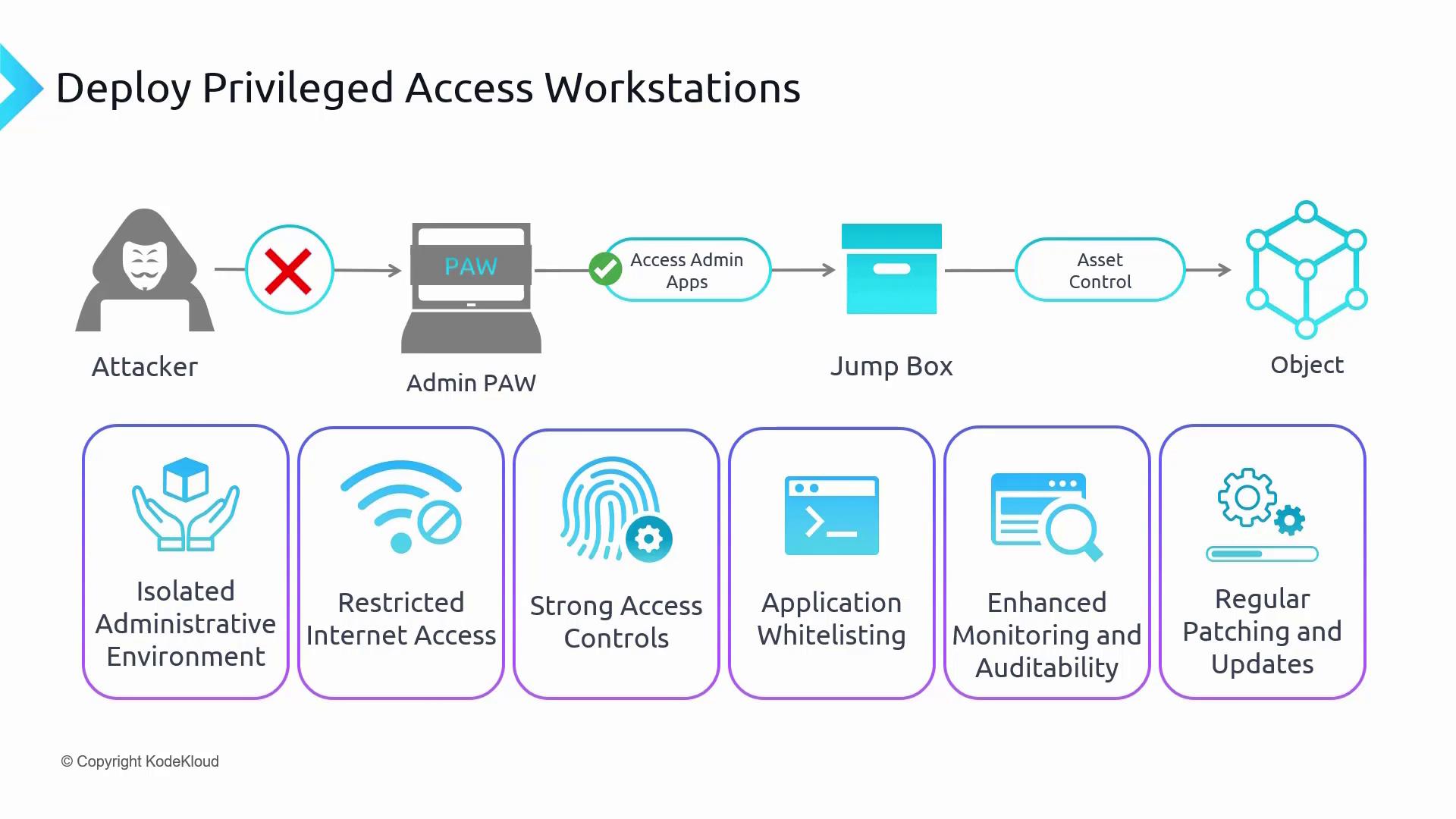
In practice, a POS serves as a remote client to a hardened Tier 0 terminal or jump box, where sensitive administrative tasks are executed. The terminal server or jump box is accessible exclusively via PADs, ensuring that both security and scalability are maintained while defending against physical and cyber threats.
-
Isolated Administrative Environment
PADs are designated solely for critical tasks and are used only by authorized personnel. Since they are not intended for routine activities—like accessing social media—they significantly reduce the risk of spreading security threats. -
Restricted Internet Access
Internet capabilities on these workstations are either severely curtailed or entirely blocked. This measure protects against online threats, including potentially harmful websites and phishing scams. -
Strong Access Controls
Robust security measures, including multi-step verification and strict password policies, regulate access to PADs. This ensures that only authorized users can log in, dramatically reducing the chances of unauthorized access. -
Application Whitelisting
Only pre-approved applications are permitted to run on PADs. This whitelist approach prevents non-essential or insecure software (such as games) from executing, thereby shielding the workstation from malware and other application-based threats. -
Enhanced Monitoring and Auditability
Continuous monitoring and comprehensive logging are integral components of PADs. Detailed logs of all activities not only aid in investigating security issues but also ensure compliance with organizational policies and regulatory requirements. -
Regular Patching and Updates
Routine updates and timely security patches maintain PAD integrity. These practices ensure that workstations are well-prepared to mitigate new and emerging cyber threats.