Table of Contents
- Service Connections
- Personal Access Tokens (PATs)
- Service Connections vs. Personal Access Tokens
- Security Best Practices
- References
Service Connections
Service Connections in Azure DevOps let pipelines and services authenticate with external resources—such as Azure Subscriptions, Docker registries, GitHub, and more—without embedding secrets directly in your YAML definitions.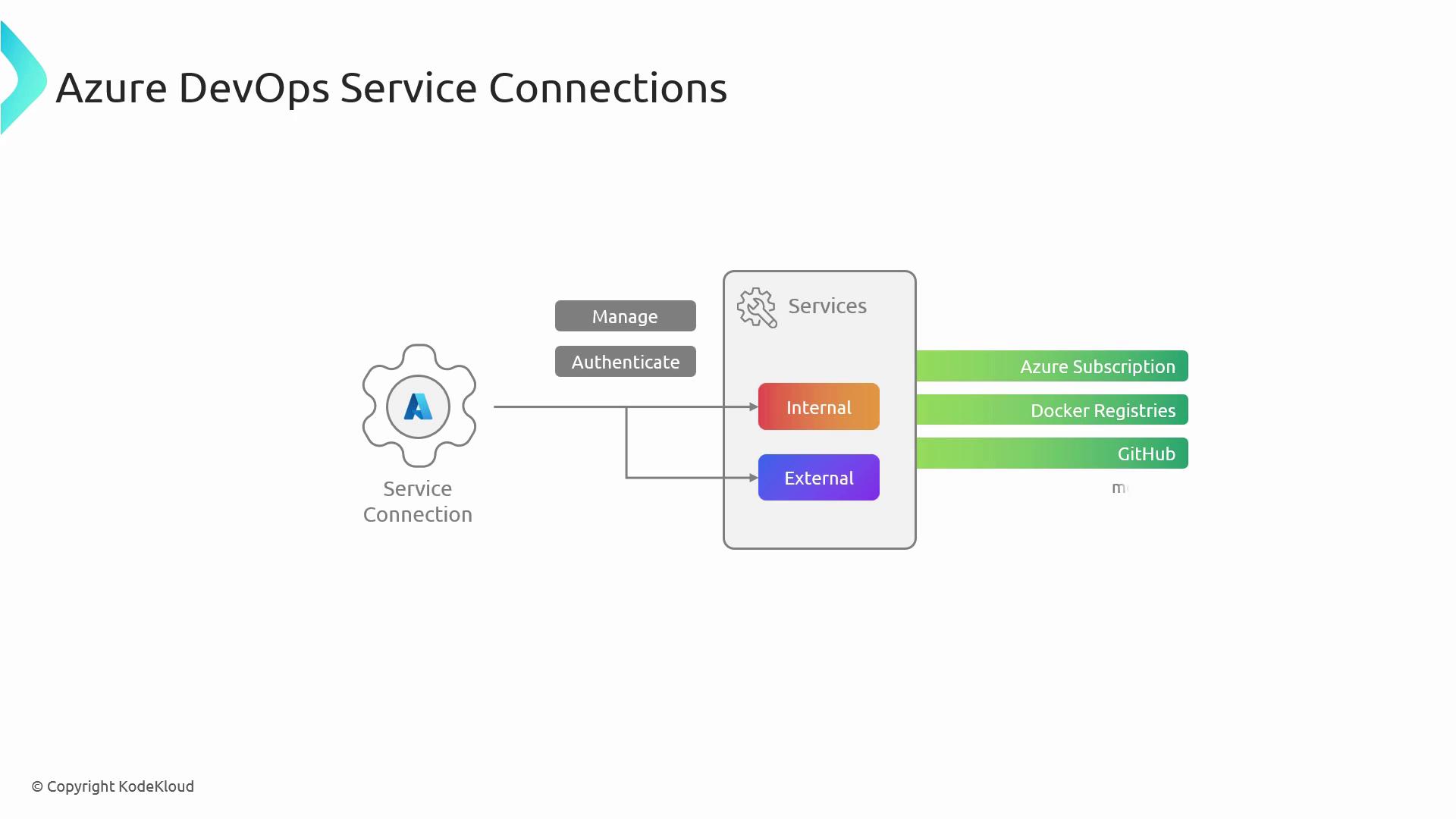
Benefits
- Centralized credential management for all pipelines
- Simplified service authentication in YAML and classic pipelines
- Improved security posture with scoped access
Creating a Service Connection
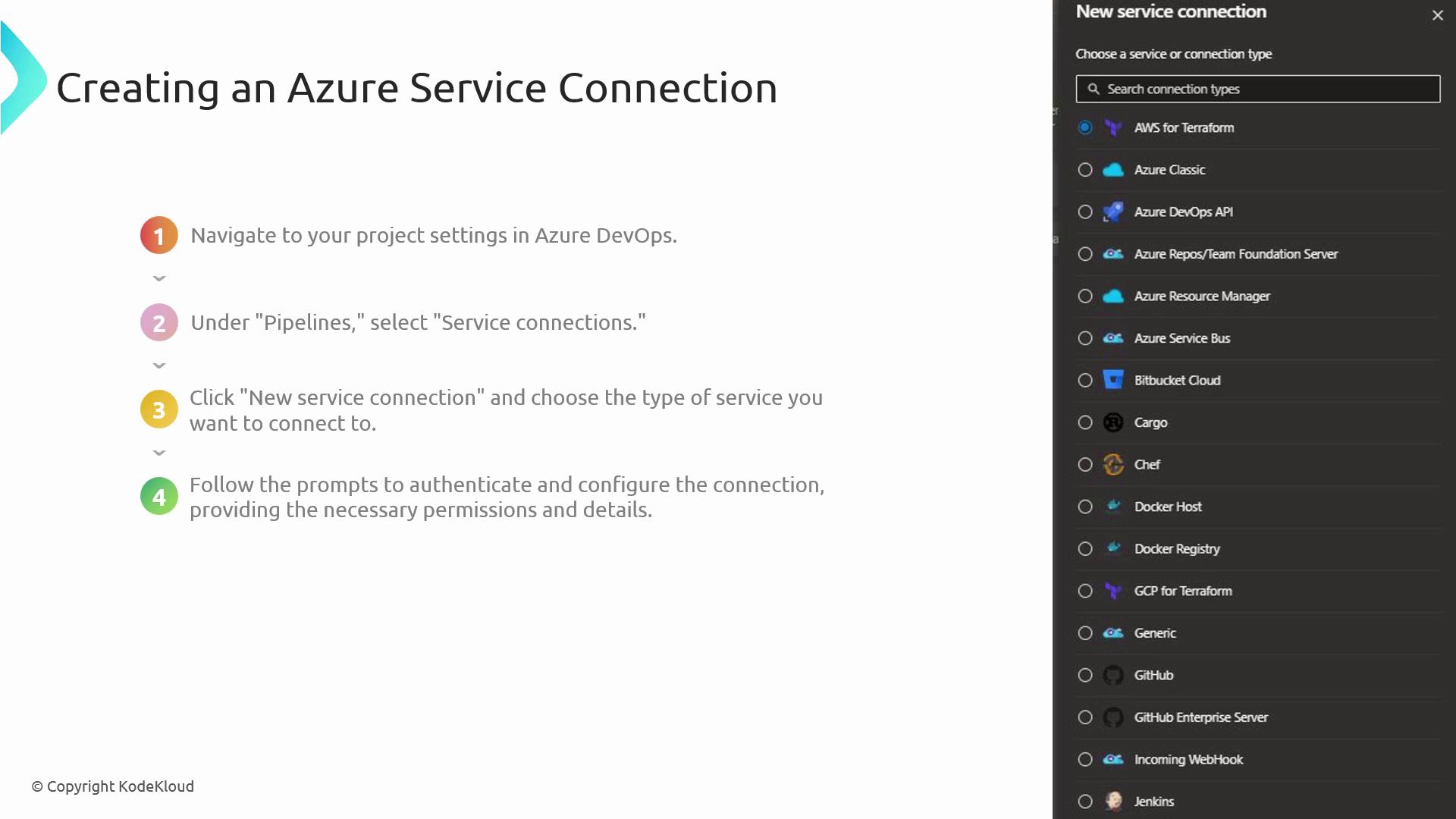
- Navigate to Project Settings in your Azure DevOps project.
- Under Pipelines, select Service connections.
- Click New service connection and pick the desired type (e.g., Azure Resource Manager, Docker Registry).
- Complete the authentication prompts and grant the necessary permissions.
- Save the service connection and reference its name in your pipeline YAML.
The AZ-400 certification exam often tests your ability to walk through these steps. Practice creating and referencing service connections in sample pipelines.
Managing Service Connections
- Edit or Update: Go to Service connections, select the connection, update settings, and save.
- Delete: Select the connection and click Delete (project administrator permissions required).
Personal Access Tokens (PATs)
Personal Access Tokens (PATs) are OAuth-like tokens used to access Azure DevOps REST APIs. They are perfect for automation scripts, third-party integrations, and CLI operations.
Generating a PAT
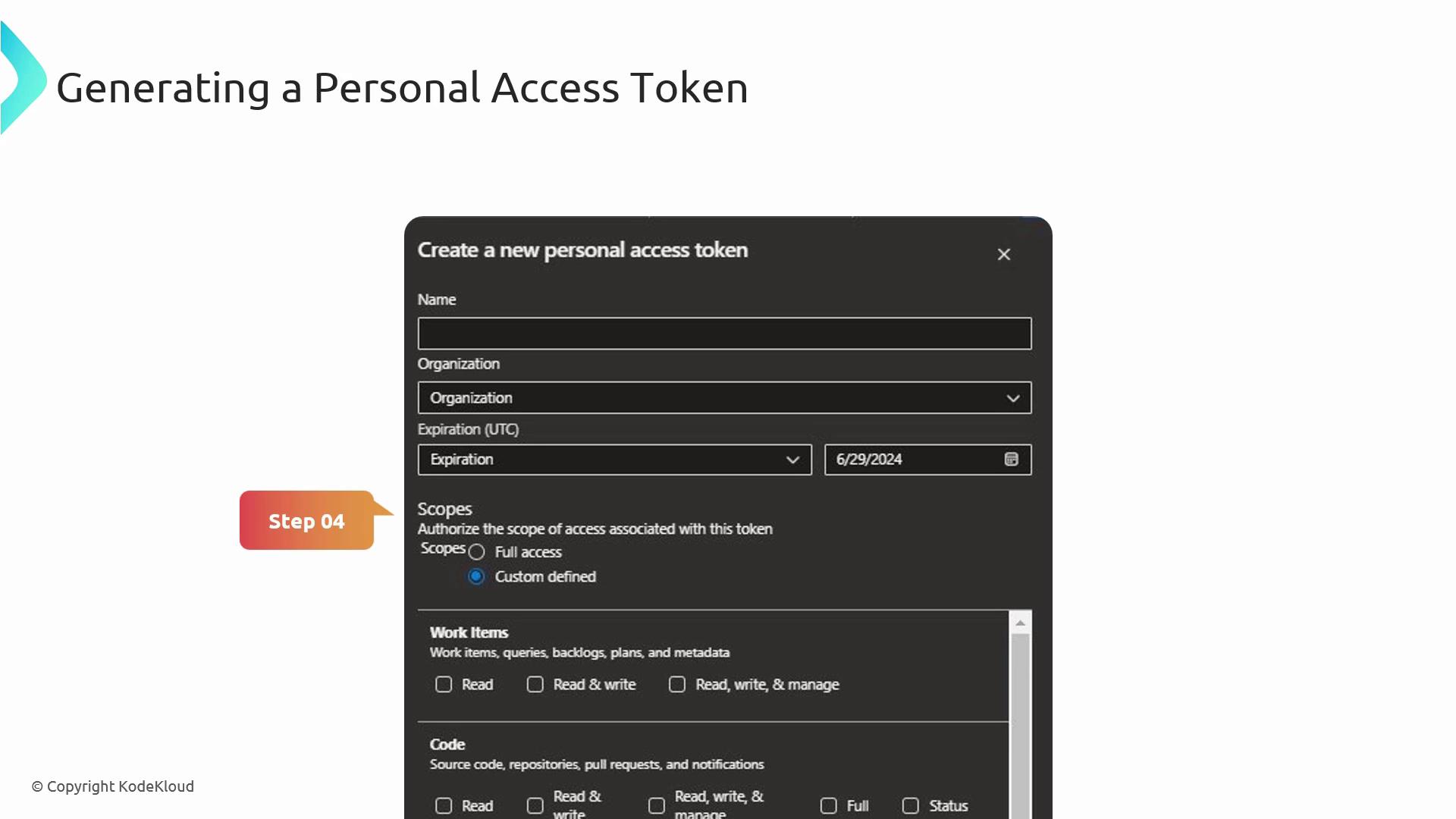
- Open your Azure DevOps profile and choose Personal Access Tokens.
- Click New Token, enter a descriptive name, set an expiration date, and select only the scopes you need (e.g., Code (read/write), Work items (read/write)).
- Click Create, then copy and store the token securely.
Treat PATs like passwords. Store them in a secure vault and never check them into source control.
Using PATs with cURL
Use your PAT in theAuthorization header to interact with the Azure DevOps REST API:
Using PATs with Python
Below is a Python script that creates a work item via the REST API usingrequests and HTTPBasicAuth:
Service Connections vs. Personal Access Tokens
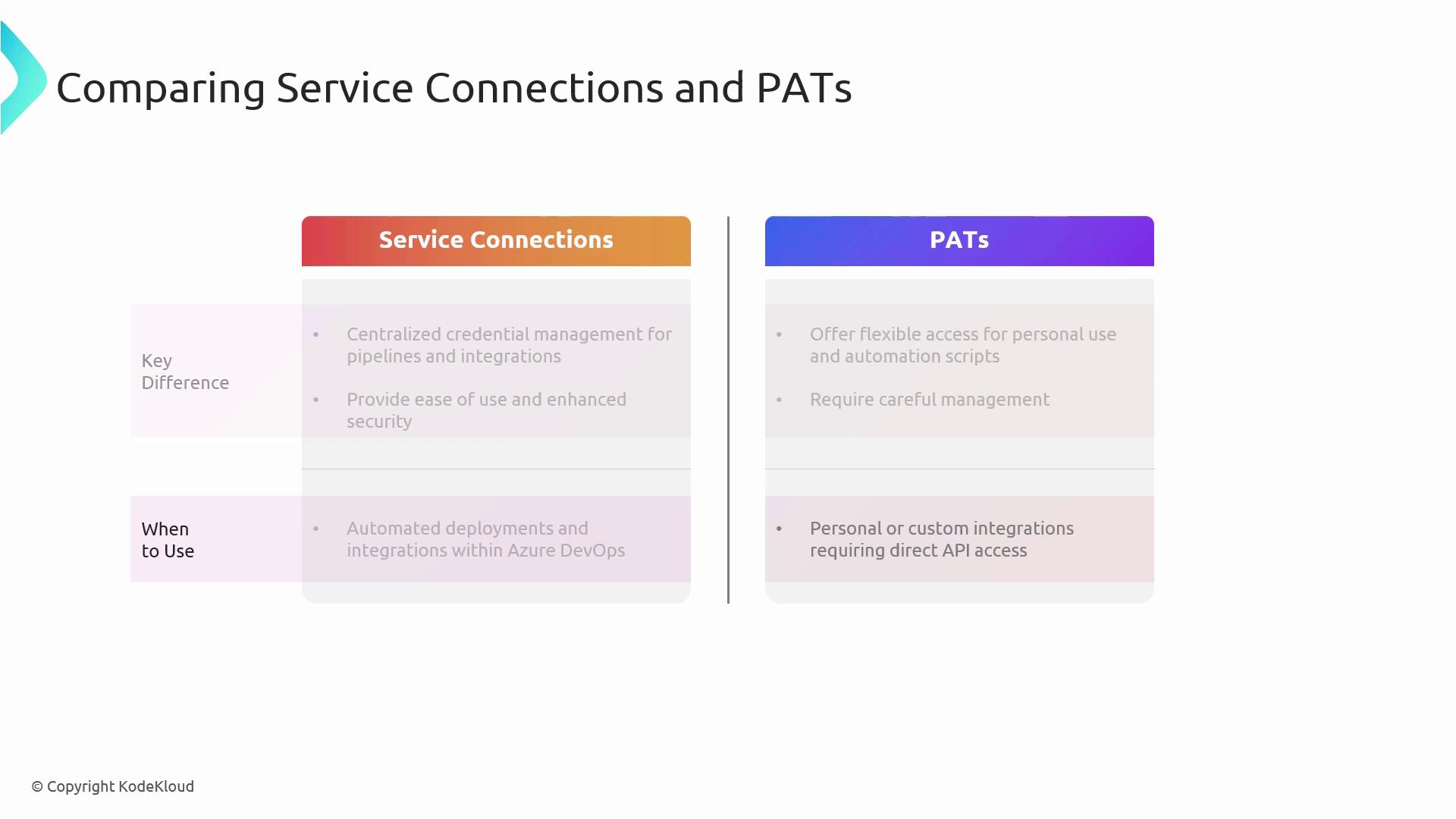
| Feature | Service Connections | Personal Access Tokens (PATs) |
|---|---|---|
| Management | Centralized in Project Settings | Decentralized per user profile |
| Use Case | Pipelines, deployments, managed identities | CLI scripts, REST API calls, third-party integrations |
| Security Scope | Scoped at resource level, supports managed identities | Scopes defined per token, manual rotation required |
| Recommended for | Automated deployments and pipeline orchestration | Personal automation and ad-hoc API interactions |
Security Best Practices
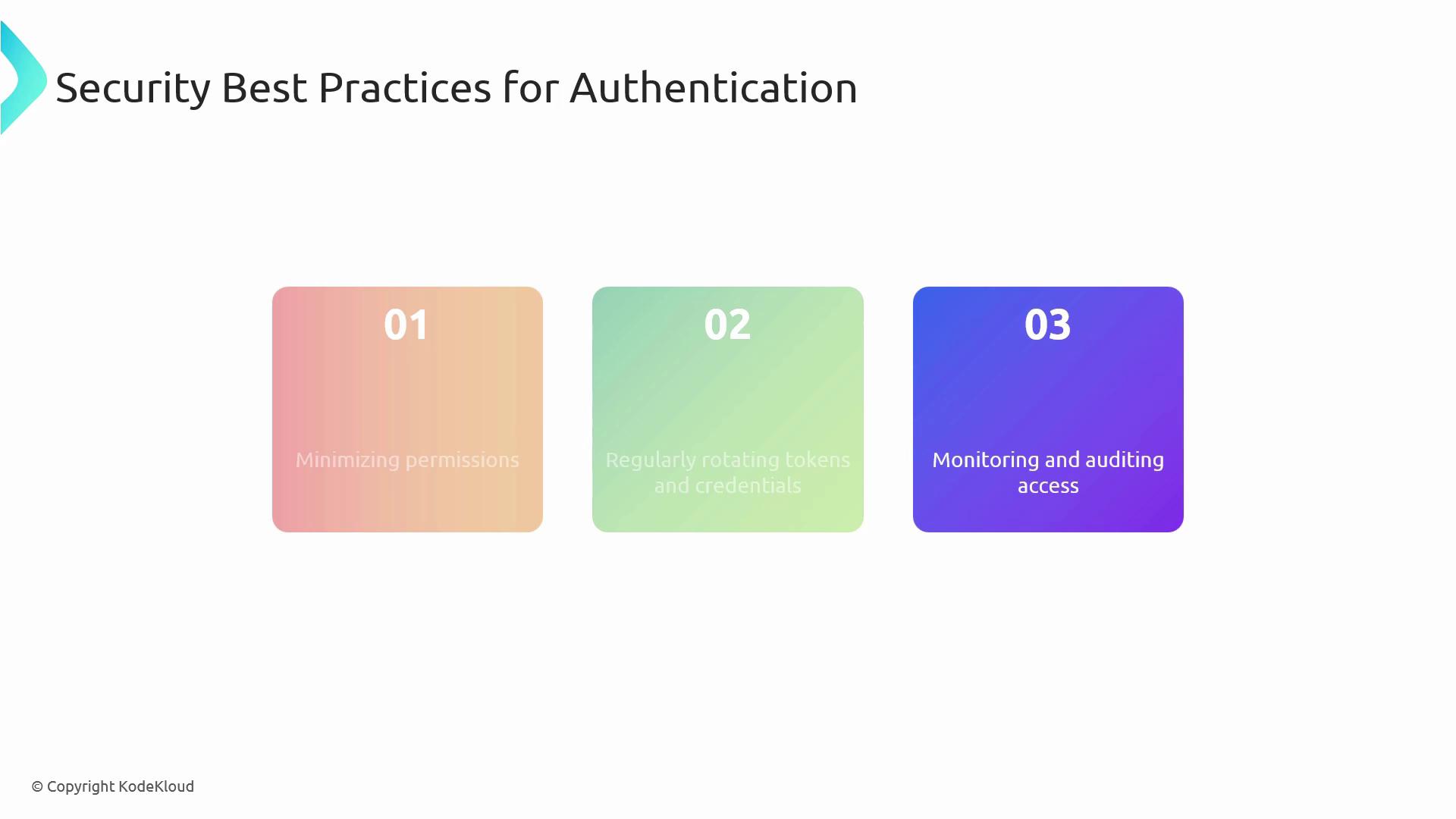
- Grant least privilege on both service connections and PATs.
- Rotate tokens and credentials regularly to reduce exposure.
- Monitor and audit logs for unauthorized access attempts.
- Enforce Multi-Factor Authentication (MFA) and conditional access policies.