Enhance your Jenkins CI/CD workflow by integrating a custom TrivyScan shared library. This guide walks you through creating the library, configuring Jenkins, referencing a feature branch, invoking scan methods, handling common errors, and reviewing pipeline artifacts.
In this tutorial we will cover:
Creating the TrivyScan Groovy script
Configuring a global trusted library in Jenkins
Referencing a feature branch in the Jenkinsfile
Invoking library methods (vulnerability and reportsConverter)
Handling “method calls not allowed” errors
Reviewing the final pipeline run and published artifacts
1. TrivyScan Groovy Script Start by creating a new Git branch and adding the TrivyScan.groovy file under vars/. This shared library defines two methods:
git checkout -b featureTrivyScan
// vars/TrivyScan.groovy def vulnerability ( String imageName ) { sh """ echo "Scanning image: ${ imageName } " trivy image ${ imageName } \ --severity LOW,MEDIUM,HIGH \ --exit-code 0 \ --quiet \ --format json \ -o trivy-image-MEDIUM-results.json trivy image ${ imageName } \ --severity CRITICAL \ --exit-code 1 \ --quiet \ --format json \ -o trivy-image-CRITICAL-results.json """ } def reportsConverter () { sh """ trivy convert \ --format template \ --template "@/usr/local/share/trivy/templates/html.tpl" \ --output trivy-image-MEDIUM-results.html \ trivy-image-MEDIUM-results.json trivy convert \ --format template \ --template "@/usr/local/share/trivy/templates/html.tpl" \ --output trivy-image-CRITICAL-results.html \ trivy-image-CRITICAL-results.json trivy convert \ --format template \ --template "@/usr/local/share/trivy/templates/junit.tpl" \ --output trivy-image-MEDIUM-results.xml \ trivy-image-MEDIUM-results.json trivy convert \ --format template \ --template "@/usr/local/share/trivy/templates/junit.tpl" \ --output trivy-image-CRITICAL-results.xml \ trivy-image-CRITICAL-results.json """ }
Method Name Purpose Output Files vulnerability Scan Docker image for vulnerabilities trivy-image-MEDIUM-results.json, trivy-image-CRITICAL-results.jsonreportsConverter Convert JSON scan reports to HTML and JUnit trivy-image-MEDIUM-results.html, trivy-image-CRITICAL-results.html, *.xml
Branching allows you to test changes in featureTrivyScan without affecting your main pipeline.
As a Jenkins administrator:
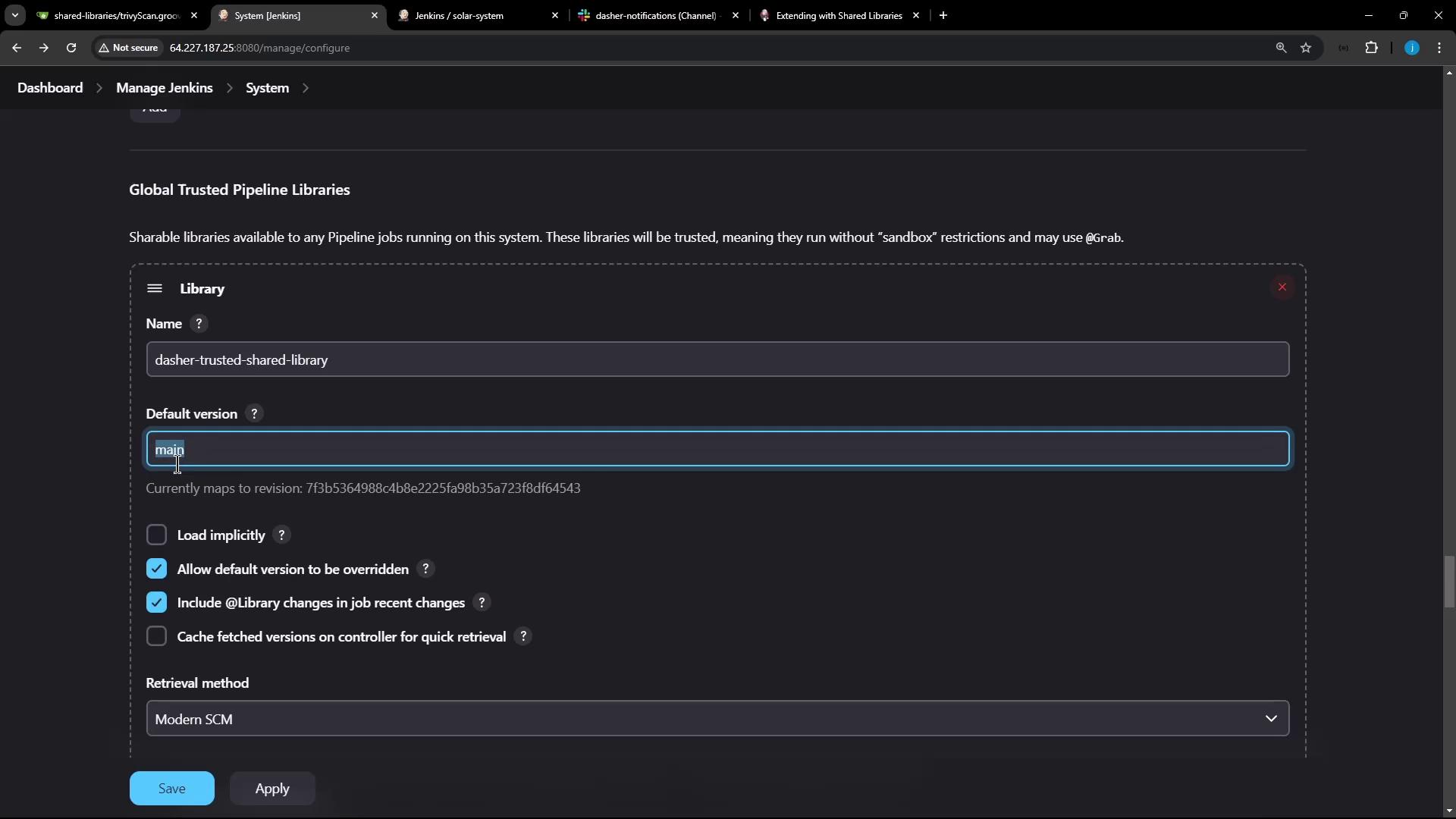
Navigate to Manage Jenkins > Configure System > Global Pipeline Libraries .
Add a new library:
Name: dasher-trusted-shared-library
Default version: main
Allow default version to be overridden : Enabled
Enabling “default version override” lets you specify feature branches like featureTrivyScan in your Jenkinsfile.
3. Reference the Feature Branch in Your Jenkinsfile At the top of your Jenkinsfile, use the @Library annotation to load the shared library from the featureTrivyScan branch:
@Library ( 'dasher-trusted-shared-library@featureTrivyScan' ) _
Define the rest of your declarative pipeline:
pipeline { agent any tools { // Define tools here if needed } environment { MONGO_URI = "mongodb+srv://.../superData" MONGO_DB_CREDS = credentials( 'mongo-db-credentials' ) SONAR_SCANNER_HOME = tool 'sonarqube-scanner-610' GITEA_TOKEN = credentials( 'gitea-api-token' ) } stages { stage( 'Install Dependencies' ) { options { timestamps() } steps { // Your dependency install steps } } stage( 'Build Docker Image' ) { steps { sh 'docker build -t siddharth67/solar-system:$GIT_COMMIT .' } } stage( 'Trivy Vulnerability Scanner' ) { steps { script { trivyScan . vulnerability( "siddharth67/solar-system: $GIT_COMMIT " ) } } post { always { script { trivyScan . reportsConverter() } publishHTML([ allowMissing : true , alwaysLinkToLastBuild : true , keepAll : true , reportDir : './' ]) } } } // stage('Push Docker Image') { ... } } }
4. Invoking Shared-Library Methods In declarative pipelines, all calls to shared-library methods (for example, trivyScan.vulnerability(...)) must be wrapped inside a script block:
script { trivyScan . vulnerability( "your/image:tag" ) }
5. Handling Common “Method Calls Not Allowed” Errors If you encounter an error like:
Method calls on objects not allowed outside "script" blocks.
ensure you’ve moved every shared-library invocation into a script { ... } section, as shown above.
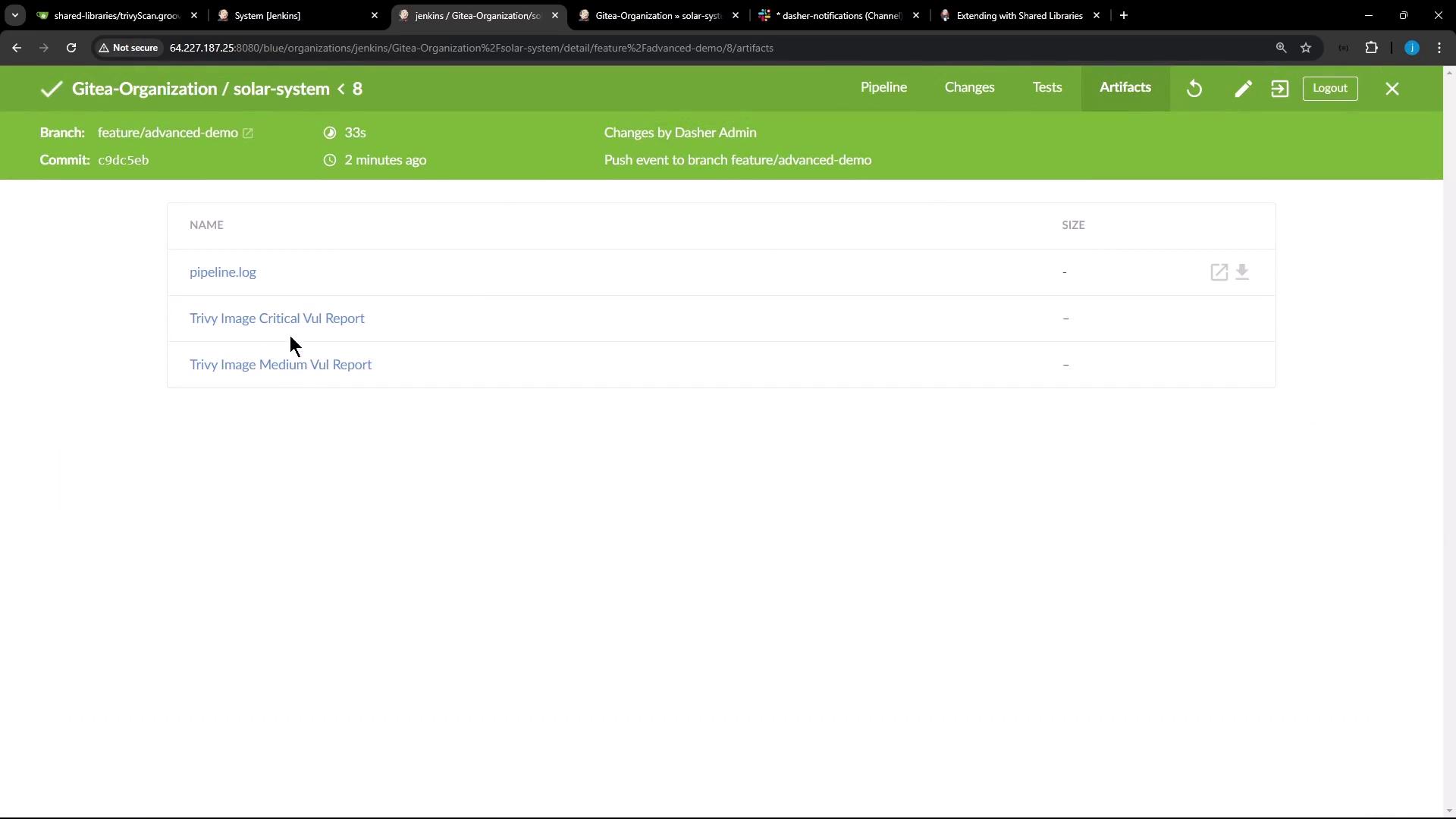
6. Reviewing Pipeline Run and Artifacts Once you push your updated Jenkinsfile, your pipeline (e.g., build #8) will:
Fetch your shared library from featureTrivyScan
Execute Trivy vulnerability scans
Convert JSON results into HTML/JUnit reports
Console snippet:
> git fetch ... origin/featureTrivyScan > git checkout -f refs/remotes/origin/featureTrivyScan ... trivy image siddharth67/solar-system: < commi t > --severity LOW,MEDIUM,HIGH ... trivy image siddharth67/solar-system: < commi t > --severity CRITICAL ... trivy convert --format template ... html.tpl ...
Artifacts include JSON, HTML, and XML reports:
Summary
Add your Groovy methods under vars/TrivyScan.groovy.
Enable “default version override” in Jenkins global libraries.
Reference your feature branch with @Library.
Wrap all shared-library method calls in script blocks.
Use trivyScan.vulnerability(...) and trivyScan.reportsConverter() for scanning and report conversion.
Publish results with publishHTML.
By modularizing your vulnerability scanning logic into a shared library, you keep your Jenkinsfile clean, reusable, and easy to maintain.
Links and References