/admin endpoint of your example.com site using HTTP Basic Authentication. The main site remains publicly accessible while only /admin requires credentials. We’ll cover:
- Verifying your site setup
- Updating the Nginx configuration
- Generating an
.htpasswdfile - Testing and reloading Nginx
- (Optional) Protecting the entire site
- Exploring advanced auth solutions
1. Verify Your Site
Make sure Nginx is serving your site over HTTPS on port 443:2. Update Nginx Configuration
Open your SSL-enabled server block (e.g.,/etc/nginx/sites-available/example-https):
server block to include a dedicated /admin location:
HTTP Basic Authentication transmits credentials as Base64-encoded text. Always use HTTPS to prevent interception.
3. Create the .htpasswd File
Generate a username and encrypted password for Basic Auth:
-
Change to the directory for password files:
-
Initialize the file and add the
adminuser: -
Append an encrypted password (you’ll be prompted):
-
Verify the contents:
Ensure that
.htpasswd is readable by the Nginx user but not world-readable:4. Test and Reload Nginx
Validate and apply your configuration:- Public pages load as before.
/adminprompts for credentials.
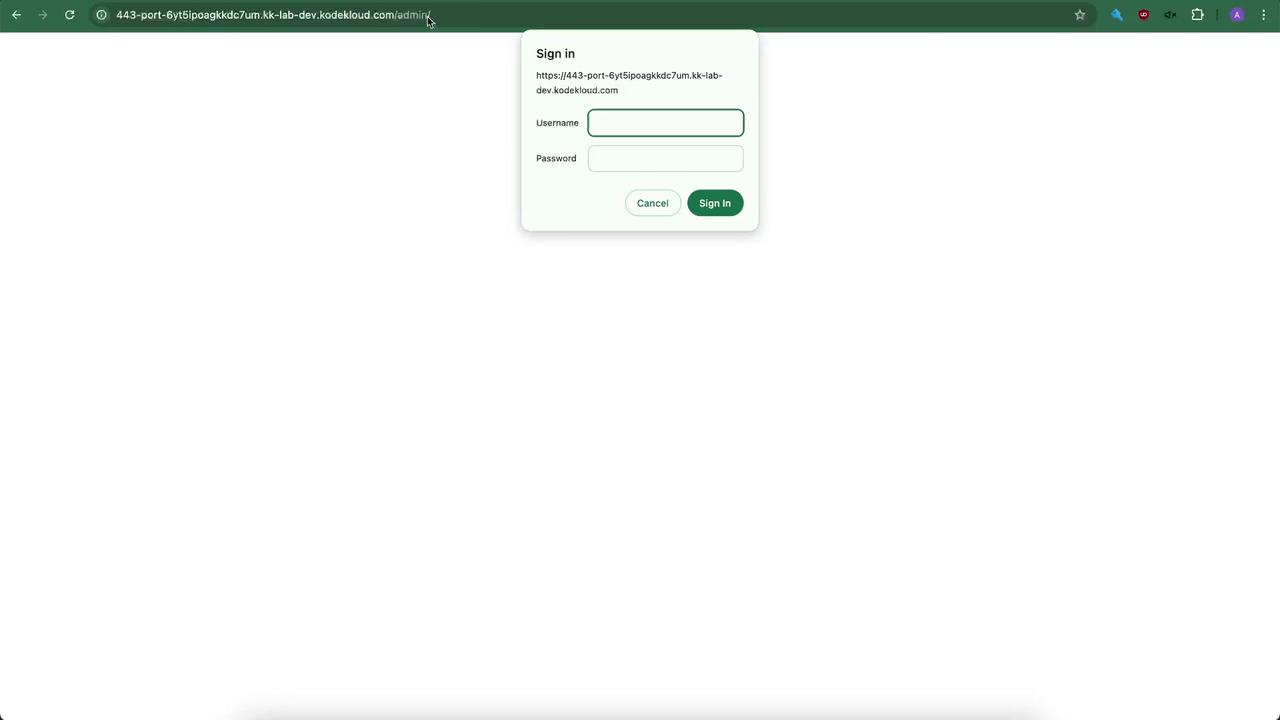
admin and your password to access the admin area.
5. (Optional) Password-Protect the Entire Site
If you want every page to require authentication, move theauth_basic directives into the / block:
https://example.com will now prompt for the Basic Auth credentials. Test it in an incognito/private window.
6. Beyond Basic Auth
For scalable, production-grade authentication, consider integrating with identity providers and single sign-on solutions:| Resource | Use Case | Link |
|---|---|---|
| OAuth 2.0 / OpenID Connect | Token-based authentication flows | https://oauth.net/ / https://openid.net/connect/ |
| Okta SSO (Nginx Plus) | Enterprise SSO integration | https://www.okta.com/ |
| Active Directory | Windows AD integration | https://docs.microsoft.com/windows-server/identity/active-directory |
Installing the JavaScript module
Required by some advanced Nginx+ auth integrations:| OS | Command |
|---|---|
| Debian/Ubuntu | sudo apt install nginx-plus-module-js |
| RHEL/CentOS | sudo yum install nginx-plus-module-js |
nginx.conf:
By following these steps, you’ve added HTTP Basic Authentication to your Nginx server and explored more robust alternatives for production. For further reading, see the official Nginx documentation and KodeKloud labs.