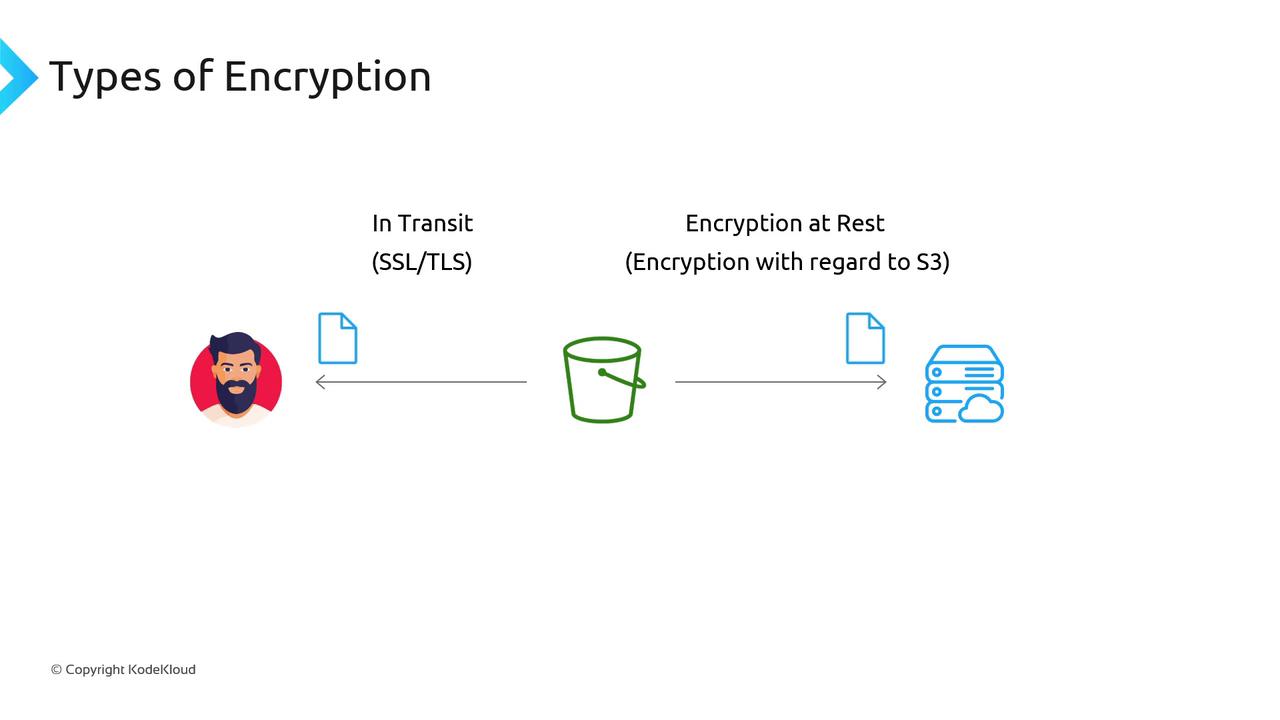
When working with S3, always consider encryption at two critical stages:
- Encryption in Transit – Data is automatically encrypted using SSL/TLS protocols (the same technology behind HTTPS) when uploading or retrieving files from an S3 bucket.
- Encryption at Rest – Once data is stored, S3 encrypts it on AWS-hosted servers to ensure that even if the storage media is compromised, the data remains protected.
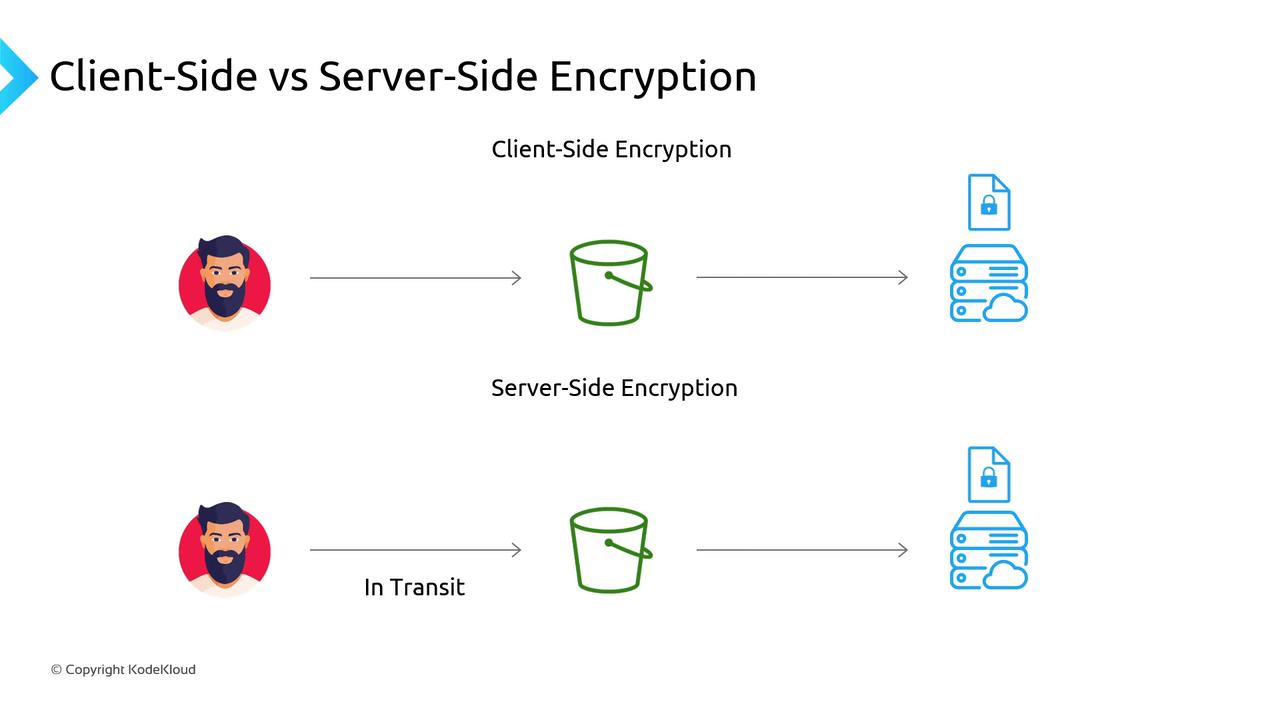
In this method, you generate the encryption keys and encrypt your files locally before uploading them to S3. Although this approach gives you full control over the encryption process, it also means that you are solely responsible for key management and the encryption/decryption processes. • Server-Side Encryption
With server-side encryption, you send your unencrypted data to S3—secured by SSL/TLS in transit—and then S3 encrypts your data before storing it. Server-side encryption comes in three distinct methods: – SSE-S3 (Server-Side Encryption with Amazon S3 Managed Keys)
AWS manages both the encryption keys and the entire encryption/decryption process. Each object is encrypted with a unique key, which is itself encrypted using a root key managed by AWS. – SSE-C (Server-Side Encryption with Customer-Provided Keys)
You provide your own key during the upload process. While S3 handles the actual encryption and decryption, you must manage the key and supply it with each request. – SSE-KMS (Server-Side Encryption with AWS Key Management Service Keys)
This method gives you enhanced key management control. AWS KMS generates and manages the keys, allowing you to set key policies and monitor key usage. S3 still handles the encryption and decryption processes.

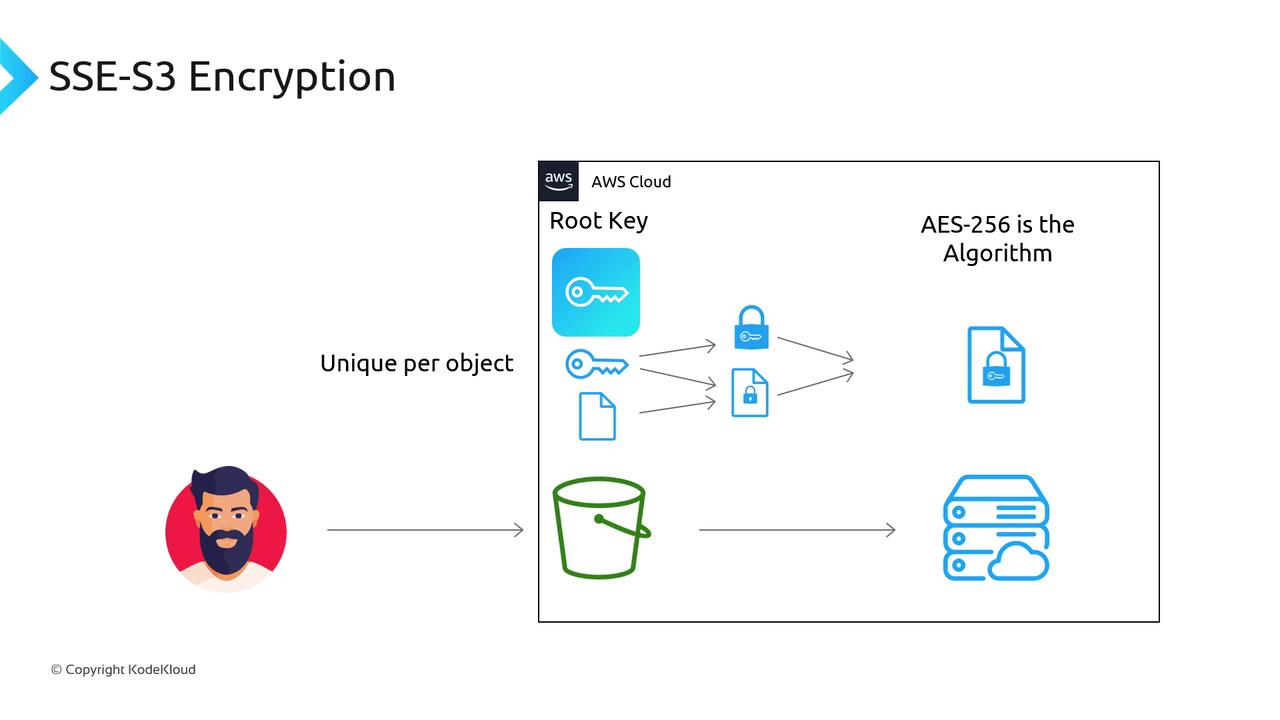
SSE-S3 (Server-Side Encryption with Amazon S3 Managed Keys)
In SSE-S3, AWS handles the complete encryption process:- When you upload a file, S3 uses a hidden root key to generate a unique encryption key for that particular object.
- The object is encrypted using the AES-256 encryption algorithm.
- The unique encryption key is then itself encrypted with the root key and stored together with the encrypted object.
- When you request the object, S3 decrypts the encryption key using the root key and then decrypts the object.
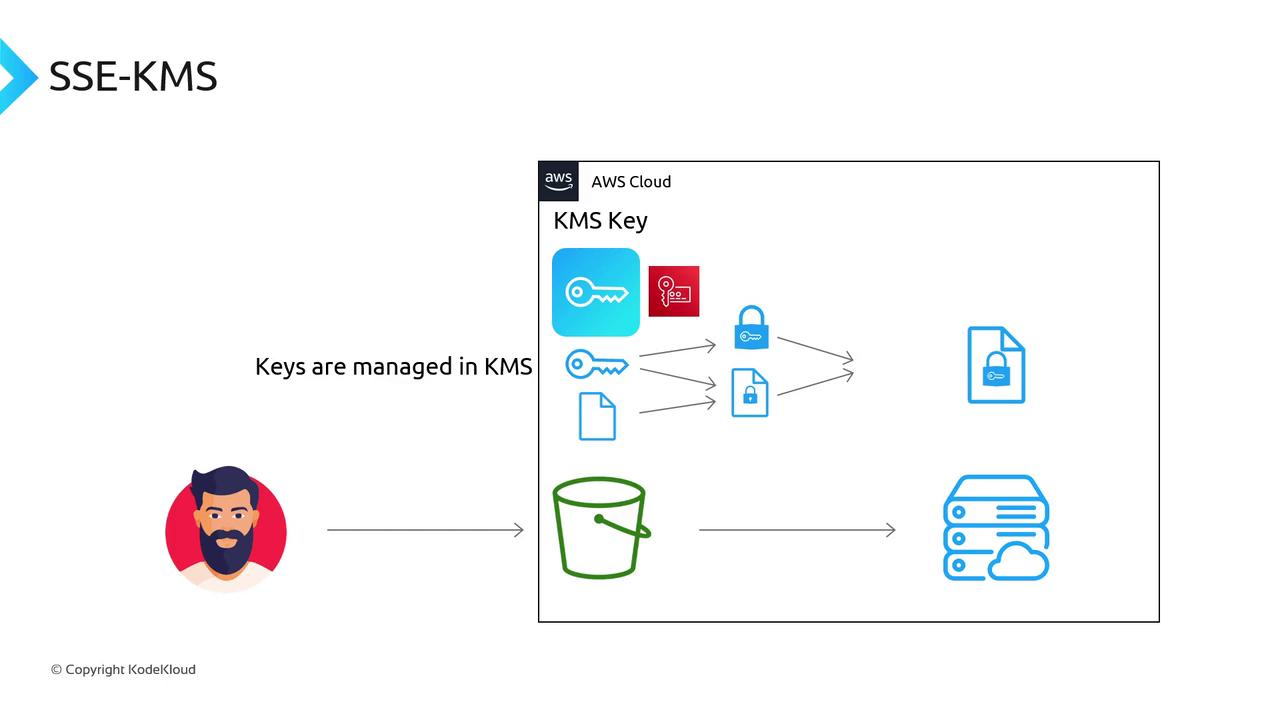
SSE-KMS (Server-Side Encryption with AWS Key Management Service)
SSE-KMS integrates closely with AWS Key Management Service to provide enhanced control over encryption keys:- AWS KMS manages key generation and storage, allowing you to define key policies and monitor key usage.
- When you upload a file, a KMS key is used to generate a unique encryption key that encrypts your object similar to SSE-S3.
- S3 manages the encryption and decryption, while the key management is fully handled by KMS.
SSE-C (Server-Side Encryption with Customer-Provided Keys)
With SSE-C, you are in control of providing the encryption key for file uploads:- You generate and securely manage your own encryption key prior to uploading.
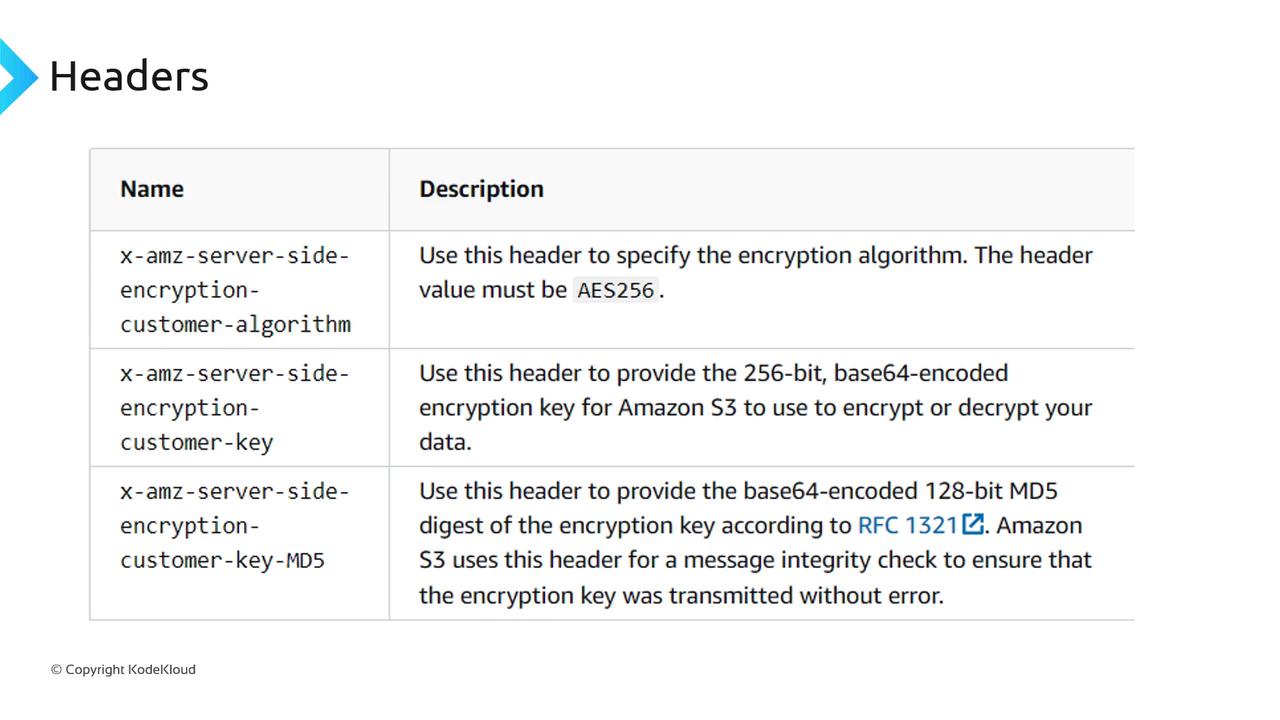
- During the upload process, you include headers that specify the encryption algorithm (typically AES-256), your encryption key, and the MD5 digest of the key to verify its integrity.
- S3 uses the provided key to encrypt the object and stores a hash of this key.
- When retrieving the object, you must supply the same encryption key so that S3 can decrypt the file.
Summary of Responsibilities
| Encryption Method | Key Generation & Management | Encryption/Decryption Responsibility |
|---|---|---|
| Client-Side Encryption | User-generated | Performed locally by the user |
| SSE-C | Customer-provided | S3 handles the process using provided keys |
| SSE-S3 | Managed by AWS | S3 performs encryption/decryption automatically |
| SSE-KMS | Managed by AWS KMS with user configuration | S3 performs encryption/decryption with KMS support |