

Mandatory Access Control (MAC)
In a MAC system, access is enforced by the operating system based on a set of predefined policies determined by an administrator. Users cannot modify these policies. Files and resources receive security labels (e.g., top secret or confidential), and access is granted based on the user’s security clearance. This centralized approach ensures robust security.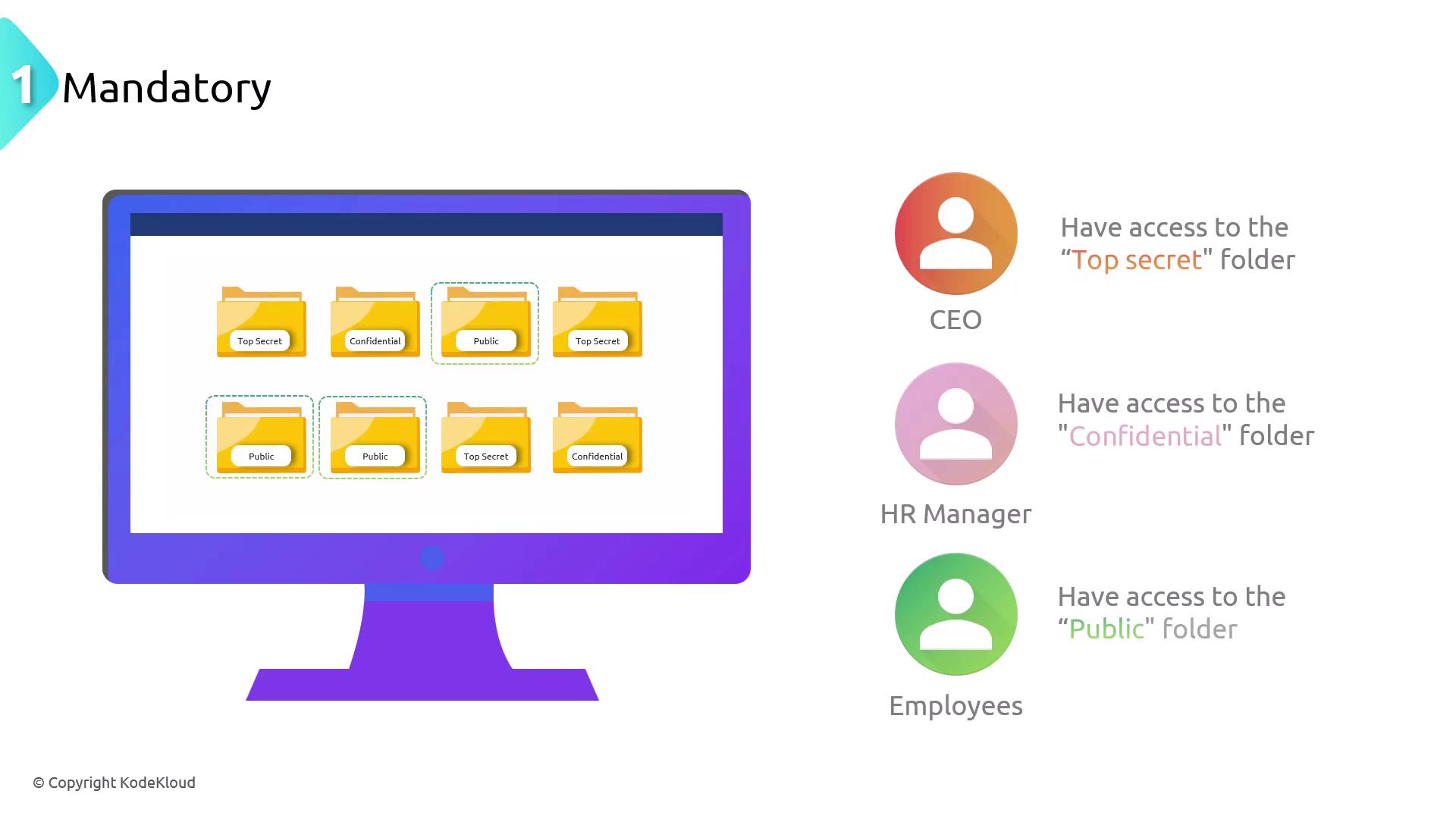
Discretionary Access Control (DAC)
DAC allows resource owners to manage access permissions. In this model, the owner sets the permissions, providing flexibility especially in personal or commercial computing environments. An example is when a Windows file owner grants specific read or write permissions to individual users or groups.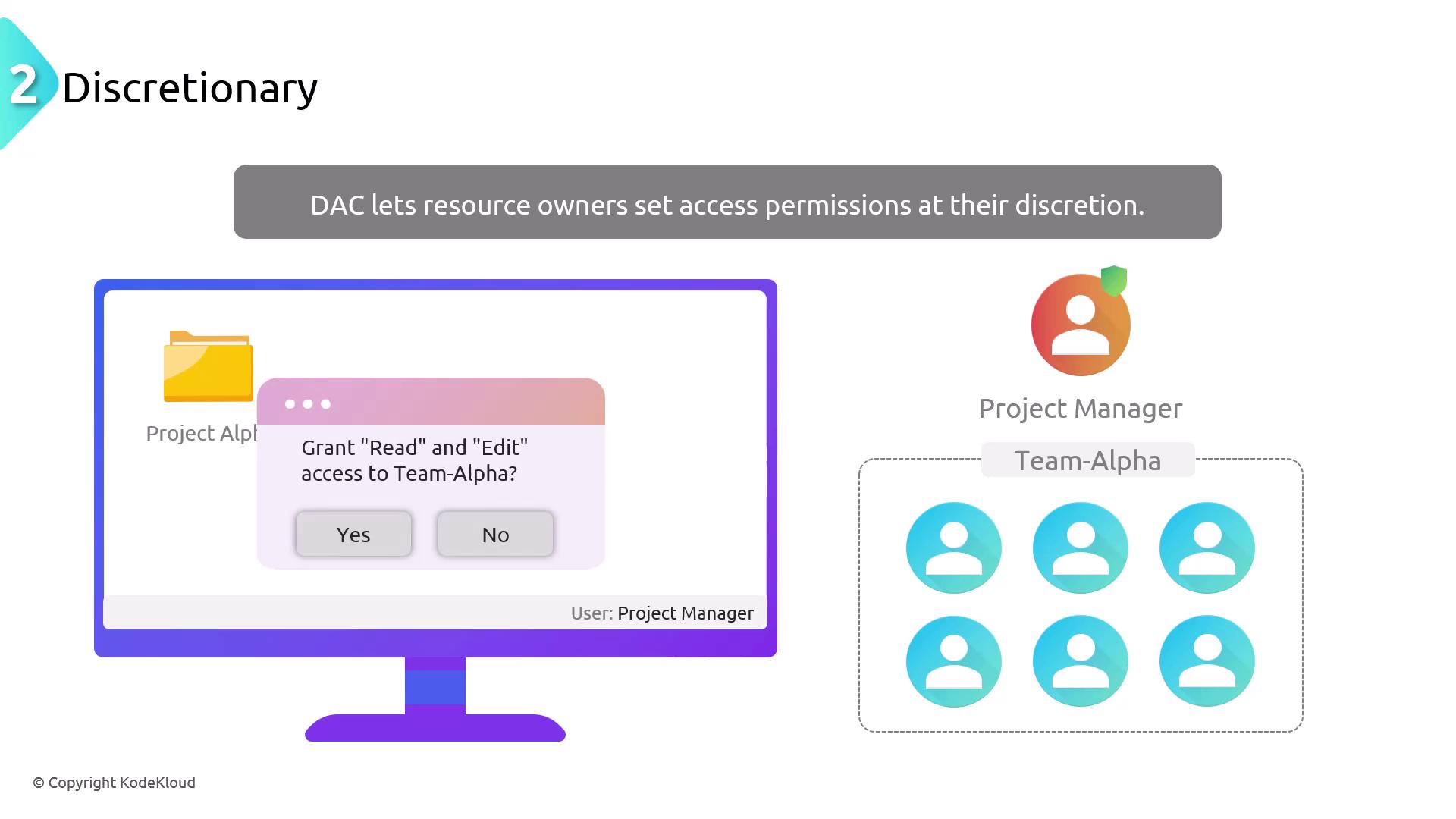
Role-Based Access Control (RBAC)
RBAC assigns permissions to users based on their roles within an organization. This method simplifies large-scale access management by granting permissions that align with job responsibilities and functions.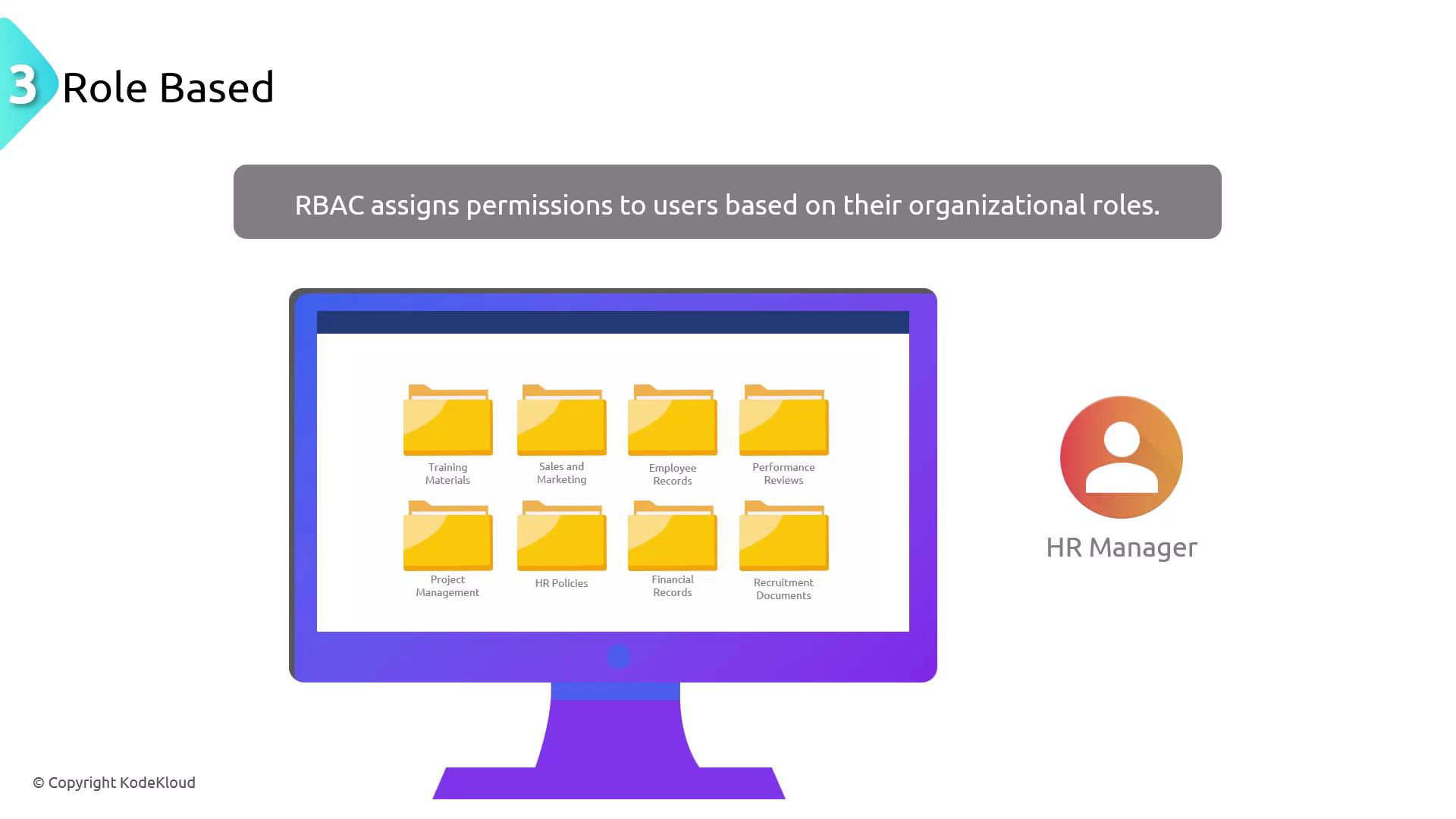
Rule-Based Access Control
Rule-based access control relies on predefined rules to determine access permissions based on conditions such as time, location, or other specific factors. This dynamic method allows decisions to adapt to changing environmental conditions, such as restricting access outside of business hours or from unauthorized IP addresses.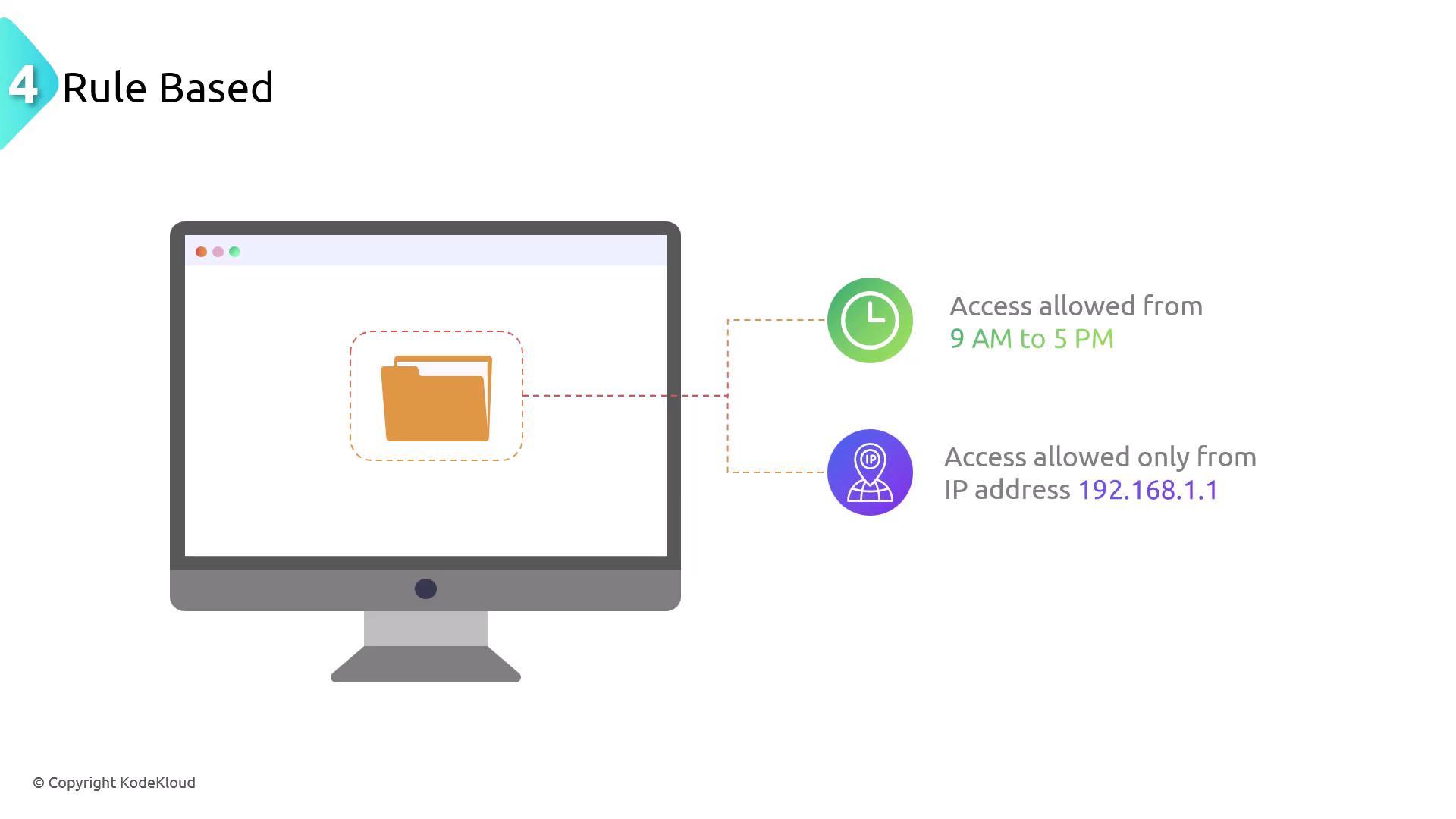
Attribute-Based Access Control (ABAC)
ABAC uses distinct attributes of users, resources, and the environment to make nuanced access decisions. Attributes like user roles, resource types, and access time enable fine-grained control that can be tailored to specific scenarios. For example, access to a resource may depend on a combination of a user’s department, role, and the time of access.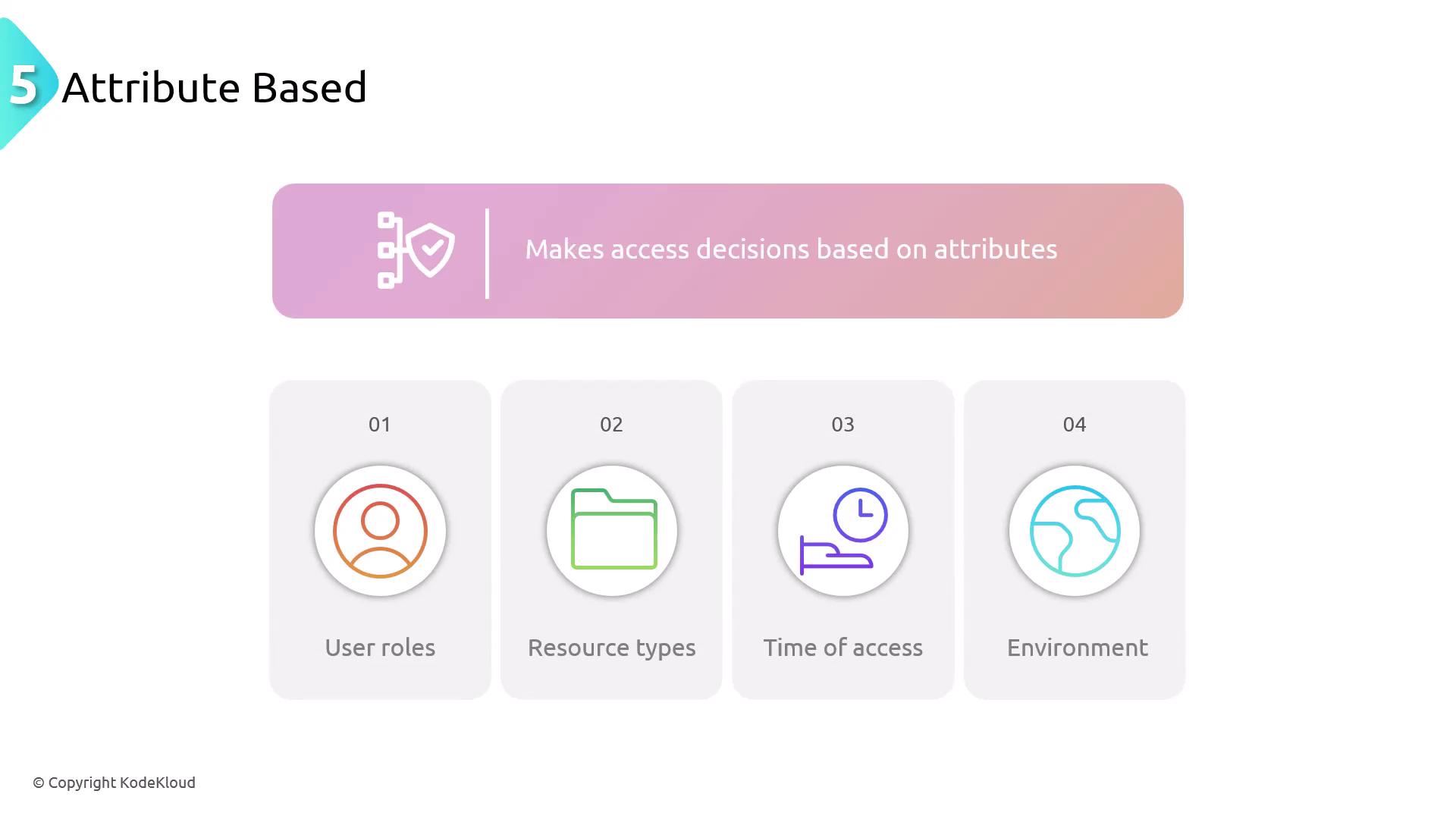
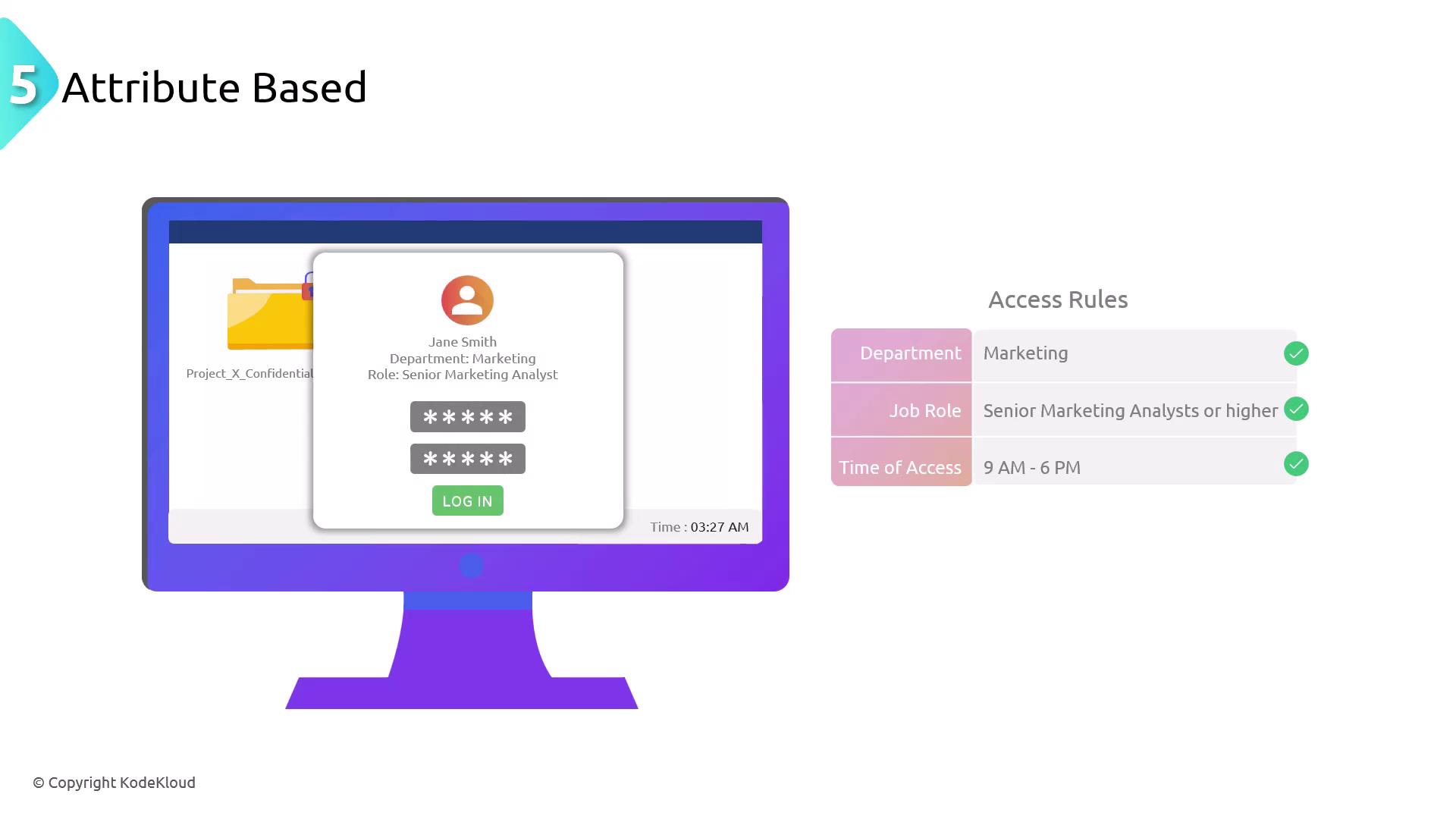
Implementing the right access control model is vital for safeguarding sensitive data and ensuring compliance with security regulations. Choosing the appropriate model depends on an organization’s specific needs.