AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is built with default resiliency at its core—similar to services like CloudWatch. IAM’s design ensures that it remains robust without requiring further tuning. Enhancing its reliability is unnecessary as any failure would jeopardize AWS operations.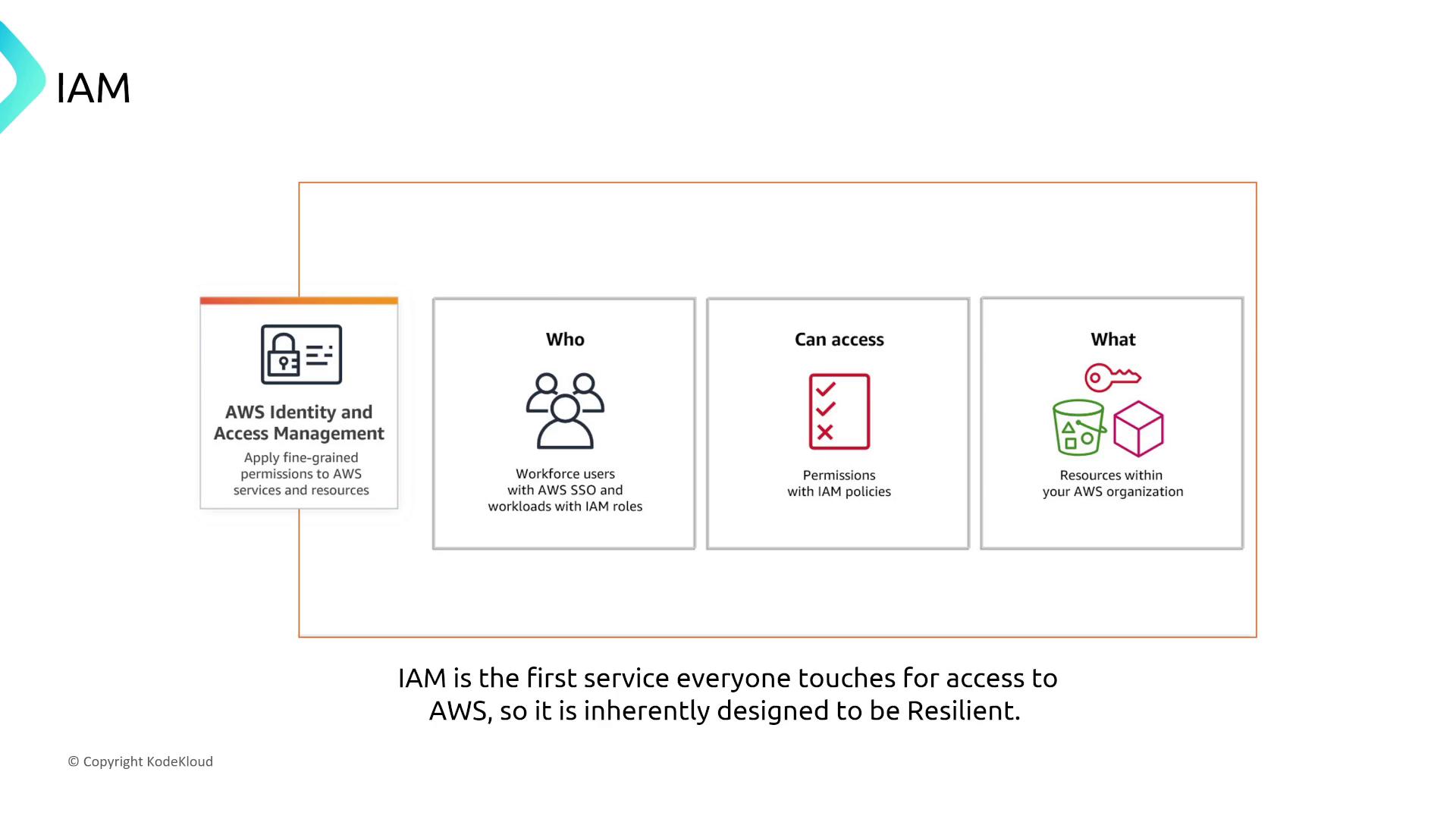
User Authentication with Amazon Cognito
Amazon Cognito offers a highly managed and fault-tolerant approach for user authentication in mobile and web applications. With built-in multi-resiliency, Cognito provides robust identity management without additional configuration.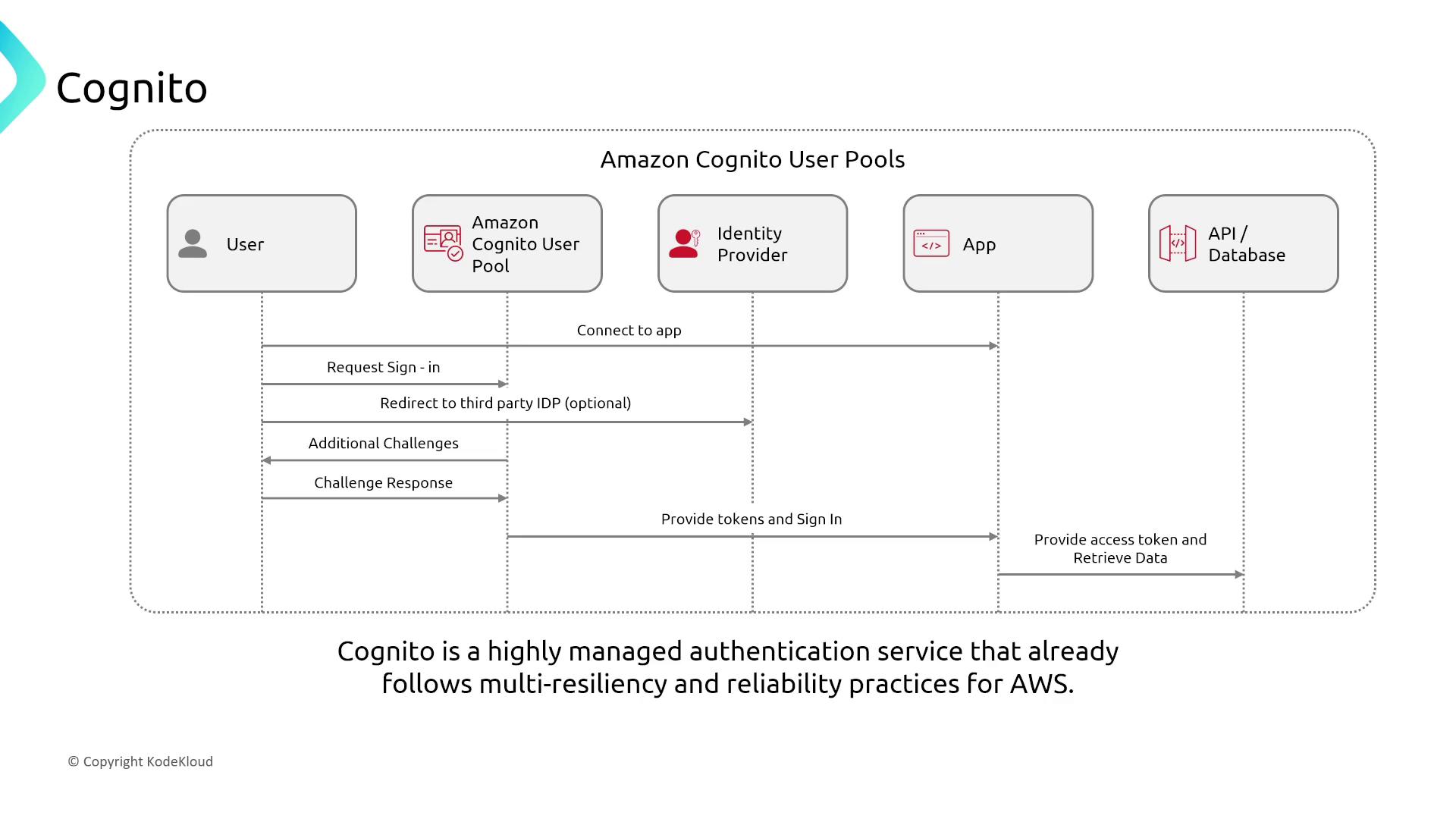
Verified Permissions
Verified Permissions allows you to enforce application access policies as code, ensuring adherence to least privilege principles. Its functionality is built to operate reliably, eliminating the need for further enhancements.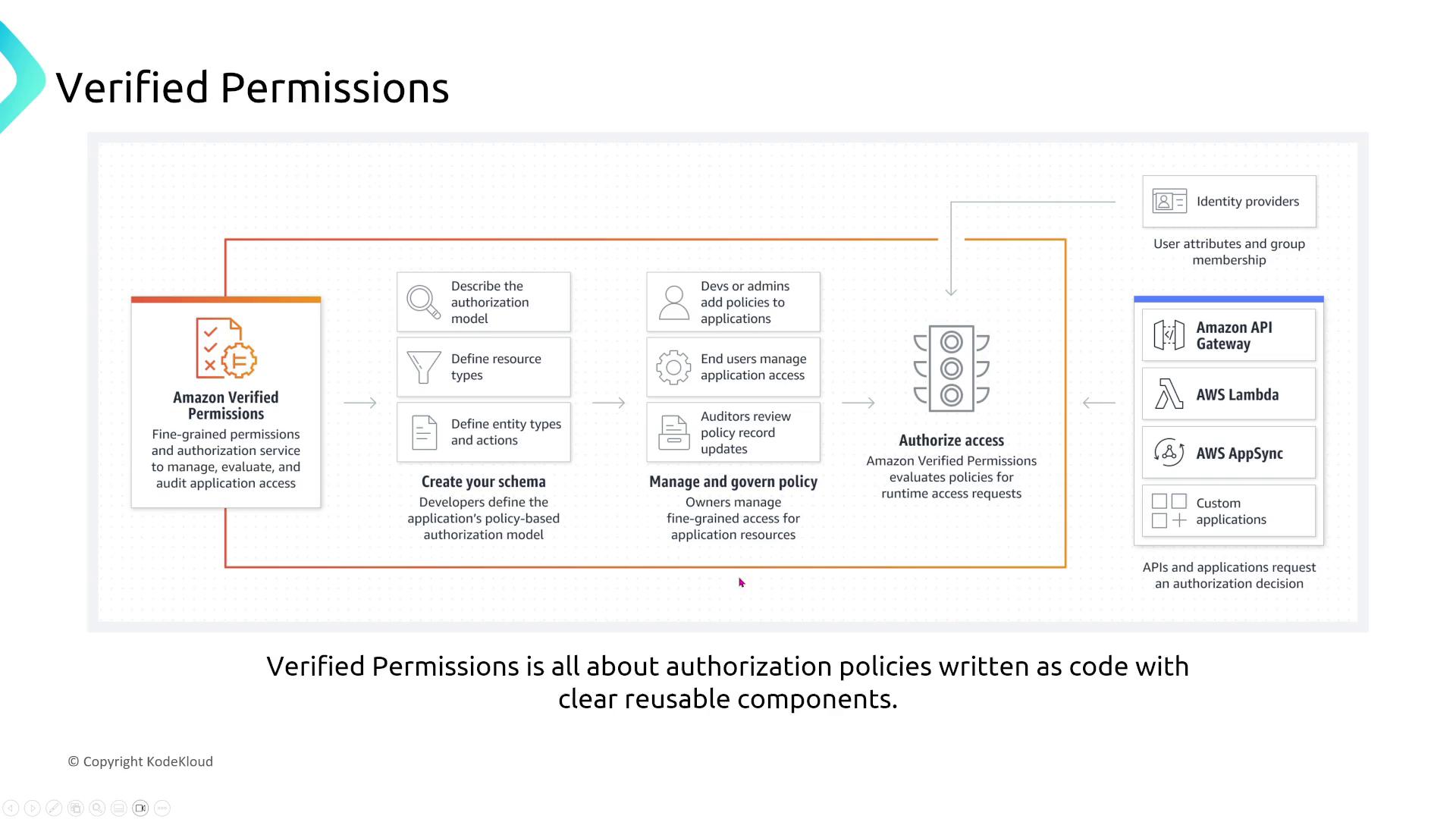
Auditing Services
AWS CloudTrail
AWS CloudTrail automatically captures all API calls and activities, providing a resilient auditing solution without further adjustments. Integration with CloudWatch, EventBridge, and other monitoring tools further enhances its observability.
AWS Config
AWS Config continuously monitors resource configurations, evaluating them against compliance baselines with inherent redundancy. Its built-in resiliency means that tracking non-compliance does not require additional manual adjustments.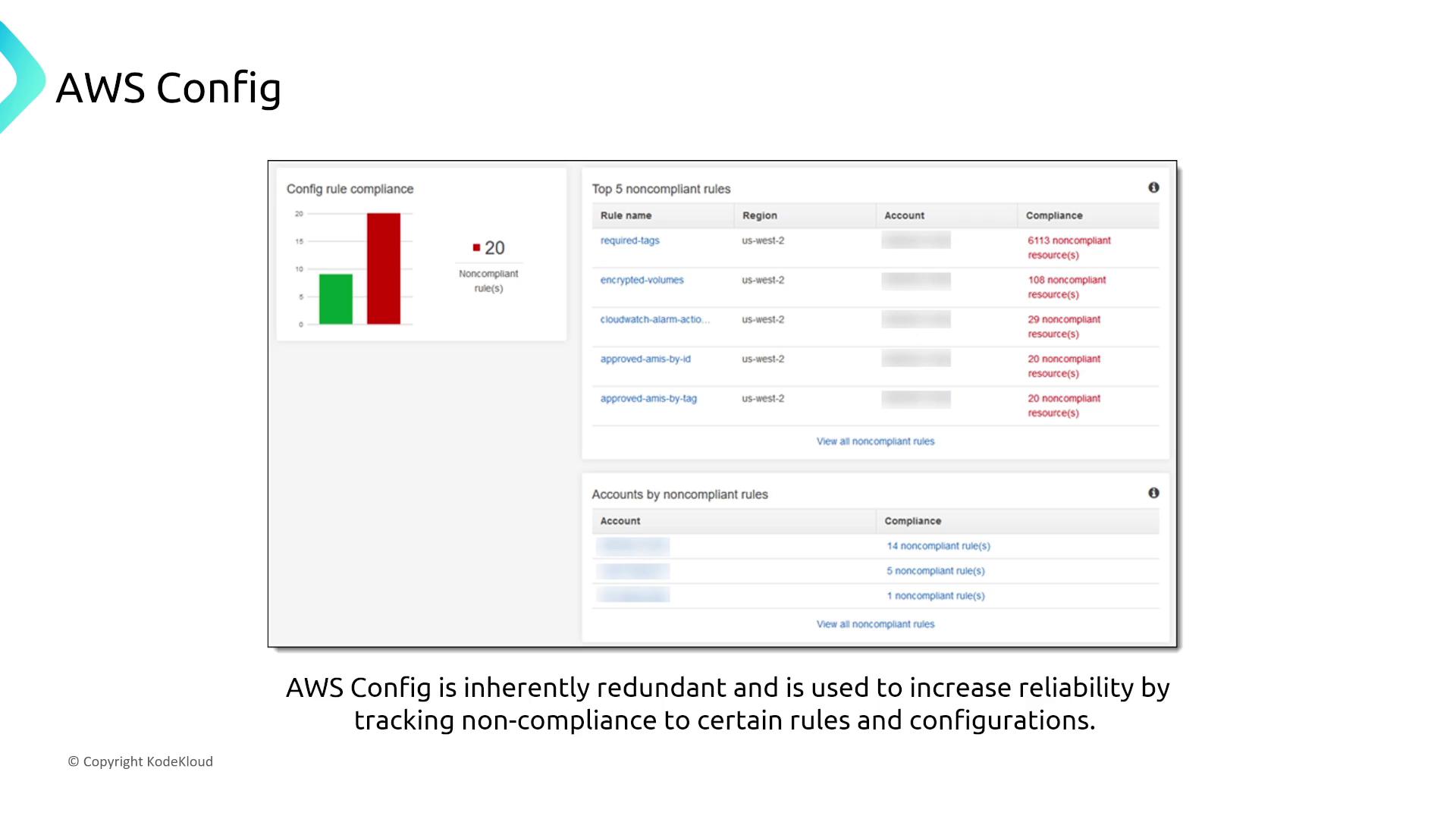
AWS Artifact
AWS Artifact provides a secure repository for compliance and attestation documents, without any active reliability tuning. Its role is solely to host essential documents while inheriting AWS’s overall infrastructure resiliency.
Threat Detection Services
Amazon GuardDuty
Amazon GuardDuty uses machine learning and anomaly detection to monitor network traffic and detect potential threats. Its inherent design provides seamless threat monitoring without requiring custom reliability configurations.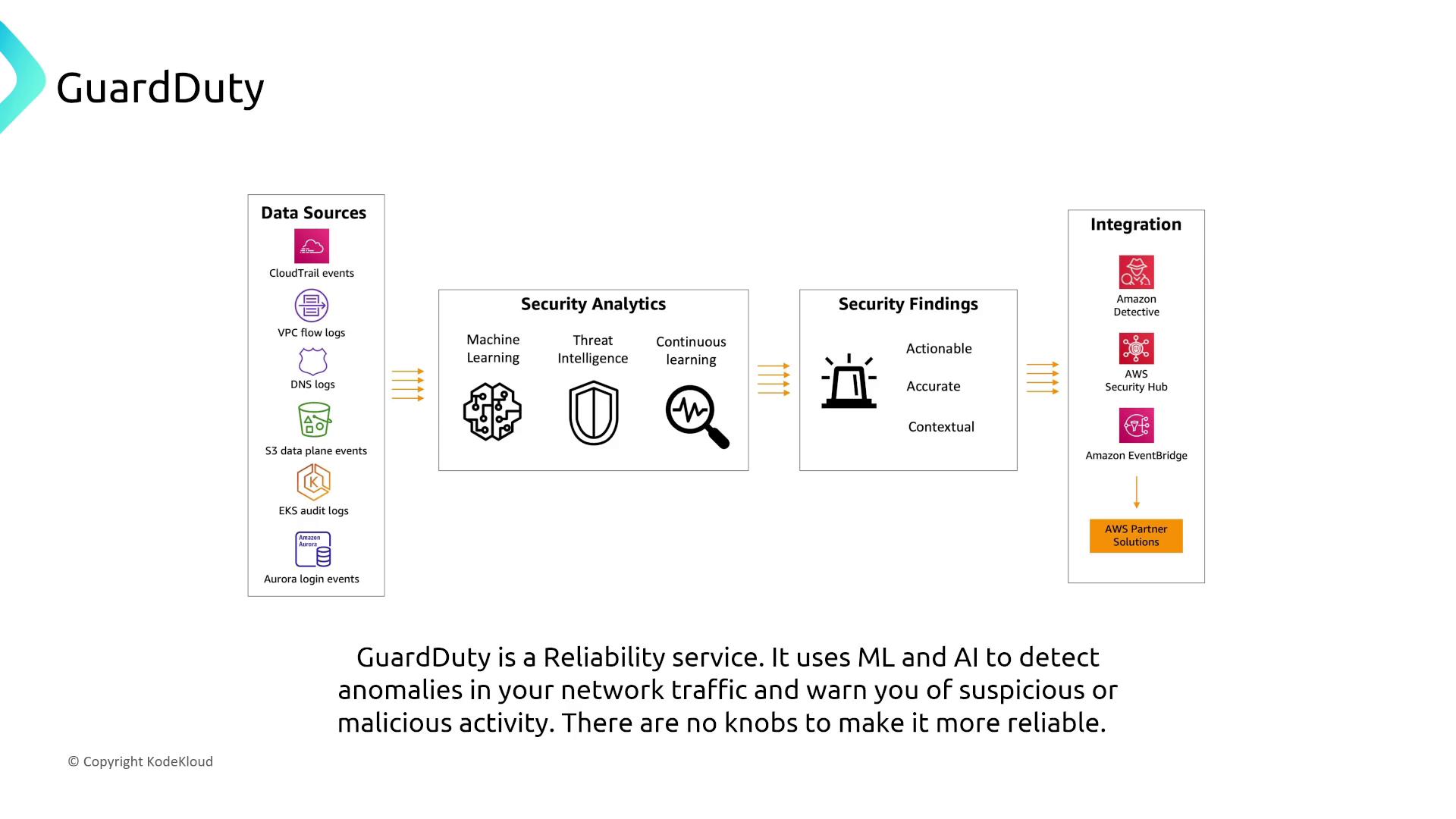
AWS Inspector
AWS Inspector performs automated vulnerability scanning across various AWS platforms, including Lambda, EC2, and container images in ECR. Its automated report generation and scanning are reliable by design.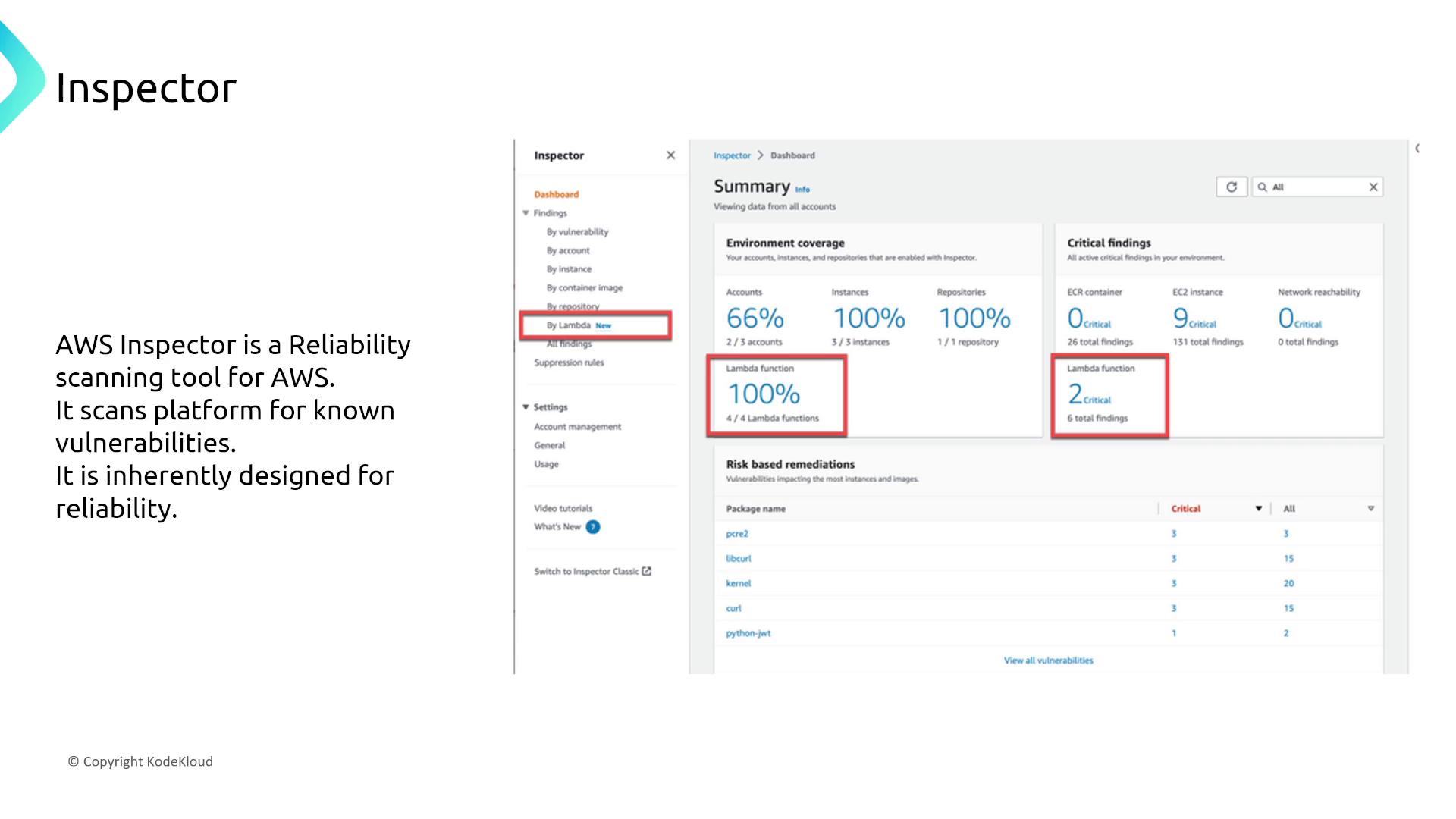
Amazon Macie
Amazon Macie utilizes advanced machine learning to detect and classify sensitive information in S3 buckets. Designed for fault tolerance, Macie requires no additional reliability tuning.
Reliability Hub
Reliability Hub aggregates security findings from various AWS services into a single, unified interface. This consolidation relies on the inherent reliability of the underlying services.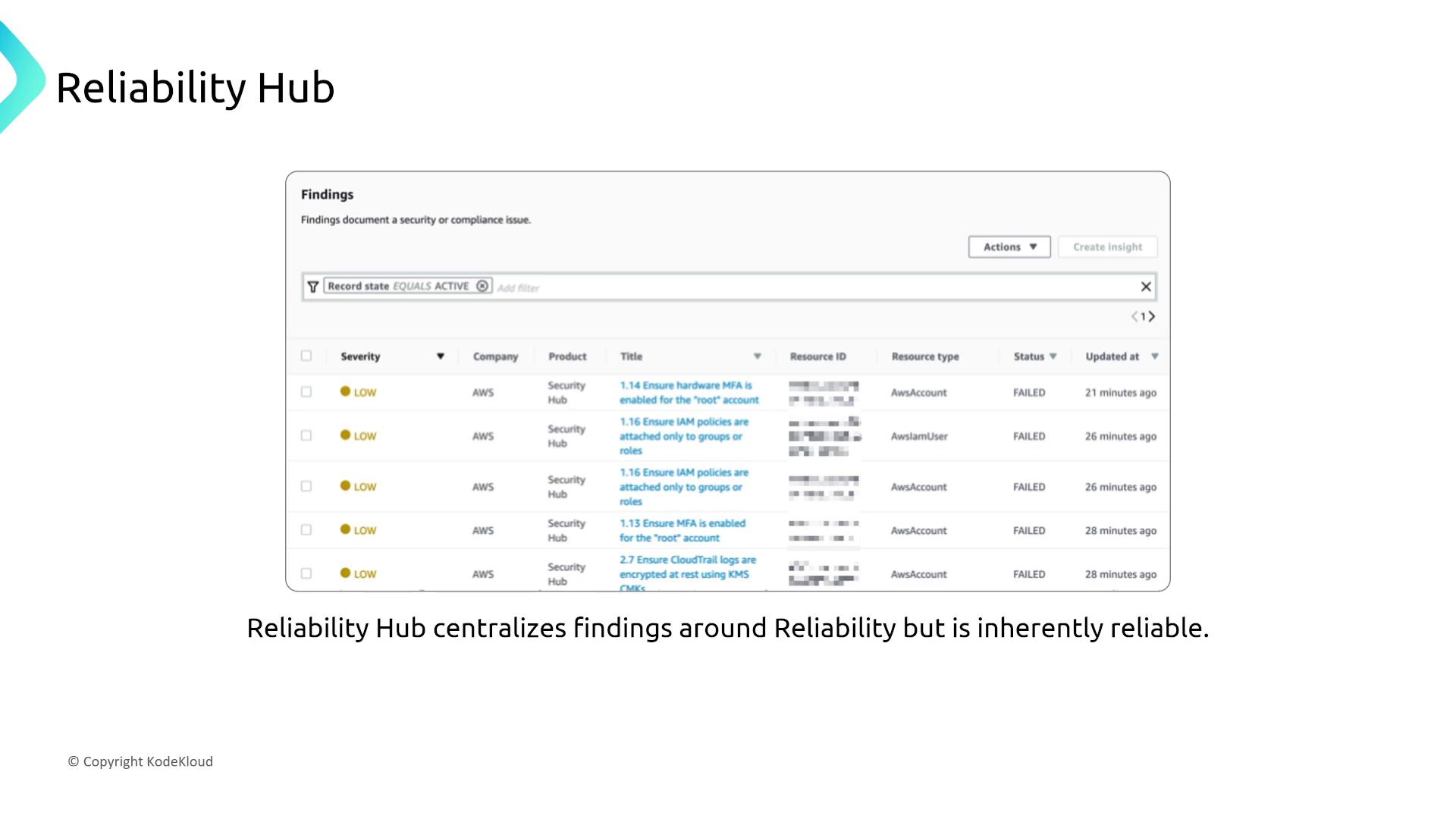
Encryption Services
AWS KMS and CloudHSM
AWS KMS offers a software-based solution for encryption key management with minimal administrative overhead. In contrast, CloudHSM, a hardware-based solution, enhances reliability through clustering and multi-AZ deployments for high availability and fault tolerance.
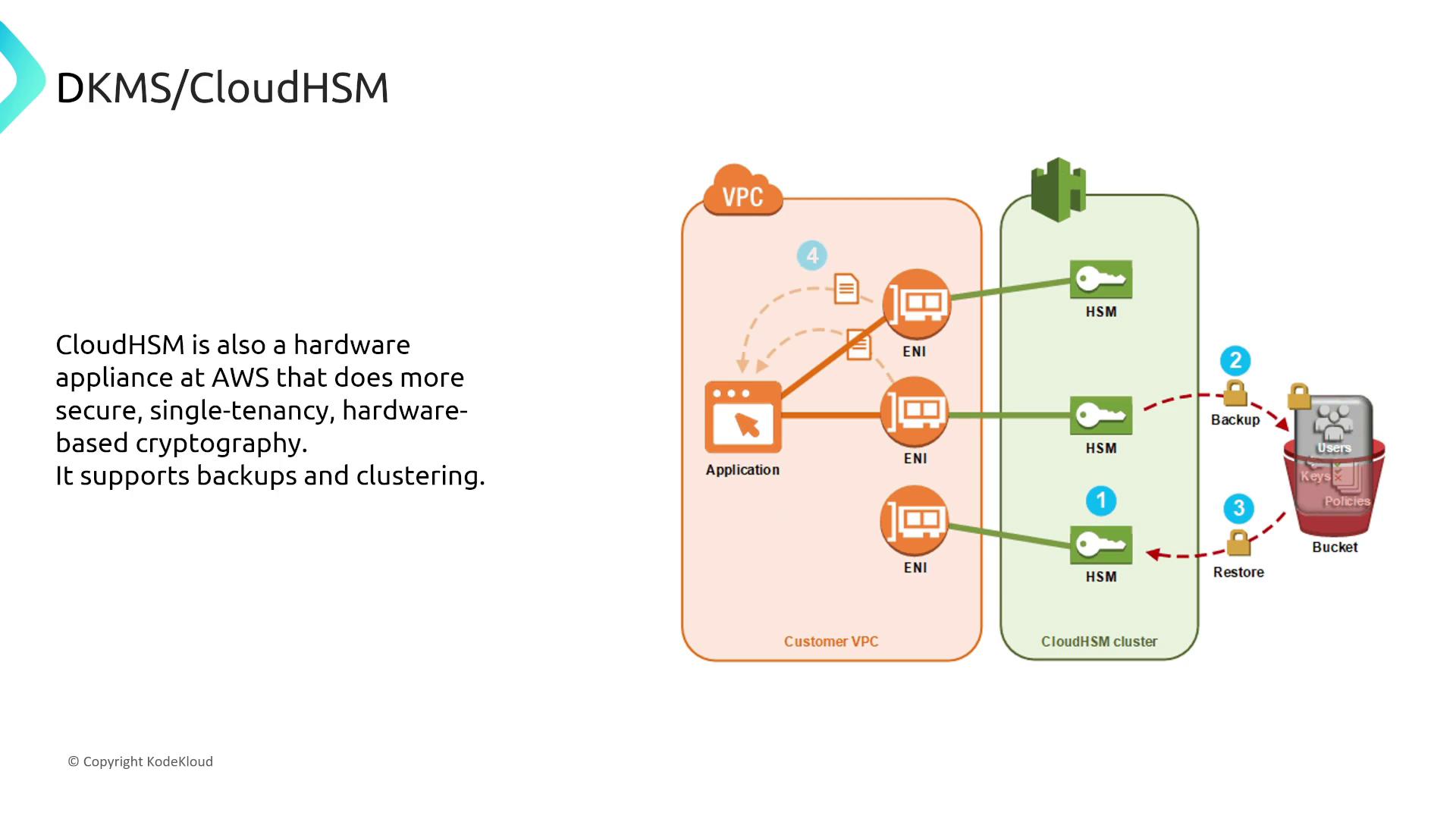
For organizations requiring dedicated hardware security modules with multi-AZ deployment and clustering for extra security assurance, CloudHSM is the optimal choice.
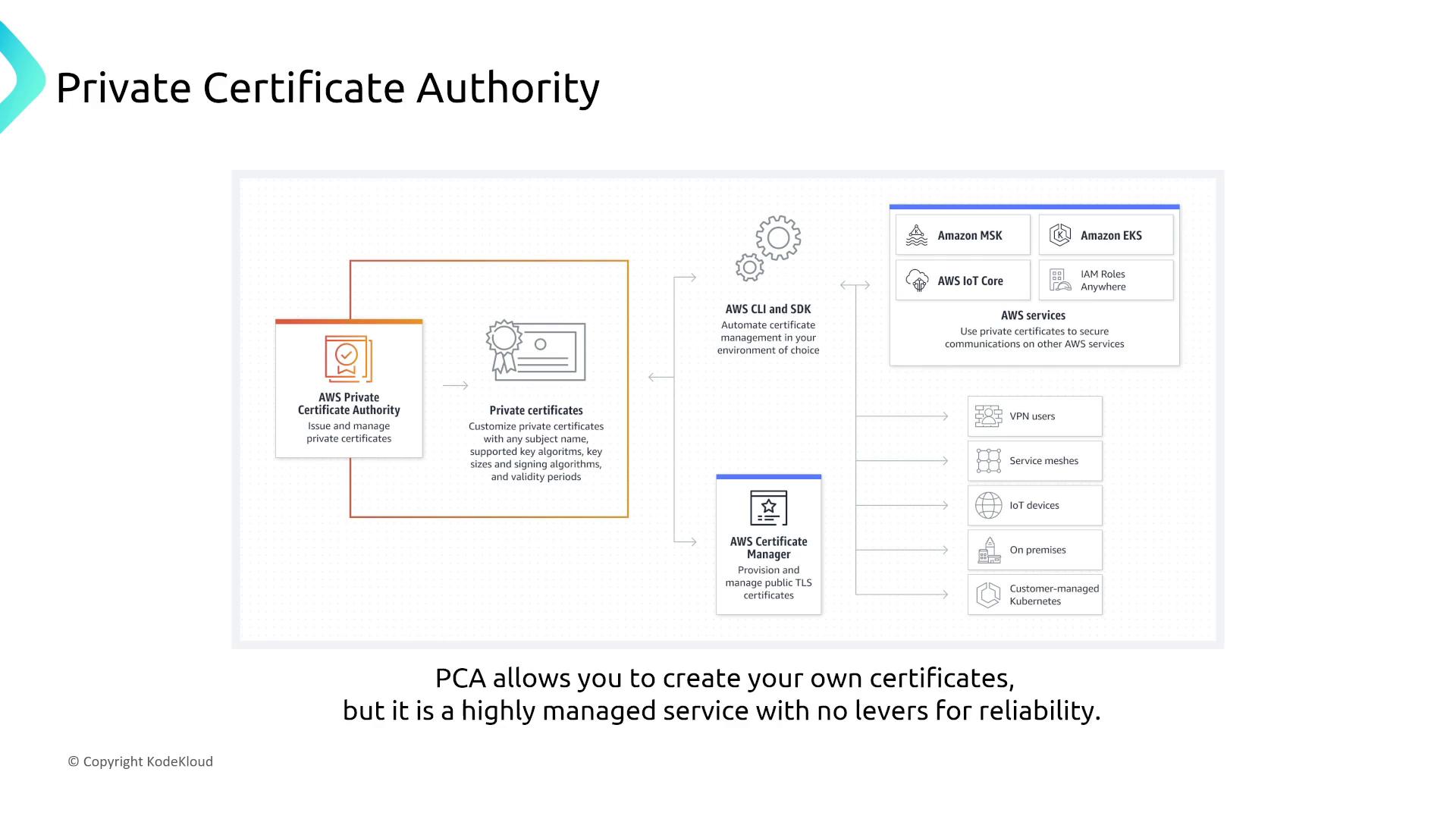
AWS Certificate Manager and AWS Private Certificate Authority
AWS Certificate Manager (ACM) and AWS Private Certificate Authority (PCA) offer managed services to simplify the deployment of certificates and private infrastructure. Both services come with built-in high availability, requiring no additional reliability tuning.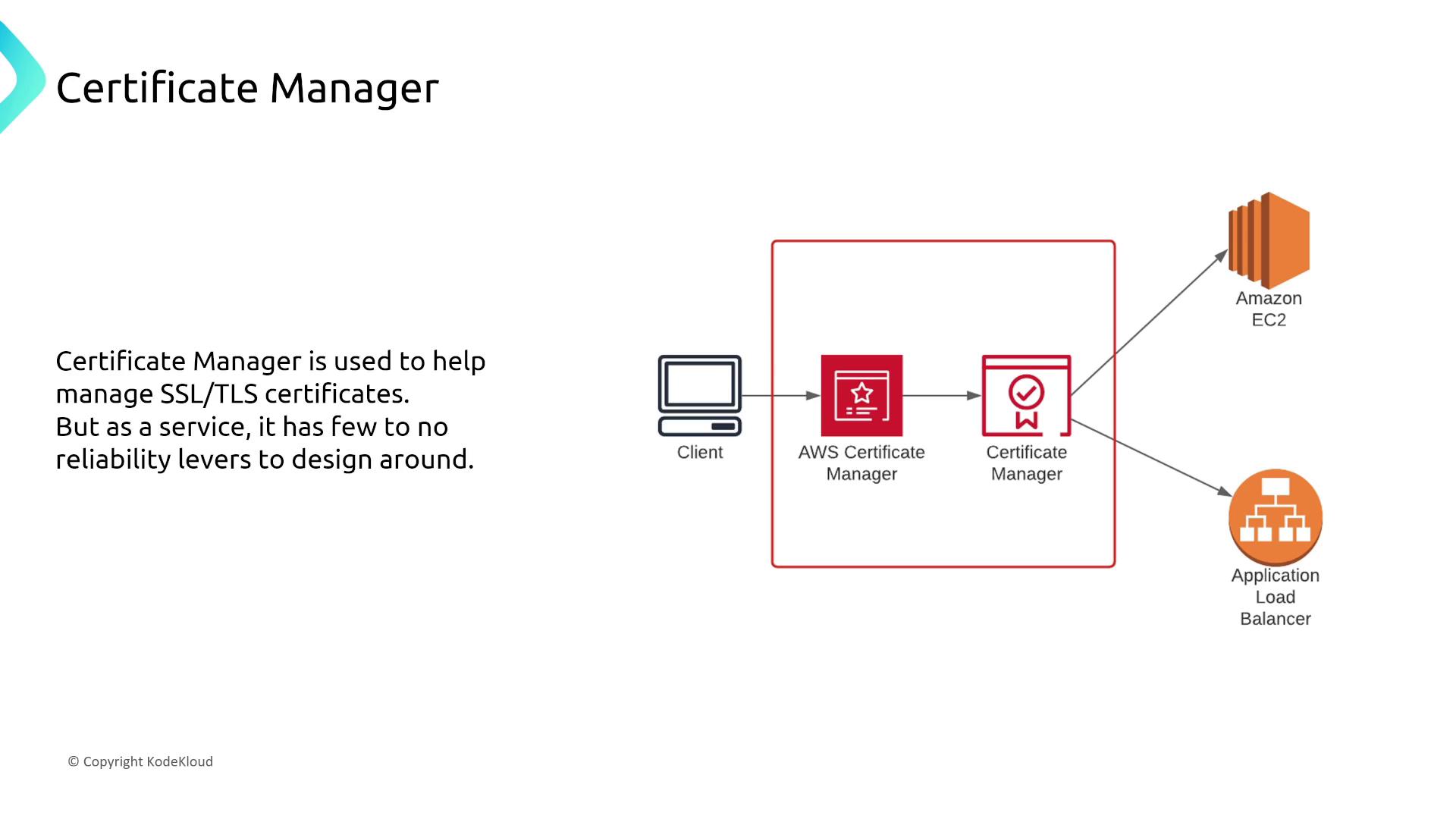
AWS Secrets Manager
AWS Secrets Manager ensures secure storage of sensitive information such as database credentials. Its primary mechanism for enhancing reliability is cross-region replication, which provides standby copies in other regions without additional configuration within a single region.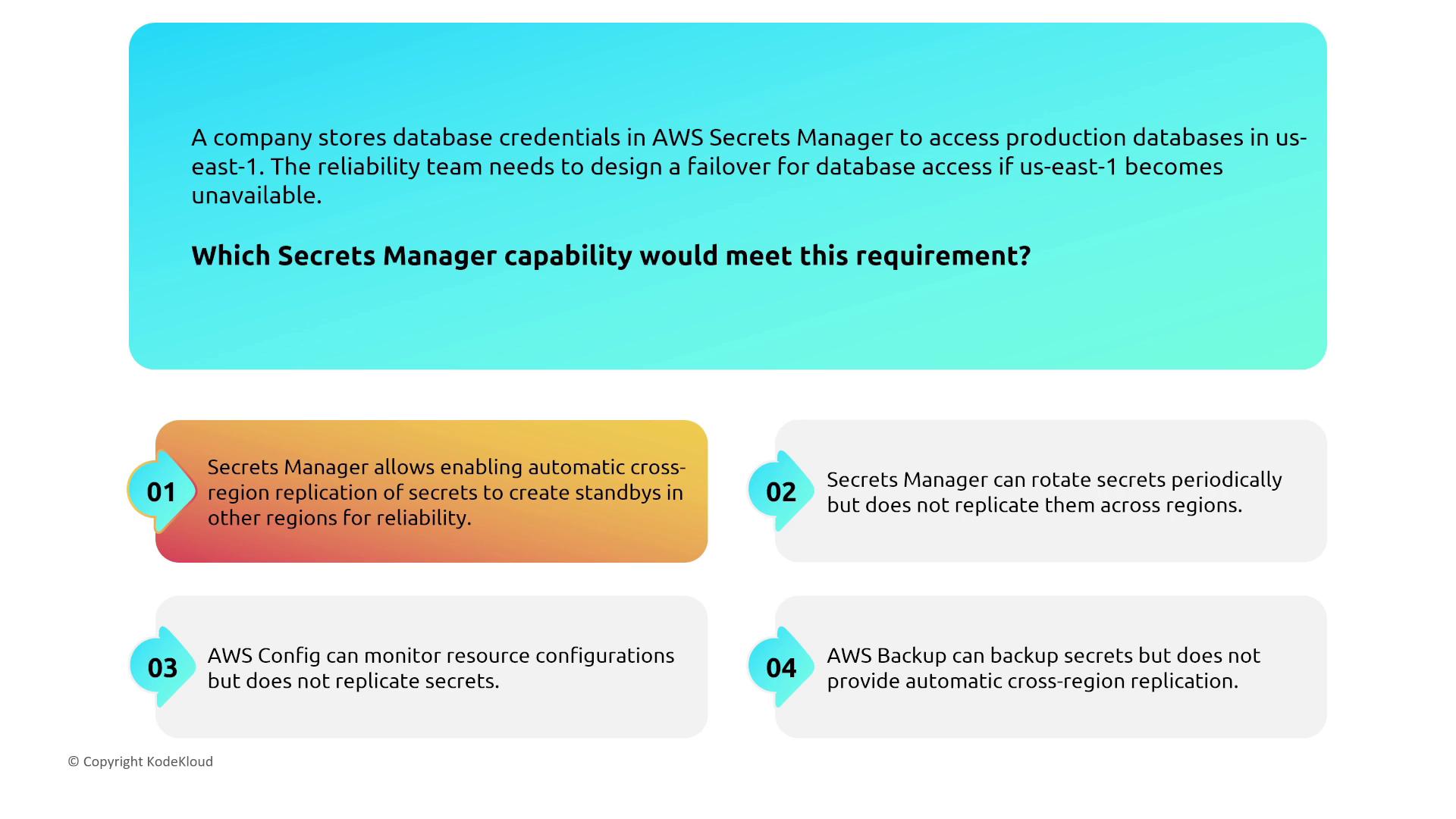
Network Security
Network Access Control Lists (NACLs) and Security Groups
Network ACLs and security groups function respectively as stateless and stateful firewalls inherently built with redundancy. In the unlikely event of an issue, a simple instance restart or contact with AWS support can restore functionality.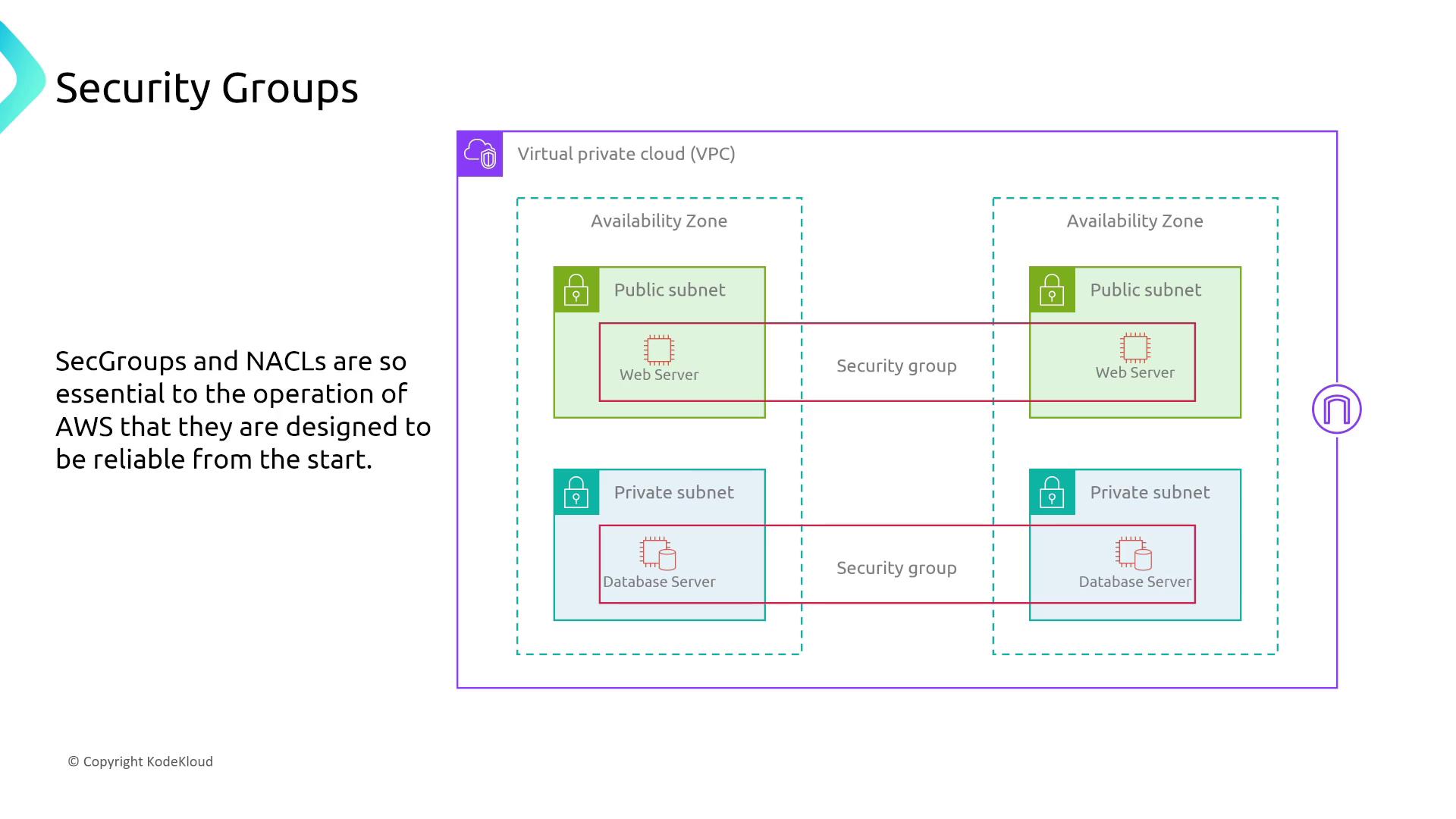
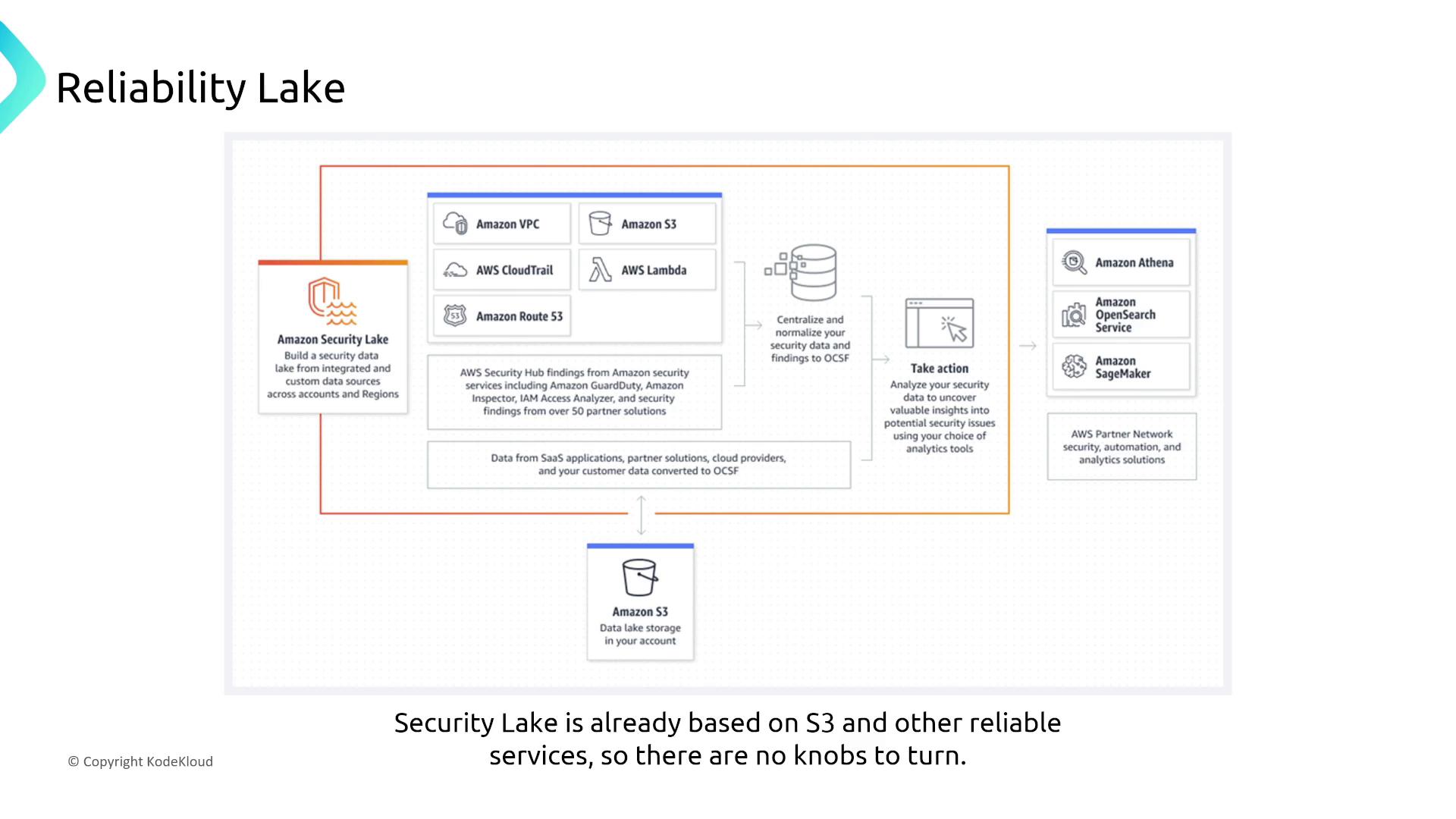
AWS Security Lake
AWS Security Lake aggregates security data from various AWS services into a centralized repository to provide a holistic view of your security posture. Its design leverages AWS’s inherent reliability, ensuring automation and remediation actions within a robust framework.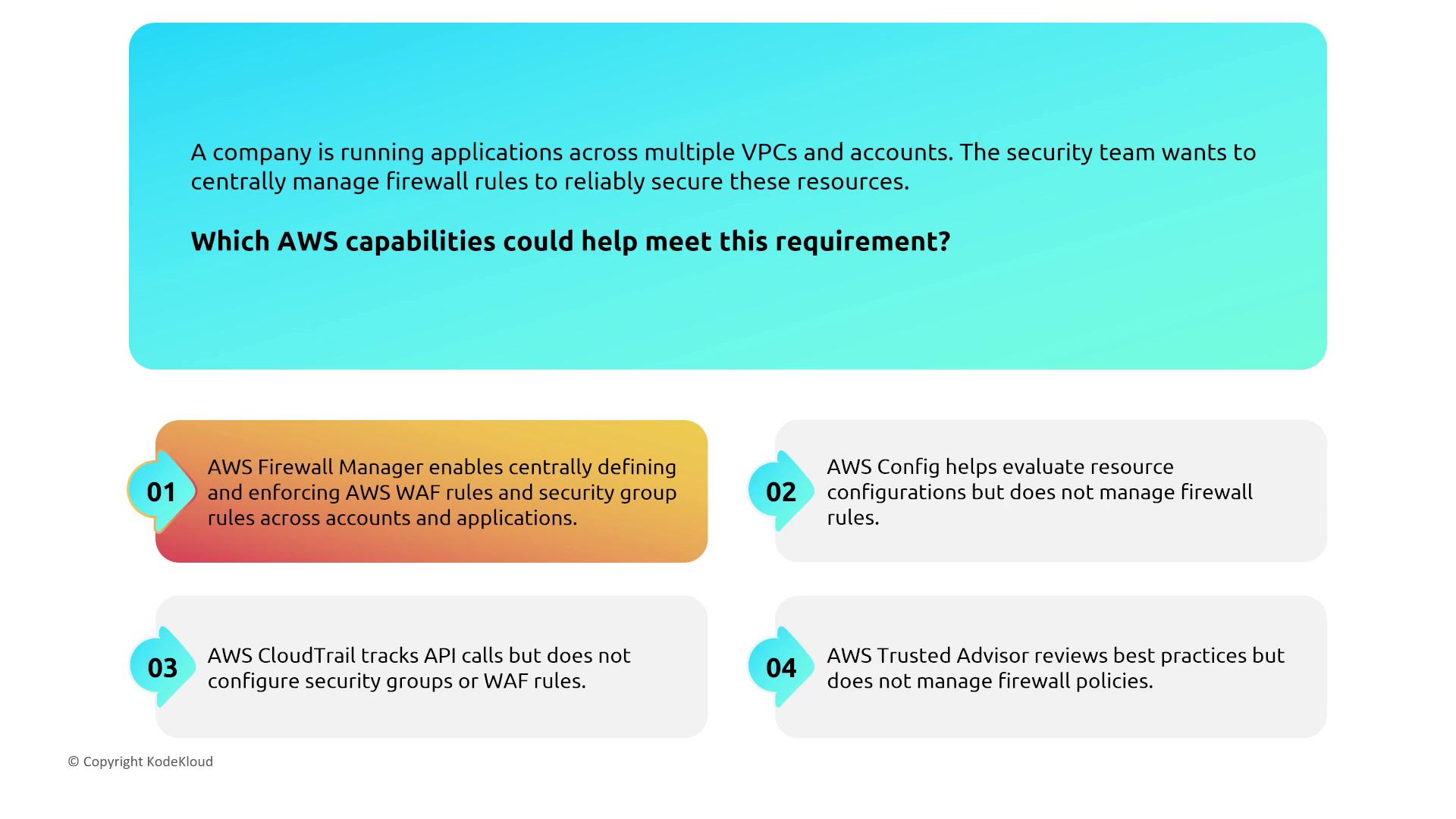
AWS Web Application Firewall (WAF)
AWS WAF is a globally distributed, highly managed service that protects web applications from common attacks including SQL injection and cross-site scripting. Its distributed architecture provides excellent reliability in managing web threats.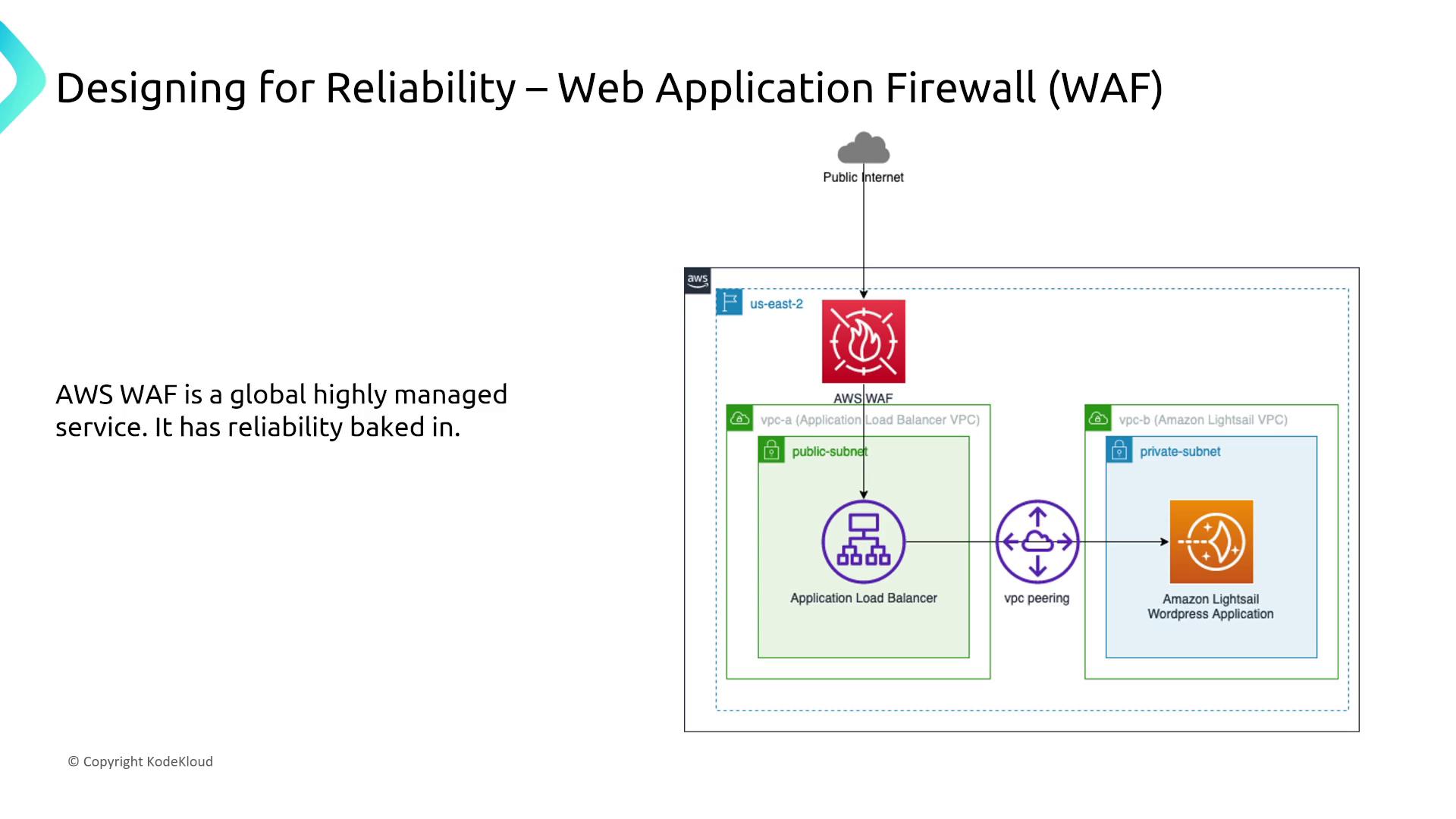
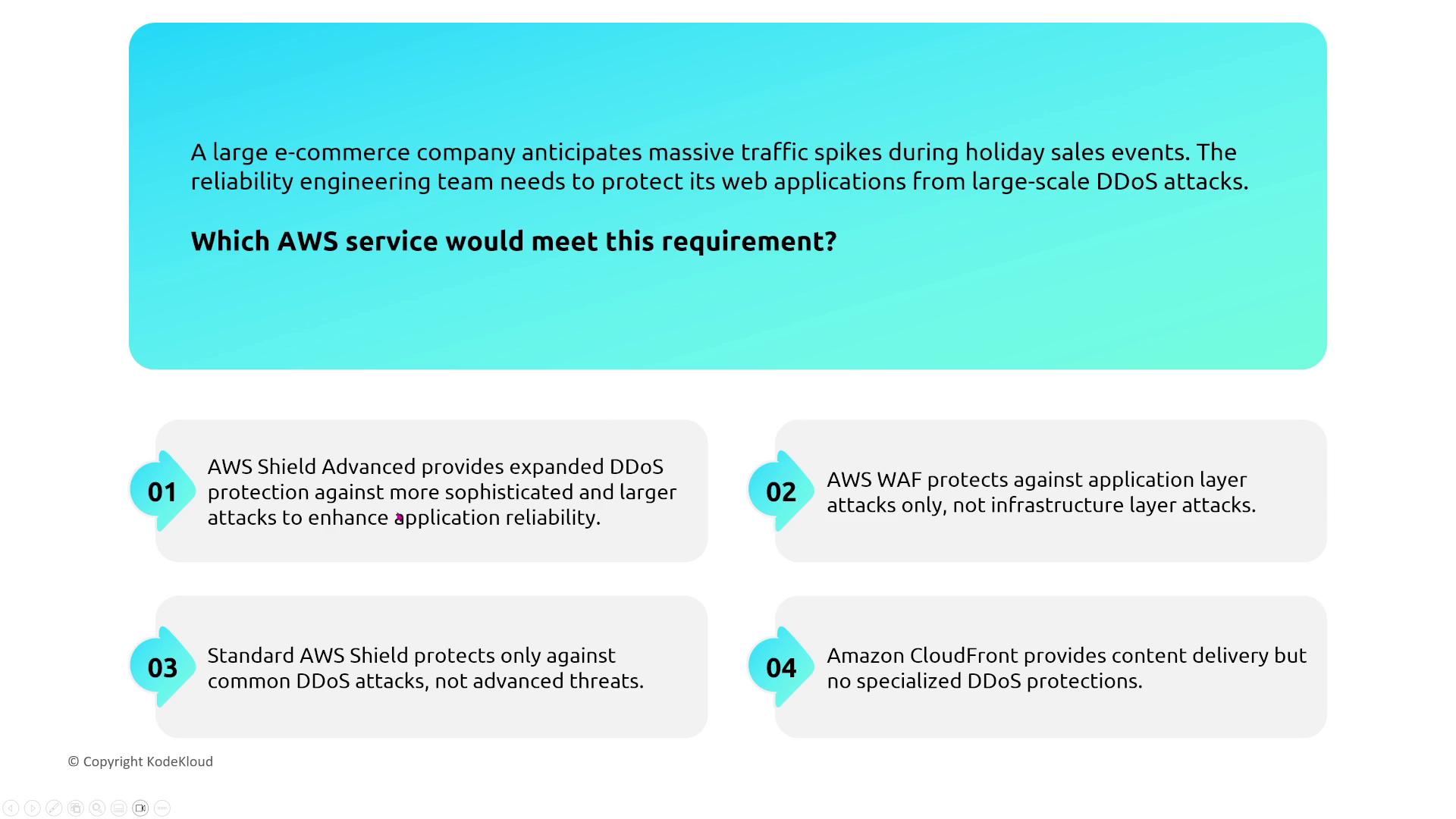
AWS Shield
AWS Shield provides always-on DDoS protection. The standard tier delivers inherent reliability, while Shield Advanced (with additional cost and commitment) integrates with services like AWS WAF and Firewall Manager to offer proactive DDoS threat mitigation.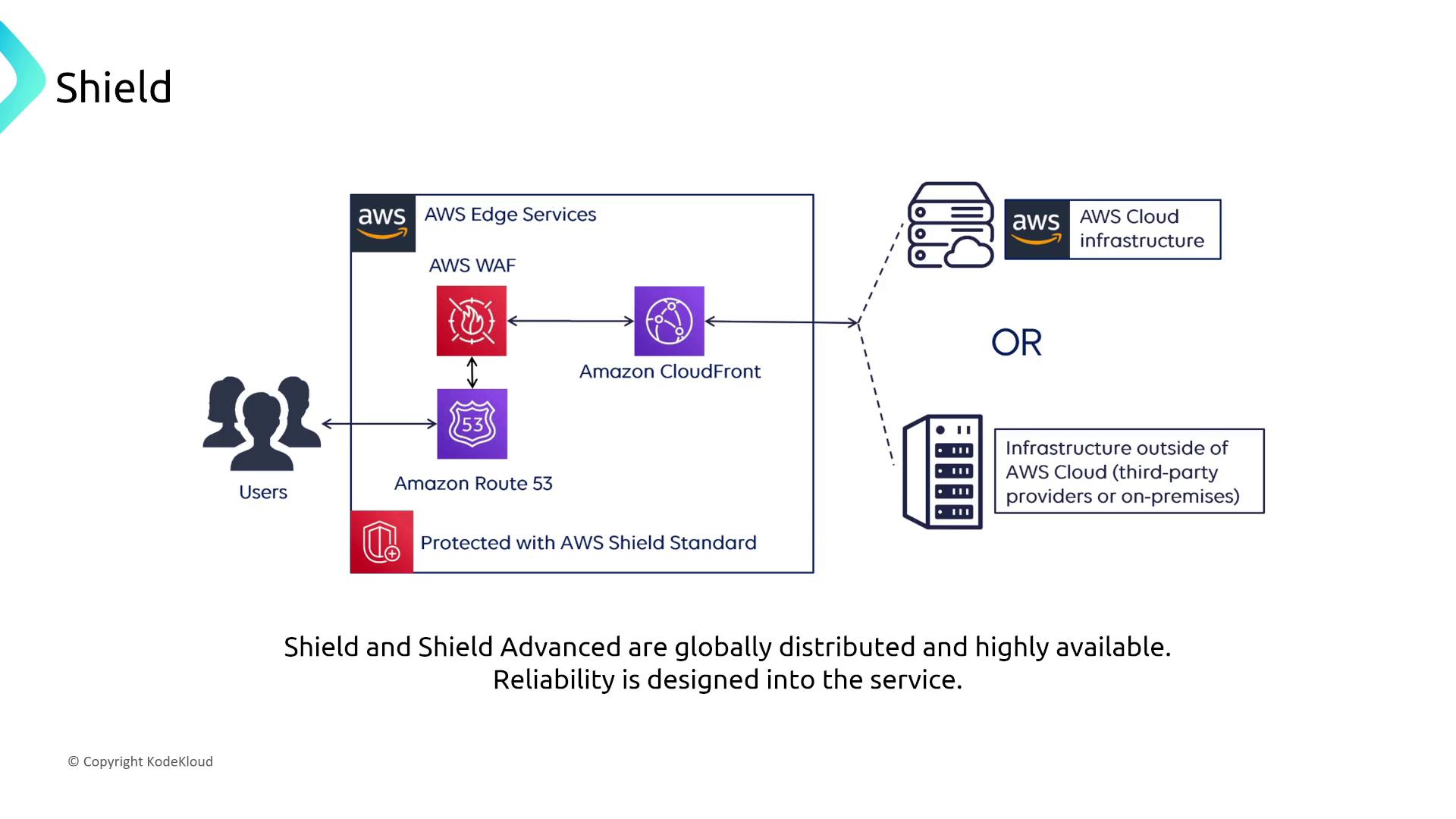
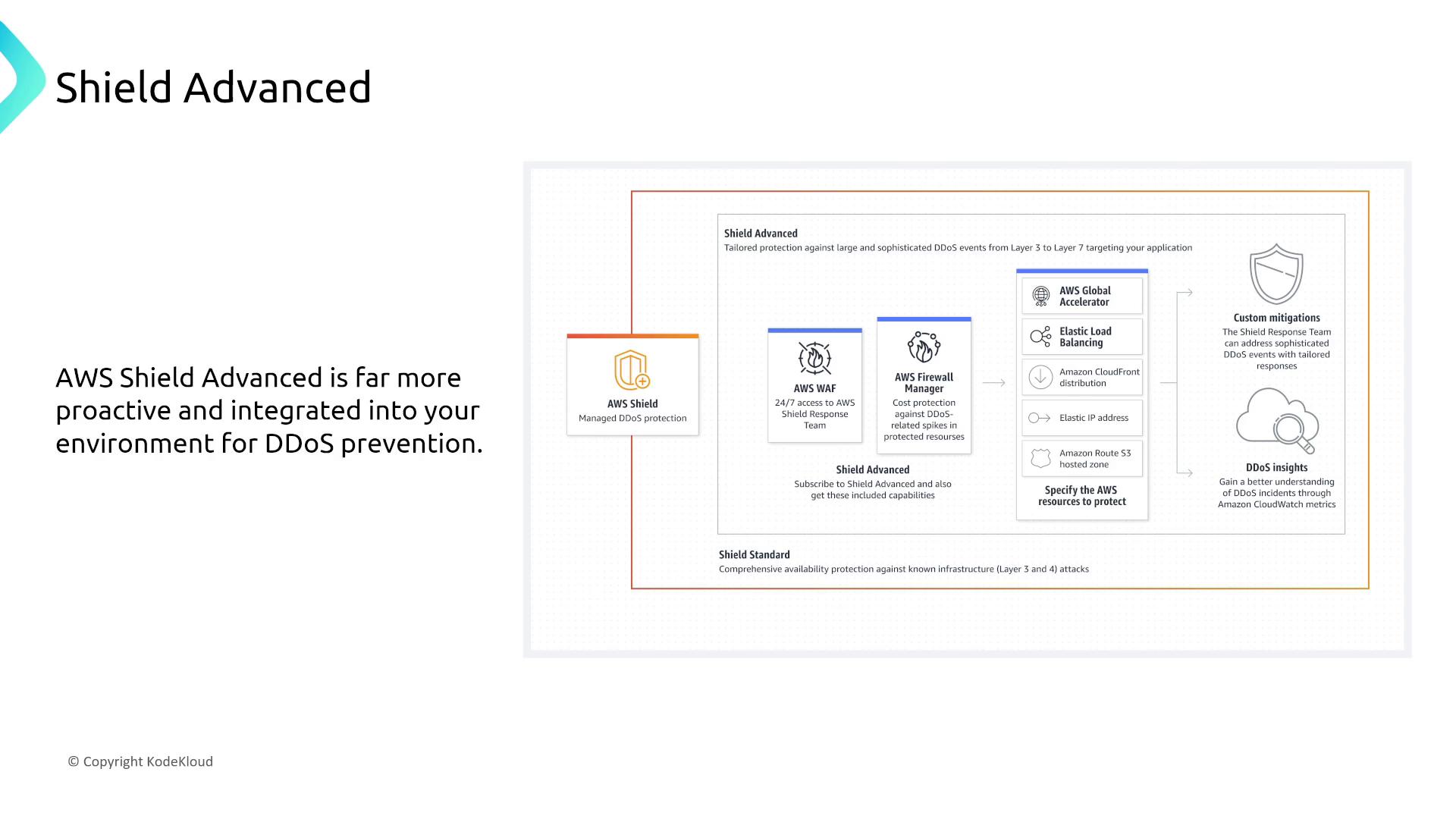
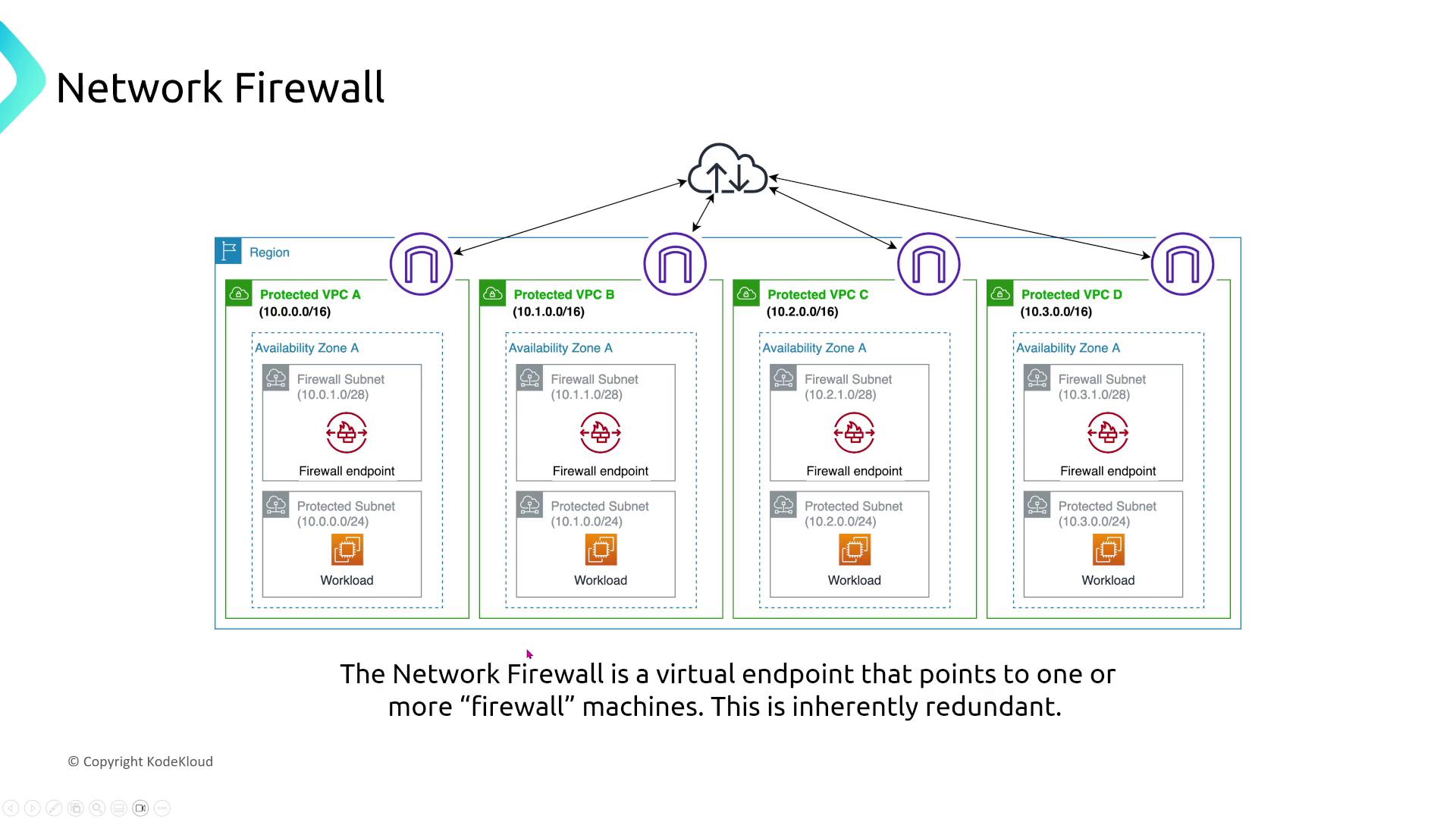
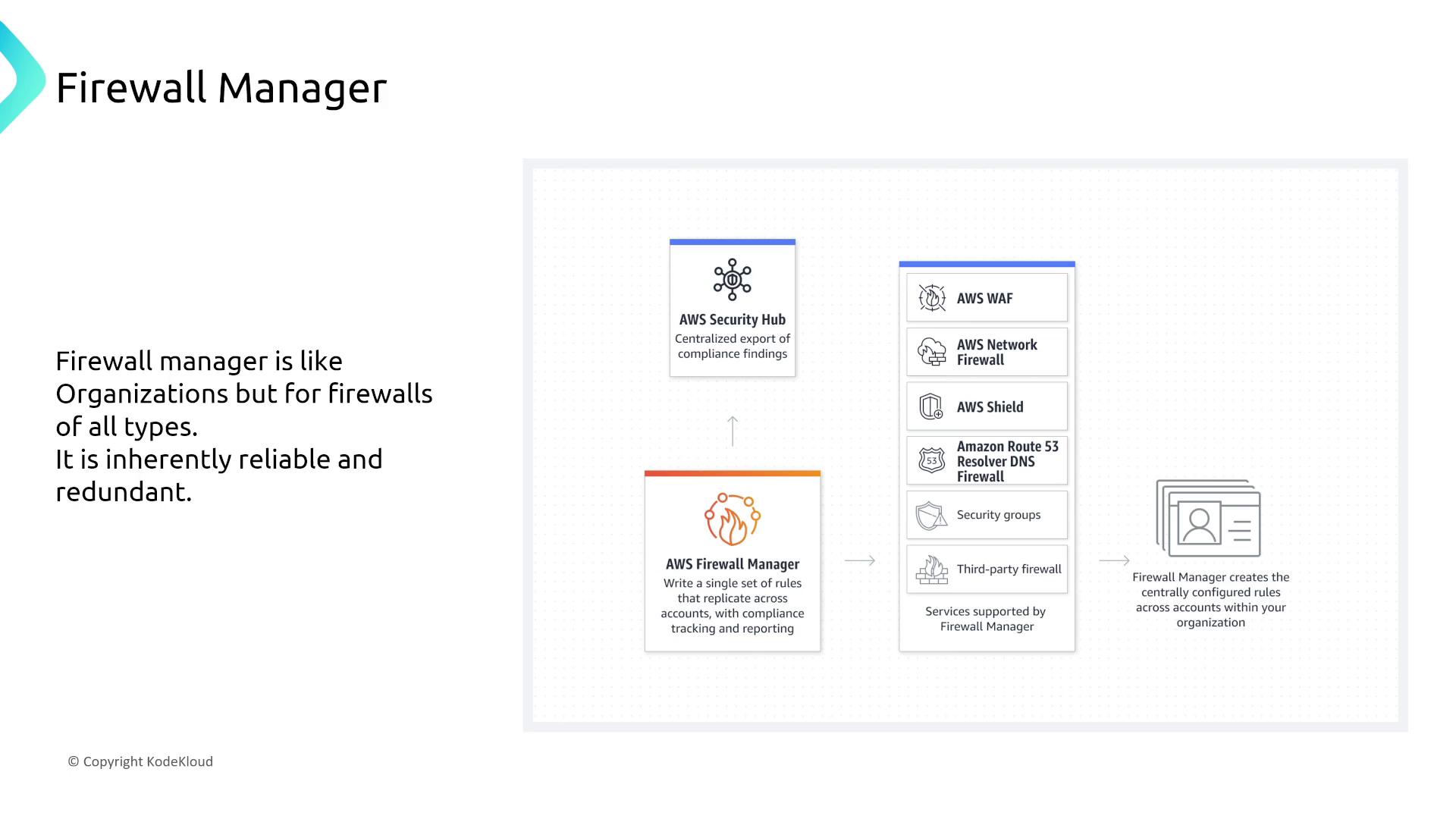
AWS Network Firewall and Firewall Manager
AWS Network Firewall offers a virtual, multi-AZ firewall solution that ensures redundancy across availability zones. Combined with AWS Firewall Manager, organizations can centrally manage and enforce security policies across multiple accounts and VPCs.