Before diving deeper into threat actors, it is important to understand the differences between vulnerabilities, threats, and risk:
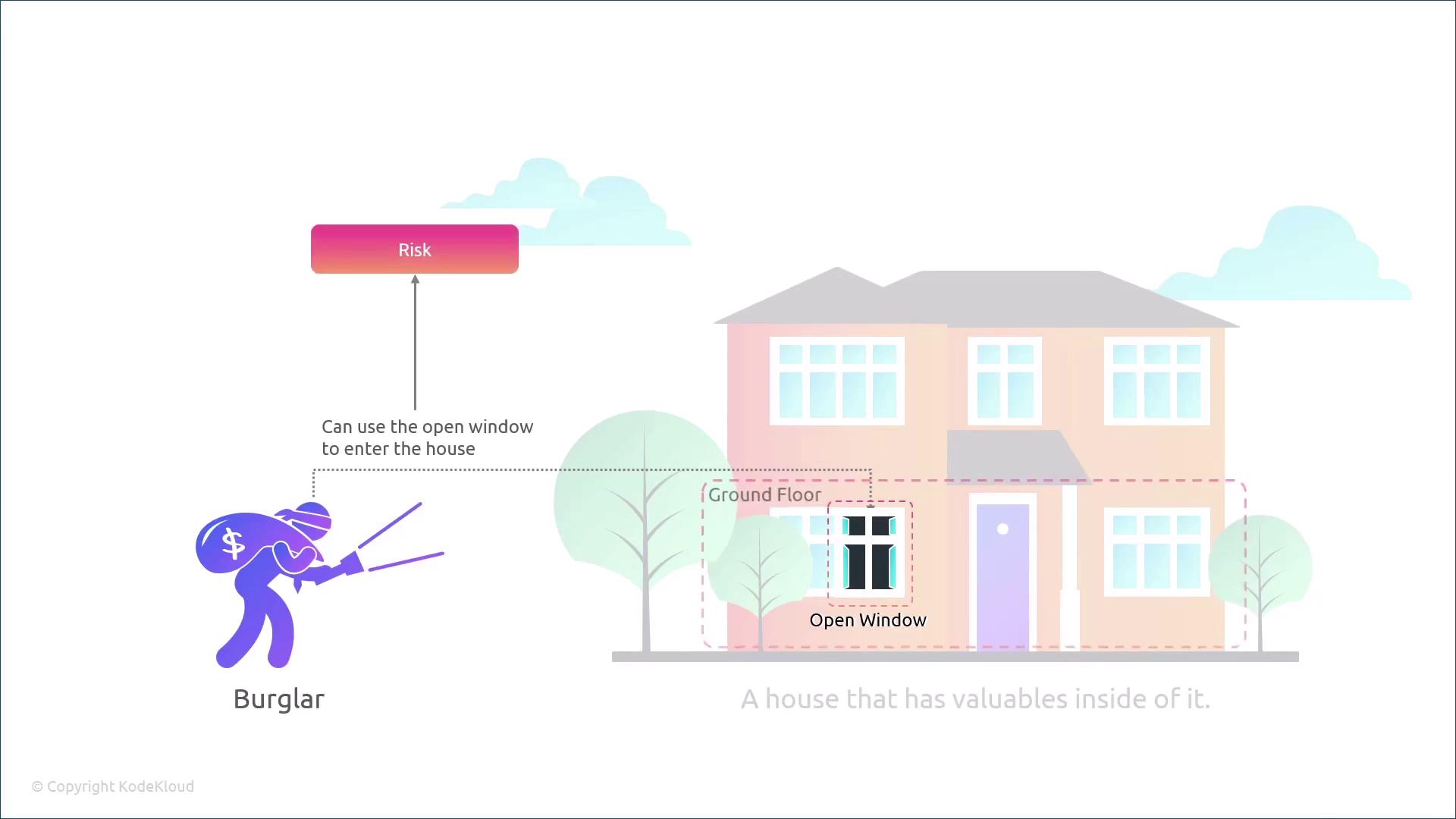
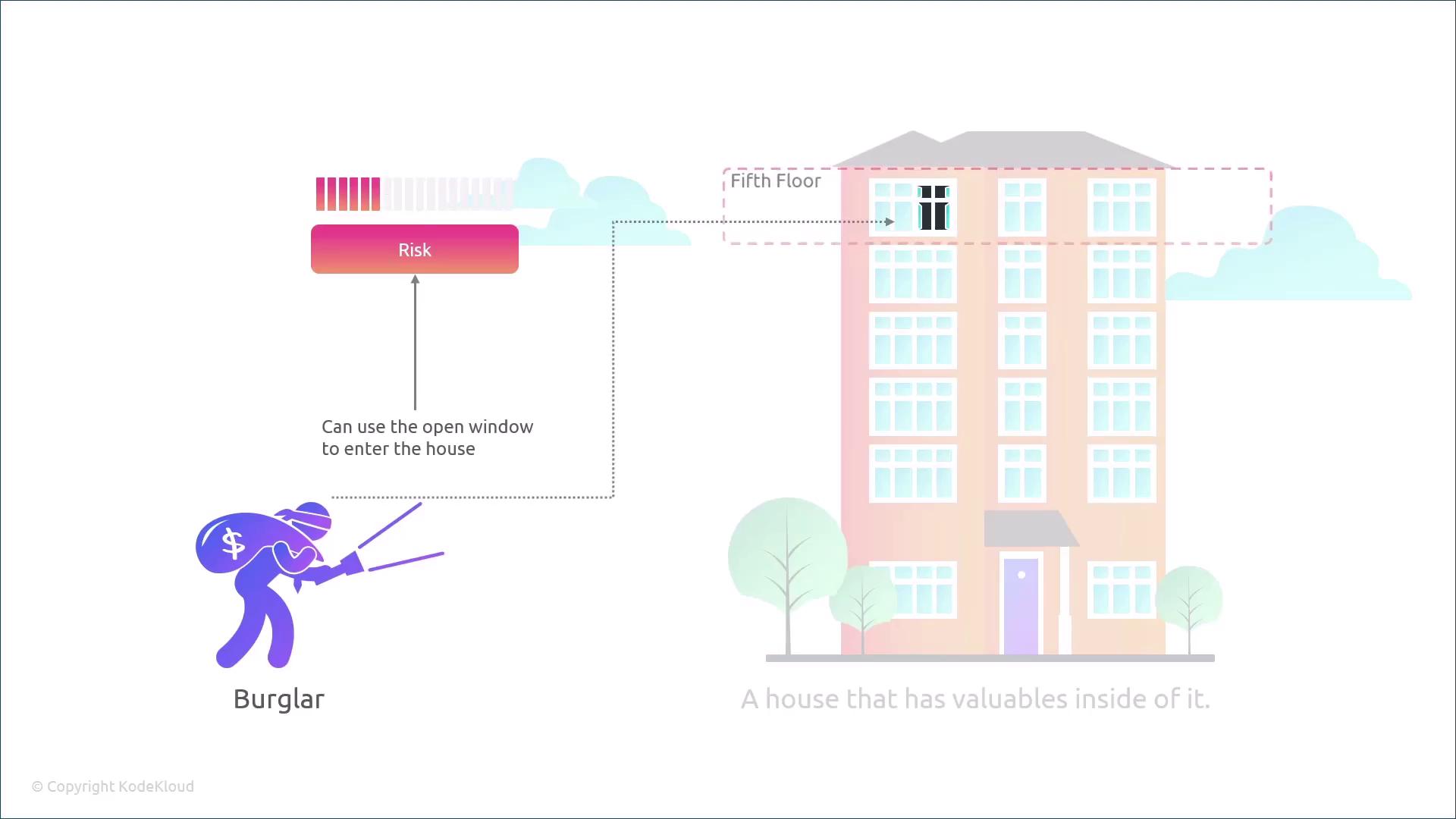
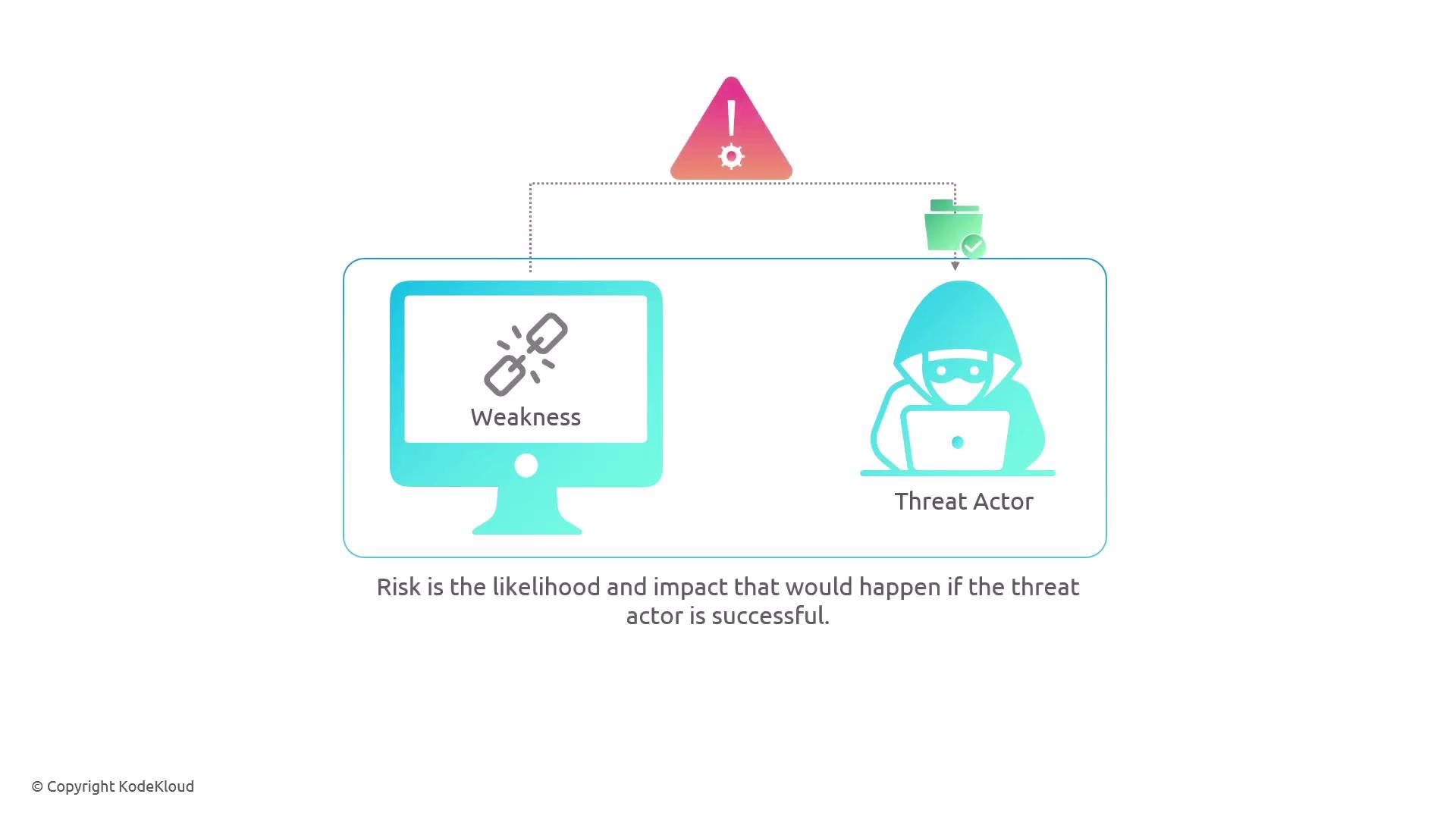
- A vulnerability is a flaw or weakness.
- A threat involves a threat actor who is willing and able to exploit a vulnerability.
- Risk is determined by the likelihood of the exploitation and the potential impact.
- The likelihood that a threat will exploit a vulnerability.
- The potential impact if the exploitation is successful.
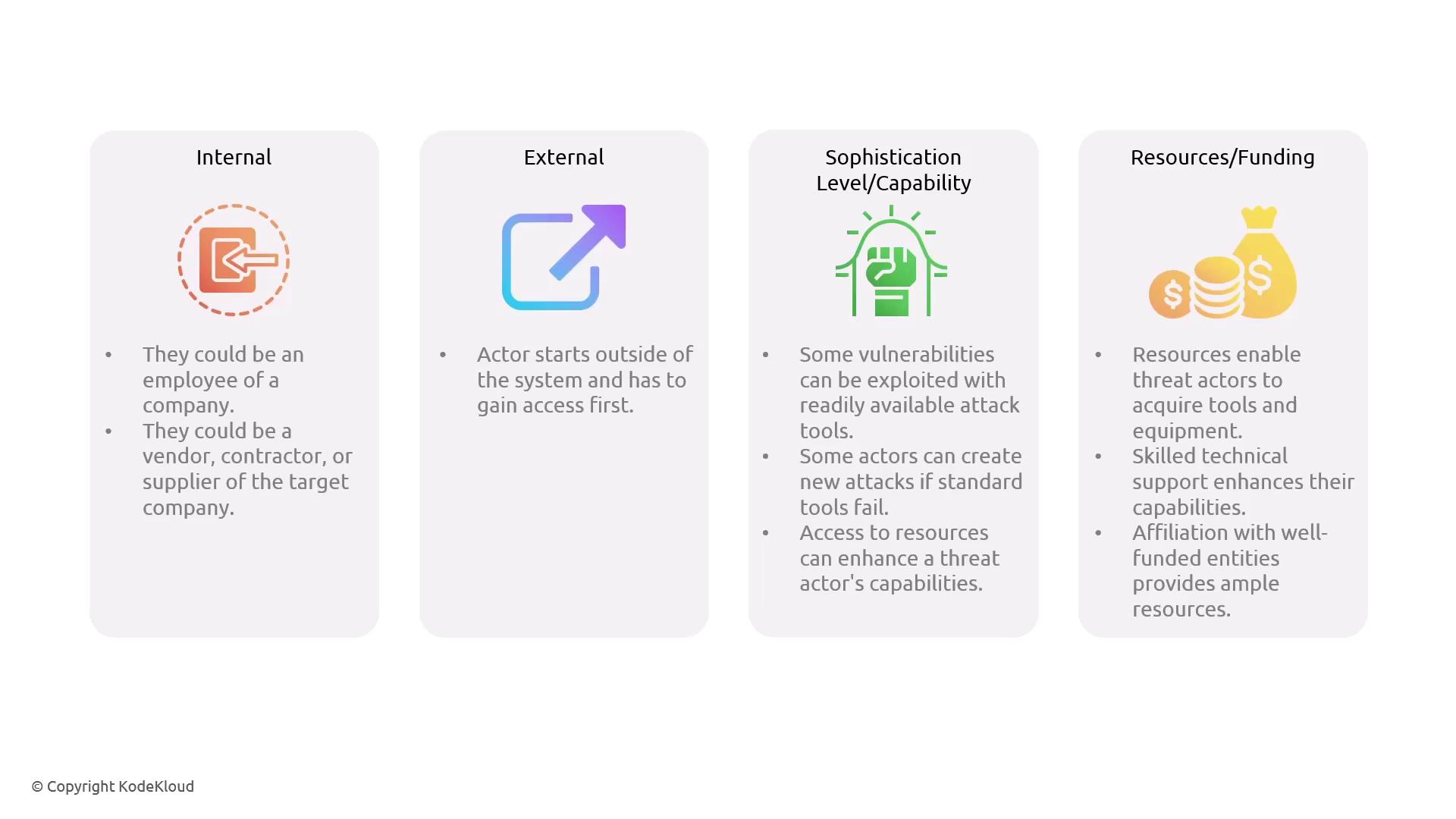
- Internal Threat Actors: These individuals already have access permissions within the system. This category includes employees, vendors, contractors, or suppliers.
- External Threat Actors: These attackers must first gain access to the system before attempting to exploit vulnerabilities.