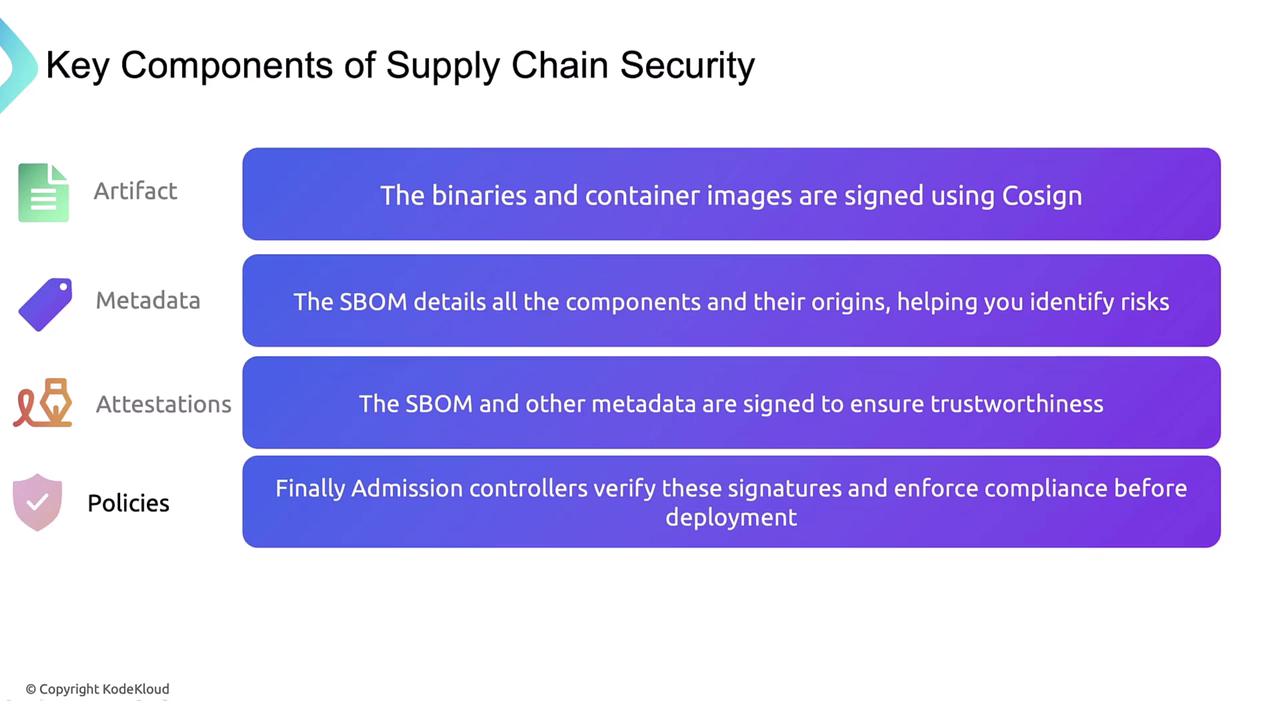
Core Areas of Supply Chain Security
| Core Area | Description | Tool / Standard |
|---|---|---|
| Artifacts | Build outputs: images, binaries | Sigstore Cosign |
| Metadata | Software Bill of Materials (SBOM) | SPDX |
| Attestations | Signed provenance statements | in-toto |
| Policies | Automated compliance enforcement | Sigstore Policy Controller |
1. Artifacts: Signing and Verification
Artifacts—your container images, binaries, and libraries—must be signed to prove integrity and origin.Sigstore’s Cosign offers a simple, keyless workflow for signing container images.
2. Metadata: Generating and Validating SBOMs
A Software Bill of Materials (SBOM) is an “ingredients list” for your application, detailing file checksums, licenses, and origins.An SBOM (Software Bill of Materials) is often authored in SPDX format. It tracks every component and its license.
3. Attestations: Building a Chain of Trust
Attestations are cryptographic statements that vouch for metadata such as provenance, SBOM authenticity, or vulnerability scans. Sign an SBOM attestation:in-toto defines and verifies attestations across your entire pipeline. Sample step definition:
4. Policies: Automated Compliance Enforcement
Policies block deployments of unsigned or non-compliant artifacts. AClusterImagePolicy example: