Downgrade Attacks
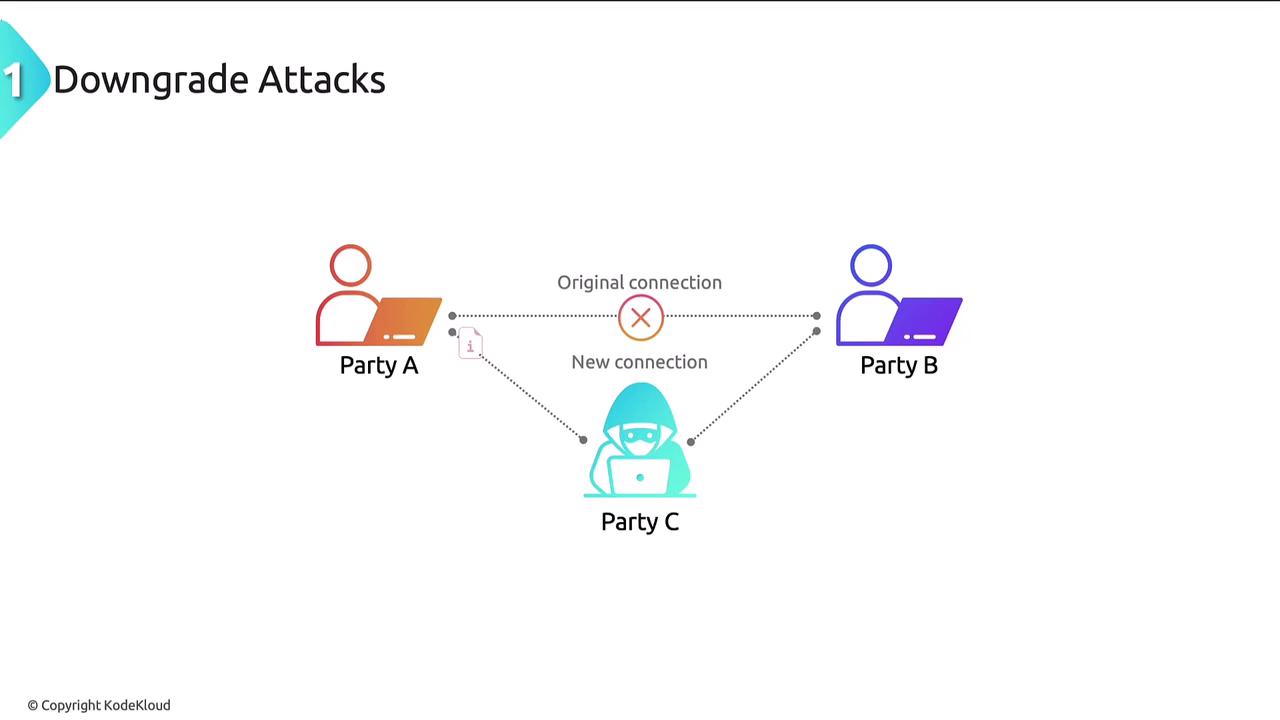
A downgrade attack, also known as a version rollback attack, deceives systems into using an older, less secure version of a protocol or cryptographic algorithm. By forcing the communication to rely on an outdated protocol, attackers can exploit well-known vulnerabilities. The typical steps in a downgrade attack include:- Handshake Interception: The attacker targets the initial connection phase where the client and server negotiate cryptographic parameters.
- Protocol Manipulation: By intercepting and altering the handshake, the attacker forces both parties to agree on an older protocol version.
- Exploitation: With the connection downgraded, the attacker leverages known weaknesses in the legacy protocol.
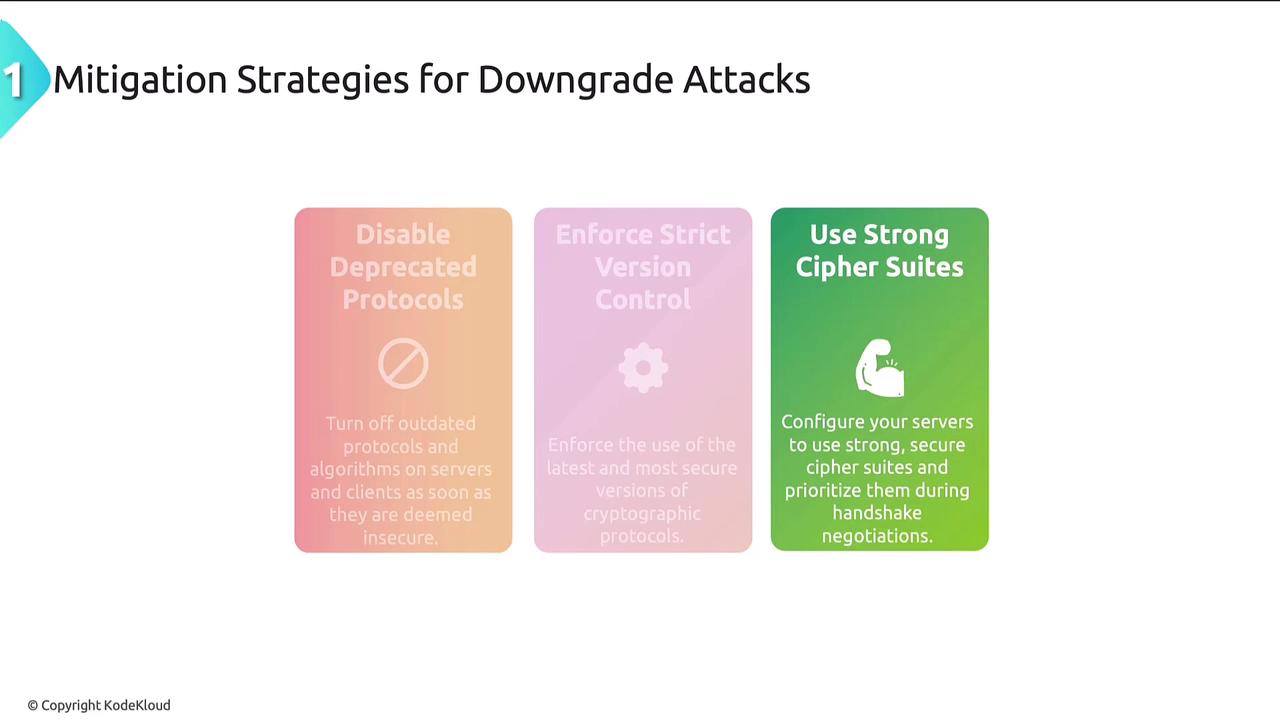
Mitigation Strategies for Downgrade Attacks
To defend against downgrade attacks, follow these best practices:- Disable Deprecated Protocols: Remove support for outdated protocols and weak cryptographic algorithms on both servers and clients.
- Enforce Secure Protocol Versions: Configure systems to only allow the latest and most secure versions of cryptographic protocols.
- Prioritize Strong Cipher Suites: Ensure servers are set up to negotiate only robust cipher suites during handshakes.
Always update your systems and configurations regularly to avoid known vulnerabilities associated with outdated protocols.
Collision Attacks
Collision attacks target weaknesses in hash functions. In an ideal scenario, a hash algorithm produces a unique output for every distinct input. However, some older hashing functions allow different inputs to yield the same hash value, resulting in a collision.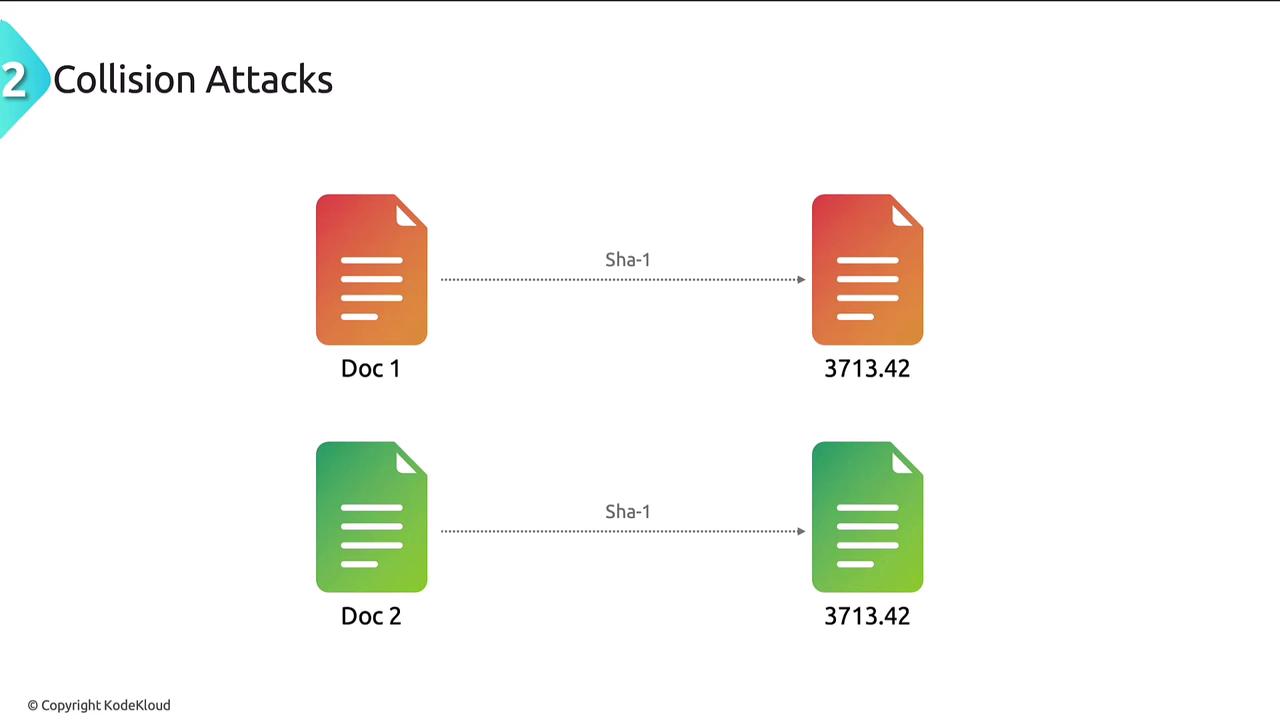

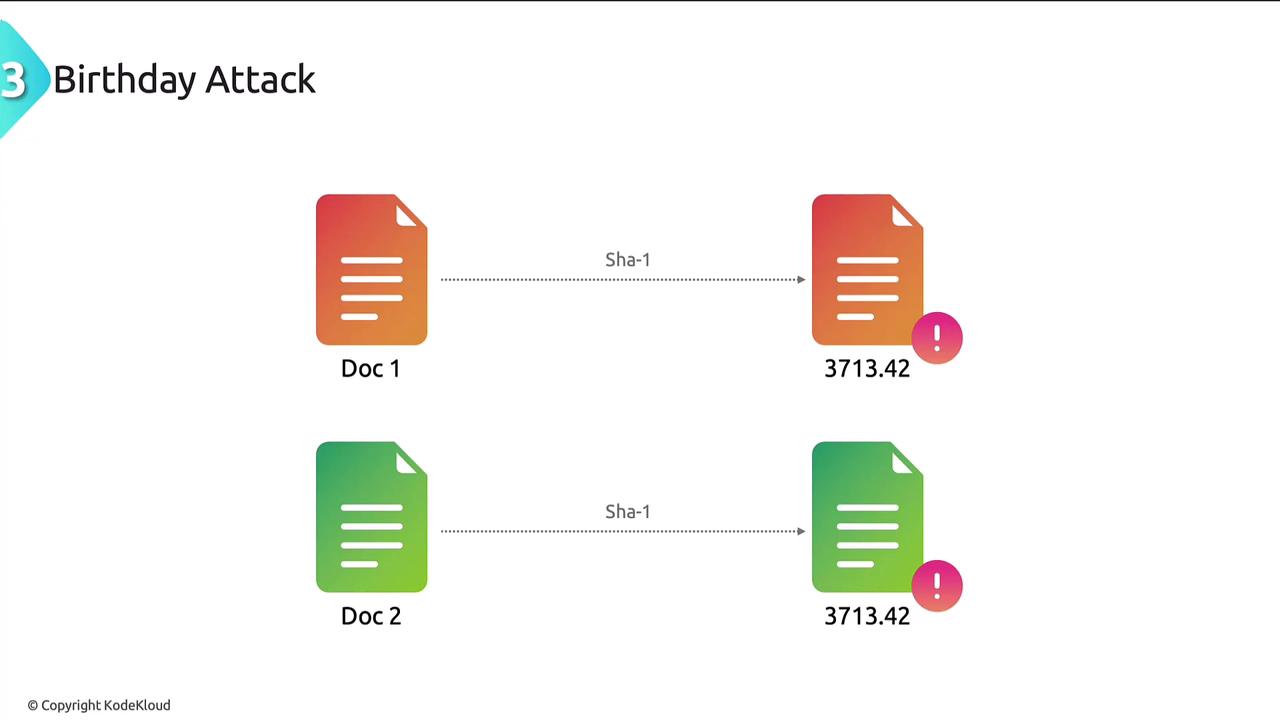
Birthday Attacks
Birthday attacks exploit the statistical principle known as the birthday paradox. In probability theory, the birthday paradox reveals that among just 23 people, there is over a 50% chance that two individuals share the same birthday. Cryptographers adapt this principle to find collisions in hash functions.
Mitigation Strategies for Birthday Attacks
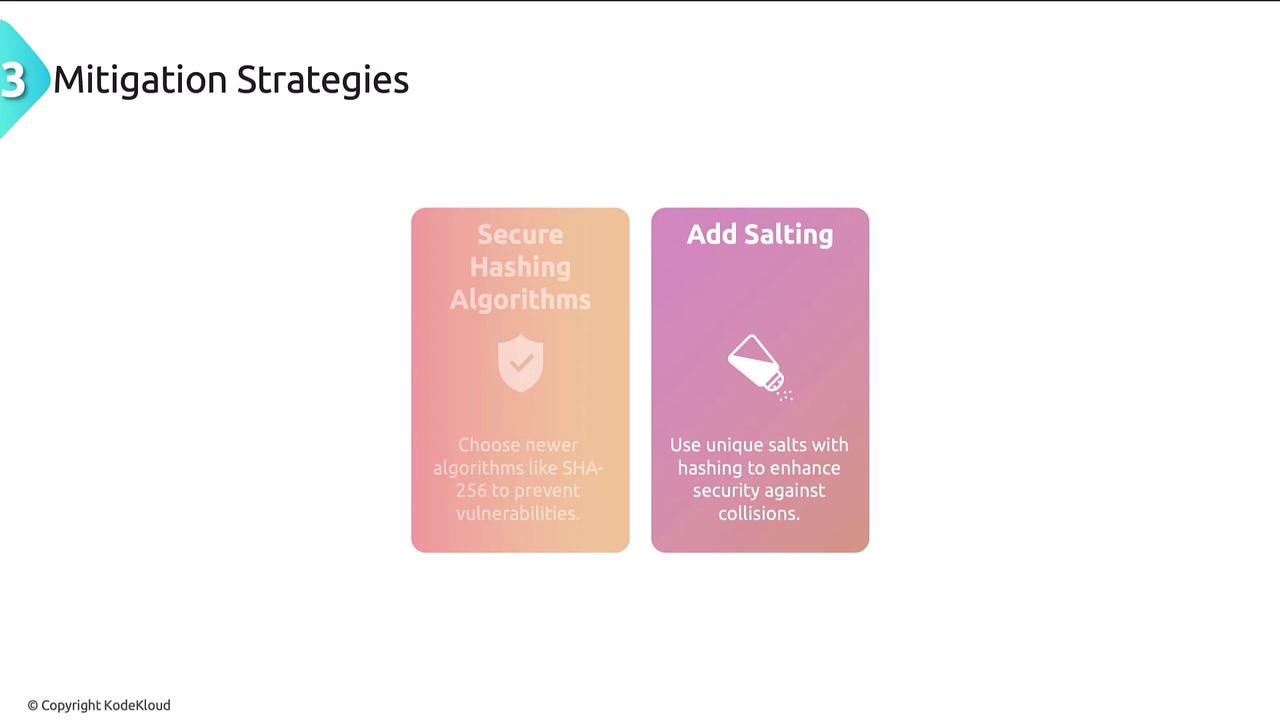
To reduce the potential for birthday attacks, implement the following measures:- Adopt Secure Hash Functions: Transition from vulnerable algorithms like SHA-1 to more secure alternatives such as SHA-256.
- Incorporate Salting: Improve security by adding a random salt to the hashing process, making precomputed collisions much more challenging.
Using outdated hash functions like MD5 or SHA-1 can seriously compromise data integrity. Always use updated cryptographic standards to safeguard your information.
Conclusion
Cryptographic attacks—specifically downgrade attacks, collision attacks, and birthday attacks—pose serious threats to the confidentiality, integrity, and overall security of data. Understanding these attack methods and implementing robust mitigation strategies can significantly enhance an organization’s cryptographic defenses. Maintaining up-to-date protocols, using secure algorithms, and applying additional security measures are critical steps in protecting sensitive information.