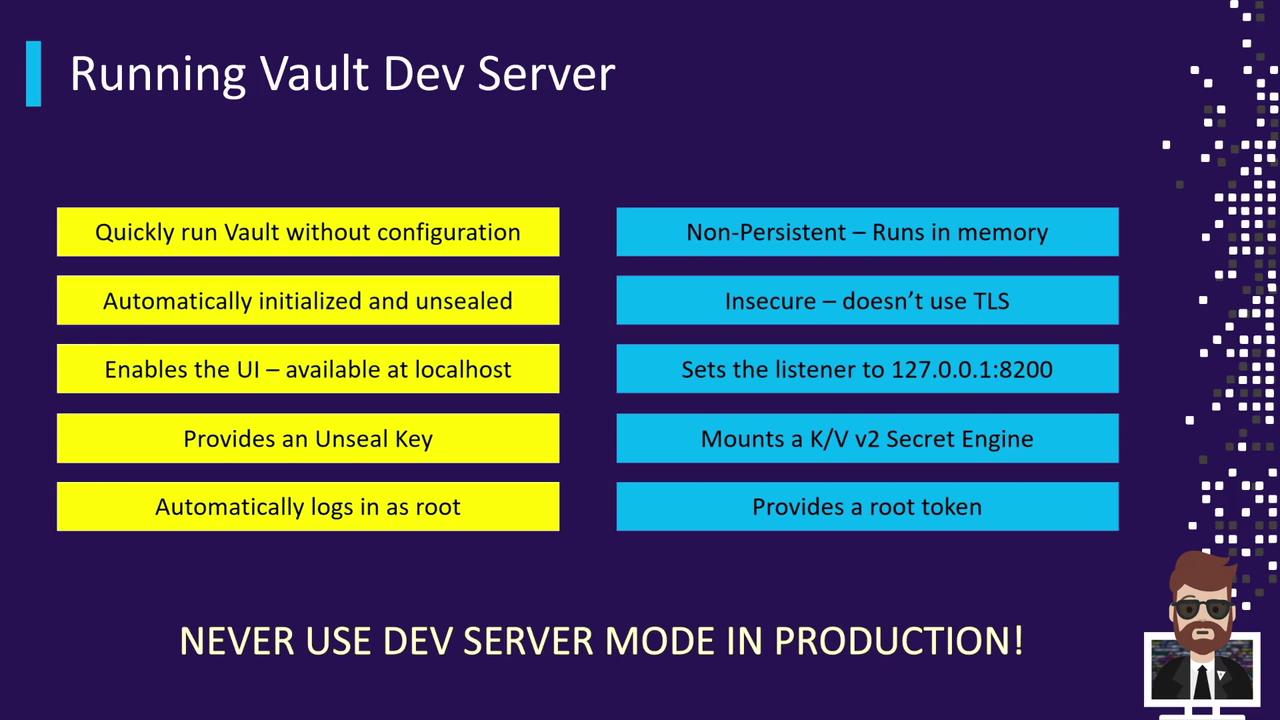
Vault Dev Server skips all security controls.
- Data is lost when the process stops.
- All traffic is unencrypted.
Never use Dev Server in a production or sensitive environment.
Dev Server Features
| Feature | Description |
|---|---|
| Auto-initialized & unsealed | Vault comes up ready to use without manual setup |
| Built-in UI | Accessible at http://127.0.0.1:8200 |
| Provides a root token | Displayed in the startup logs |
| In-memory storage | Non-persistent; all data is lost when Vault stops |
| No TLS | All API calls and UI traffic are in clear text |
Default KV v2 Secrets Engine at secret/ | Pre-mounted for immediate key/value operations |
| Single authentication method | Root token only; no additional auth backends enabled by default |
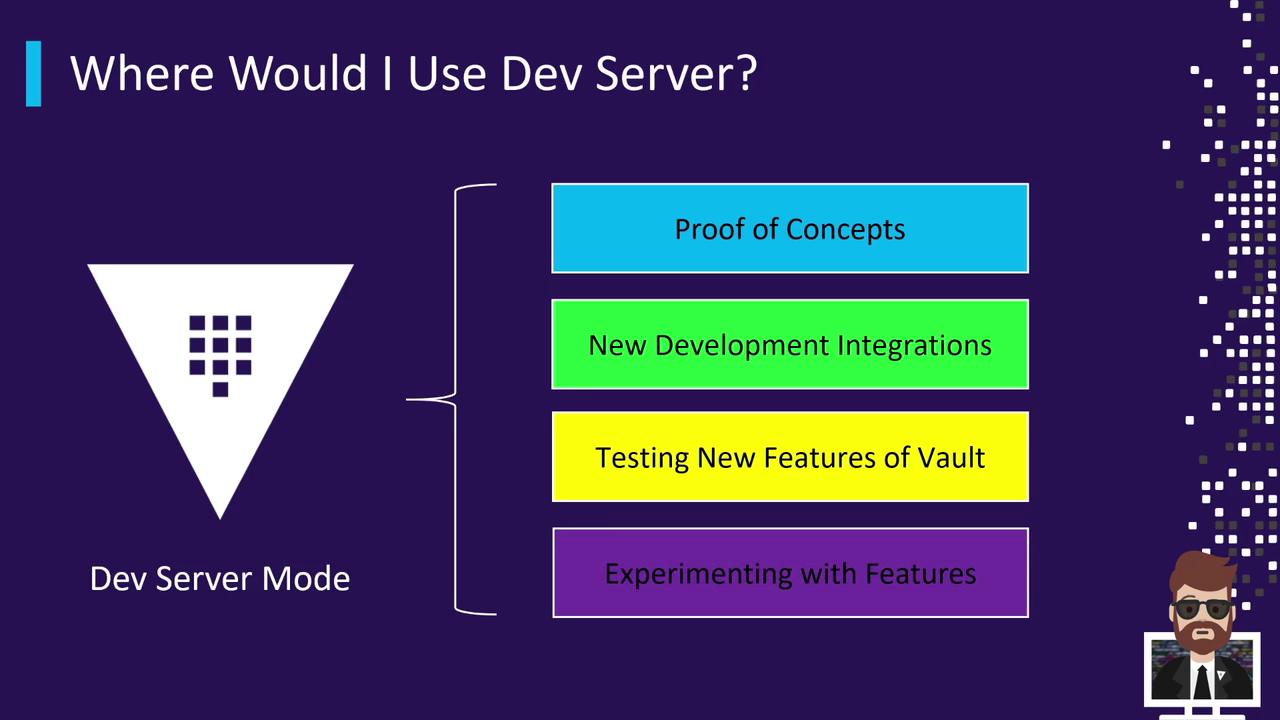
When to Use Dev Server
Vault Dev Server is perfect for:- Proof-of-concepts (POCs) for secret management
- Testing new Vault features or upgrades
- Developing CI/CD integrations (e.g., with Jenkins)
- Exploring unfamiliar secrets engines
Launching the Dev Server
Assuming thevault binary is on your PATH, open a terminal (or PowerShell on Windows) and execute:
Before running additional commands, point your shell to the Dev Server:
Verify Vault Status
Confirm that Vault is unsealed and running:Next Steps
- Authenticate
Use the root token from the startup log: - Mount & Test Secrets Engines
For example, enable a new KV engine atkv-data/: - Cleanup
When you’re done, terminate the Vault process. All in-memory data will be discarded.