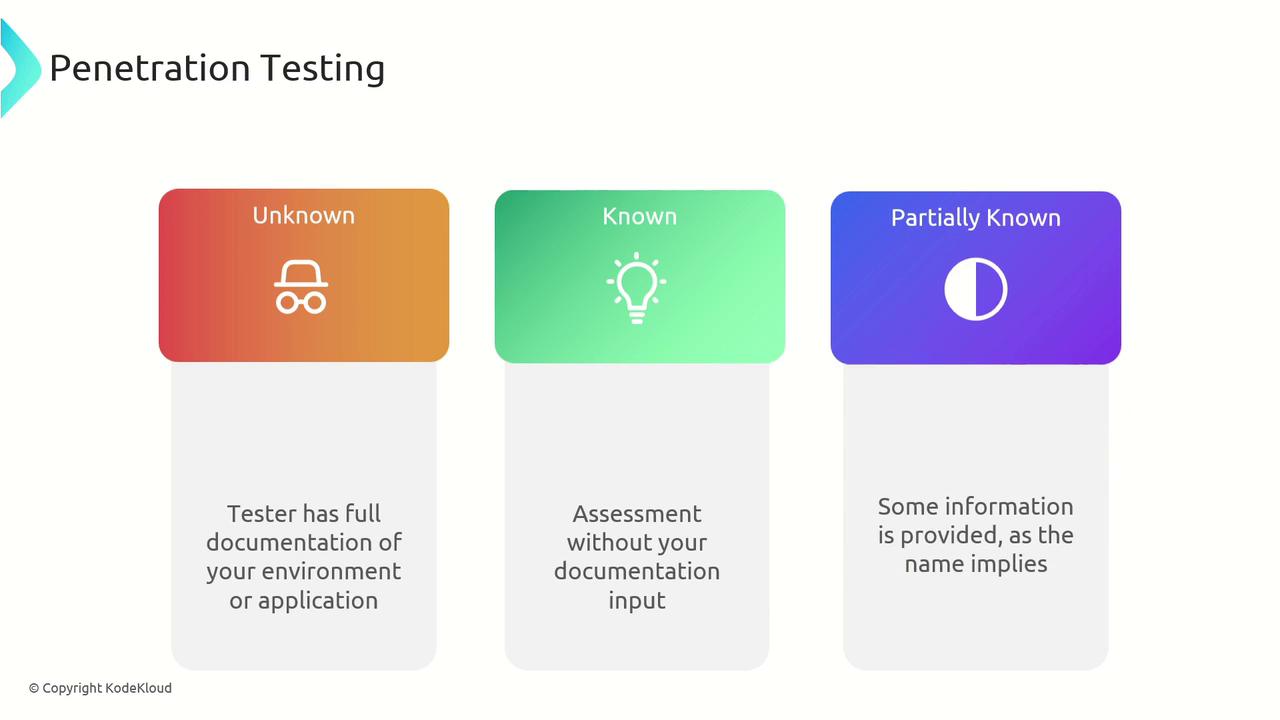
- A known penetration test provides the tester with comprehensive documentation of the environment or application, allowing for an in-depth analysis.
- An unknown penetration test is conducted without any prior information, emulating the perspective of an external attacker with no insider insights.
- A partially known test offers limited information, striking a balance between the other two approaches.
Remember, penetration testing goes beyond identifying outdated software patches or misconfigurations; it mimics an attacker’s steps to breach a system.
Active Reconnaissance
Active reconnaissance involves direct interaction with the target system. Testers use techniques like port scanning and service enumeration to extract details such as software versions, configuration data, and running services. This method provides real-time insights into potential vulnerabilities.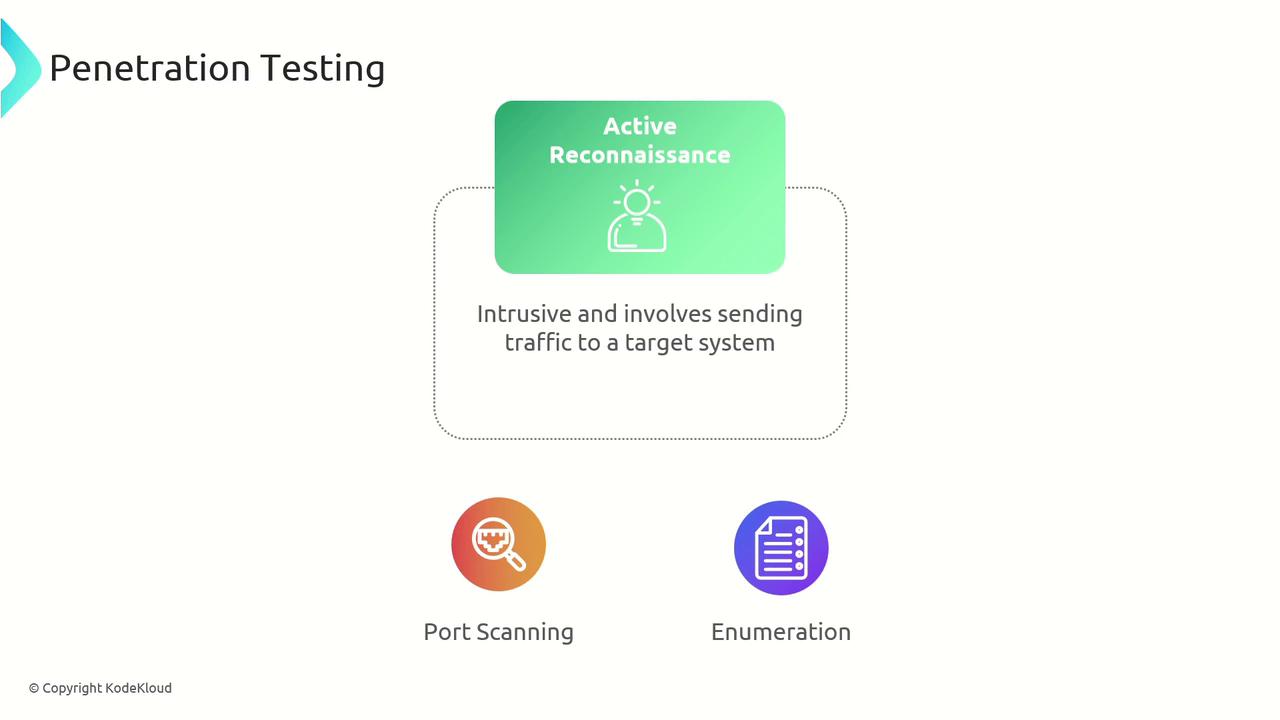
Passive Reconnaissance
In contrast, passive reconnaissance gathers public information without directly engaging with the target. This approach leverages open-source intelligence (OSINT), WHOIS records to ascertain domain ownership, network traffic analysis for identifying IP addresses and ports, and even data from social media platforms.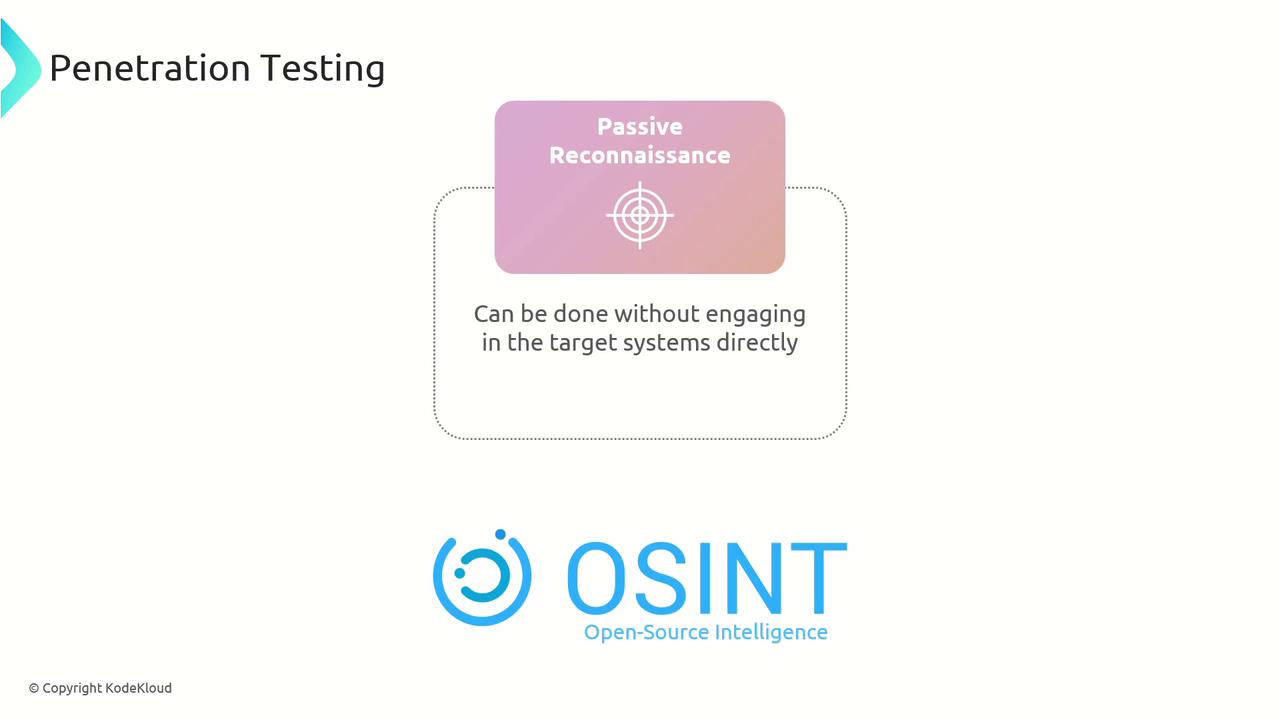
Both active and passive reconnaissance are essential for a comprehensive security assessment. While active methods reveal immediate vulnerabilities, passive techniques provide background context that can shape a more strategic testing approach.