Common Vulnerability Enumeration (CVE)
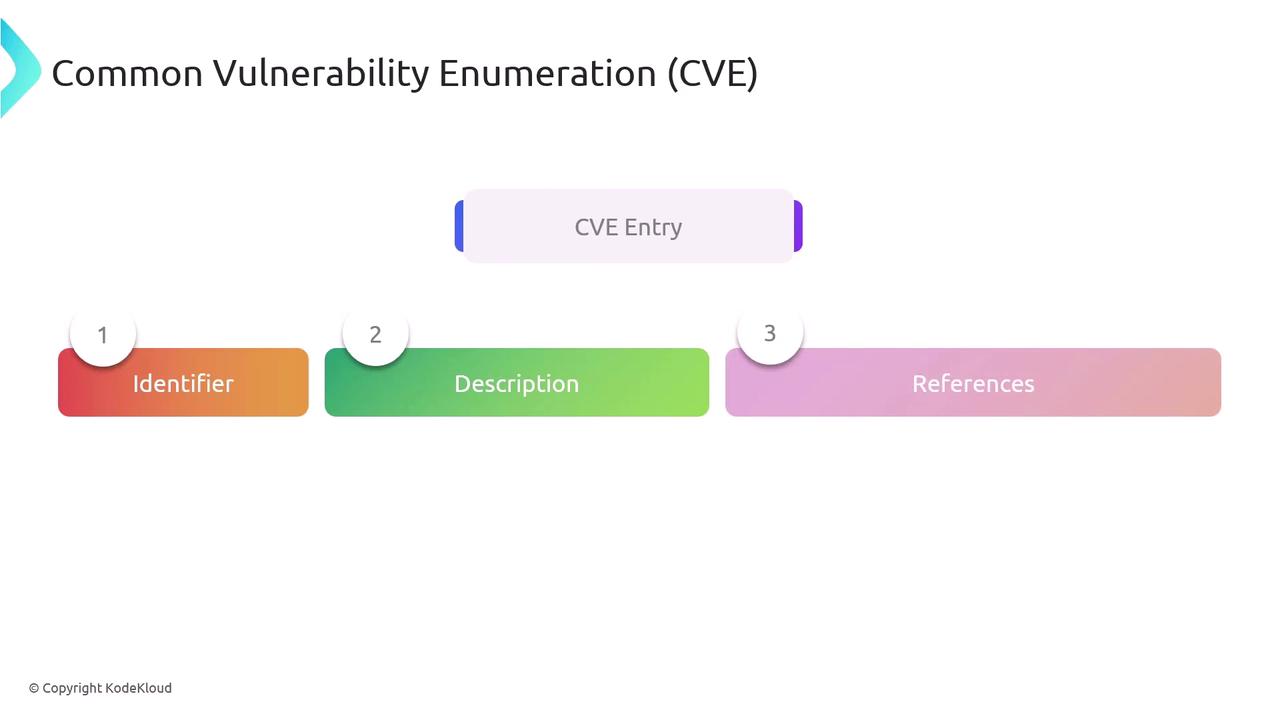
Common Vulnerability Enumeration (CVE) is a standardized system for identifying and cataloging vulnerabilities in software and hardware. Each vulnerability is assigned a unique identifier, which simplifies sharing and communication between security professionals, researchers, and vendors. Every CVE entry typically includes an identifier, a brief description of the vulnerability, and references to supplementary information such as security advisories and patches.
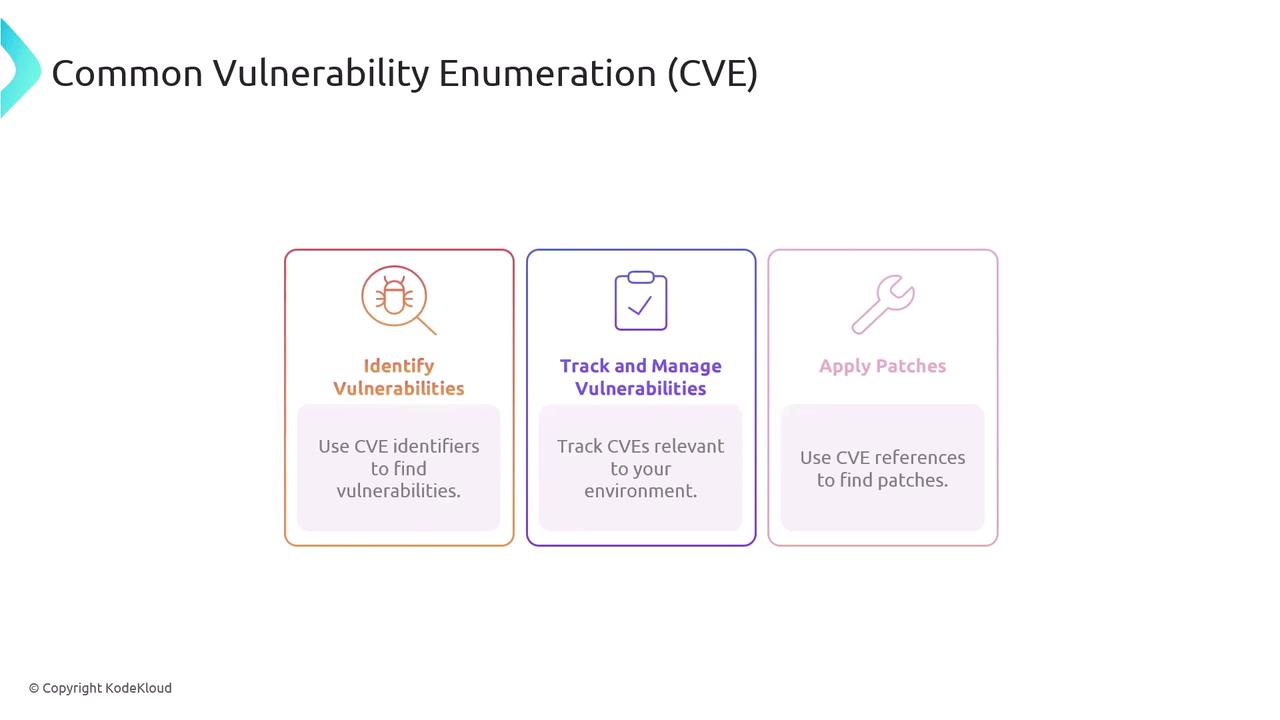
- Identification – Use CVE identifiers to efficiently search for vulnerabilities in your systems and software.
- Tracking and Management – Maintain a curated list of CVEs relevant to your environment to effectively monitor and manage vulnerabilities.
- Patch Application – Refer to CVE information to locate and apply patches and updates addressing specific vulnerabilities.
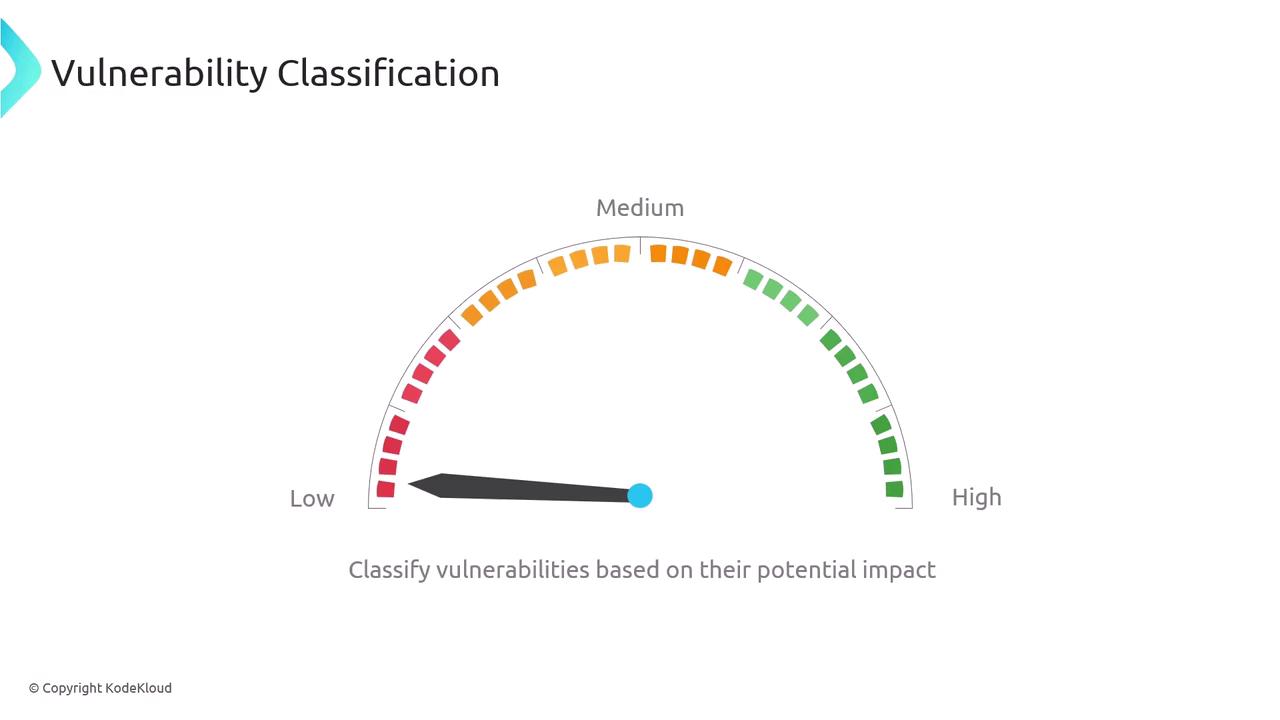
Vulnerability Classification
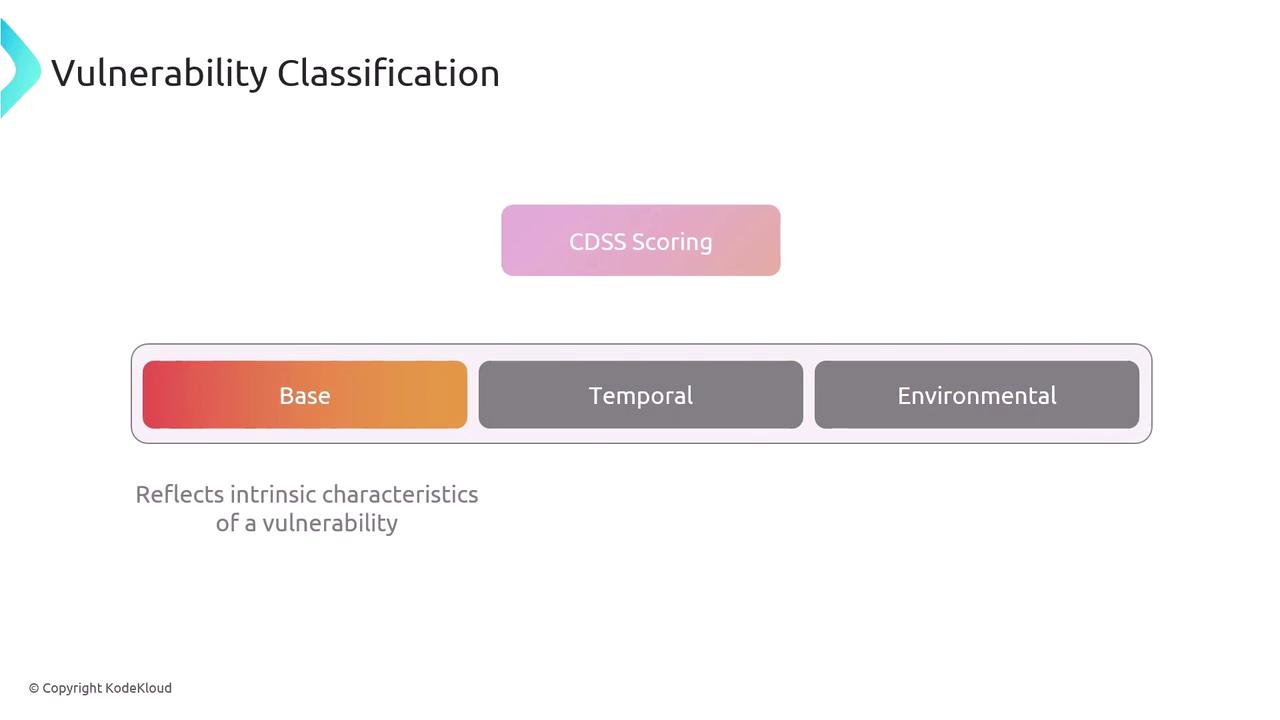
Vulnerability classification involves categorizing vulnerabilities based on attributes like severity, impact, and exploitability. This systematic categorization aids in prioritizing remediation efforts and ensures that resources are allocated effectively. A prominent classification system is the Common Vulnerability Scoring System (CVSS), which assesses vulnerabilities on a scale from 0 to 10 by evaluating factors such as exploitability and impact. Alternatively, some organizations may utilize qualitative severity levels (high, medium, low) or custom assessments based on potential operational impact.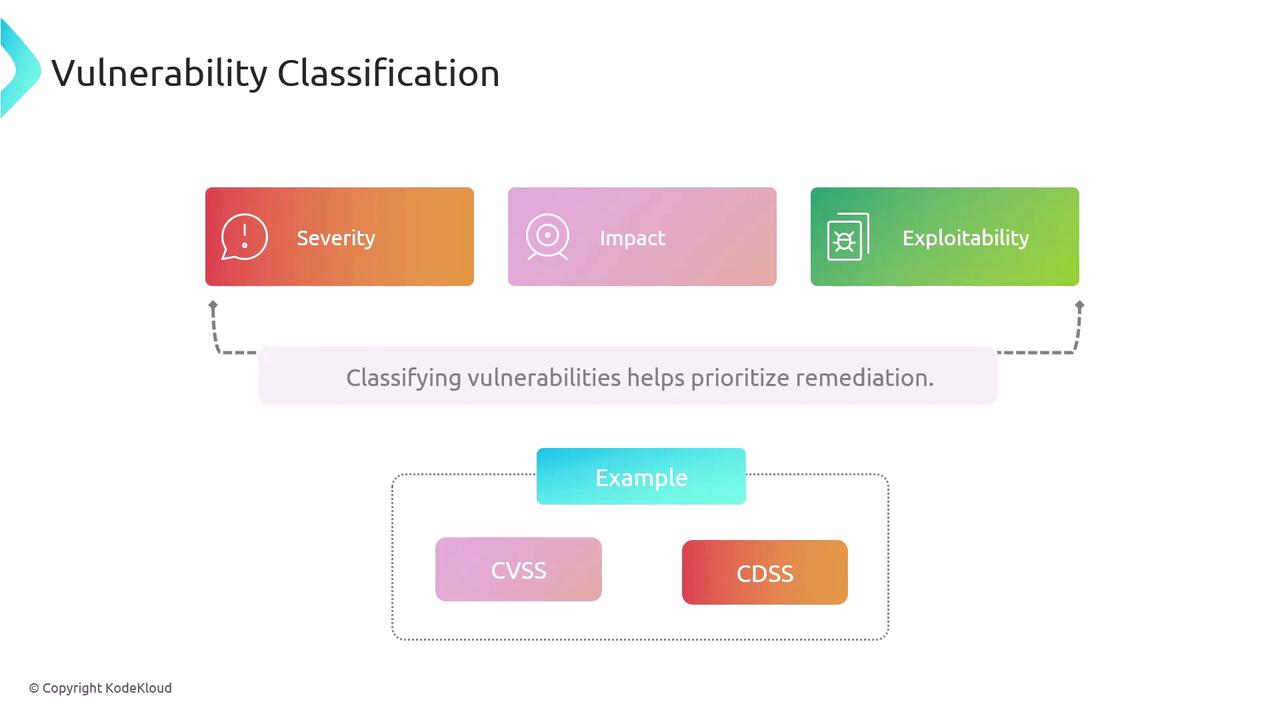
Environmental Variables
Environmental variables encompass the specific conditions under which a vulnerability exists. These conditions include network configuration, security controls, and overall operational environment. The context provided by these variables can significantly influence both the impact and exploitability of a vulnerability. For example, a vulnerability with a high CVSS score may represent less risk in an environment with robust network segmentation and strict access controls when compared to a less secure setting.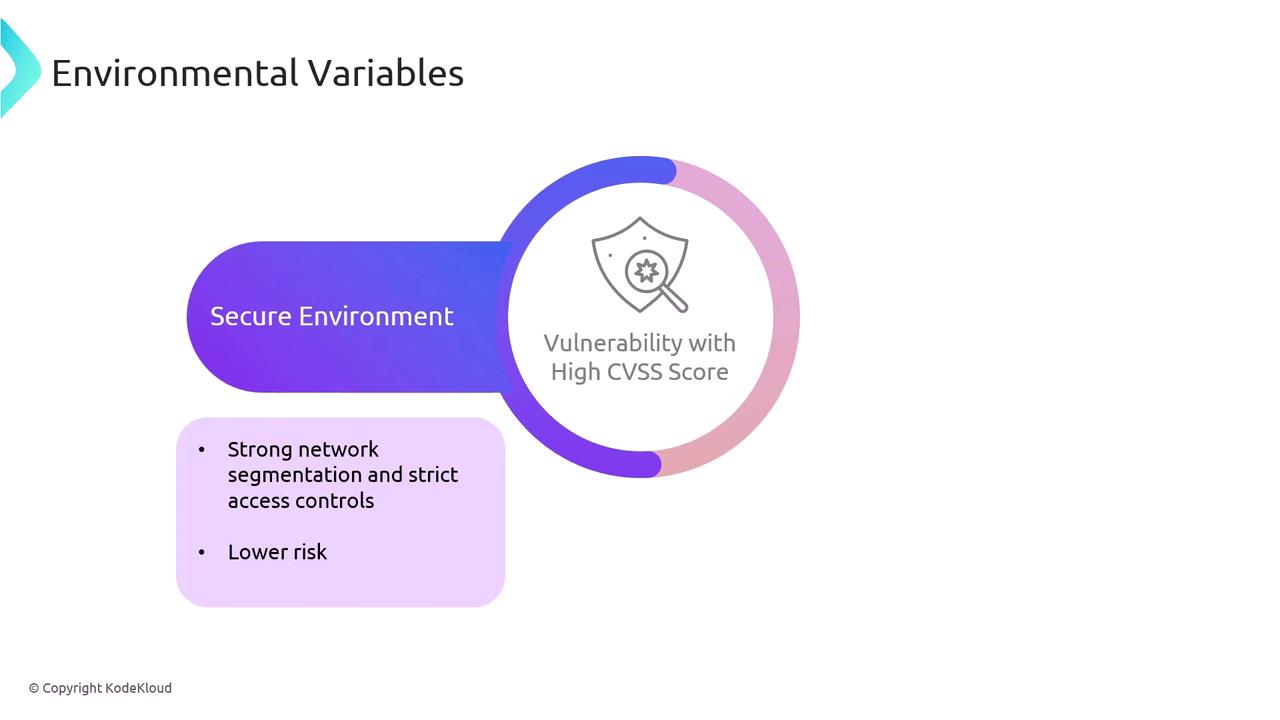
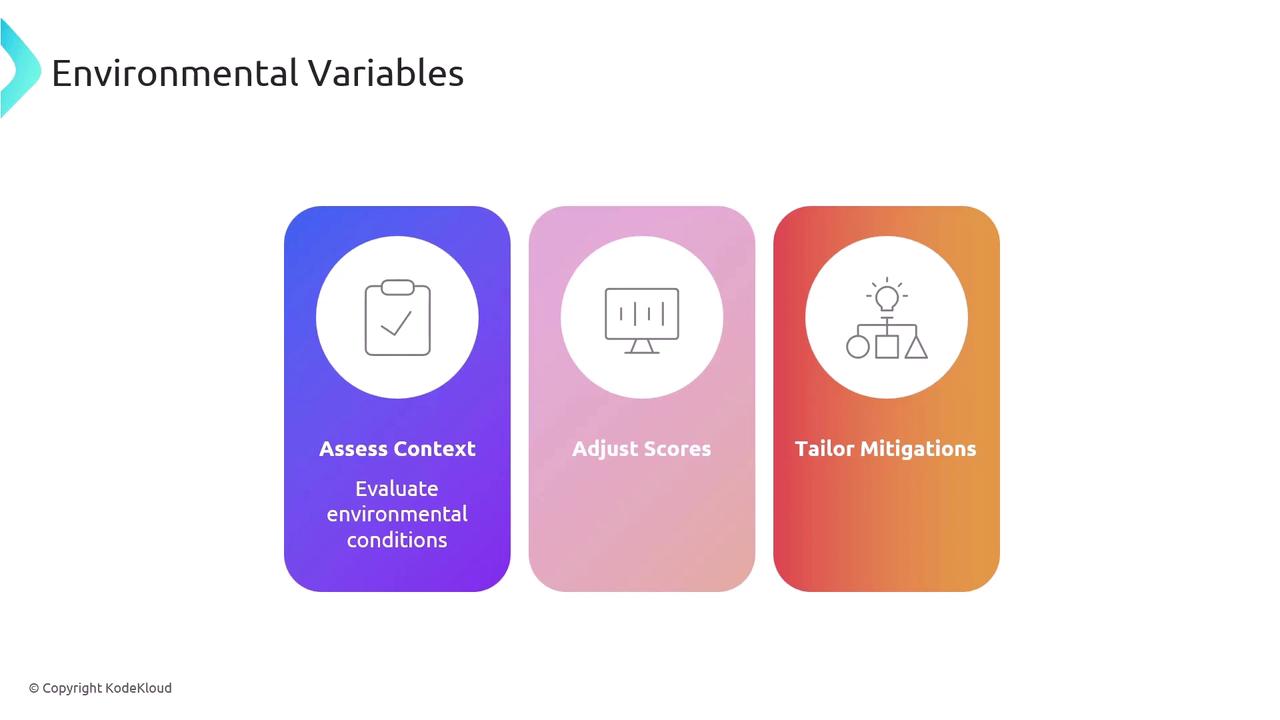
- Context Assessment: Evaluate the specific configurations and conditions within your environment.
- Score Adjustment: Use environmental metrics (as in CDSS) to modify scores based on actual risk.
- Mitigation Tailoring: Develop mitigation strategies that address the unique aspects of your operational context.
Industry and Organizational Impact
Understanding the impact of a vulnerability on your industry and organization is vital. This analysis evaluates factors such as sector-specific challenges, operational dependencies, and regulatory requirements. For example, vulnerabilities affecting a financial system can have far-reaching consequences, particularly for banks operating under strict regulatory oversight and high customer trust standards.Risk Tolerance in Vulnerability Management
Risk tolerance defines the degree of risk an organization is willing to accept while pursuing its strategic objectives. It is shaped by the organization’s risk appetite, regulatory constraints, and overall business priorities. For example, an organization with a low risk tolerance might remediate all identified vulnerabilities, whereas one with a higher tolerance may concentrate on addressing only the most critical threats. To integrate risk tolerance into your vulnerability management process:- Evaluate Risk Appetite: Align your security strategy with your organization’s risk preferences.
- Engage Stakeholders: Collaborate with key decision-makers to define an acceptable level of risk.
- Document Policies: Clearly document your organization’s risk tolerance to inform and guide remediation priorities.
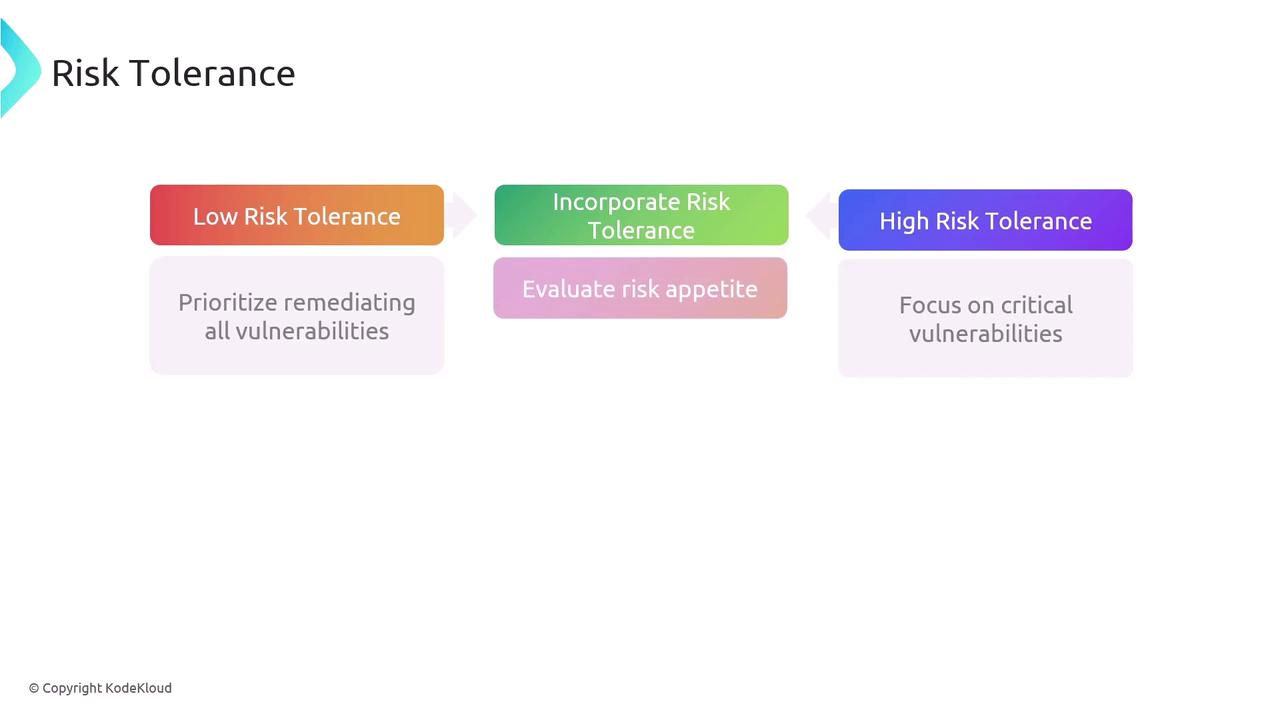
Incorporating risk tolerance into your vulnerability management strategy ensures that remediation efforts are aligned with your organization’s business objectives and regulatory requirements.
Conclusion
Vulnerability analysis is an essential component of a robust security strategy. By mastering the fundamentals of the Common Vulnerability Enumeration (CVE) system, understanding various vulnerability classification methodologies, evaluating environmental variables, considering industry and organizational impacts, and integrating risk tolerance, organizations can effectively identify, prioritize, and mitigate vulnerabilities. This comprehensive approach enables the development of tailored security measures, ensuring that your organization’s unique context and level of acceptable risk are at the forefront of your defense strategy.
Additional Resources
- CVE® – Common Vulnerabilities and Exposures
- NVD – National Vulnerability Database
- Microsoft Security Advisory
For further insights into vulnerability analysis, consider exploring additional documentation and knowledge bases that offer comprehensive guidelines on security best practices.