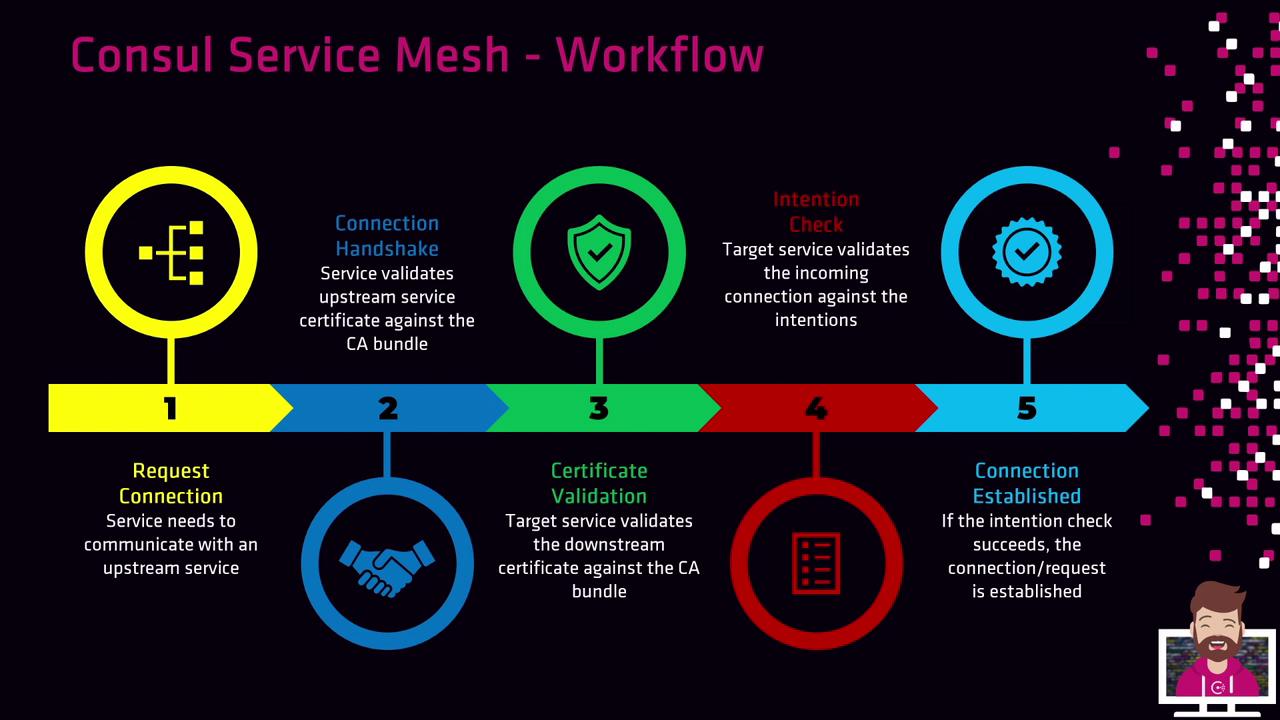
- Request Connection: The source Sidecar Proxy asks for a connection to an upstream service.
- Handshake: Peers perform an mTLS handshake.
- Certificate Validation: Each proxy validates the peer’s certificate against the CA.
- Intention Check: The destination proxy queries Consul for Intentions (Allow/Deny).
- Connection Established: If permitted, traffic flows over an encrypted mTLS channel.
Additional Features

- Layer 7 Traffic Management: Canary, blue/green, and traffic-splitting deployments.
- Service Mesh Gateways:
- Ingress Gateways: Bring external traffic into the mesh.
- Federation Gateways: Connect meshes across datacenters or regions without private networks.
- Terminating Gateways: Streamline traffic routing in Kubernetes.
- Topology Visualizations: Live service maps in Consul UI (v1.9+).