Securing Cluster Hosts
The security of your Kubernetes cluster begins with the hosts themselves. Protect your underlying infrastructure by following these practices:- Disable root access.
- Turn off password-based authentication.
- Enforce SSH key-based authentication.
- Implement additional measures to secure your physical or virtual systems.

API Server Access Control
The Kube API server is at the heart of Kubernetes operations because all cluster interactions—whether via the kubectl command-line tool or directly through API calls—pass through it. Effective access control is essential, focusing on two key questions:- Who can access the cluster?
- What actions are they permitted to perform?
Authentication
Authentication verifies the identity of a user or service before granting access to the API server. Kubernetes offers various authentication mechanisms to suit different security needs:- Static user IDs and passwords
- Tokens
- Client certificates
- Integration with external authentication providers (e.g., LDAP)

Authorization
After authentication, authorization determines what actions a user or service is allowed to perform. The default mechanism, Role-Based Access Control (RBAC), associates identities with specific permissions. Kubernetes also supports:- Attribute-Based Access Control (ABAC)
- Node Authorization
- Webhook-based authorization

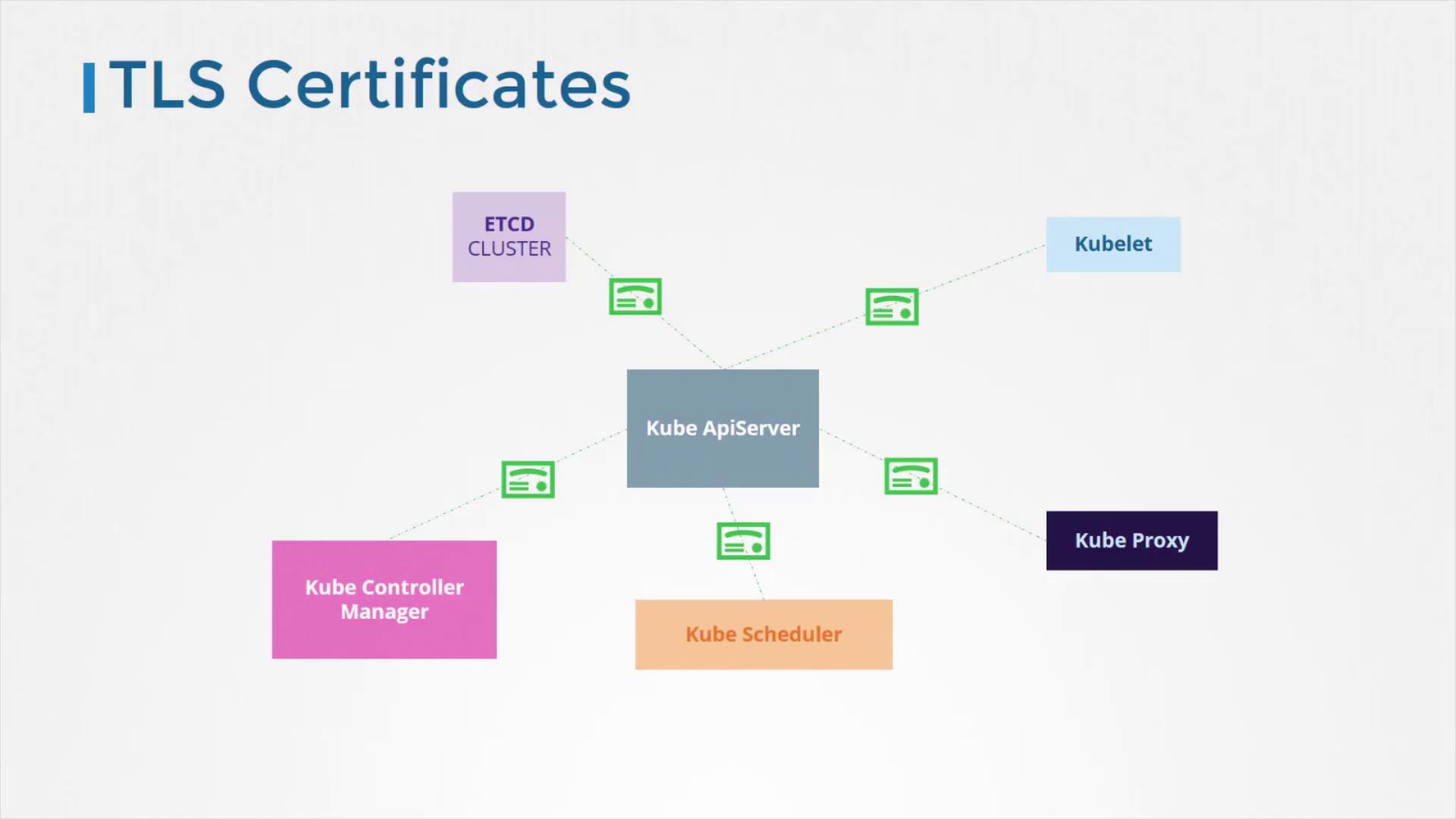
Securing Component Communications
Secure communications between Kubernetes components are enabled via TLS encryption. This ensures that data transmitted between key components remains confidential and tamper-proof. Encryption protects:- Communication within the etcd cluster
- Interactions between the Kube Controller Manager and Kube Scheduler
- Links between worker node components such as the Kubelet and Kube Proxy
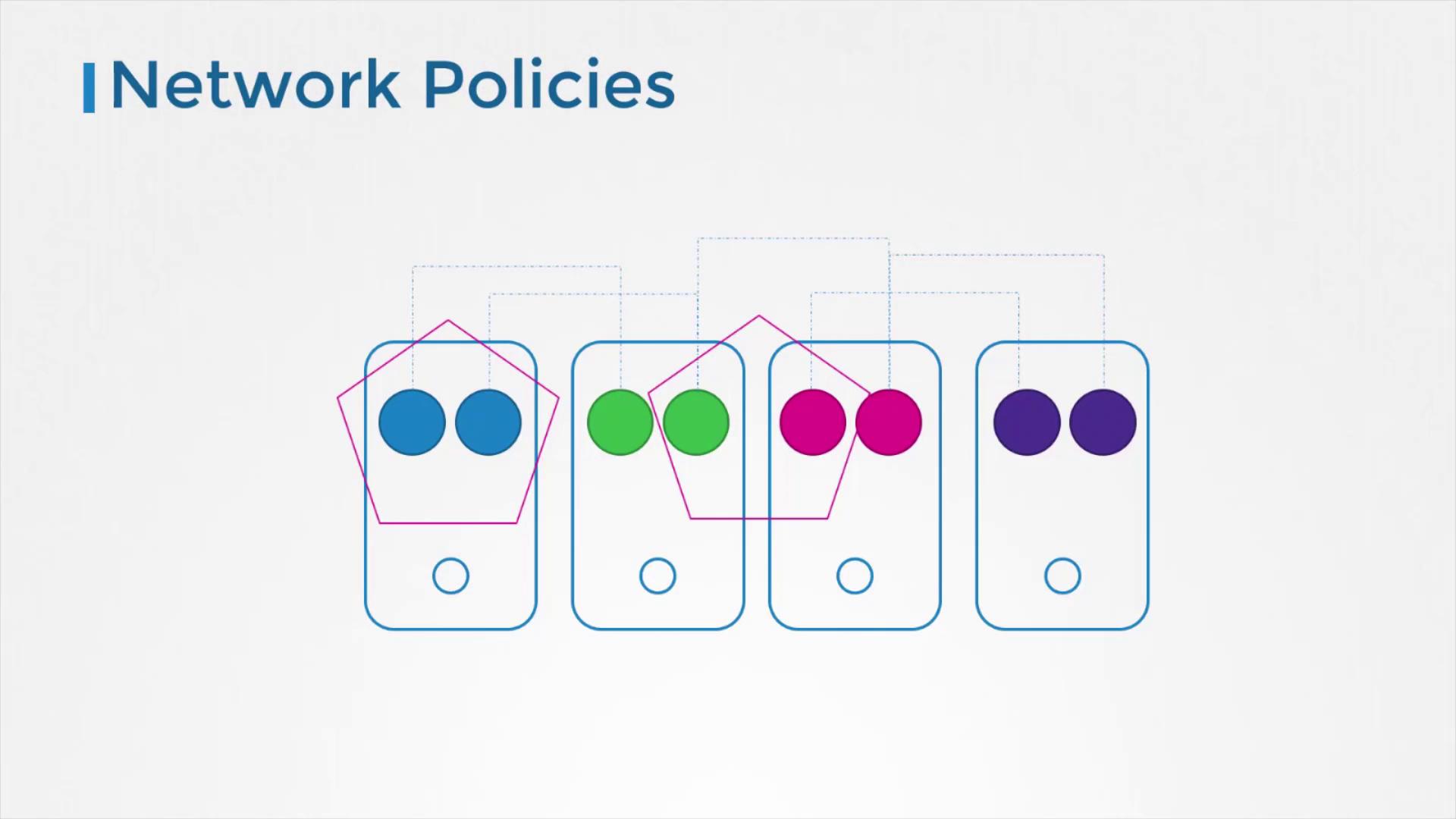
Network Policies
By default, pods in a Kubernetes cluster communicate freely with one another. To restrict unwanted interactions and enhance security, Kubernetes provides network policies. These policies allow you to:- Control traffic flow between specific pods
- Enforce security rules at the network level
For a secure Kubernetes environment, consider combining these security primitives with additional best practices and tools to counter evolving threats.