Monitor these indicators continuously and update your threat intelligence strategies to stay ahead of emerging security challenges.
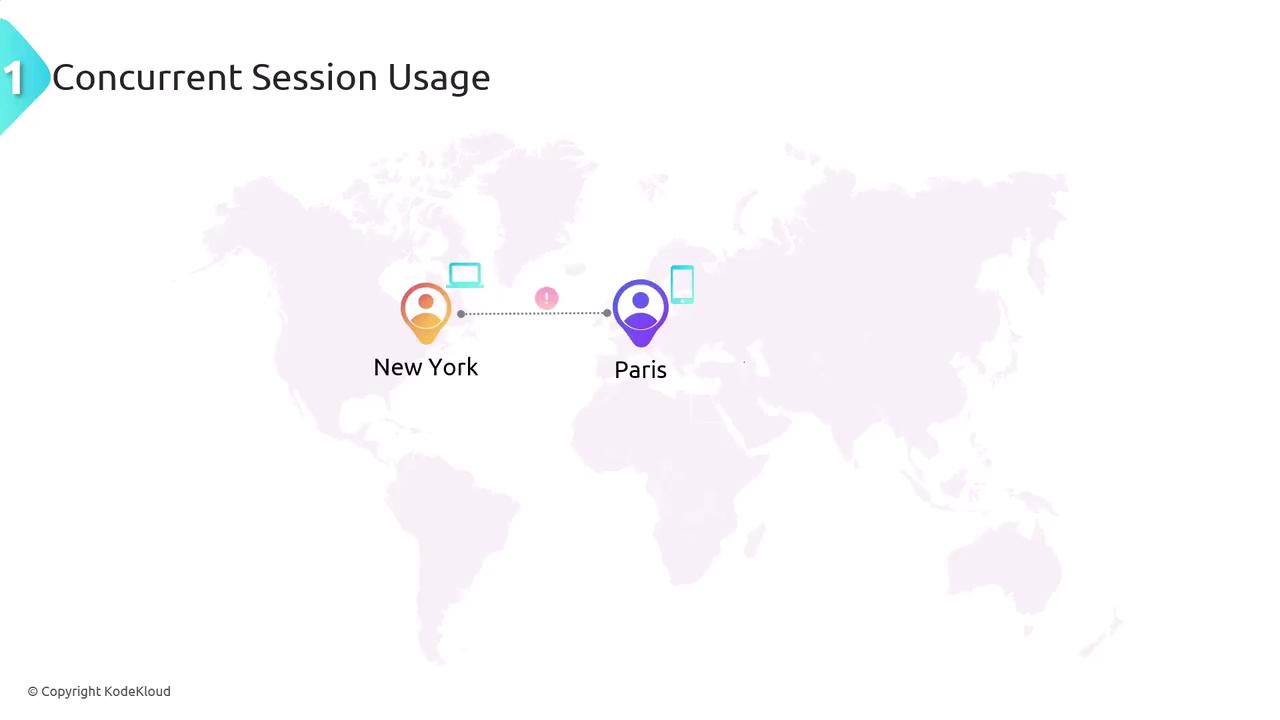
Concurrent Session Usage
Concurrent session usage is detected when multiple active sessions for the same user account occur simultaneously from different locations or devices. Standard user behavior typically involves one active session per device or location. When sessions appear from geographically separated places, it may indicate account compromise.
Blocked Content
Blocked content refers to attempts to access or upload data that violates security policies. Such actions indicate potential attempts to bypass security controls. Any attempt to transmit or retrieve restricted content should immediately trigger an alert, as this behavior may be linked to malicious intent.

Impossible Travel
Impossible travel occurs when login attempts are made from geographically distant locations within a timeframe too short for physical travel to be feasible. For instance, a login from London followed by another from Tokyo within minutes is highly suspicious and may suggest a compromised account.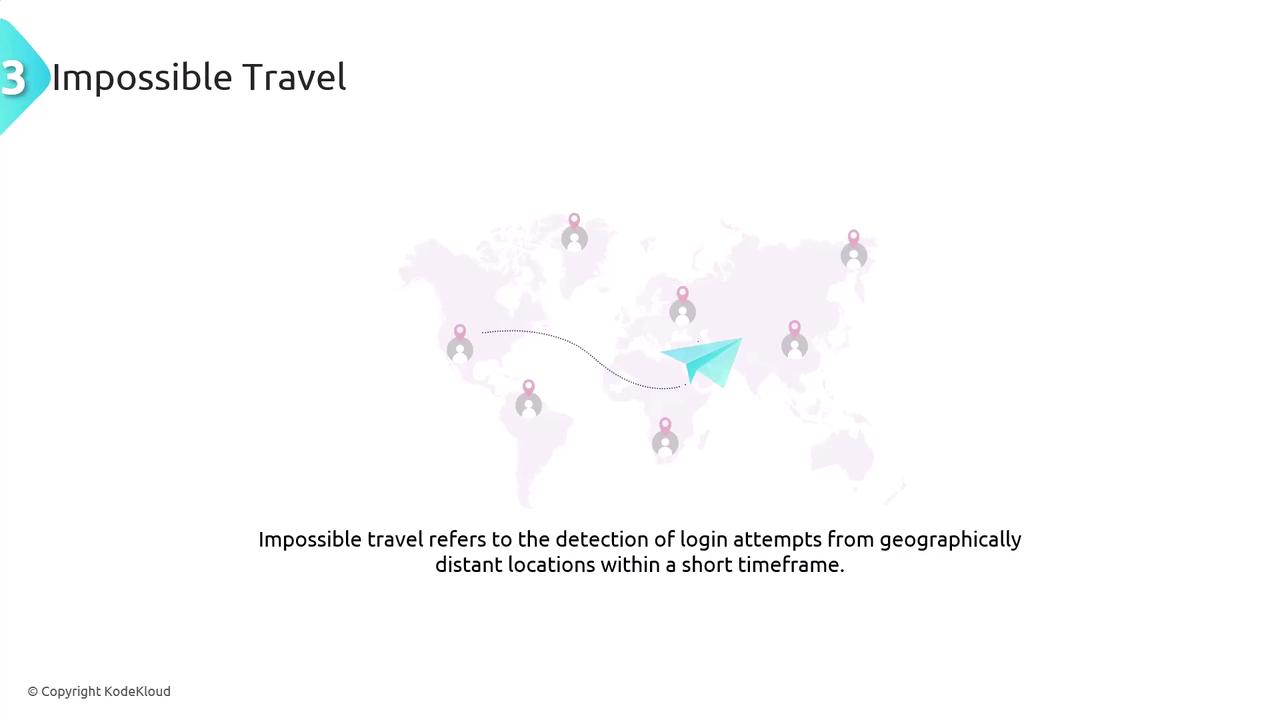
If you observe impossible travel patterns, investigate immediately and consider additional authentication measures.
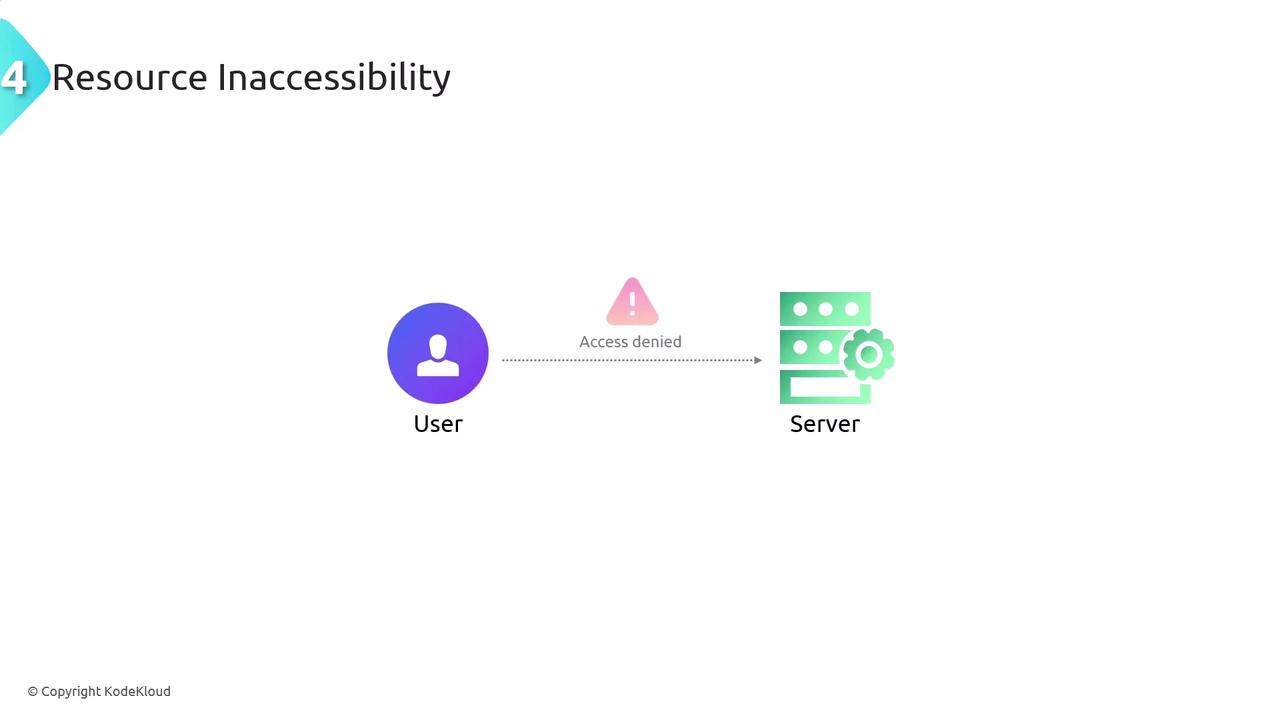
Resource Inaccessibility
Resource inaccessibility is when genuine users suddenly lose access to critical systems or data. This disruption might result from denial-of-service attacks, account compromises, or other malicious activities. Under normal circumstances, users have consistent access to essential resources, so any abrupt loss of access should be promptly examined.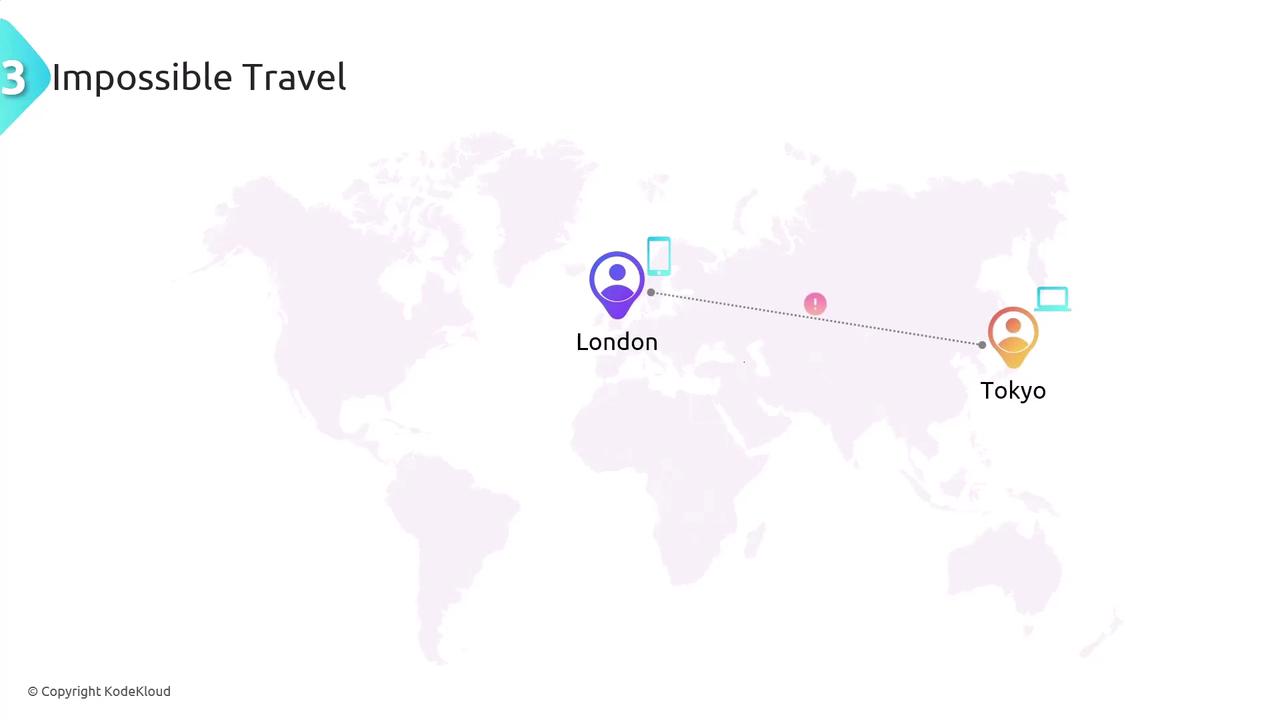
Out-of-Cycle Logging
Out-of-cycle logging refers to system or user logging activities that occur outside of normal business hours or established operation cycles. Since logging usually adheres to a regular schedule, any unexpected log events can signal unauthorized access or other suspicious activity.
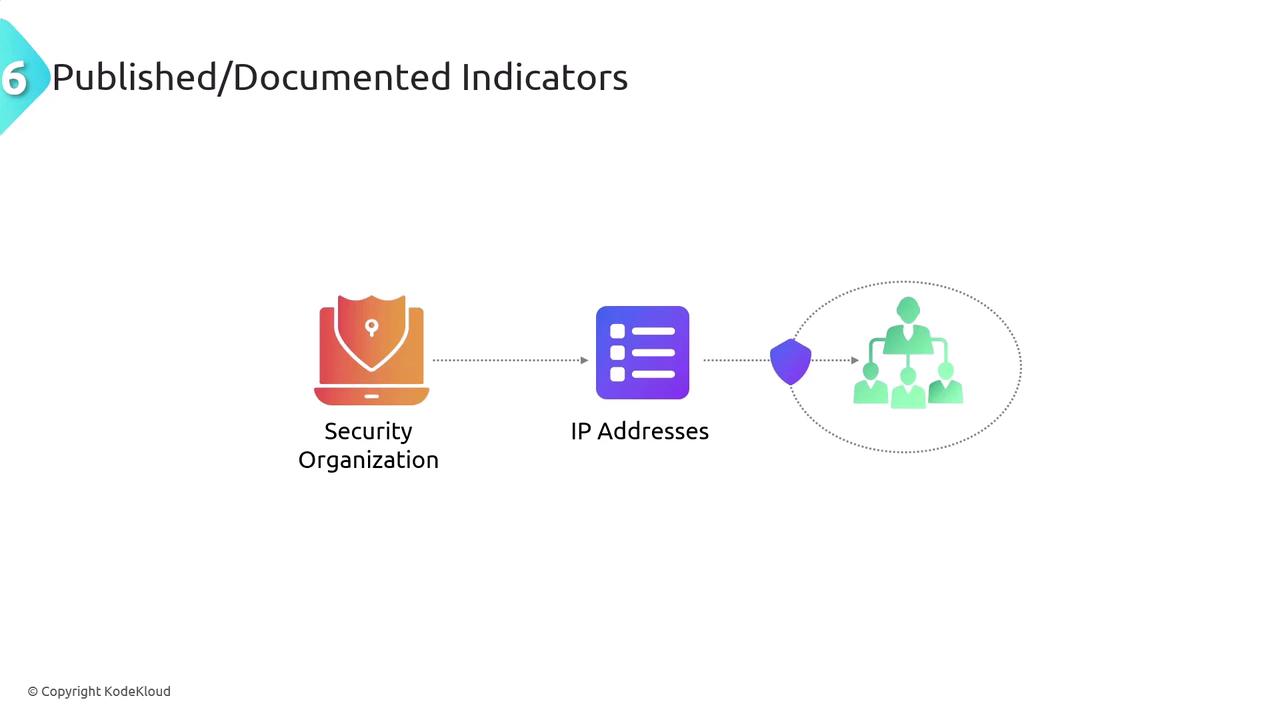
Published or Documented Indicators
Published or documented indicators, also known as indicators of compromise (IOCs), include known IP addresses, domain names, file hashes, and other artifacts linked to malicious activities. Publicly available IOCs, shared by security researchers and organizations, provide valuable threat intelligence that can be integrated into your security monitoring systems.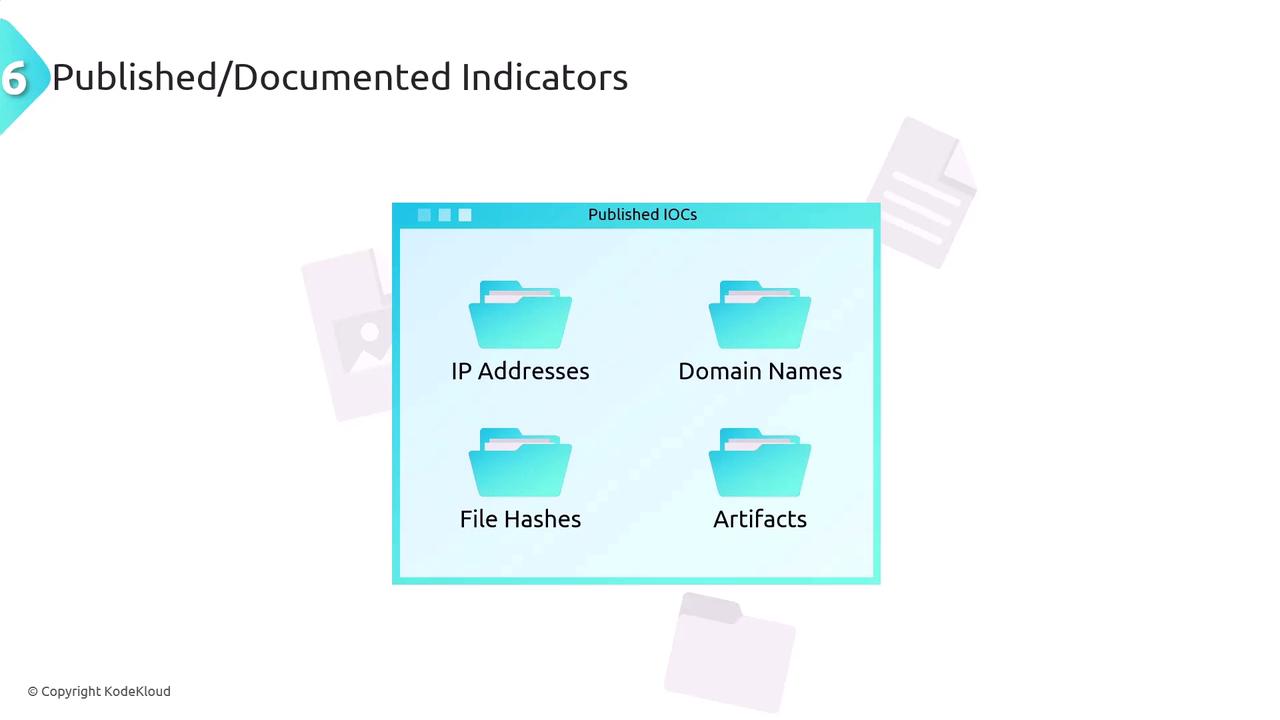
Conclusion
Recognizing and understanding the various indicators of malicious activity is vital for establishing a robust security posture. By closely monitoring signals such as concurrent session usage, blocked content, impossible travel, resource inaccessibility, out-of-cycle logging, and integrating published IOCs into your defenses, organizations can effectively detect and respond to security incidents. Implementing comprehensive detection and mitigation strategies is key to minimizing the overall impact of these threats. Stay vigilant and continuously update your security practices to protect your organization against evolving cyber threats.