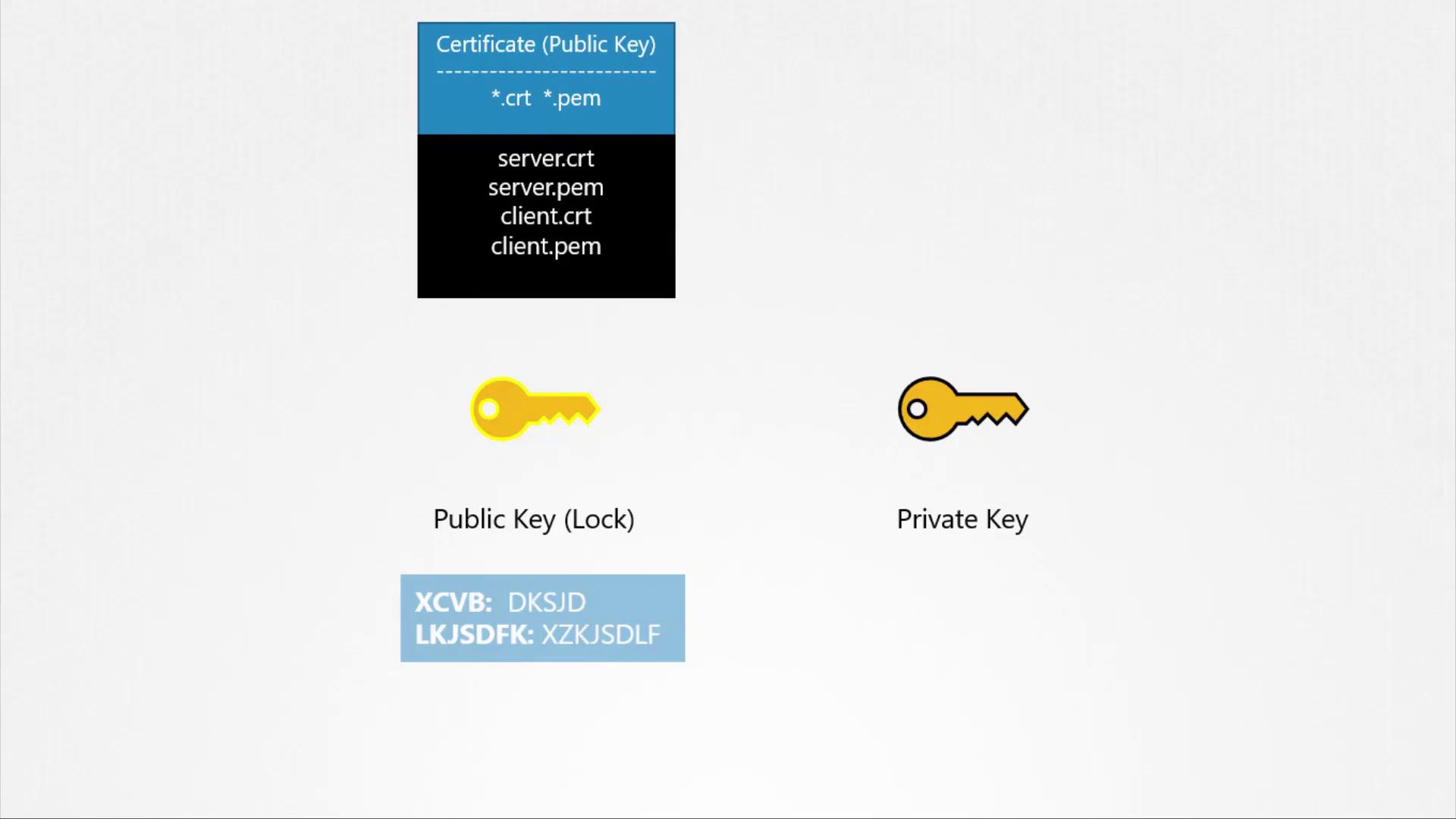
- The server generates a key pair (private and public keys).
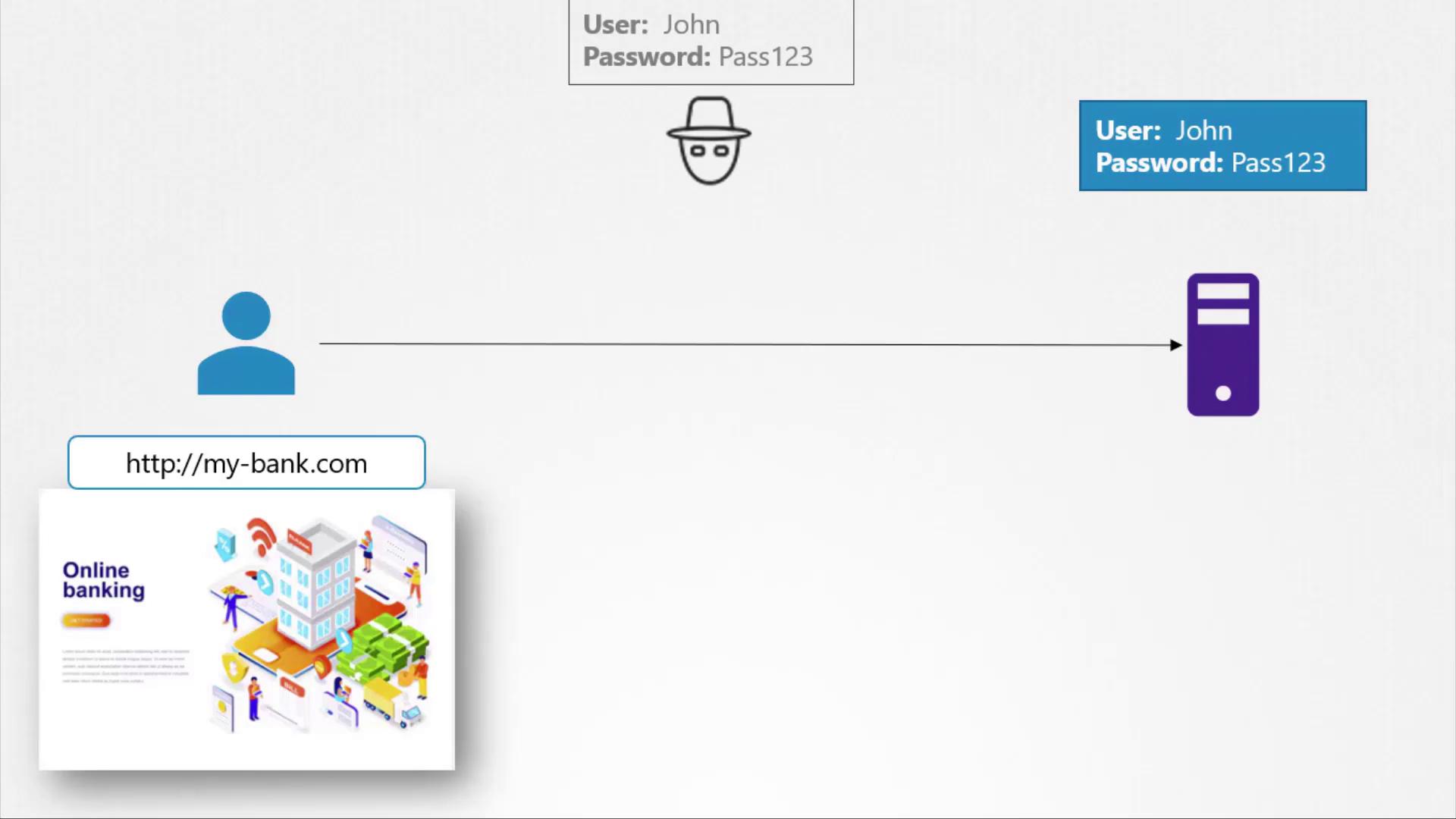
- Upon a user’s initial HTTPS request, the server sends its public key embedded within a certificate.
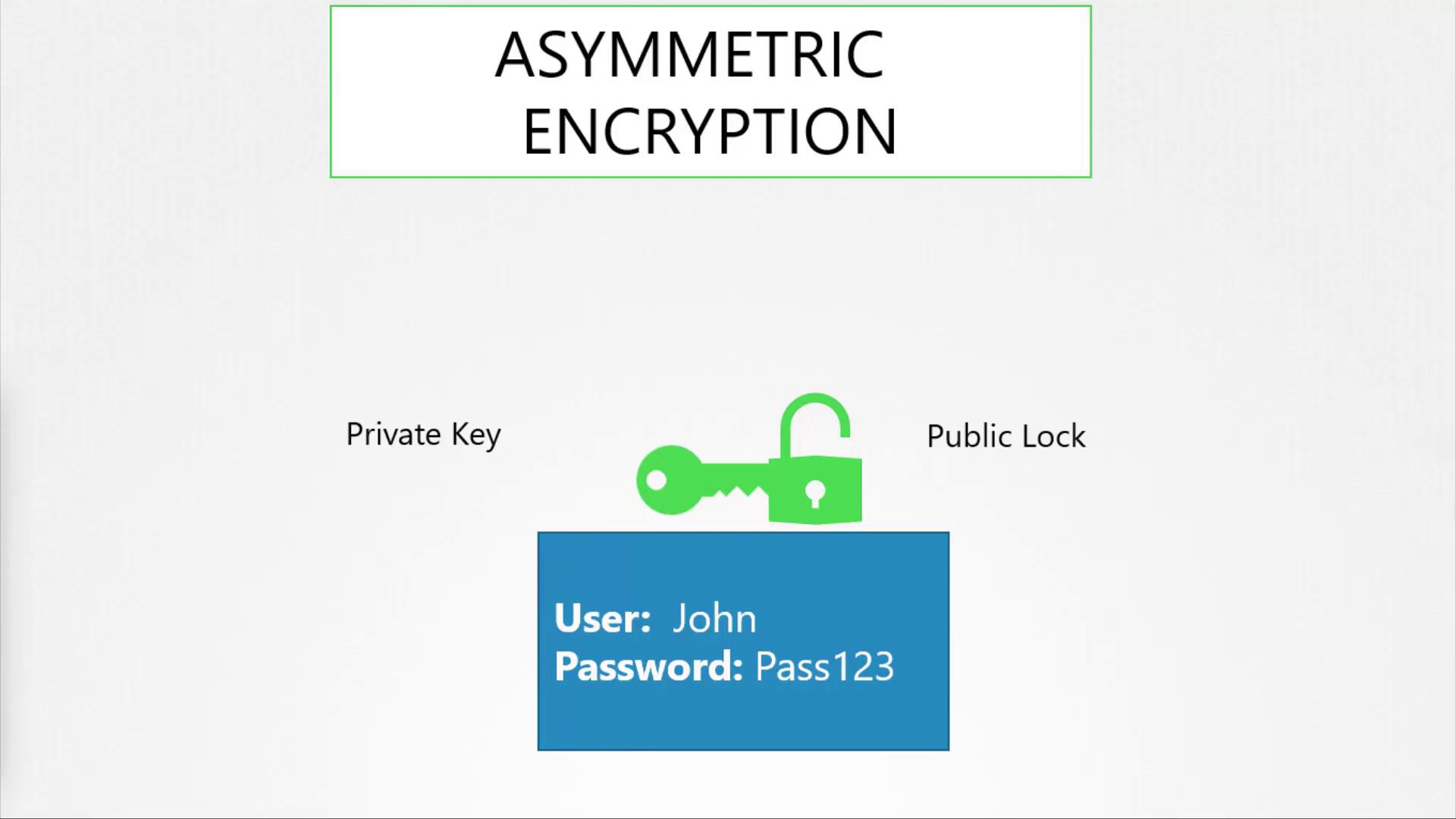
- The client’s browser encrypts a newly generated symmetric key using the server’s public key.
- The encrypted symmetric key is sent back to the server.
- The server decrypts the symmetric key using its private key.
- All subsequent communications are encrypted with this symmetric key.
- Identity of the issuing authority
- The server’s public key
- Domain and other related information

- The server presents the certificate.
- The browser validates it using pre-installed CA public keys.
- Upon successful validation, the browser and server establish a secure session using a symmetric key exchanged via asymmetric encryption.
- Asymmetric encryption uses a pair of keys (public and private) to securely exchange symmetric keys.
- SSH access is secured using key pairs.
- Web servers use CA-signed certificates to establish HTTPS connections.
- A Certificate Signing Request (CSR) is generated and sent to a CA for signing.
- Signed certificates, combined with the server’s key pair, secure the communication session. :::