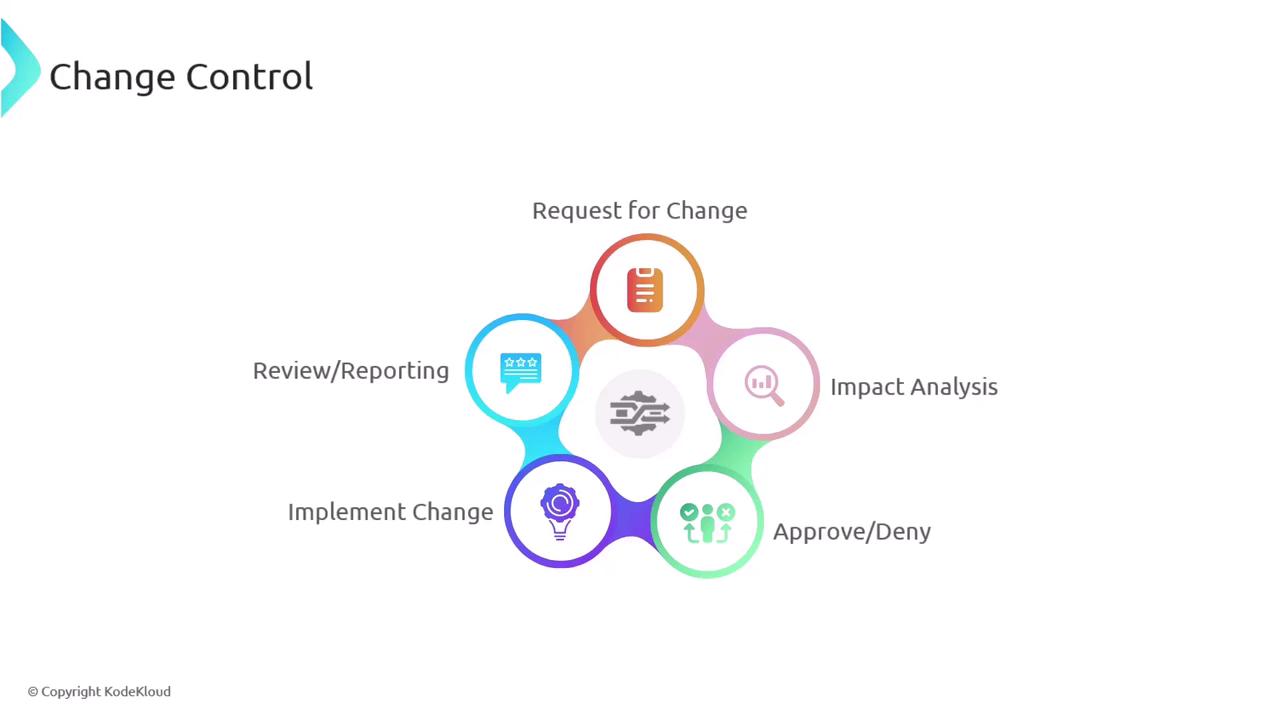

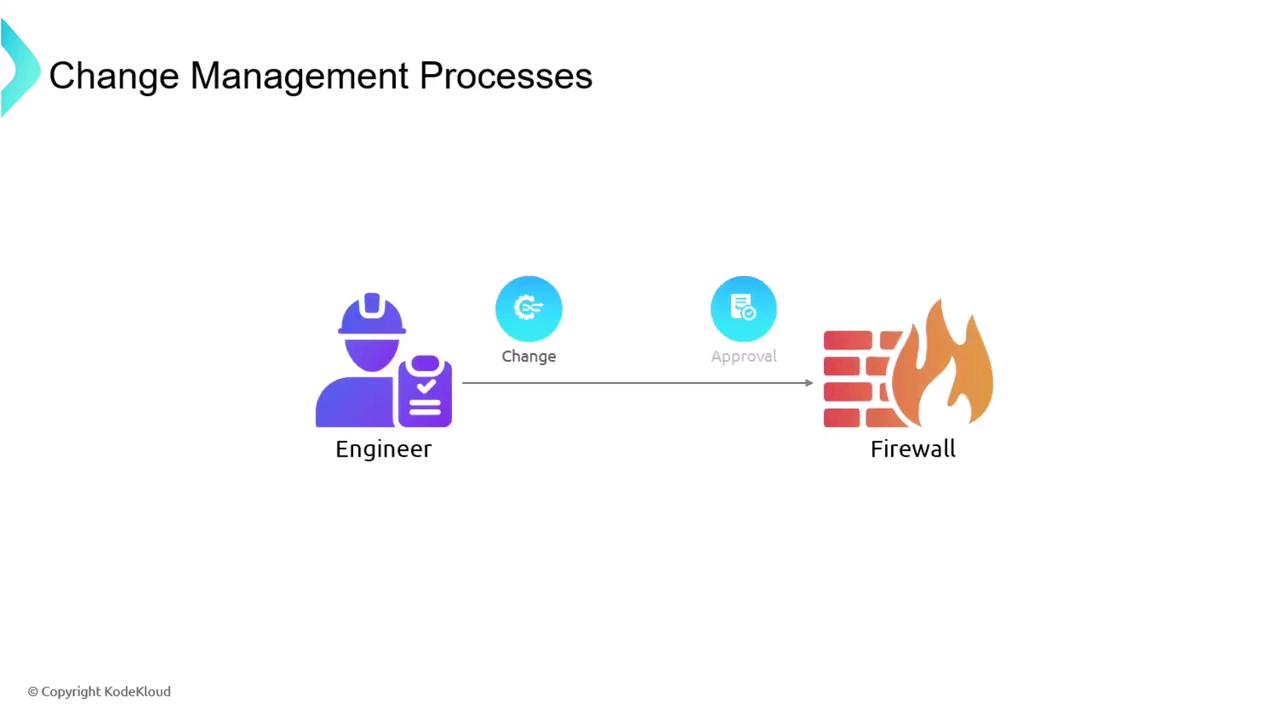
During change management meetings, requesters are often asked to provide supporting documentation such as updated diagrams, revised policies, or new procedures. Common steps in the process include:
- Obtaining necessary approvals
- Communicating with stakeholders
- Submitting impact analyses
- Presenting test results
- Proposing backup plans for risk mitigation
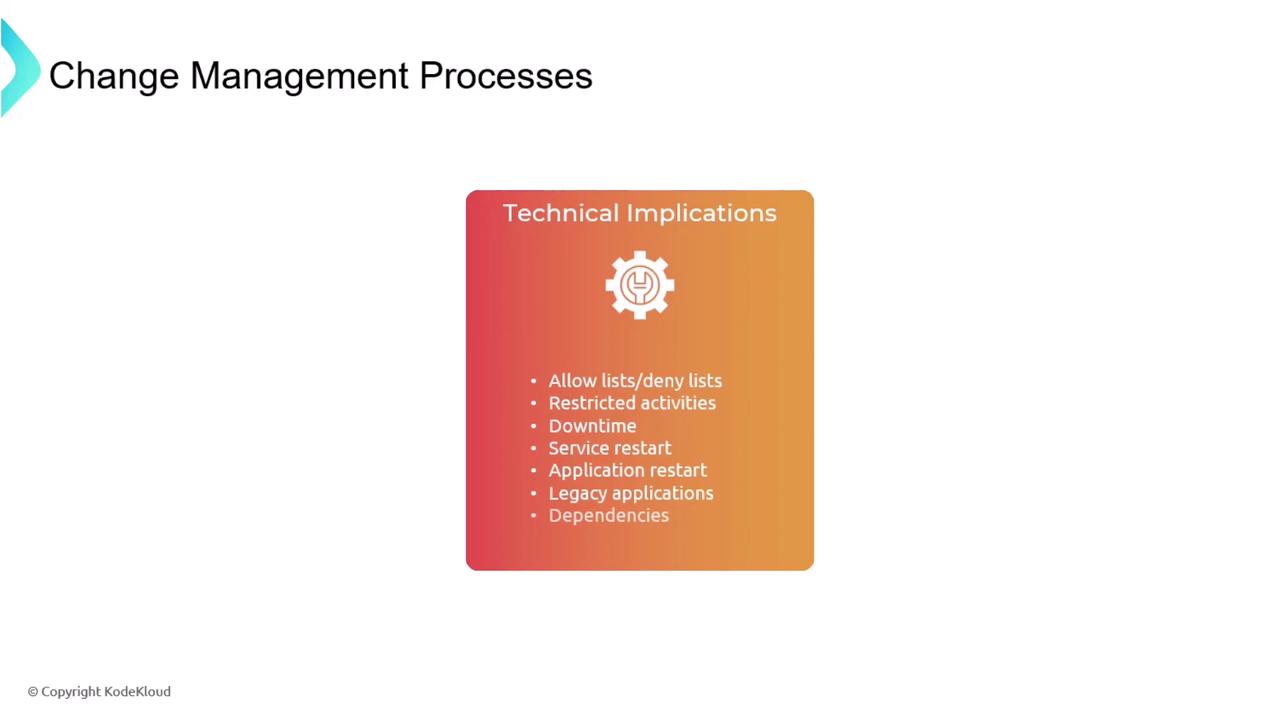
- Will the implementation require downtime?
- Is a service restart necessary?
- Are there dependencies that could impact other applications?
- An overview of security controls and their importance
- The definition and significance of control categories and types
- The critical role of physical security measures
- The importance of the Confidentiality, Integrity, and Availability (CIA) triad in safeguarding data
- Additional concepts such as non-repudiation, honeypots, and key elements of Zero Trust
- Detailed insights into change management processes and their technical implications
